The document describes a PhD project that aims to analyze semantic networks of identifier names in source code to improve code maintainability and quality. The project seeks to extract semantic relationships between identifier names from source code to build semantic networks. These networks will then be analyzed to identify naming inconsistencies and recommend more semantically coherent identifier names to enhance code comprehension.








![2010 CRC PhD Student Conference
write(i39)
payload1 = payload()
key2 = key()
write(i14|7c|payload1|HMAC(sha1, i7|7c52657175657374|payload1, key2))
msg3 = read()
var4 = msg3{5,23}
branchF((memcmp(msg3{28,20},
HMAC(sha1, i8|7c526573706f6e7365|i14|7c|payload1|var4, key2)) != i0))
accept(var4)
Figure 1: An excerpt from the symbolic client trace. X{start, len} denotes
the substring of X starting at start of length len. iN is an integer with value N
(width information is omitted), and branchT and branchF are the true or false
branches taken by the code.
for the client side shown in figure 1: we see the client sending the request and
checking the condition on the server response before accepting it.
We are currently working to implement symbolic handling of buffer lengths
and sound handling of loops as well as making the extracted models compatible
with those understood by ProVerif and CryptoVerif, in particular simplifying
away any remaining arithmetic expressions from the symbolic trace.
One obvious drawback of concolic execution is that it only follows the single
path that was actually taken by the code. This is enough to produce an accurate
model when there is only one main path, however, libraries like OpenSSL contain
multiple nontrivial paths. Thus, to achieve verification of those libraries, we
plan to move the analysis towards being fully static in future.
Related Work One of the earliest security verification attempts directly
on code is probably CSur [Goubault-Larrecq and Parrennes, 2005] that deals
directly with C protocol implementations. It translates programs into a set
of Horn clauses that are fed directly into a general purpose theorem prover.
Unfortunately, it never went beyond some very simple implementations and has
not been developed since.
The work [J¨rjens, 2006] describes an approach of translating Java programs
u
in a manner similar to above. In our work we try to separate reasoning about
pointers and integers from reasoning about cryptography, in hope to achieve
greater scalability.
Some work has been done on verification of functional language implementa-
tions, either by translating the programs directly into π-calculus [Bhargavan et
al., 2006; Bhargavan et al., 2008] or by designing a type system that enforces
security [Bengtson et al., 2008]. Unfortunately, it is not trivial to adapt such
approaches to C-like languages.
ASPIER [Chaki and Datta, 2008] is using model checking for verification and
has been applied to OpenSSL. However, it does not truly start from C code: any
code explicitly dealing with pointers needs to be replaced by abstract summaries
Page 2 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-9-320.jpg)
![2010 CRC PhD Student Conference
that presumably have to be written manually.
Concolic execution is widely used to drive automatic test generation, like in
[Cadar et al., 2008] or [Godefroid et al., 2008]. One difference in our concolic
execution is that we need to assign symbols to whole bitstrings, whereas the
testing frameworks usually assign symbols to single bytes. We believe that our
work could be adapted for testing of cryptographic software. Usual testing
approaches try to create an input that satisfies a set of equations resulting from
checks in code. In presence of cryptography such equations will (hopefully) be
impossible to solve, so a more abstract model like ours might be useful.
A separate line of work deals with reconstruction of protocol message formats
from implementation binaries [Caballero et al., 2007; Lin et al., 2008; Wondracek
et al., 2008; Cui et al., 2008; Wang et al., 2009]. The goal is typically to
reconstruct field boundaries of a single message by observing how the binary
processes the message. Our premises and goals are different: we have the
advantage of starting from the source code, but in exchange we aim to reconstruct
the whole protocol flow instead of just a single message. Our reconstruction
needs to be sound to enable verification — all possible protocol flows should be
accounted for.
References
[Bengtson et al., 2008] Jesper Bengtson, Karthikeyan Bhargavan, C´dric Four-
e
net, Andrew D. Gordon, and Sergio Maffeis. Refinement types for secure
implementations. In CSF ’08: Proceedings of the 2008 21st IEEE Computer
Security Foundations Symposium, pages 17–32, Washington, DC, USA, 2008.
IEEE Computer Society.
[Bhargavan et al., 2006] Karthikeyan Bhargavan, C´dric Fournet, Andrew D.
e
Gordon, and Stephen Tse. Verified interoperable implementations of security
protocols. In CSFW ’06: Proceedings of the 19th IEEE workshop on Computer
Security Foundations, pages 139–152, Washington, DC, USA, 2006. IEEE
Computer Society.
[Bhargavan et al., 2008] Karthikeyan Bhargavan, C´dric Fournet, Ricardo Corin,
e
and Eugen Zalinescu. Cryptographically verified implementations for TLS.
In CCS ’08: Proceedings of the 15th ACM conference on Computer and
communications security, pages 459–468, New York, NY, USA, 2008. ACM.
[Caballero et al., 2007] Juan Caballero, Heng Yin, Zhenkai Liang, and Dawn
Song. Polyglot: automatic extraction of protocol message format using
dynamic binary analysis. In CCS ’07: Proceedings of the 14th ACM conference
on Computer and communications security, pages 317–329, New York, NY,
USA, 2007. ACM.
[Cadar et al., 2008] Cristian Cadar, Daniel Dunbar, and Dawson Engler. Klee:
Unassisted and automatic generation of high-coverage tests for complex sys-
Page 3 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-10-320.jpg)
![2010 CRC PhD Student Conference
tems programs. In USENIX Symposium on Operating Systems Design and
Implementation (OSDI 2008), San Diego, CA, december 2008.
[Chaki and Datta, 2008] Sagar Chaki and Anupam Datta. Aspier: An auto-
mated framework for verifying security protocol implementations. Technical
Report 08-012, Carnegie Mellon University, October 2008.
[Cui et al., 2008] Weidong Cui, Marcus Peinado, Karl Chen, Helen J. Wang, and
Luis Irun-Briz. Tupni: automatic reverse engineering of input formats. In CCS
’08: Proceedings of the 15th ACM conference on Computer and communications
security, pages 391–402, New York, NY, USA, 2008. ACM.
[DBL, 2008] Proceedings of the Network and Distributed System Security Sympo-
sium, NDSS 2008, San Diego, California, USA, 10th February - 13th February
2008. The Internet Society, 2008.
[Godefroid et al., 2008] Patrice Godefroid, Michael Y. Levin, and David A. Mol-
nar. Automated whitebox fuzz testing. In NDSS [2008].
[Goubault-Larrecq and Parrennes, 2005] J. Goubault-Larrecq and F. Parrennes.
Cryptographic protocol analysis on real C code. In Proceedings of the 6th
International Conference on Verification, Model Checking and Abstract Inter-
pretation (VMCAI’05), volume 3385 of Lecture Notes in Computer Science,
pages 363–379. Springer, 2005.
[J¨rjens, 2006] Jan J¨ rjens. Security analysis of crypto-based Java programs
u u
using automated theorem provers. In ASE ’06: Proceedings of the 21st
IEEE/ACM International Conference on Automated Software Engineering,
pages 167–176, Washington, DC, USA, 2006. IEEE Computer Society.
[Lin et al., 2008] Zhiqiang Lin, Xuxian Jiang, Dongyan Xu, and Xiangyu Zhang.
Automatic protocol format reverse engineering through context-aware moni-
tored execution. In NDSS [2008].
[Wang et al., 2009] Zhi Wang, Xuxian Jiang, Weidong Cui, Xinyuan Wang, and
Mike Grace. Reformat: Automatic reverse engineering of encrypted messages.
In Michael Backes and Peng Ning, editors, ESORICS, volume 5789 of Lecture
Notes in Computer Science, pages 200–215. Springer, 2009.
[Wondracek et al., 2008] Gilbert Wondracek, Paolo Milani Comparetti, Christo-
pher Kruegel, and Engin Kirda. Automatic Network Protocol Analysis. In
15th Symposium on Network and Distributed System Security (NDSS), 2008.
Page 4 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-11-320.jpg)
![2010 CRC PhD Student Conference
Analysing semantic networks of
identifier names to improve source code
maintainability and quality
Simon Butler
sjb792@student.open.ac.uk
Supervisors Michel Wermelinger, Yijun Yu & Helen Sharp
Department/Institute Centre for Research in Computing
Status Part-time
Probation viva After
Starting date October 2008
Source code is the written expression of a software design consisting of identifier
names – natural language phrases that represent concepts being manipulated
by the program – embedded in a framework of keywords and operators provided
by the programming language. Identifiers are crucial for program comprehen-
sion [9], a necessary activity in the development and maintenance of software.
Despite their importance, there is little understanding of the relationship be-
tween identifier names and source code quality and maintainability. Neither is
there automated support for identifier management or the selection of relevant
natural language content for identifiers during software development.
We will extend current understanding of the relationship between identifier
name quality and source code quality and maintainability by developing tech-
niques to analyse identifiers for meaning, modelling the semantic relationships
between identifiers and empirically validating the models against measures of
maintainability and software quality. We will also apply the analysis and mod-
elling techniques in a tool to support the selection and management of identifier
names during software development, and concept identification and location for
program comprehension.
The consistent use of clear identifier names is known to aid program com-
prehension [4, 7, 8]. However, despite the advice given in programming conven-
tions and the popular programming literature on the use of meaningful identifier
names in source code, the reality is that identifier names are not always meaning-
ful, may be selected in an ad hoc manner, and do not always follow conventions
[5, 1, 2].
Researchers in the reverse engineering community have constructed mod-
els to support program comprehension. The models range in complexity from
textual search systems [11], to RDF-OWL ontologies created either solely from
source code and identifier names [8], or with the inclusion of supporting doc-
umentation and source code comments [13]. The ontologies typically focus on
Page 5 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-12-320.jpg)
![2010 CRC PhD Student Conference
class and method names, and are used for concept identification and location
based on the lexical similarity of identifier names. The approach, however, does
not directly address the quality of identifier names used.
The development of detailed identifier name analysis has focused on method
names because their visibility and reuse in APIs implies a greater need for them
to contain clear information about their purpose [10]. Caprile and Tonella [3]
derived both a grammar and vocabulary for C function identifiers, sufficient
for the implementation of automated name refactoring. Høst and Østvold [5]
have since analysed Java method names looking for a common vocabulary that
could form the basis of a naming scheme for Java methods. Their analysis of
the method names used in multiple Java projects found common grammatical
forms; however, there were sufficient degenerate forms for them to be unable to
derive a grammar for Java method names.
The consequences of identifier naming problems have been considered to be
largely confined to the domain of program comprehension. However, Deißenb¨ck o
and Pizka observed an improvement in maintainability when their rules of con-
cise and consistent naming were applied to a project [4], and our recent work
found statistical associations between identifier name quality and source code
quality [1, 2]. Our studies, however, only looked at the construction of the
identifier names in isolation, and not at the relationships between the meaning
of the natural language content of the identifiers. We hypothesise that a rela-
tionship exists between the quality of identifier names, in terms of their natural
language content and semantic relationships, and the quality of source code,
which can be understood in terms of the functionality, reliability, and usability
of the resulting software, and its maintainability [6]. Accordingly, we seek to
answer the following research question:
How are the semantic relationships between identifier names, in-
ferred from their natural language content and programming lan-
guage structure, related to source code maintainability and quality?
We will construct models of source code as semantic networks predicated
on both the semantic content of identifier names and the relationships between
identifier names inferred from the programming language structure. For exam-
ple, the simple class Car in Figure 1 may be represented by the semantic network
in Figure 2. Such models can be applied to support empirical investigations of
the relationship between identifier name quality and source code quality and
maintainability. The models may also be used in tools to support the manage-
ment and selection of identifier names during software development, and to aid
concept identification and location during source code maintenance.
