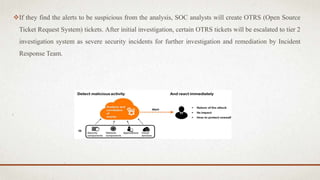
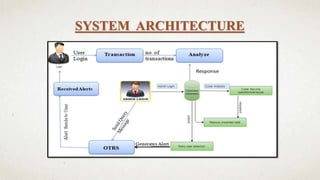
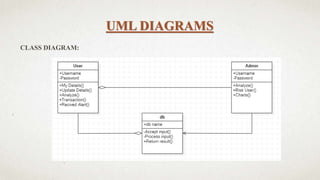
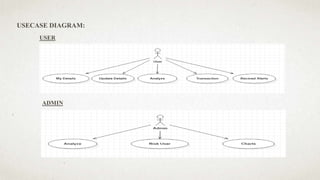
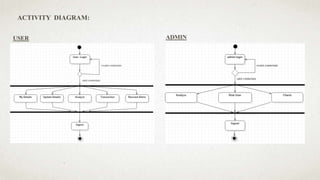
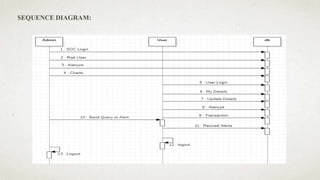
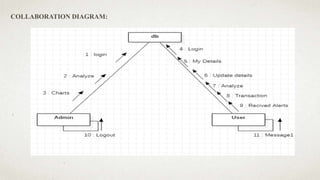
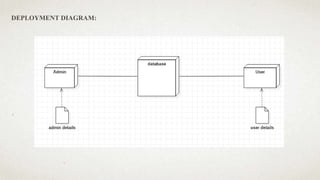
The document outlines a user-centric machine learning framework for enhancing the functionality of Security Operations Centers (SOCs) in cyber security. It highlights the importance of a proactive approach in detecting potential threats by utilizing existing security information and event management systems. The proposed system aims to improve user awareness and risk reduction by analyzing security data and optimizing detection methodologies.