This document outlines the development of an Uber clone using Spring Boot and MySQL, detailing the creation of a new database and various project dependencies required for features such as user management, car tracking, and payment processing. It emphasizes the importance of user authentication, the structure of user data entities, and includes code snippets for user-related functionalities such as adding and updating users. Additionally, it discusses the implementation of a user service that handles user operations securely using password hashing techniques.


![@Entity
public class User {
@Id
@GeneratedValue(strategy=GenerationType.AUTO)
private Long id;
private String givenName;
private String surname;
private String phone;
private String email;
private String password;
private String facebookId;
private String googleId;
private boolean driver;
private String car;
private boolean hailing;
private Long assignedUser;
private float currentRating;
private double latitude;
private double longitude;
private float direction;
@Lob
private byte[] avatar;
User
The User JPA entity uses an auto increment ID value for simplicity. Let’s go over the various pieces here.
These are part of the users settings just general configuration](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-5-320.jpg)
![@Entity
public class User {
@Id
@GeneratedValue(strategy=GenerationType.AUTO)
private Long id;
private String givenName;
private String surname;
private String phone;
private String email;
private String password;
private String facebookId;
private String googleId;
private boolean driver;
private String car;
private boolean hailing;
private Long assignedUser;
private float currentRating;
private double latitude;
private double longitude;
private float direction;
@Lob
private byte[] avatar;
User
The password stores the hashed value of the password and not the plain text version. We’ll discuss hashing passwords soon](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-6-320.jpg)
![@Entity
public class User {
@Id
@GeneratedValue(strategy=GenerationType.AUTO)
private Long id;
private String givenName;
private String surname;
private String phone;
private String email;
private String password;
private String facebookId;
private String googleId;
private boolean driver;
private String car;
private boolean hailing;
private Long assignedUser;
private float currentRating;
private double latitude;
private double longitude;
private float direction;
@Lob
private byte[] avatar;
User
We will use these when we need to enable login with a social network account. These are the internal network ID’s we’ll use for verification](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-7-320.jpg)
![@Entity
public class User {
@Id
@GeneratedValue(strategy=GenerationType.AUTO)
private Long id;
private String givenName;
private String surname;
private String phone;
private String email;
private String password;
private String facebookId;
private String googleId;
private boolean driver;
private String car;
private boolean hailing;
private Long assignedUser;
private float currentRating;
private double latitude;
private double longitude;
private float direction;
@Lob
private byte[] avatar;
User
A driver is also a user in the system. If this user is a driver this is marked as true. By referring to both the end user and the driver with the same class we can simplify the
code](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-8-320.jpg)
![@Entity
public class User {
@Id
@GeneratedValue(strategy=GenerationType.AUTO)
private Long id;
private String givenName;
private String surname;
private String phone;
private String email;
private String password;
private String facebookId;
private String googleId;
private boolean driver;
private String car;
private boolean hailing;
private Long assignedUser;
private float currentRating;
private double latitude;
private double longitude;
private float direction;
@Lob
private byte[] avatar;
User
If this is a driver this is the description of his car we’ll need for the app](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-9-320.jpg)
![@Entity
public class User {
@Id
@GeneratedValue(strategy=GenerationType.AUTO)
private Long id;
private String givenName;
private String surname;
private String phone;
private String email;
private String password;
private String facebookId;
private String googleId;
private boolean driver;
private String car;
private boolean hailing;
private Long assignedUser;
private float currentRating;
private double latitude;
private double longitude;
private float direction;
@Lob
private byte[] avatar;
User
This field is set to true if we are currently in the process of hailing a taxi](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-10-320.jpg)
![@Entity
public class User {
@Id
@GeneratedValue(strategy=GenerationType.AUTO)
private Long id;
private String givenName;
private String surname;
private String phone;
private String email;
private String password;
private String facebookId;
private String googleId;
private boolean driver;
private String car;
private boolean hailing;
private Long assignedUser;
private float currentRating;
private double latitude;
private double longitude;
private float direction;
@Lob
private byte[] avatar;
User
If the taxi is taken by a user this field maps to the user ID. It is set to null if the taxi is available](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-11-320.jpg)
![@Entity
public class User {
@Id
@GeneratedValue(strategy=GenerationType.AUTO)
private Long id;
private String givenName;
private String surname;
private String phone;
private String email;
private String password;
private String facebookId;
private String googleId;
private boolean driver;
private String car;
private boolean hailing;
private Long assignedUser;
private float currentRating;
private double latitude;
private double longitude;
private float direction;
@Lob
private byte[] avatar;
User
We will have a separate object dealing with rating but we can’t sum it for every query so the rating value will be cached here](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-12-320.jpg)
![@Entity
public class User {
@Id
@GeneratedValue(strategy=GenerationType.AUTO)
private Long id;
private String givenName;
private String surname;
private String phone;
private String email;
private String password;
private String facebookId;
private String googleId;
private boolean driver;
private String car;
private boolean hailing;
private Long assignedUser;
private float currentRating;
private double latitude;
private double longitude;
private float direction;
@Lob
private byte[] avatar;
User
This is the position and direction of the current user whether it’s a taxi or an end user. Notice I chose to just store the location values instead of using one of the custom
location based API’s supported by hibernate and mysql. I looked into those API’s and they are very powerful if you need complex location based API’s but for most
simple purposes like we have here they are an overkill and would have made the project more complex than it needs to be.
