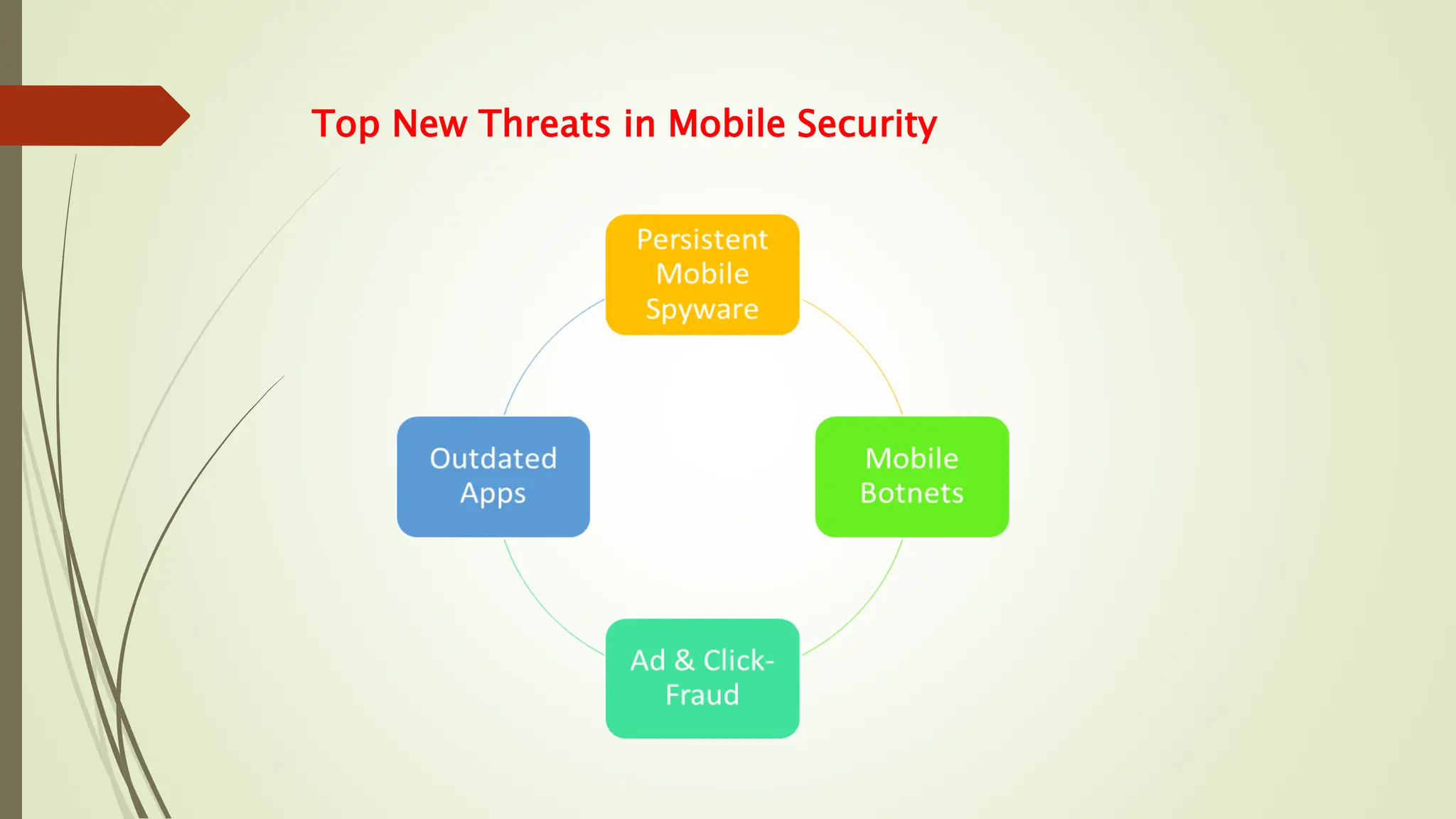
The document discusses the importance of cybersecurity awareness, highlighting its significance in preventing cybercrime and promoting safe online practices. During Cybersecurity Awareness Month, individuals are educated on various threats such as identity theft, malware, and phishing attacks, and the necessity of security training is emphasized. The document also outlines measures like two-factor authentication, password management, and mobile security tips to safeguard personal and business data.