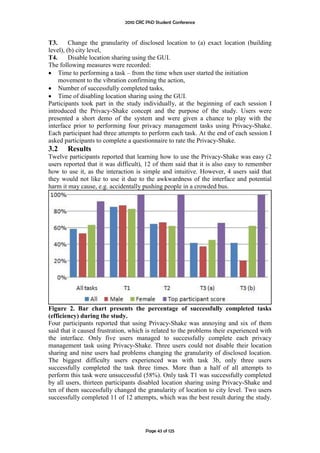
public c l a s s Car extends V e h i c l e {
Engine e n g i n e ;
}
Figure 1: The class Car
We will analyse identifier names mined from open source Java projects to
create a catalogue of identifier structures to understand the mechanisms em-
ployed by developers to encode domain information in identifiers. We will build
Page 6 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-13-320.jpg)
![2010 CRC PhD Student Conference
on the existing analyses of C function and Java method identifier names [3, 5, 8],
and anticipate the need to develop additional techniques to analyse identifiers,
particularly variable identifier names.
extends
Car Vehicle
has a
has instance named
Engine engine
Figure 2: A semantic network of the class Car
Modelling of both the structural and semantic relationships between iden-
tifiers can be accomplished using Gellish [12], an extensible controlled natural
language with dictionaries for natural languages – Gellish English being the
variant for the English language. Unlike a conventional dictionary, a Gellish
dictionary includes human- and machine-readable links between entries to de-
fine relationships between concepts – thus making Gellish a semantic network –
and to show hierarchical linguistic relationships such as meronymy, an entity–
component relationship. Gellish dictionaries also permit the creation of multiple
conceptual links for individual entries to define polysemic senses.
The natural language relationships catalogued in Gellish can be applied to
establish whether the structural relationship between two identifiers implied by
the programming language is consistent with the conventional meaning of the
natural language found in the identifier names. For example, a field is implic-
itly a component of the containing class allowing the inference of a conceptual
and linguistic relationship between class and field identifier names. Any incon-
sistency between the two relationships could indicate potential problems with
either the design or with the natural language content of the identifier names.
We have assumed a model of source code development and comprehension
predicated on the idea that it is advantageous for coherent and relevant semantic
relationships to exist between identifier names based on their natural language
content. To assess the relevance of our model to real-world source code we
will validate the underlying assumption empirically. We intend to mine both
software repositories and defect reporting systems to identify source code impli-
cated in defect reports and evaluate the source code in terms of the coherence
and consistency of models of its identifiers. To assess maintainability we will
investigate how source code implicated in defect reports develops in successive
versions – e.g. is the code a continuing source of defects? – and monitor areas of
source code modified between versions to determine how well our model predicts
defect-prone and defect-free regions of source code.
We will apply the results of our research to develop a tool to support the
selection and management of identifier names during software development, as
well as modelling source code to support software maintenance. We will evaluate
and validate the tool with software developers – both industry partners and
FLOSS developers – to establish the value of identifier naming support. While
intended for software developers, the visualisations of source code presented by
Page 7 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-14-320.jpg)
![2010 CRC PhD Student Conference
the tool will enable stakeholders (e.g. domain experts) who are not literate
in programming or modelling languages (like Java and UML) to examine, and
feedback on, the representation of domain concepts in source code.
References
[1] S. Butler, M. Wermelinger, Y. Yu, and H. Sharp. Relating identifier naming
flaws and code quality: an empirical study. In Proc. of the Working Conf.
on Reverse Engineering, pages 31–35. IEEE Computer Society, 2009.
[2] S. Butler, M. Wermelinger, Y. Yu, and H. Sharp. Exploring the influence
of identifier names on code quality: an empirical study. In Proc. of the
14th European Conf. on Software Maintenance and Reengineering, pages
159–168. IEEE Computer Society, 2010.
[3] B. Caprile and P. Tonella. Restructuring program identifier names. In
Proc. Int’l Conf. on Software Maintenance, pages 97–107. IEEE, 2000.
[4] F. Deißenb¨ck and M. Pizka. Concise and consistent naming. Software
o
Quality Journal, 14(3):261–282, Sep 2006.
[5] E. W. Høst and B. M. Østvold. The Java programmer’s phrase book.
In Software Language Engineering, volume 5452 of LNCS, pages 322–341.
Springer, 2008.
[6] International Standards Organisation. ISO/IEC 9126-1: Software engineer-
ing – product quality, 2001.
[7] D. Lawrie, H. Feild, and D. Binkley. An empirical study of rules for well-
formed identifiers. Journal of Software Maintenance and Evolution: Re-
search and Practice, 19(4):205–229, 2007.
[8] D. Ratiu. Intentional Meaning of Programs. PhD thesis, Technische Uni-
¸
versit¨t M¨nchen, 2009.
a u
[9] V. Rajlich and N. Wilde. The role of concepts in program comprehension.
In Proc. 10th Int’l Workshop on Program Comprehension, pages 271–278.
IEEE, 2002.
[10] M. Robillard. What makes APIs hard to learn? Answers from developers.
IEEE Software, 26(6):27–34, Nov.-Dec. 2009.
[11] G. Sridhara, E. Hill, L. Pollock, and K. Vijay-Shanker. Identifying word
relations in software: a comparative study of semantic similarity tools. In
Proc Int’l Conf. on Program Comprehension, pages 123–132. IEEE, June
2008.
[12] A. S. H. P. van Renssen. Gellish: a generic extensible ontological language.
Delft University Press, 2005.
[13] R. Witte, Y. Zhang, and J. Rilling. Empowering software maintainers with
semantic web technologies. In European Semantic Web Conf., pages 37–52,
2007.
Page 8 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-15-320.jpg)
![2010 CRC PhD Student Conference
Discovering translational patterns
in symbolic representations of music
Tom Collins
http://users.mct.open.ac.uk/tec69
Supervisors Robin Laney
Alistair Willis
Paul Garthwaite
Department/Institute Centre for Research in Computing
Status Fulltime
Probation viva After
Starting date October 2008
RESEARCH QUESTION
How can current methods for pattern discovery in music be improved and integrated
into an automated composition system?
The presentation will address the first half of this research question: how can current
methods for pattern discovery in music be improved?
INTRA-OPUS PATTERN DISCOVERY
Suppose that you wish to get to know a particular piece of music, and that you have a
copy of the score of the piece or a MIDI file. (Scores and MIDI files are symbolic
representations of music and are the focus of my presentation, as opposed to sound
recordings.) Typically, to become familiar with a piece, one listens to the MIDI file or
studies/plays through the score, gaining an appreciation of where and how material is
repeated, and perhaps also gaining an appreciation of the underlying structure.
The literature contains several algorithmic approaches to this task, referred to as
‘intra-opus’ pattern discovery [2, 4, 5]. Given a piece of music in a symbolic
representation, the aim is to define and evaluate an algorithm that discovers and
returns patterns occurring within the piece. Some potential applications for such an
algorithm are as follows:
• A pattern discovery tool to aid music students.
• Comparing an algorithm’s discoveries with those of a music expert as a means
of investigating human perception of music.
• Stylistic composition (the process of writing in the style of another composer
or period) assisted by using the patterns/structure returned by a pattern
discovery algorithm [1, 3].
Page 9 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-16-320.jpg)
![2010 CRC PhD Student Conference
TWO IMPROVEMENTS
Current methods for pattern discovery in music can be improved in two ways:
1. The way in which the algorithm’s discoveries are displayed for a user can be
improved.
2. A new algorithm can be said to improve upon existing algorithms if, according
to standard metrics, it is the strongest-performing algorithm on a certain task.
Addressing the first area for improvement, suppose that an algorithm has discovered
hundreds of patterns within a piece of music. Now these must be presented to the
user, but in what order? Various formulae have been proposed for rating a discovered
pattern, based on variables that quantify attributes of that pattern and the piece of
music in which it appears [2, 4]. To my knowledge, none have been derived or
validated empirically. So I conducted a study in which music undergraduates
examined excerpts taken from Chopin’s mazurkas and were instructed to rate already-
discovered patterns, giving high ratings to patterns that they thought were noticeable
and/or important. A model useful for relating participants’ ratings to the attributes was
determined using variable selection and cross-validation. This model leads to a new
formula for rating discovered patterns, and the basis for this formula constitutes a
methodological improvement.
Addressing the second area for improvement, I asked a music analyst to analyse two
sonatas by Domenico Scarlatti and two preludes by Johann Sebastian Bach. The brief
was similar to the intra-opus discovery task described above: given a piece of music
in staff notation, discover translational patterns that occur within the piece. Thus, a
benchmark of translational patterns was formed for each piece, the criteria for
benchmark membership being left largely to the analyst’s discretion. Three
algorithms—SIA [5], COSIATEC [4] and my own, SIACT—were run on the same
pieces and their performance was evaluated in terms of recall and precision. If an
algorithm discovers x of the y patterns discovered by the analyst then its recall is x/y.
If the algorithm also returns z patterns that are not in the analyst’s benchmark then the
algorithm’s precision is x/(x + z). It was found that my algorithm, SIACT, out-
performs the existing algorithms with regard to recall and, more often than not,
precision.
My presentation will give the definition of a translational pattern, discuss the
improvements outlined above, and demonstrate how these improvements are being
brought together in a user interface.
SELECTED REFERENCES
1. Collins, T., R. Laney, A. Willis, and P.H. Garthwaite, ‘Using discovered,
polyphonic patterns to filter computer-generated music’, in Proceedings of the
International Conference on Computational Creativity, Lisbon (2010), 1-10.
2. Conklin, D., and M. Bergeron, ‘Feature set patterns in music’, in Computer Music
Journal 32(1) (2008), 60-70.
Page 10 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-17-320.jpg)








![2010 CRC PhD Student Conference
Verifying Authentication Properties of C Security
Protocol Code Using General Verifiers
Fran¸ois Dupressoir
c
Supervisors Andy Gordon (MSR)
Jan J¨rjens (TU Dortmund)
u
Bashar Nuseibeh (Open University)
Department Computing
Registration Full-Time
Probation Passed
1 Introduction
Directly verifying security protocol code could help prevent major security flaws
in communication systems. C is usually used when implementing security soft-
ware (e.g. OpenSSL, cryptlib, PolarSSL...) because it provides control over
side-channels, performance, and portability all at once, along with being easy
to call from a variety of other languages. But those strengths also make it hard
to reason about, especially when dealing with high-level logical properties such
as authentication.
Verifying high-level code. The most advanced results on verifying imple-
mentations of security protocols tackle high-level languages such as F#. Two
main verification trends can be identified on high-level languages. The first
one aims at soundly extracting models from the program code, and using a
cryptography-specific tool such as ProVerif (e.g. fs2pv [BFGT06]) to verify that
the extracted protocol model is secure with respect to a given attacker model.
The second approach, on the other hand, aims at using general verification tools
such as type systems and static analysis to verify security properties directly
on the program code. Using general verification tools permits a user with less
expert knowledge to verify a program, and also allows a more modular approach
to verification, even in the context of security, as argued in [BFG10].
Verifying C code. But very few widely-used security-oriented programs are
written in such high-level languages, and lower-level languages such as C are
usually favoured. Several approaches have been proposed for analysing C secu-
rity protocol code [GP05, ULF06, CD08], but we believe them unsatisfactory
for several reasons:
• memory-safety assumptions: all three rely on assuming memory-safety
1
Page 19 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-26-320.jpg)
![2010 CRC PhD Student Conference
properties,1
• trusted manual annotations: all three rely on a large amount of trusted
manual work,
• unsoundness: both [CD08] and [ULF06] make unsound abstractions and
simplifications, which is often not acceptable in a security-criticial context,
• scalability issues: [CD08] is limited to bounded, small in practice, numbers
of parallel sessions, and we believe [GP05] is limited to small programs due
to its whole-program analysis approach.
1.1 Goals
Our goal is to provide a new approach to soundly verify Dolev-Yao security
properties of real C code, with a minimal amount of unverified annotations and
assumptions, so that it is accessible to non-experts. We do not aim at verifying
implementations of encryption algorithms and other cryptographic operations,
but their correct usage in secure communication protocols such as TLS.
2 Framework
Previous approaches to verifying security properties of C programs did not de-
fine attacker models at the level of the programming language, since they were
based on extracting a more abstract model from the analysed C code (CSur and
Aspier), or simply verified compliance of the program to a separate specification
(as in Pistachio). However, to achieve our scalability goals, we choose to define
an attacker model on C programs, that enables a modular verification of the
code.
To avoid issues related to the complex, and often very informal semantics of the
C language, we use the F7 notion of a refined module (see [BFG10]). In F7,
a refined module consists of an imported and an exported interface, contain-
ing function declarations and predicate definitions, along with a piece of type-
checked F# code. The main result states that a refined module with empty
imported interface cannot go wrong, and careful use of assertions allows one
to statically verify correspondence properties of the code. Composition results
can also be used to combine existing refined modules whilst ensuring that their
security properties are preserved.