If you are building a complex GIS application I would suggest delving into some of those custom API’s.](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-13-320.jpg)
![@Entity
public class User {
@Id
@GeneratedValue(strategy=GenerationType.AUTO)
private Long id;
private String givenName;
private String surname;
private String phone;
private String email;
private String password;
private String facebookId;
private String googleId;
private boolean driver;
private String car;
private boolean hailing;
private Long assignedUser;
private float currentRating;
private double latitude;
private double longitude;
private float direction;
@Lob
private byte[] avatar;
User
This is a picture of the user stored as a database blob](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-14-320.jpg)
![private String surname;
private String phone;
private String email;
private String password;
private String facebookId;
private String googleId;
private boolean driver;
private String car;
private boolean hailing;
private Long assignedUser;
private float currentRating;
private double latitude;
private double longitude;
private float direction;
@Lob
private byte[] avatar;
@Column(unique=true)
private String authToken;
public User() {
authToken = UUID.randomUUID().toString();
}
User
One last column is the authToken which we initialize with a unique random ID. We will use this token to update the user and perform operations only the user is
authorized for.
Think of the authorization as a "key" to the server. We want to block a different user from sending a request that pretends to be our user. This is possible to do if a hacker
sniffs our network traffic and tries to "pretend" he's our app. One approach would be sending the password to the server every time but that means storing and sending
a password which holds risk.
In this case we generate a random and long key that's hard to brute force. We send the key to the client and it stores that key. From that point on we have proof that this
user is valid.
I’ve discussed this before in the restaurant app if you want to check that out.](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-15-320.jpg)



![@Service
public class UserService {
@Autowired
private UserRepository users;
@Autowired
private PasswordEncoder encoder;
public String addUser(UserDAO user) {
User u = new User(user);
u.setPassword(encoder.encode(user.getPassword()));
users.save(u);
return u.getAuthToken();
}
public byte[] getAvatar(Long id) {
User u = users.findOne(id);
return u.getAvatar();
}
public void setAvatar(String token, byte[] a) {
User u = users.findByAuthToken(token).get(0);
u.setAvatar(a);
users.save(u);
}
UserService
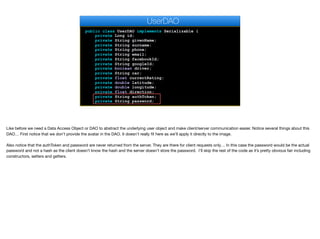
The user service class is a business object that abstracts the user access code. If we think of the User object as the database abstraction and the DAO as a
communication abstraction the service is the actual API of the server. We will later wrap it with a webservice call to make that API accessible to the end user. This might
seem like an overkill with “too many classes” which is a common problem for Java developers. However, in this case it’s justified. By using the service class I can build
unit tests that test the server logic only without going through the complexities of the web tier. I can also connect some of the common API’s through the websocket layer
moving forward. So having most of my business logic in this class makes a lot of sense.
I have two autowired values here first is the crud interface we discussed earlier that I can use to work with users and drivers.
