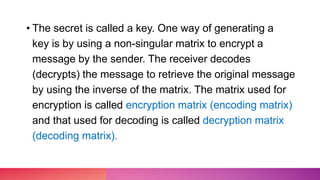
This document discusses cryptography and linear algebra. It defines cryptography as the study of secure communication techniques that allow only the sender and intended recipient to view message content. Encryption transforms information into an unreadable form using a secret key, while decryption transforms the encrypted code back into the original using the same key. An example demonstrates encrypting a message by multiplying it by an encoding matrix, transmitting the encrypted result, and decrypting it by multiplying by the inverse matrix.



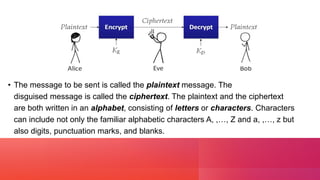
![E X A M P L E
Let the message to sent by the sender be "WELCOME".
Let the encoding matrix be
Since the key is taken as the operation of post multiplication by a square matrix of order 3, the
message is cut into pieces (WEL), (COM), (E), each of length 3 and converted into a sequence
of row matrices of numbers:
[ 23 5 12], [3 15 13], [5 0 0]](https://image.slidesharecdn.com/cryptography-230107090908-a01c123c/85/cryptography-pptx-6-320.jpg)
![[ 23 5 12], [3 15 13], [5 0 0]
Now that, we have included two zeros in the last row matrix. The reason is to get a row
matrix with 5 as the first entry.
Next, we encode the message by post-multiplying each row matrix as given below:](https://image.slidesharecdn.com/cryptography-230107090908-a01c123c/85/cryptography-pptx-7-320.jpg)
![So the encoded message is [45 –28 23] [[46 –18 3] [5 -5 5]
The receiver will decode the message by the reverse key, post- multiplying by thee inverse of A.
The reciever decodes the coded message as follows:](https://image.slidesharecdn.com/cryptography-230107090908-a01c123c/85/cryptography-pptx-8-320.jpg)
![So the sequence of
decoded row matrices is
[23 5 12], [3 15 13], [5 0 0].
Thus the receiver reads the
message as "WELCOME".](https://image.slidesharecdn.com/cryptography-230107090908-a01c123c/85/cryptography-pptx-9-320.jpg)