We define our attacker model on C programs by translating F7 interfaces into
annotated C header files. The F7 notion of an opponent, and the corresponding
security results, can then be transferred to C programs that implement an F7-
translated header. The type-checking phase in F7 is, in the case of C programs,
replaced by a verification phase, in our case using VCC. We trust that VCC is
sound, and claim that verifying that a given C program correctly implements
a given annotated C header entails that there exists an equivalent (in terms of
attacks within our attacker model) F7 implementation of that same interface.
1 Which may sometimes be purposefully broken as a source of randomness.
Page 20 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-27-320.jpg)
![2010 CRC PhD Student Conference
3 Case Study
We show how our approach can be used in practice to verify a simple implemen-
tation of an authenticated Remote Procedure Call protocol, that authenticates
the pair of communicating parties using a pre-shared key, and links requests
and responses together. We show that different styles of C code can be verified
using this approach, with varying levels of required annotations, very few of
which are trusted by the verifier. We argue that a large part of the required
annotations are memory-safety related and would be necessary to verify other
properties of the C code, including to verify the memory-safety assumptions
made by previous approaches.
4 Conclusion
We define an attacker model for C code by interpreting verified C programs as
F7 refined modules. We then describe a method to statically prove the impos-
sibility of attacks against C code in this attacker model using VCC [CDH+ 09],
a general C verifier. This approach does not rely on unverified memory-safety
assumptions, and the amount of trusted annotations is minimal. We also believe
it is as sound and scalable as the verifier that is used. Moreover, we believe our
approach can be adapted for use with any contract-based C verifier, and could
greatly benefit from the important recent developments in that area.
References
[BFG10] Karthikeyan Bhargavan, C´dric Fournet, and Andrew D. Gordon.
e
Modular verification of security protocol code by typing. In Proceed-
ings of the 37th annual ACM SIGPLAN-SIGACT symposium on
Principles of programming languages - POPL ’10, pages 445—456,
Madrid, Spain, 2010.
[BFGT06] Karthikeyan Bhargavan, C´dric Fournet, Andrew D. Gordon, and
e
Stephen Tse. Verified interoperable implementations of security pro-
tocols. In CSFW ’06: Proceedings of the 19th IEEE workshop on
Computer Security Foundations, pages 139—-152, Washington, DC,
USA, 2006. IEEE Computer Society.
[CD08] Sagar Chaki and Anupam Datta. ASPIER: an automated framework
for verifying security protocol implementations. Technical CMU-
CyLab-08-012, CyLab, Carnegie Mellon University, 2008.
[CDH+ 09] Ernie Cohen, Markus Dahlweid, Mark Hillebrand, Dirk Leinenbach,
Michal Moskal, Thomas Santen, Wolfram Schulte, and Stephan To-
bies. VCC: a practical system for verifying concurrent C. In Pro-
ceedings of the 22nd International Conference on Theorem Prov-
ing in Higher Order Logics, pages 23—42, Munich, Germany, 2009.
Springer-Verlag.
[GP05] Jean Goubault-Larrecq and Fabrice Parrennes. Cryptographic pro-
tocol analysis on real C code. In Proceedings of the 6th International
Page 21 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-28-320.jpg)
![2010 CRC PhD Student Conference
Conference on Verification, Model Checking and Abstract Interpre-
tation (VMCAI’05), volume 3385 of Lecture Notes in Computer Sci-
ence, page 363–379. Springer, 2005.
[ULF06] Octavian Udrea, Cristian Lumezanu, and Jeffrey S Foster. Rule-
Based static analysis of network protocol implementations. IN PRO-
CEEDINGS OF THE 15TH USENIX SECURITY SYMPOSIUM,
pages 193—208, 2006.
Page 22 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-29-320.jpg)

![2010 CRC PhD Student Conference
Scrum, with established design approaches, e.g., Usage-Centered Design [6], Usability Engineering
[5]. We also find examples of well-known HCI techniques such as personas [1] and scenarios [3] being
used on Agile projects.
3 A question of coordination
The second perspective on how to bring usability and Agile development together is one where it is
considered a problem of coordination. That is, the central concern is how to allow the designers and
developers to carry out their individual tasks, and bring them together at the appropriate points.
Designers require enough time at the outset of the project to perform user research and sketch out a
coherent design. To fit with the time-boxed Agile cycles, usability techniques are often adapted to fit
within shorter timescales. Advice is generally to have designers remain ahead of the developers, so that
they have enough time to design for what is coming ahead and evaluate what has already been
implemented. In the literature we find examples of process descriptions as a way of addressing this
coordination issue. They provide a way to mesh the activities of both designers and developers, by
specifying the tasks that need to be performed in a temporal sequence (e.g., [4]).
4 Work cultures of engagement
The third perspective addresses practical settings and has received little attention so far. In this
perspective, rather than concentrating on processes or rational plans that abstract away from the
circumstances of the actions, the situatedness of the work of the developers and designers is
emphasised. This perspective encompasses both of those discussed above, while acknowledging that
issues of coordination and focus are inextricably linked with the setting in which practitioners work.
That is, how the developers and designers coordinate their work and how focus is maintained, in
practice is shaped and sustained by their work setting.
With work culture I specifically mean the “set of solutions produced by a group of people to meet
specific problems posed by the situation that they face in common” [2, p.64], in a work setting. If
developers and designers are brought together by an organisation, they will be working together amid
values and assumptions about the best way to get the work done — the manifestations of a work
culture. I combine work cultures with engagement to bring the point across that how developers and
designers engage with one another depends in essential ways on the embedded values and assumptions
regarding their work and what is considered appropriate behaviour in their circumstances.
My research into practice has provided evidence for how practical settings shape developers and
designers engaging with one another. We find that developers and designers get the job done through
their localised, contingent and purposeful actions that are not explained by the perspectives above.
Further, the developers and designers can be embedded in the same work culture, such that they share
values, assumptions and behaviours for getting the work done. But we have also encountered examples
where developers and designers are in separate groups and embedded in distinct work cultures.
Engaging in this sense requires that individuals step outside their group boundaries and figure out how
to deal with each other on a daily basis — contending with very different values, assumptions and
behaviours compared to their own.
This is an important perspective to consider because of the implications for practice that it brings —
highlighting the role of work culture, self-organisation and purposeful work. It is also a significant
perspective, since we are unlikely to encounter teams in practice who are fully self-directed and
independent of other teams, individuals or organisational influences.
5 Concluding remarks
As we work through the problems that crossing disciplinary boundaries suggest, we simultaneously
need an awareness of which conception of the problem is actually being addressed. In this paper I have
identified a third perspective requiring attention, where we take account of the work settings in which
the combination of Agile development and usability is played out. According to this perspective, it
would be unrealistic to expect that one ideal approach would emerge and successfully translate to any
other work setting. Instead, it shifts attention to the work cultures involved in usability and Agile
development in practice. It shows how understanding and supporting the mechanisms of the work
cultures that achieve engagement in that setting, contribute to understanding and supporting the
mechanisms that enable usability in an agile domain.
References
1. Haikara, J.: Usability in Agile Software Development: Extending the Interaction Design
Process with Personas Approach . In: Concas, G., Damiani, E., Scotto, M., Succi, G. (eds.)
Page 24 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-31-320.jpg)





![2010 CRC PhD Student Conference
An Investigation Into Design Diagrams and Their
Implementations
Alan Hayes
alanhayes725@btinternet.com
Supervisors Dr Pete Thomas
Dr Neil Smith
Dr Kevin Waugh
Department/Institute Computing Department
Status Part-time
Probation viva After
Starting date 1st October 2005
The broad theme of this research is concerned with the application of information
technology tools and techniques to automatically generate formative feedback based
upon a comparison of two separate, but related, artefacts. An artefact is defined as a
mechanism through which a system is described. In the case of comparing two
artefacts, both artefacts describe the same system but do so through the adoption of
differing semantic and modelling constructs. For example, in the case of a student
coursework submission, one artefact would be that of a student-submitted design
diagram (using the syntax and semantics of UML class diagrams) and the second
artefact would be that of the student-submitted accompanying implementation (using
java syntax and semantics). Both artefacts represent the student’s solution to an
assignment brief set by the tutor. The design diagram describes the solution using one
set of semantic representations (UML class diagrams) whilst the implementation
represents the same solution using an alternative set (Java source code). Both artefacts
are describing the same system and represent a solution to the assignment brief. An
alternative example would be that of a student submitting an ERD diagram with an
accompanying SQL implementation.
This research aims to identify the generic mechanisms needed for a tool to be able to
compare two different, but related, artefacts and generate meaningful formative
feedback based upon this comparison. A case study is presented that applies these
components to the case of automatically generating formative assessment feedback to
the students based upon their submission. The specific area of formative feedback
being addresses is based upon a comparison between the submitted design and the
accompanying implementation. Constituent components described within each
artefact are considered to be consistent if, despite the differing modelling constructs,
they describe features that are common to both artefacts. The design (in diagrammatic
format) is viewed as prescribing the structure and function contained within the
implementation, whilst the implementation (source code) is viewed as implementing
the design whilst adhering to its specified structure and function. There are several
major challenges and themes that feed into this issue. The first is how the consistency
between a student-submitted design and its implementation can be measured in such a
way that meaningful formative feedback could be generated. This involves being able
to represent both components of the student submission in a form that facilitates their
comparison. Thomas et al [2005] and Smith et al [2004] describe a method of
reducing a student diagram into meaningful minimum components. Tselonis et al
Page 30 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-37-320.jpg)
![2010 CRC PhD Student Conference
[2005] adopt a graphical representation mapping entities to nodes and relationships to
arcs. Consequently, one component of this research addresses how the student
submitted design and its source code representation can be reduced to their constituent
meaningful components.
The second challenge associated with this research addresses the problem of how to
facilitate a meaningful comparison between these representations and how the output
of a comparison can be utilised to produce meaningful feedback. This challenge is
further complicated as it is known that the student submission will contain errors.
Smith et al [2004] and Thomas et al [2005] identified that the student diagrams will
contain data that is either missing or extraneous. Thomasson et al [2006] analysed the
designs of novice undergraduate computer programmers and identified a range of
typical errors found in the student design diagrams. Additionally, Bollojou et al
[2006] analysed UML modelling errors made by novice analysts and have identified a
range of typical semantic errors made. Some of these errors will propagate into the
student implementation whilst some will not.
This research investigates how such analysis and classifications can be used to
support the development of a framework that facilitates the automation of the
assessment process. This work will be complemented by an analysis of six data sets
collated for this research. Each data set is comprised of a set of student diagrams and
their accompanying implementations. It is anticipated that this work will be of interest
to academic staff engaged in the teaching, and consequently assessment, of
undergraduate computing programmes. It will also be of interest to academic staff
considering issues surrounding the prevention of plagiarism. Additionally, it will be
of interest to those engaged in the field of software engineering and in particular to
those involved in the auditing of documentation and practice.
References
[1] Higgins C., Colin A., Gray G., Symeonidis P. and Tsintsifas A. 2005 Automated
Assessment and Experiences of Teaching Programming. In Journal on
Educational Resources in Computing (JERIC) Volume 5 Issue 3, September 2005.
ACM Press
[2] Thomasson B., Ratcliffe M. and Thomas L., 2005 Identifying Novice Difficulties
in Object Oriented Design. In Proceedings of Information Technology in
Computer Science Education (ITiCSE ’06), June 2006, Bologna, Italy.
[3] Bolloju N. and Leung F. 2006 Assisting Novice Analysts in Developing Quality
Conceptual Models with UML. In Communications of the ACM June 2006, Vol
49, No. 7, pp 108-112
[4] Tselonis C., Sargeant J. and Wood M. 2005 Diagram Matching for Human-
Computer Collaborative Assessment. In Proceedings of the 9th International
conference on Computer Assisted Assessment, 2005.
Page 31 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-38-320.jpg)
![2010 CRC PhD Student Conference
[5] Smith N., Thomas, P. and Waugh K. (2004) Interpreting Imprecise Diagrams. In
Proceedings of the Third International Conference in Theory and Applications of
Diagrams. March 22-24, Cambridge, UK. Springer Lecture Notes in Computer
Science, eds: Alan Blackwell, Kim Marriott, Atsushi Shimomnja, 2980, 239-241.
ISBN 3-540-21268-X.
[6] Thomas P., Waugh K. and Smith N., (2005) Experiments in the Automated
Marking of ER-Diagrams. In Proceedings of 10th Annual Conference on
Innovation and Technology in Computer Science Education (ITiCSE 2005)
(Lisbon, Portugal, June 27-29, 2005).