The second one is this Spring Boot interface used to hash and salt the passwords. Just using this interface means that even in a case of a hack your users passwords
would still be safe. I’ll discuss this further soon.](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-20-320.jpg)
![@Service
public class UserService {
@Autowired
private UserRepository users;
@Autowired
private PasswordEncoder encoder;
public String addUser(UserDAO user) {
User u = new User(user);
u.setPassword(encoder.encode(user.getPassword()));
users.save(u);
return u.getAuthToken();
}
public byte[] getAvatar(Long id) {
User u = users.findOne(id);
return u.getAvatar();
}
public void setAvatar(String token, byte[] a) {
User u = users.findByAuthToken(token).get(0);
u.setAvatar(a);
users.save(u);
}
UserService
Adding a user consists of creating a new User object with the DAO and invoking the builtin CRUD save method. Here we encode the password this is pretty seamless in
Spring but remarkably secure as it uses a salted hash. Passwords aren't encrypted they are hashed and salted. Encryption is a 2 way algorithm, you can encode data
and decode it back. Hashing codes the data in such a way that can't be reversed. To verify the password we need to rehash it and check the hashed strings. Hashing
alone isn't enough as it can be assaulted with various attacks. One of the tricks against hash attacks is salt. The salt is random data that's injected into the hash. An
attacker can't distinguish between the salt and hash data which makes potential attacks much harder. The password hashing algorithm of Spring Boot always produces a
60 character string which would be pretty hard to crack.
I’ll soon discuss the process of checking a password for validity as it’s a pretty big subject](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-21-320.jpg)
![@Service
public class UserService {
@Autowired
private UserRepository users;
@Autowired
private PasswordEncoder encoder;
public String addUser(UserDAO user) {
User u = new User(user);
u.setPassword(encoder.encode(user.getPassword()));
users.save(u);
return u.getAuthToken();
}
public byte[] getAvatar(Long id) {
User u = users.findOne(id);
return u.getAvatar();
}
public void setAvatar(String token, byte[] a) {
User u = users.findByAuthToken(token).get(0);
u.setAvatar(a);
users.save(u);
}
UserService
Notice that getAvatar uses the id value. That leaves a small security weakness where a user can scan the id's for images of the drivers/users. I'm not too concerned
about that issue so I'm leaving it in place, however letting a user update the avatar is something that needs a secure token…](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-22-320.jpg)
![public void setAvatar(String token, byte[] a) {
User u = users.findByAuthToken(token).get(0);
u.setAvatar(a);
users.save(u);
}
public void updateUser(UserDAO user) {
User u = users.findByAuthToken(user.getAuthToken()).get(0);
u.setCar(user.getCar());
u.setEmail(user.getEmail());
u.setFacebookId(user.getFacebookId());
u.setGivenName(user.getGivenName());
u.setSurname(user.getSurname());
u.setGoogleId(user.getGoogleId());
u.setLatitude(user.getLatitude());
u.setLongitude(user.getLongitude());
u.setPhone(user.getPhone());
users.save(u);
}
public UserDAO loginByPhone(String phone,
UserService
Continuing with the security aspect notice that things such as password and token are special cases that we don't want to update using the same flow as they are pretty
sensitive](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-23-320.jpg)











![@RequestMapping(method=RequestMethod.GET,value = "/login")
public @ResponseBody UserDAO login(@RequestParam(
value="password", required=true) String password,String phone, String googleId, String facebookId)
throws UserAuthenticationException {
if(phone != null) {
return users.loginByPhone(phone, password);
}
if(facebookId != null) {
return users.loginByFacebook(facebookId, password);
}
if(googleId != null) {
return users.loginByGoogle(googleId, password);
}
return null;
}
@RequestMapping(value = "/avatar/{id:.+}",
method = RequestMethod.GET)
public ResponseEntity<byte[]> getAvatar(
@PathVariable("id") Long id) {
byte[] av = users.getAvatar(id);
if(av != null) {
return ResponseEntity.ok().
contentType(MediaType.IMAGE_JPEG).body(av);
}
return ResponseEntity.notFound().build();
}
UserWebservice
Images just map to a URL for the given image id so the URL /user/avatar/userId will return the image for the given user with the mime type image/jpeg. If the image isn't
there we'll return an HTTP not-found error (404) which we can handle in the client code](https://image.slidesharecdn.com/creatinganuberclone-partxi-transcript-220804064705-2eadd1ae/85/Creating-an-Uber-Clone-Part-XI-Transcript-pdf-35-320.jpg)