Page 32 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-39-320.jpg)
![2010 CRC PhD Student Conference
An Investigation into Interoperability of Data Between
Software Packages used to Support the Design, Analysis and
Visualisation of Low Carbon Buildings
Robina Hetherington
R.E.Hetherington@open.ac.uk
Supervisors Robin Laney
Stephen Peake
Department/Institute Computing
Status Fulltime
Probation viva Before
Starting date January 2010
This paper outlines a preliminary study into the interoperability of building design and
energy analysis software packages. It will form part of a larger study into how
software can support the design of interesting and adventurous low carbon buildings.
The work is interdisciplinary and is concerned with design, climate change and
software engineering.
Research Methodology
The study will involve a blend of research methods. Firstly the key literature
surrounding the study will be critically reviewed. A case study will look at the
modelling of built form, with reflection upon the software and processes used. The
model used in the case study will then be used to enable the analysis of data
movement between software packages. Finally conclusions regarding the structures,
hierarchies and relationships between interoperable languages used in the process will
be drawn. This will inform the larger study into how software can support the design
of interesting and adventurous low carbon buildings.
Research questions:
1. What are the types of software used to generate building models and conduct
the analysis of energy performance?
2. What is the process involved in the movement of data from design software to
energy analysis software to enable the prediction of the energy demands of
new buildings?
3. What are the potential limitations of current interoperable languages used to
exchange data and visualise the built form?
Context
Software has an important role in tackling climate change, it is “a critical enabling
technology” [1]. Software tools can be used to support decision making surrounding
climate change in three ways; prediction of the medium to long term effects,
formation and analysis of adaptation strategies and support of mitigation methods.
This work falls into the later category, to reduce the sources of greenhouse gases
through energy efficiency and the use of renewable energy sources [2].
Climate change is believed to be caused by increased anthropogenic emissions of
green house gases. One of the major greenhouse gases is carbon dioxide. In the UK
Page 33 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-40-320.jpg)
![2010 CRC PhD Student Conference
the Climate Change Act of 2008 has set legally binding targets to reduce the emission
of carbon dioxide by 80% from 1990 levels by 2050 [3]. As buildings account for
almost 50% of UK carbon dioxide emissions the necessary alteration of practices
related to the construction and use of buildings will have a significant role in
achieving these targets [4]. In 2007 the UK Government announced the intention that
all new houses would be carbon neutral by 2016 in the “Building a Greener Future:
policy statement”. This is to be achieved by progressive tightening of Building
Regulations legislation over a number of years [4]. Consultations are currently taking
place on the practicalities of legislating for public sector buildings and all new non-
domestic buildings to be carbon neutral by 2018 and 2019 respectively [5]. The
changes in praxis in the next 20-30 years facing the construction industry caused by
this legislation are profound [6].
Software used in building modelling
Architecture has gone through significant changes since the 1980s when CAD
[Computer Aided Draughting/Design] was introduced. The use of software has
significantly altered working practices and enabled imaginative and inspiring designs,
sometimes using complex geometries only achievable through the use of advanced
modelling and engineering computational techniques. However, the advances in
digital design media have created a complex web of multiple types of software,
interfaces, scripting languages and complex data models [7].
The types of software used by architects can be grouped into three main categories:
CAD software that can be used to generate 2D or 3D visualizations of buildings. This
type of software evolved from engineering and draughting practices, using command
line techniques to input geometries. This software is mainly aimed at imitating paper
based practices, with designs printed to either paper or pdf.
Visualization software, generally used in the early design stages for generating high
quality renderings of the project.
BIM [Building Information Modelling] software has been a significant development
in the last few years. BIM software contains the building geometry and spatial
relationship of building elements in 3D. It can also hold geographic information,
quantities and properties of building components, with each component as an ‘object’
recorded in a backend database. Building models of this type are key to the
calculations now required to support zero carbon designs [8]. Examples of BIM
software are Revit by Autodesk[9], and ArchiCAD by Graphisoft[10] and Bentley
Systems [11]
Energy analysis software
Analysis software is used to perform calculations such as heat loss, solar gains,
lighting, acoustics, etc. This type of analysis is usually carried out by a specialist
engineer, often subsequent to the architectural design. The available tools are thus
aimed at the expert engineer who have explicit knowledge to run and interpret the
results of the simulation. This means that, until recent legislative changes, there was
no need for holistic performance assessment to be integrated into design software
[12].
Calculation of energy consumption requires a model of the proposed building to make
the detailed estimates possible. Examples of expert tools that use models for the
calculation are TRNSYS [13], IES Virtual Environment [14], EnergyPlus [15]. One
tool that supports the architectural design process is Ecotect [16], which has a more
intuitive graphical interface and support to conduct a performance analysis [12].
Page 34 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-41-320.jpg)
![2010 CRC PhD Student Conference
Energy analysis is one-way iterative process, with geometric meshes and data
transferred from the design package to the various analysis tools. Every design
iteration will (or should) involve a re-run of the environmental analysis tool [17]. The
mesh geometry requires manipulation for this movement into the analysis software
from the modelling environment and data such as material properties needs to be re-
entried, with a significant penalty in time and possible loss or corruption of data
[18][19].
Key research into interoperable languages used in the AEC [Architectural
Engineering and Construction] industry
A number of interoperable languages, relating to building designs, have been
developed since the release of version 1.0 of the XML [eXtensible Markup
Languages] standard in February 1998. They include visualisation schemas mainly
used for as the source for the display of models: X3D[eXtensible 3D], based on
VRML [Virtual Reality Modeling Language], CityGML for the representation of 3D
urban objects and COLLADA [COLLAborative Design Activity]. The ifcXML
[Industry Foundation Classes eXtensible Markup Language] specification, developed
by the IAI [Industrial Alliance for Interoperability], was designed to facilitate the
movement of information from and between BIM software. It was designed in a
“relational” manner, as a result of the BIM database concept. Accordingly there is
concern about the potential file size and complexity of the standard arising from the
XML format and the amount of data it can contain [20] [21]. Also, the seamless
interoperability it is intended to support has proved to be elusive. Take up has been
slow and incomplete with software companies not always supportive [22]. A
language designed specifically for interchange of data between design modelling
environments and energy analysis packages is gbXML [Green Building eXtensible
Markup Language]. In comparison with ifcXML it is considerably simpler and easier
to understand [23]. However, it limitations are evident in the geometric detail
contained in the file which inhibits the transfer back to the design package [17].
Next stage – a case study
This paper has set the case study in context and given the key research in the area of
interoperability in AEC projects. In the next stage a small house will be designed in
Revit and the environmental design analysed in Ecotect to gain experience in using the
tools and enable reflection on the software and procedures involved. ifcXML and
gbXML files will be exported and analysed.
Future work
The software used in this study are all developed by commercial organizations,
typically with an incremental, yearly update. New software, such as Ecotect, is often
brought in from an independent developer. However, open platforms are generally
considered to “promote innovation and diversity more effectively than proprietary
ones” [24]. In the field of climate change, given the profound threat to humanity, a
community approach is seen as potentially a better way forward [25]. Future work
will look at how building design software may evolve to meet the challenge of
designing interesting and beautiful low carbon buildings.
References
[1] S.M. Easterbrook, “First international workshop on software research and climate change,”
Proceeding of the 24th ACM SIGPLAN conference companion on Object oriented programming
systems languages and applications - OOPSLA '09, Orlando, Florida, USA: 2009, p. 1057.
[2] S. Peake and J. Smith, Climate change : from science to sustainability, Milton Keynes
Page 35 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-42-320.jpg)
![2010 CRC PhD Student Conference
[England]; Oxford: Open University; Oxford University Press, 2009.
[3] Great Britain, Climate Change Act of 2008, 2008.
[4] Department for Communities and Local Government, “Building a Greener Future: policy
statement,” Jul. 2007.
[5] Zero Carbon Hub, “Consultation on Zero Carbon Non-Domestic Buildings”
http://www.zerocarbonhub.org/events_details.aspx?event=3 [Accessed January 28, 2010].
[6] T. Oreszczyn and R. Lowe, “Challenges for energy and buildings research: objectives, methods
and funding mechanisms,” Building Research & Information, vol. 38, 2010, pp. 107-122.
[7] R. Oxman, “Digital architecture as a challenge for design pedagogy: theory, knowledge, models
and medium,” Design Studies, vol. 29, 2008, pp. 99-120.
[8] E. Krygiel and B. Nies, Green BIM : successful sustainable design with building information
modeling, Indianapolis Ind.: Wiley Pub., 2008.
[9] Autodesk, “Revit Architecture Building Information Modeling Software - Autodesk,” Revit
Architecture Building Information Modeling Software - Autodesk
http://usa.autodesk.com/adsk/servlet/pc/index?id=3781831&siteID=123112 [Accessed April 26,
2010].
[10] Graphisoft, “ArchiCAD 13 - Overview,” ArchiCAD 13 - Overview
http://www.graphisoft.com/products/archicad/ [Accessed April 26, 2010].
[11] Bentley, “Construction Software | Architectural Software | Building Information Modeling,”
Construction Software | Architectural Software | Building Information Modeling
http://www.bentley.com/en-US/Solutions/Buildings/ [Accessed April 26, 2010].
[12] A. Schlueter and F. Thesseling, “Building information model based energy/exergy performance
assessment in early design stages,” Automation in Construction, vol. 18, 2009, pp. 153-163.
[13] Transsolar Energietechnik GmbH, “TRANSSOLAR Software | TRNSYS Overview,”
TRANSSOLAR Software | TRNSYS Overview
http://www.transsolar.com/__software/docs/trnsys/trnsys_uebersicht_en.htm [Accessed April 26,
2010].
[14] IES, “IES - Sustainable 3D Building Design, Architecture Software - Integrated Environmental
Solutions,” IES - Sustainable 3D Building Design, Architecture Software - Integrated
Environmental Solutions http://www.iesve.com/content/default.asp?page= [Accessed April 26,
2010].
[15] U.S. Department of Energy, “Building Technologies Program: EnergyPlus,” Building
Technologies Program: EnergyPlus http://apps1.eere.energy.gov/buildings/energyplus/
[Accessed April 26, 2010].
[16] Autodesk, “Autodesk - Autodesk Ecotect Analysis,” Autodesk - Autodesk Ecotect Analysis
http://usa.autodesk.com/adsk/servlet/pc/index?siteID=123112&id=12602821 [Accessed April 26,
2010].
[17] N. Hamza and M. Horne, “Building Information Modelling: Empowering Energy Conscious
Design,” 3rd Int’l ASCAAD Conference on Em‘body’ing Virtual Architecture, Alexandria,
Egypt: .
[18] I. Pritchard and E. Willars, Climate Change Toolkit, 05 Low Carbon Design Tools, RIBA, 2007.
[19] A. Lawton and D. Driver, “Autodesk Sustainable Design Curriculum 2010 – Lesson 1,” 2010.
[20] V. Bazjanac, “Building energy performance simulation as part of interoperable software
environments,” Building and Environment, vol. 39, 2004, pp. 879-883.
[21] R. Howard and B. Bjork, “Building information modelling – Experts’ views on standardisation
and industry deployment,” Advanced Engineering Informatics, vol. 22, 2008, pp. 271-280.
[22] R. Jardim-Goncalves and A. Grilo, “Building information modeling and interoperability,”
Automation in Construction, 2009.
[23] B. Dong, K. Lam, Y. Huang, and G. Dobbs, “A comparative study of the IFC and gbXML
informational infrastructures for data
exchange in computational design support environments,” Tenth International IBPSA
Conference, Beijing: IBPSA China: 2007.
[24] S. Johnson, “Rethinking a Gospel of the Web,” The New York Times
http://www.nytimes.com/2010/04/11/technology/internet/11every.htm?pagewanted=print
[Accessed April 26, 2010].
[25] A.A. Voinov, C. DeLuca, R.R. Hood, S. Peckham, C.R. Sherwood, and J.P.M. Syvitski, “A
Community Approach to Earth Systems Modeling,” Eos, Transactions American Geophysical
Union, vol. 91, 2010, p. 117.
Page 36 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-43-320.jpg)
![2010 CRC PhD Student Conference
Understanding Object-Relational Impedance Mismatch: A
Framework Based Approach
Chris Ireland
cji26@student.open.ac.uk
Supervisors David Bowers
Mike Newton
Kevin Waugh
Department/Institute Computing
Status 5th Year, Part-time
Probation viva Completed
Starting date 1 October 2005
Research Question
Object-relational impedance mismatch is the label used to classify the problems faced by the developer
of an object-oriented application that must use a relational database for storage. What is object-
relational impedance mismatch, how do we know if a particular strategy is the most appropriate way to
address the problems it presents and what can be done to improve the situation?
Background
In [1] I describe a framework and classification (Figure 1) that provide new insights into the object-
relational mapping (ORM) strategies used to address problems of an object-relational impedance
mismatch.
Concept
Conceptual
Object Orientation Mismatch Relational
(Reconciliation)
Language
Representation
OOPL (e.g. Java) Mismatch SQL
(Pattern)
Schema
Emphasis
Application Mismatch DB Schema
(Mapping)
Behaviour
Instance
Insta
e
ur
nce
ct
Mis
(Tran match
ru
St
sform
ation
)
Object State Row
Figure 1 - My Conceptual Framework and Classification of Impedance Mismatch
What is not clear are how one uses my framework to understand an ORM strategy, where does one
start, how does one proceed, what can one expect to discover and how do we understand changes that
may improve the situation? Figure 2 provides an overview of one process for using my framework. I
Page 37 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-44-320.jpg)
![2010 CRC PhD Student Conference
describe this process in more detail in [5]. The process and framework have been validated by
comparing and contrasting the outcomes with those possible using the classification of Fussell [6].
Figure 2 - My Framework Based Approach
The framework may also be used to understand (possible) solutions to problems of an object-relational
impedance mismatch. At the last CRC PhD Student Conference I set an objective to understand the
consequences of changes introduced in Object-Relational SQL (OR-SQL) [7] using my framework.
OR-SQL is a language level change and may be one solution to problems of an object-relational
impedance mismatch. This work is complete and the results have been published in [8]. I found that
OR-SQL does not improve the situation and that the term relational database is now overloaded.
So what…
ORM strategies are not new. There is a body of literature (e.g. Keller [2], Ambler [3], Hohenstein [4])
that provide a description and analysis of each ORM strategy. This analysis is focused on the practical
consequences of combining object and relational artefacts rather than understanding the underlying
issues with an ORM strategy. Achieving an understanding of the underlying issues is the objective of
my framework and process. Analysis using my framework asks that one thinks about an ORM strategy
in a new way. In so doing it helps to provide new insights into an ORM strategy, highlight new issues,
understand cause and effect, and suggest improvements to an ORM strategy.
In [1] (this was awarded a best paper at the conference), [5] and [8] I have shown that the framework
and process do provide new insights. These insights provide an opportunity to improve an ORM
strategy and the context in which that ORM strategy operates, and to understand how best to make use
Page 38 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-45-320.jpg)
![2010 CRC PhD Student Conference
of new features in OR-SQL. Such information is useful to standards bodies, tools vendors and those
who define an ORM strategy using SQL or OR-SQL. Thinking about the consequences of an ORM
strategy provides information necessary to choose between alternatives. This information is invaluable
to those who implement an ORM strategy.
The Problem
The framework provides guidance on the use of my framework but there is still a need for clear
guidance on how to compare object and relational representations. What is the basis for a comparison
and how might we go about making a comparison?
Current Research Activities
I am exploring how we might explore the different kinds of impedance mismatch described in Figure
1. To that end I am developing a technique based on equivalence. Problems of an impedance mismatch
exist because object and relational representations are different, but how are they equivalent?
An object and a relational design reflect aspects of a universe of discourse ([9], p2-1). That universe of
discourse provides a point of reference common to both object and relational representations. Whilst
each design uses a different conceptual framework, language and structure(s) to describe that universe
they are representations of the same universe. So, whilst object and relational representations are
different, if we are not to lose information in a round-trip between an object-oriented application and a
relational database they must be equivalent descriptions of that universe. The problem is how do we
describe that universe without favouring one conceptual framework over another?
I introduce a third silo into the framework: the reference silo. The reference silo is currently theoretical
and artefacts within it an ideal. In this silo there is a reference concept level, a reference language level,
a reference schema level and a reference instance level. Each level provides artefacts for the description
of some aspect of a universe of discourse. This description does not need to be perfect, but as a
minimum it must be a superset of those semantics and structures that may be described using object
and relational artefacts.
Identity Entity Identity based
independent of on value of a
attributes tuple
Identity is
implicit Identity is
Object Identify a Relational explicit
Schema particular Schema
occurrence
Identity of an
object Identity of a
row
Figure 3 - Exploring Identity Between Object and Relational Representations of an Entity
Page 39 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-46-320.jpg)
![2010 CRC PhD Student Conference
Employing the reference silo I can then explore those semantics and structures of a reference
representation that are captured in an object and a relational representation. Each representation is
shown as a set in a Venn diagram (e.g. Figure 3) where, depending on the level of the framework, a
set may contain conceptual building blocks, language structures, design representations or data formats.
In Figure 3 I provide one example that shows that there is little in common between object and
relational representations of identity at the language level. My argument is that only those semantics
and structures that are equivalent i.e. they are captured in both representations, can form part of a no-
loss transformation between object and relational representations. It follows that current pattern
strategies to map identity between object and relational representations (e.g. Blaha [10], p420, Keller
[2], p21 and Fowler, in Ambler [11], p285), are at best misguided.
The work on equivalence will enhance my process (Figure 2) and provide a more robust approach to
exploring individual ORIM problems and ORM strategies. I expect that this will also open up new
avenues for research into the nature and development of the reference silo.
Remaining Work
I have provided a convincing and published body of evidence to support my claims for the framework.
The work on equivalence provides the final piece of work for my thesis and will open up new avenues
for future research. The work on equivalence necessary for my Thesis will be complete by the summer
of 2010. If time permits I would like to publish the work on equivalence before submitting my Thesis
in the summer of 2011.
References
1. Ireland, C., Bowers, D., Newton, M., Waugh, K.: A Classification of Object-Relational Impedance
Mismatch. In: Chen, Q., Cuzzocrea, A., Hara, T., Hunt, E., Popescu, M. (eds.): The First International
Conference on Advances in Databases, Knowledge and Data Applications, Vol. 1. IEEE Computer Society,
Cancun, Mexico (2009) p36-43
2. Keller, W.: Mapping Objects to Tables: A Pattern Language. In: Bushman, F., Riehle, D. (eds.): European
Conference on Pattern Languages of Programming Conference (EuroPLoP), Irsee, Germany (1997)
3. Ambler, S.: Mapping Objects to Relational Databases: O/R Mapping In Detail. (2006)
4. Hohenstein, U.: Bridging the Gap between C++ and Relational Databases. In: Cointe, P. (ed.): European
Conference on Object-Oriented Programming, Vol. Lecture Noted on Computer Science 1098. Springer-
Verlag, Berlin (1996) 398-420
5. Ireland, C., Bowers, D., Newton, M., Waugh, K.: Understanding Object-Relational Mapping: A Framework
Based Approach. International Journal On Advances in Software 2 (2009)
6. Fussell, M.L.: Foundations of Object Relational Mapping. Vol. 2007. ChiMu Corporation (1997)
7. Eisenberg, A., Melton, J.: SQL: 1999, formerly known as SQL3. SIGMOD Record 28 (1999) 119-126
8. Ireland, C., Bowers, D., Newton, M., Waugh, K.: Exploring the use of Mixed Abstractions in SQL:1999 - A
Framework Based Approach. In: Chen, Q., Cuzzocrea, A., Hara, T., Hunt, E., Popescu, M. (eds.): The
Second International Conference on Advances in Databases, Knowledge and Data Applications, Vol. 1.
IEEE Computer Society, Les Menuires, France (2010) TBA
9. Griethuysen, J.J.v. (ed.): Concepts and Terminology for the Conceptual Schema and the Information Base.
ISO, New York (1982)
10. Blaha, M.R., Premerlani, W.J., Rumbaugh, J.E.: Relational database design using an object-oriented
methodology. Communications of the ACM 31 (1988) 414-427
11. Ambler, S.W.: Agile Database Techniques - Effective Strategies for the Agile Software Developer. Wiley
(2003)
Page 40 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-47-320.jpg)
![2010 CRC PhD Student Conference
“Privacy-Shake”, a Haptic Interface for Managing Privacy
Settings in Mobile Location Sharing Applications.
Lukasz Jedrzejczyk
l.jedrzejczyk@open.ac.uk
Supervisors Arosha Bandara
Bashar Nuseibeh
Blaine Price
Department/Institute Computing Dept.
Status Fulltime
Probation viva After
Starting date June 2008
Abstract
I describe the “Privacy-Shake”, a novel interface for managing coarse grained privacy
settings. I built a prototype that enables users of Buddy Tracker, an example location
sharing application, to change their privacy preferences by shaking their phone. Users
can enable or disable location sharing and change the level of granularity of disclosed
location by shaking and sweeping their phone. In this poster I present and motivate
my work on Privacy-Shake and report on a lab-based evaluation of the interface with
16 participants.
1. INTRODUCTION
The proliferation of location sharing applications raises several concerns related to
personal privacy. Some solutions involving location privacy policies have been
suggested (e.g., [1]). However, prior research shows that end-users have difficulties in
expressing and setting their privacy preferences [2,3]. Setting privacy rules is a time-
consuming process, which many people are unwilling to do until their privacy is
violated. Moreover, privacy preferences vary across the context, and it is hard to
define privacy policy that reflects the dynamic nature of our lives. I see this as a
strong motivation to design interfaces that help users update their privacy settings as a
consequence of their daily tasks within the system. The underlying requirement of my
interface is to provide an efficient, heads-up interface for managing location privacy
that does not overwhelm the configuration over action [4].
In order to fulfil this requirement I developed the Privacy-Shake, a haptic interface [5]
supporting ad-hoc privacy management. To evaluate the Privacy-Shake interface I
conducted a lab-based study to examine its effectiveness and explore users‟ reactions
to that technology. I also evaluated several usability aspects of Privacy-Shake and
compared its performance against graphical user interface. My study confirmed the
potential of haptic interfaces for performing simple privacy tasks and showed that
Privacy-Shake can be faster than the GUI. However, my subjective results suggest
further work on improving the interface, such as support for individual calibration and
personalized gestures for better efficiency.
Page 41 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-48-320.jpg)

![2010 CRC PhD Student Conference
58% of all attempts were successful. I observed that females performed slightly better
at using Privacy-Shake with 64% efficiency versus 53% for males.
4. CONCLUSIONS AND FUTURE WORK
I presented the concept and initial results of the evaluation of Privacy-Shake, a novel
interface for „heads-up‟ privacy management. The chosen demographic was not broad,
but the study helped me identify both social and technical issues related to the
interface. One of the main issues I found were lack of individual calibration and
support for more discreet movements, which highlights the future research agenda for
my work on Privacy-Shake. Though the actual efficiency is not ideal, the comparison
between the mean time of performing tasks T2 (6 seconds) and T4 (18 seconds)
shows that haptic interface can be successfully used to perform some basic privacy
management tasks faster than the traditional GUI. The Privacy-Shake concept
received a positive feedback, which encourages me to continue the work on
improving the interface and enhancing the user experience. Further work is also
needed to extend the functionality of Privacy-Shake by implementing new gestures
for managing group settings or expressing more fine-grained preferences.
5. REFERENCES
[1] G. Myles, A. Friday, and N. Davies, “Preserving Privacy in Environments
with Location-Based Applications,” IEEE Pervasive Computing, vol. 2, 2003, pp. 56-
64.
[2] L.F. Cranor and S. Garfinkel, Security and usability: designing secure systems
that people can use, O'Reilly Media, Inc., 2005.
[3] N. Sadeh, J. Hong, L. Cranor, I. Fette, P. Kelley, M. Prabaker, and J. Rao,
“Understanding and capturing people‟s privacy policies in a people finder
application,” The Journal of Personal and Ubiquitous Computing, vol. 13, Aug. 2009,
pp. 401-412.
[4] S. Lederer, I. Hong, K. Dey, and A. Landay, “Personal privacy through
understanding and action: five pitfalls for designers,” Personal Ubiquitous Computing,
vol. 8, 2004, pp. 440-454.
[5] S. Robinson, P. Eslambolchilar, and M. Jones, “Sweep-Shake: finding digital
resources in physical environments,” Proc. of Mobile HCI'09, ACM, 2009, p.12.
Page 44 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-51-320.jpg)
![2010 CRC PhD Student Conference
Designing a Climate Change Game for Interactive Tabletops
Stefan Kreitmayer
stefan@kreitmayer.com
Supervisors Dr. Robin Laney
Department/Institute Computing
Status Visiting Research Student
Probation viva n.a.
Starting date February – June 2010
During my 4 months visiting studentship I am developing a game that utilises the
affordances of multi-user interaction with tabletop surfaces for a persuasive goal.
Players' beliefs about some of the risks of man-made global climate destabilisation
should be influenced in a way that supports more responsible behaviour.
Persuasive games for personal computers are widespread in practice[1][2], and there
is abundant literature suggesting theoretical frameworks and design guidelines[3].
Similarly, designing applications for interactive tabletops is an active field of
research. However, there are currently not many persuasive games for interactive
tabletops, and emerging design issues have not been fully addressed in the literature.
With a growing awareness of the persuasive potential of computer games, and
interactive tabletops becoming increasingly affordable, it is to be expected that more
game designers will address this medium in the near future. Beyond usability
questions, designers will face questions resulting from contradicting paradigms.
While the affordances of tabletops to support multi-user collaboration are
permanently highlighted[4], the computer game area is only just emerging out of a
long tradition of single-user and competitive gameplay[5]. Currently the vast majority
of persuasive games are designed for browsers and mobile phones, aimed at single
users. Fogg[6] explains fundamental differences in the way persuasion works in single
user interaction as opposed to group interaction, and this can be incorporated into
design for tabletops.
This research aims to contribute towards understanding some of the apparent points of
friction between two media and two areas of research. With this in mind, my research
question can be summarised as follows:
Do players perceive a game's moral message differently depending on whether they
engage in collaborative, cooperative, or competitive gameplay?
As the single message of the game, I chose out of the vast climate change discourse a
fact which is commonly accepted to be true, can be easily conveyed to a broad
audience in a small amount of time, but at the same time is not over-advertised in the
media. The message is as follows: Architectural designs with most of the window area
facing the sun help to save heating energy, thereby supporting CO2 mitigation and
lowering the risk of climate change effects.
Page 45 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-52-320.jpg)
![2010 CRC PhD Student Conference
I am planning to develop three versions of the tabletop game which all share the same
interface, aesthetic, mechanics, and message. Differences should focus on the
supported gameplay: collaborative, cooperative, or competitive respectively. Here we
define the three concepts according to [5]: Collaborative gameplay implies that goals,
rewards, and penalties are shared among players. Cooperative gameplay differs in that
each player eventually wants to reach their individual goal and reward, but they may
occasionally choose to collaborate, if the collaboration supports their individual goal.
Competitive gameplay means that “the goals of the players are diametrically opposed”
[5]. For the sake of simplicity all three versions of the game are designed for two
players.
A quantitative user study will be conducted to assess the different impacts on players'
opinions, depending on which version of the game they have played.
Experiments could take place in a public space or in the laboratory. I am planning an
experiment with 30 pairs of players, divided into 3 balanced groups, each group
engaging with a different type of gameplay: 10 pairs play the collaborative game, 10
pairs play the cooperative game, and 10 pairs play the competitive game. Before and
after playing, players should answer questionnaires similar in content to those in the
American Climate Values Survey[7]. Using a Likert scale, results can be analysed
quantitatively. For more qualitative results, a second experiment could be done with
the same participants at the same place and time. After a pair has played their game
and completed the questionnaires, they are invited to play the other games as well and
give statements about their impressions of whether and how their opinions have
changed in relation to different types of gameplay.
References:
[1] http://persuasivegames.com/
[2] http://www.valuesatplay.org/
[3] I. Bogost. Persuasive Games: The Expressive Power of Videogames. MIT Press,
2007
[4] E. Hornecker, P. Marshall, N. Dalton, Y. Rogers. Collaboration and interference:
Awareness with mice or touch input. In: Proceedings of the ACM 2008 conference on
Computer supported cooperative work, 8-12 Nov 2008, San Diego, CA, USA.
[5] J. P. Zagal, J. Rick, I. Hsi. Collaborative games: Lessons learned from board
games. SIMULATION & GAMING, Vol. 37 No. 1, March 2006 24-40. Sage
Publications
[6] B. J. Fogg. Persuasive Technology: Using Computers to Change What We Think
and Do. Morgan Kaufmann, 2003
[7] ECOAMERICA.NET. The American Climate Values Survey.
Available at http://www.ecoamerica.org/docs/ecoAmerica_ACVS_Summary.pdf
Last Accessed 26 Mar 2010.
Page 46 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-53-320.jpg)
![2010 CRC PhD Student Conference
REASONING ABOUT FLAWS IN SOFTWARE DESIGN:
DIAGNOSIS AND RECOVERY
TAMARA LOPEZ
T.LOPEZ@OPEN.AC.UK
Supervisors Marian Petre, Charles Haley and Bashar Nuseibeh
Department Computing
Status Full-time
Probation Viva Before
Starting Date February 2010
Since its diagnosis at the 1960’s NATO conferences as one of the key problems in
computing[1, 2], the provision of reliable software has been a core theme in software
engineering research. One strand of this research analyzes software that fails, while
a second develops and tests techniques for ensuring software success.
Despite these efforts, the threat of failure and the quest for a multivalent yet com-
prehensive ”sense” of quality[2] remain powerful drivers for research and provoca-
tive tropes in anecdotal accounts of computing[3]. However, current analytical
approaches tend to result in overly broad accounts of why software fails or in
overly narrow views about what is required to make software succeed. This sug-
gests a need for a different approach toward the study of failure that can address
the complexities of large scale ”systems-of-systems”[4, 5], while accounting for the
effects and trajectories of specific choices made within software initiatives.
To address this gap, this research asks: How does failure manifest in actual soft-
ware development practice? What constitutes a flaw, and what are the conditions
surrounding its occurrence and correction? What can adopting a situational ori-
entation tell us more generally about why some software fails and other software
succeeds?
Background
Within computing literature, failure analysis typically takes two perspectives:
Page 47 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-54-320.jpg)
![2010 CRC PhD Student Conference
• Systemic analyses identify weak elements in complex organizational,
operational and software systems. Within these systems, individual or
multiple faults become active at a moment in time or within a clearly
bounded interval of time, and result in catastrophic or spectacular op-
erational failure[6, 7]. Alternatively, software deemed ”good enough” is
released into production with significant problems that require costly main-
tenance, redesign and redevelopment[8, 5].
• Means analyses treat smaller aspects or attributes of software engi-
neering as they contribute to the goal of creating dependable software[4].
These studies develop new or test existing techniques to strengthen all
stages of development such as requirements engineering[9], architectural
structuring[10], testing and maintenance [11] and verification and validation[12].
Systemic analyses produce case studies and often do not conclude with specific,
precise reasons for failure. Instead they retrospectively identify the system or sub-
system that failed, and provide general recommendations for improvement going
forward. Even when they do isolate weaknesses in the processes of software creation
or in particular software components, they do not produce general frameworks or
models that can be extended to improve software engineering practice.
Means analyses employ a range of methods including statistical, program analy-
sis, case study development, formal mathematical modeling and systems analysis.
Frequently, they examine a single part of the development process, with a corre-
sponding focus on achieving a single dependability mean[4]. The studies are often
experimental, applying a set of controlled techniques to existing bodies of soft-
ware in an effort to prove, verify and validate that software meets a quantifiable,
pre-determined degree of ”correctness”.
Methodology
This research will produce an analysis of the phenomenon of failure that lies some-
where between the broad, behavioral parameters of systemic analyses and the
narrowly focused goals of means analyses. To do this, it will draw upon recent
software engineering research that combines the socially oriented qualitative ap-
proaches of computer supported cooperative work(CSCW) with existing software
Page 48 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-55-320.jpg)
![2010 CRC PhD Student Conference
analysis techniques to provide new understandings of longstanding problems in
software engineering. In one such group of studies, de Souza and collaborators
have expanded the notion of dependency beyond its technical emphasis on the
ways in which software components rely on one another, demonstrating that hu-
man and organizational factors are also coupled to and expressed within software
source code[14, 15]. In a study published in 2009, Aranda and Venolia made a case
for developing rich bug histories using qualitative analyses in order to reveal the
complex interdependencies of social, organizational and technical knowledge that
influence and inform software maintenance[16].
In the manner of this and other cooperative and human aspects of software en-
gineering(CHASE) work, the research described here will apply a combination of
analytic and qualitative methods to examine the role of failure in the software
development process as it unfolds. Studies will be designed to allow for analysis
and examination of flaws within a heterogeneous artifact universe, with particu-
lar emphasis given to the interconnections between technical workers and artifacts.
Ethnographically informed techniques will be used to deepen understanding about
how the selected environments operate, and about how notions of failure and re-
covery operate within the development processes under investigation.
References
[1] P. Naur and B. Randell, “Software engineering: Report on a conference sponsored by the
NATO Science Committee Garmisch, Germany, 7th to 11th October 1968,” NATO Science
Committee, Scientific Affairs Division NATO Brussels 39 Belgium, Tech. Rep., January
1969. [Online]. Available: http://homepages.cs.ncl.ac.uk/brian.randell/NATO/
[2] J. Buxton and B. Randell, “Software engineering techniques: Report on a conference
sponsored by the NATO Science Committee Rome, Italy, 27th to 31st October 1969,” NATO
Science Committee, Scientific Affairs Division NATO Brussels 39 Belgium, Tech. Rep.,
April 1970 1970. [Online]. Available: http://homepages.cs.ncl.ac.uk/brian.randell/NATO/
[3] R. Charette, “Why software fails,” IEEE Spectrum, vol. 42, no. 9, pp. 42–49, 2005.
[4] B. Randell, “Dependability-A unifying concept,” in Proceedings of the Conference on Com-
puter Security, Dependability, and Assurance: From Needs to Solutions. IEEE Computer
Society Washington, DC, USA, 1998.
[5] ——, “A computer scientist’s reactions to NPfIT,” Journal of Information Technology,
vol. 22, no. 3, pp. 222–234, 2007.
Page 49 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-56-320.jpg)
![2010 CRC PhD Student Conference
[6] N. G. Leveson and C. S. Turner, “Investigation of the Therac-25 accidents,” IEEE Computer,
vol. 26, no. 7, pp. 18–41, 1993.
[7] B. Nuseibeh, “Ariane 5: Who dunnit?” IEEE Software, vol. 14, pp. 15–16, 1997.
[8] D. Ince, “Victoria Climbie, Baby P and the technological shackling of British childrens social
work,” Open University, Tech. Rep. 2010/01, 2010.
[9] T. Thein Than, M. Jackson, R. Laney, B. Nuseibeh, and Y. Yu, “Are your lights off? Using
problem frames to diagnose system failures,” Requirements Engineering, IEEE International
Conference on, vol. 0, pp. v–ix, 2009.
[10] H. S¨zer, B. Tekinerdoˇan, and M. Ak¸it, “FLORA: A framework for decomposing software
o g s
architecture to introduce local recovery,” Software: Practice and Experience, vol. 39, no. 10,
pp. 869–889, 2009. [Online]. Available: http://dx.doi.org/10.1002/spe.916
[11] F.-Z. Zou, “A change-point perspective on the software failure process,” Software
Testing, Verification and Reliability, vol. 13, no. 2, pp. 85–93, 2003. [Online]. Available:
http://dx.doi.org/10.1002/stvr.268
[12] A. Bertolino and L. Strigini, “Assessing the risk due to software faults: Estimates of
failure rate versus evidence of perfection,” Software Testing, Verification and Reliability,
vol. 8, no. 3, pp. 155–166, 1998. [Online]. Available: http://dx.doi.org/10.1002/(SICI)1099-
1689(1998090)8:3¡155::AID-STVR163¿3.0.CO;2-B
[13] Y. Dittrich, D. W. Randall, and J. Singer, “Software engineering as cooperative work,”
Computer Supported Cooperative Work, vol. 18, no. 5-6, pp. 393–399, 2009.
[14] C. R. B. de Souza, D. Redmiles, L.-T. Cheng, D. Millen, and J. Patterson, “Sometimes
you need to see through walls: A field study of application programming interfaces,” in
CSCW ’04: Proceedings of the 2004 ACM conference on Computer supported cooperative
work. New York, NY, USA: ACM, 2004, pp. 63–71.
[15] C. de Souza, J. Froehlich, and P. Dourish, “Seeking the source: Software source code as a
social and technical artifact,” in GROUP ’05: Proceedings of the 2005 international ACM
SIGGROUP conference on Supporting group work. New York, NY, USA: ACM, 2005, pp.
197–206.
[16] J. Aranda and G. Venolia, “The secret life of bugs: Going past the errors and omissions in
software repositories,” in Proceedings of the 2009 IEEE 31st International Conference on
Software Engineering. IEEE Computer Society, 2009, pp. 298–308.
Page 50 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-57-320.jpg)
![2010 CRC PhD Student Conference
Presupposition Analysis in Requirements
Lin Ma
l.ma@open.ac.uk
Supervisors Prof. Bashar Nuseibeh
Prof. Anne De Roeck
Dr. Paul Piwek
Dr. Alistair Willis
Department/Institute Department of Computing
Status Fulltime
Probation viva After
Starting date 1-Feb-2009
Motivation
Natural language is the most commonly used representation language in requirements
engineering [1]. However, compared with formal logics, natural language is
inherently ambiguous and lacks a formal semantics [2]. Communicating requirements
perfectly through natural language is thus not easy. Examining the linguistic
phenomena in natural language requirements can help with decoding what a person
means in communication. This method was originally used in psychotherapy and then
adopted in requirements engineering [3]. Presupposition is one of these linguistic
phenomena. It simplifies communication by pointing to references to bits of
knowledge that are taken for granted by the document writer. In requirements
engineering, however, we must know exactly what information we’ve lost by
simplification, or we run the risk of a misunderstanding. For instance, the requirement
(1) Accessibility in the experimental hall is required for changing the piggy board
where the device will be mounted.
commits the reader to the presuppositions that there is an experimental hall, there is a
piggy board and there is a device. These types of implicit commitments might be
misinterpreted or overlooked due to different background knowledge in the other
stakeholder’s domain. More precisely, for instance, concerning the presupposition that
there is a piggy board in example (1), the reader of this requirement may know a
piggy board A and choose to believe A is the thing that the document writer is writing
about. However, the document writer may mean piggy board B or just any new piggy
board. In this research, we propose to use natural language processing techniques for
automatically detecting such implicit commitments in requirements documents, and
identifying which of those are not made explicit.
Background
Presuppositions are triggered by certain types of syntactic structures – presupposition
triggers [4]. Therefore, presuppositions can be found by identifying the triggers in the
Page 51 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-58-320.jpg)
![2010 CRC PhD Student Conference
text. The presupposition trigger types can be divided into two general classes –
definite descriptions (noun phrases starting with determiners such as the piggy board
in example (1)) and other trigger types (for example, cleft - It + be + noun +
subordinate clause, stressed constituents - words in italic in texts). Definite
descriptions differ from other trigger types because they occur very frequently in all
styles of natural language [5], are easy to retrieve (because of their distinct structure
with the determiner the) and they often have possible referential relations with earlier
text [6]. We hence focus on presuppositions triggered by definite descriptions in this
research.
One major problem in the study of presupposition is presupposition projection. An
elementary presupposition is a presupposition of part of an utterance. Presupposition
projection, as the name suggests, is the study of whether an elementary presupposition
is a presupposition of the whole utterance (termed as actual presupposition). Here two
examples are given for distinct scenarios in requirements, one where an elementary
presupposition projects out and one where it does not:
(2) a. If funds are inadequate, the system will notify….
b. If there is a system, the system will notify…
Intuitively, when a reader accepts utterance (2b), he/she does not take the
presupposition that there is a system for granted. The elementary presupposition that
there is a system in the consequent of the conditional somehow does not project. The
same elementary presupposition that there is a system nevertheless projects out in
example (2a), which signals to the reader that the document writer takes for granted
that there is a system.
Methodology
The Binding Theory [7] of presupposition is a widely accepted formal framework for
modelling presupposition, in which presupposition is viewed as anaphora (anaphora
are expressions, such as a pronoun, which depends for its interpretation on a
preceding expression, i.e., an antecedent). Presupposition projection is treated as
looking for a path to an earlier part of the discourse which hosts an antecedent that
can bind the presupposition. Whenever an antecedent is found in the discourse, the
presupposition is bound, and thus does not project out. Therefore, according to the
Binding Theory, the actual presuppositions in a discourse are those which do not have
any antecedent existing earlier in the discourse. We adopt this view as the theoretical
ground.
[8] presents an automated approach for classifying definite descriptions. This
approach is compatible with the Binding Theory. It classifies definite descriptions as:
Discourse new: those that are independent from previous discourse elements for
the description interpretation (according to the Binding Theory, discourse new
definite descriptions introduce actual presuppositions with respect to a discourse,
because they do not have any antecedent);
Page 52 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-59-320.jpg)
![2010 CRC PhD Student Conference
Anaphoric: those that have co-referential 1 (co-reference is defined as multiple
expressions in a sentence or document have the same referent) antecedents in the
previous discourse;
Bridging [9]: those that either (i) have an antecedent denoting the same discourse
entity, but using a different head noun (e.g. a house . . . the building), or (ii) are
related by a relation other than identity to an entity already introduced in the
discourse (e.g. the partial relation between memory…the buffer).
Given example (3), “the experimental hall” has an antecedent in the previous sentence
– “an experiment hall”, so it will be classified as anaphoric. If we somehow have the
knowledge that a piggy board is a small circuit board mounted on a larger board, “the
piggy board” is a bridging definite description referring to part of “PAD boards”.
Finally, “the device” is a discourse new definite description which triggers the actual
presupposition that there is a device with respect to the discourse.
(3) An experimental hall shall be built….
PAD boards shall be used….
Accessibility in the experimental hall is required for changing the piggy board
where the device will be mounted.
In [8], the authors used a set of heuristics based on an empirical study of definite
descriptions [6] for performing the classification task. The heuristics include, for
example:
For discourse new definite descriptions: one of the heuristics is to examine a list
of special predicates (e.g. fact). If the head noun of the definite description
appears in the list, it is classified as discourse new.
For anaphoric definite descriptions: matching the head noun and modifiers with
earlier noun phrases. If there is a matching, it is classified as anaphoric. For
example, An experimental hall…the experimental hall.
For bridging: one of the heuristics is to use WordNet [10] for identifying relations
between head nouns with earlier noun phrases. If there is a relation, such as a
part-of relation, it is classified as bridging. For example, PAD boards…the piggy
board.
However, as stated by the authors of [8], this approach is insufficient to deal with
complex definite descriptions with modifiers and lacks a good knowledge base to
resolve the bridging definite descriptions (WordNet performed really poor in this
case). In my research, we will further develop this approach and implement a software
system that is able to analyze the projection behavior of presuppositions triggered by
definite descriptions in requirements documents. The development focus is on
analyzing modifiers of definite descriptions and making use of external knowledge
sources (such as ontologies built upon Wikipedia [11]) for resolving bridging definite
descriptions. Especially for bridging definite descriptions, if the relation can be
1
In a strict sense, the concept of anaphora is different from co-reference because the former requires
the meaning of its antecedents to interpret, but the latter do not. Here they are used as synonymies as
multiple expressions in a sentence or document have the same referent.
Page 53 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-60-320.jpg)
![2010 CRC PhD Student Conference
identified in the knowledge base, it will help with making a choice between creating a
new discourse entity or picking up an existing antecedent. As a result, the actual
presuppositions (the discourse new definite descriptions) can be identified. The
system will be evaluated through existing corpora with annotated noun phrases, such
as the GNOME corpus [12]. We will also manually annotate several requirements
documents and perform the evaluation on the annotation results.
References
[1] L. Mich and R. Garigliano, “NL-OOPS: A requirements analysis tool based on
natural language processing,” Proceedings of the 3rd International Conference
on Data Mining Methods and Databases for Engineering,, Bologna, Italy: 2002.
[2] V. Gervasi and D. Zowghi, “Reasoning about inconsistencies in natural language
requirements,” ACM Transactions on Software Engineering and Methodology
(TOSEM), vol. 14, 2005, pp. 277–330.
[3] R. Goetz and C. Rupp, “Psychotherapy for system requirements,” Cognitive
Informatics, 2003. Proceedings. The Second IEEE International Conference on,
2003, pp. 75–80.
[4] S.C. Levinson, Pragmatics, Cambridge, UK: Cambridge University Press, 2000.
[5] J. Spenader, “Presuppositions in Spoken Discourse,” Phd. Thesis, Department of
Linguistics Stockholm University, 2002.
[6] M. Poesio and R. Vieira, “A corpus-based investigation of definite description
use,” Computational Linguistics, vol. 24, 1998, pp. 183–216.
[7] R.A. Van der Sandt and B. Geurts, “Presupposition, anaphora, and lexical
content,” Text Understanding in LILOG, O. Herzog and C. Rollinger, Eds.,
Springer, 1991, pp. 259-296.
[8] R. Vieira and M. Poesio, “An empirically based system for processing definite
descriptions,” Computational Linguistics, vol. 26, 2000, pp. 539–593.
[9] H.H. Clark, “Bridging,” Thinking, 1977, pp. 411–420.
[10] C. Fellbaum, WordNet: An Electronic Lexical Database, Cambridge, MA: MIT
press, 1998.
[11] M.C. Müller, M. Mieskes, and M. Strube, “Knowledge Sources for Bridging
Resolution in Multi-Party Dialog,” Proceedings of the 6th International
Conference on Language Resources and Evaluation, Marrakech, Morocco:
2008.
[12] M. Poesio, “Annotating a corpus to develop and evaluate discourse entity
realization algorithms: issues and preliminary results,” Proc. of the 2nd LREC,
2000, pp. 211–218.
Page 54 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-61-320.jpg)
![2010 CRC PhD Student Conference
Merging Verifiable and Evolving Access Control Properties
Lionel Montrieux
L.M.C.Montrieux@open.ac.uk
Supervisors Dr Charles B. Haley, C.B.Haley@open.ac.uk
Dr Yijun Yu, Y.Yu@open.ac.uk
Department Computing
Status Full-time
Probation viva not passed
Starting date October 2009
1 Introduction
Recent years have seen a strong advance in formal methods for security [J¨r05]. Many success
u
have been obtained: many security protocols have been proved to be flawed, and many others to
be correct in a precise sense delimiting exactly their applicability.
UMLsec is an extension of UML that allows developers to waive security aspects into a standard
UML model. The UMLsec tool [J¨r04] allows them to check that their models satisfy the security
u
properties they want to enforce.
Yet, the growing demand to evolve systems continuously raises new questions and new research
opportunities. Not only is it necessary to make sure that a system meets security requirements,
but it is also crucial to make sure that those requirements are still met by the system on each
step of its constant evolution. Hence, it is necessary to develop processes and tools that help the
developers ensuring lifelong compliance to security, privacy or dependability requirements.
Specifically, access control plays an important role in protecting assets from unauthorised access.
Several access control models, like Role-Based Access Control (RBAC) [SFK00] or Organization-
Based Access Control (OrBAC) [ABB+ 03] have been defined to help administrators grant permis-
sions to users in an easy and scalable way, while allowing permission changes to be easily made.
With complex software, maintaining a sound access control infrastructure and ensuring properties
like separation of duty can become a challenge. Processes and tools that can verify such properties
against a given model as well as all of its evolutions are necessary to increase confidence in one’s
access control infrastructure.
2 Verification of Access Control properties in UMLsec
The verification process we propose is made of three different parts: first, we want to extend
the existing RBAC specification in UMLsec to allow one to specify more complex access control
properties. Then, we want to verify that a given model actually enforces the UMLsec access
control specification. Finally, we generate code that conforms to the access control property that
has previously been defined and verified.
Page 55 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-62-320.jpg)
![2010 CRC PhD Student Conference
2.1 Extending the UMLsec specification of RBAC
UMLsec includes a set of properties to specify RBAC permissions, using the RBAC stereotype on
an Activity diagram [J¨r05]. However, it supports only a limited subset of the RBAC standard.
u
We want to develop it to include other levels of RBAC standard compliance, as well as other
similar access control models, like OrBAC. We also want to model authentication procedures using
UMLsec, and to allow one to automatically integrate the UMLsec property into other diagrams,
like class diagrams and sequence diagrams, once the initial property has been defined on one or
several activity diagrams.
Other approaches have been proposed to model RBAC permissions on UML models, like Se-
cureUML [LBD02]. SecureUML differs from UMLsec as it focuses on RBAC only. The way RBAC
properties are represented is also different: instead of using stereotypes and tagged values to an-
notate the model, the SecureUML approach adds classes to a class diagram to describe users,
roles and permissions, and uses OCL [OMG10] to describe additional constraints. access control
directives, like EJB configuration files, can also be generated from a SecureUML model.
2.2 Verifying a UMLsec property
Once the UMLsec property has been defined, we want to make sure that the model actually
enforces it. Not only do we want to make sure that the model doesn’t allow a user to perform
an operation s/he’s not authorised to perform, but we also want to make sure that rules like
Separation of Duty are actually enforced. Verification of the enforcement of the access control
definition by the model already exists for the current UMLsec RBAC property, but is limited to
activity diagrams. With the extended access control model that we propose come new challenges
to verify the suitability of the model. Not only will we have to verify new properties on the activity
diagram, but we will also have to verify the other diagrams of the model that may contain access
control rules: class diagrams, sequence diagrams, . . .
Since the access control definition might be spread over several diagrams, we will also have to
verify that it doesn’t contain any contradiction.
2.3 Code generation from a UMLsec specification
Once access control permissions have been defined for a model using UMLsec, we want to
generate code that actually enforces those. We compared two different code generation approaches
from the existing RBAC UMLsec property. The first one produces Object-Oriented code, while the
second one produces Aspect-Oriented code [IKL+ 97] to enforce the access control permissions,
together with Object-Oriented code for the functional code. It seems that the second solution
provides a better implementation, since the access control enforcement code is clearly separated
from the functional code. It also makes further changes to the code easier to perform, and makes
the traceability between the code and the UMLsec access control property easier to maintain.
Moreover, the current implementation only generates code for the JAAS framework [jaa01]. We
would like to offer the possibility to generate code for other frameworks as well.
3 Merging conflicting access control properties
An interesting case of evolution of a software system is merging conflicting access control prop-
erties. A example might be two companies merging, each running its own software with its own
access control properties. Rationalising the new company’s information system will imply using
only one system, with only one access control property.
We want to propose a framework, based on UMLsec, to allow one to merge several access control
properties on a given model. Conflicting definition of roles are likely to arise, as well as conflicting
Page 56 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-63-320.jpg)
![2010 CRC PhD Student Conference
Figure 1: Merging access control properties
constraints and assignations. We want to give developers the opportunity to identify possible
conflicts.
Assuming that we have two different access control properties defined using UMLsec on the
same model. If we can verify that the model enforces both definitions individually, then we want
to merge those two definitions, raise possible conflicts to the user, and, once those conflicts have
been resolved, the resulting access control will also be enforced by the model. This process is
described in figure 1.
References
[ABB+ 03] A. Abou El Kalam, R. El Baida, P. Balbiani, S. Benferhat, F. Cuppens, Y. Deswarte,
A. Mi`ge, C. Saurel, and G. Trouessin. Organization Based Access Control, June 2003.
e
[IKL+ 97] John Irwin, Gregor Kiczales, John Lamping, Jean-Marc Loingtier, Chris Maeda,
Anurag Mendhekar, and Cristina Videira Lopes. Aspect-oriented programming. pro-
ceedings of the European Conference on Object-Oriented Programming (ECOOP), June
1997.
[jaa01] Jaas tutorials, 2001. http://java.sun.com/j2se/1.5.0/docs/guide/security/jaas/ tutori-
als/index.html (Last accessed September 2009).
[J¨r04]
u Jan J¨rjens.
u Umlsec tool, 2004. Published at
http://mcs.open.ac.uk/jj2924/umlsectool/index.html (Accessed Sept. 2008).
[J¨r05]
u Jan J¨rjens. Secure Systems Development with UML. Springer-Verlag, 2005.
u
[LBD02] Torsten Lodderstedt, David Basin, and J¨rgen Doser. Secureuml: A uml-based mod-
u
eling language for model-driven security, 2002.
[OMG10] OMG. Object constraint language (ocl) 2.2, February 2010.
http://www.omg.org/spec/OCL/2.2/ (last accessed May 2010).
[SFK00] R. Sandhu, D. Ferraiolo, and R. Kuhn. The NIST model for role-based access control:
towards a unified standard. In Proceedings of the fifth ACM workshop on Role-based
access control, pages 47–63, 2000.
Page 57 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-64-320.jpg)
![2010 CRC PhD Student Conference
Effective Tutoring with Affective Embodied Conversational
Agents
Sharon Moyo
menziwa@hotmail.com
Supervisors Dr Paul Piwek
Dr Neil Smith
Department/Institute Computing
Status Part‐time
Probation viva After
Starting date Oct 2007
This natural language generation project aims to investigate the impact of affect
expression using embodied conversational agents (ECAs) in computer‐based learning
environments. Based on the idea that there is a link between emotions and learning,
we are developing an affect expression strategy. We will implement the strategy
within a tutoring system in two domains: Information Technology (IT) and Business
Studies.
Current research has not firmly established the impact of affect expression strategies
within tutorial feedback which supports learners in computer‐based learning
environments [1]. Our approach is to provide affective support through empathy.
Empathy is described as expressing emotion that is based on another’s situation
(target) and not merely one’s own [2]. An individual can show: parallel empathy that
mirrors the target’s emotion; or reactive empathy that might be different to the
target’s emotion [2].
The empathic tutor interventions will be designed to support positive emotions [3]
and reduce negative learner emotions [4] using a range of verbal and non‐verbal (or
multimodal) interventions. These interventions will be combined with corrective and
meta‐cognitive feedback [5] and presented to users as a hint or summary.
We will conduct a series of studies. Initially, we intend to develop implement and
evaluate an algorithm that generates multimodal empathic behaviours using an ECA.
The experiment conditions will include multimodal channels of communication:
speech vs. speech and facial expression vs. speech and gesture vs. speech, facial
expression and gesture. We hypothesize that participants will identify the ECA’s
expression most accurately in the condition using three channels to generate
affective expressions in comparison to the other conditions.
Page 58 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-65-320.jpg)
![2010 CRC PhD Student Conference
Additionally we aim to evaluate when and how parallel or reactive empathy can be
used to best effect in learning environments. Subsequently, we will integrate the
algorithm into a web‐based tutoring environment and conduct an evaluation in the
domain of Business Studies. Finally, in the main study we will evaluate the empathic
tutoring system in a classroom setting over several weeks in the domain of
Information Technology (IT).
We intend to contribute to current research by describing how an ECA can
effectively express multimodal [6] empathic behaviour within computer‐based
learning. More specifically, we aim to create a framework to model parallel and
reactive empathy and the learning contexts where they can be used in a quiz‐based
web environment. We intend to validate these results through evaluations across
two domains: Information Technology and Business demonstrating that the
framework can be applied to other quiz‐based learning environments.
References:
1. Arroyo, I., et al. Designing Affective Support to Foster Learning, Motivation
and Attribution. in AIED 2009. 2009. Brighton, UK: IOS.
2. Davis, M., Empathy: A Social Psychological Approach. 1994, Madison, WI:
Brown and Benchmark.
3. Bickmore, T. and D. Schulman, Practical approaches to comforting users with
relational agents, in CHI '07 extended abstracts on Human factors in
computing systems. 2007, ACM: San Jose, CA, USA.
4. Burleson, W., Affective learning companions: Strategies for empathetic
agents with real‐time multimodal affective sensing to foster meta‐cognitive
and meta‐affective approaches to learning, motivation, and perseverance. .
2006, Massachusetts Institute of Technology: Cambridge, MA.
5. Tan, J. and G. Biswas. The Role of Feedback in Preparation for Future
Learning: A Case Study in Learning by Teaching Environments. in ITS 2006.
2006: Springer‐Verlag.
6. Cassell, J., et al. Animated Conversation: Rule‐Based Generation of Facial
Expression, Gesture and Spoken Intonation for Multiple Conversational
Agents. . in Siggraph 94, ACM SIGGRAPH. 1994: Addison Wesley.
Page 59 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-66-320.jpg)




![2010 CRC PhD Student Conference
Generating Accessible Natural Language Explanations for OWL
Ontologies
Tu Anh Nguyen
t.nguyen@open.ac.uk
Supervisors Richard Power
Paul Piwek
Sandra Williams
Department/Institute Computing Department
Status Full-time
Probation Viva Before
Starting date October 2009
Introduction
This research aims to develop a computational approach to generating accessible natural
language explanations for entailments in OWL ontologies. The purpose of it is to support
non-specialists, people who are not expert in description logic and formal ontology lan-
guages, in understanding why an inference or an inconsistency follows from an ontology.
This would help to further improve the ability of users to successfully debug, diagnose and
repair their ontologies. The research is linked to the Semantic Web Authoring Tool (SWAT)
project, the on-going project aiming to provide a natural language interface for ordinary
users to encode knowledge on the semantic web. The research questions are:
• Do justifications for entailments in OWL ontologies conform to a relatively small
number of common abstract patterns for which we could generalise the problem to
generating explanations by patterns?
• For a certain entailment and its justification, how to produce an explanation in natural
language that is accessible for non-specialists?
An ontology is a formal, explicit specification of a shared conceptualisation [6]. An ontology
language is a formal language used to encode ontologies. The Web Ontology Language,
OWL [8], is a widely used description logic based ontology language. Since OWL became
a W3C standard, there has been a remarkable increase in the number of people trying to
build and use OWL ontologies. Editing environments such as Prot´g´ [15] and Swoop [13]
e e
were developed in order to support users with editing and creating OWL ontologies.
As ontologies have begun to be widely used in real world applications and more expressive
ontologies have been required, there is a significant demand for editing environments that
provide more sophisticated editing and browsing services for debugging and repairing. In
addition to being able to perform standard description logic reasoning services namely sat-
isfiability checking and subsumption testing, description logic reasoners such as FaCT++
[22] and Pellet [20] can compute entailments (e.g., inferences) to improve the users com-
prehension about their ontologies. However, without providing some kind of explanation,
it can be very difficult for users to figure out why entailments are derived from ontologies.
The generation of justifications for entailments has proven enormously helpful for identi-
fying and correcting mistakes or errors in ontologies. Kalyanpur and colleagues defined a
Page 65 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-72-320.jpg)
![2010 CRC PhD Student Conference
justification for an entailment of an ontology as the precise subset of logical axioms from
the ontology that are responsible for the entailment to hold [12]. Furthermore, he presented
a user study showing that the availability of justifications had a remarkable positive impact
on the ability of users to debug and repair their ontologies [11]. Justifications have also
been recently used for debugging very large ontologies such as SNOMED [1], which size is
too large to be able to debug and repair manually.
There are several recent studies into capturing justifications for entailments in OWL ontolo-
gies [12, 21, 9]. Nevertheless, OWL is a semantic markup language based on RDF and XML,
languages that are oriented toward machine processability rather than human readability.
Moreover, while a justification gathers together the axioms, or premises, sufficient for an
entailment to hold, it is left up to the reader to work out how these premises interplay with
each other to give rise to the entailment in question. Therefore, many users may struggle
to understand how a justification supports an entailment since they are either unfamiliar
with OWL syntax and semantics, or lack of knowledge about the logic underpinning the
ontology. In other words, the ability of users to work out how an entailment arises from a
justification currently depends on their understanding of OWL and description logic.
In recent years, the development of ontologies has been moving from “the realm of artificial
intelligence laboratories to the desktops of domain experts”, who have insightful knowledge
of some domain but no expertise in description logic and formal ontology languages [14].
It is for this reason that the desire to open up OWL ontologies to a wide non-specialist
audience has emerged. Obviously, the wide access to OWL ontologies depends on the devel-
opment of editing environments that use some transparent medium; and natural language
(e.g., English, Italian) text is an appropriate choice since it can be easily comprehended by
the public without training. Rector and colleagues observed common problems that users
frequently encounter in understanding the logical meaning and inferences when working
with OWL-DL ontologies, and expressed the need for a “pedantic but explicit” paraphrase
language to help users grasp the accurate meaning of logical axioms in ontologies [18].
Several research groups have proposed interfaces to encode knowledge in semantics-based
Controlled Natural Languages (CNLs) [19, 4, 10]. These systems allow users to input sen-
tences conforming with a CNL then parse and tranform them into statements in formal
ontology languages. The SWAT project [16] introduces an alternative approach based on
Natural Language Generation. In SWAT, users specify the content of an ontology by “di-
rectly manipulating on a generated feedback text” rather than using text interpretation;
therefore, “editing ontologies on the level of meaning, not text” [17].
Obviously, the above mentioned interfaces are designed for use by non-specialists to build up
ontologies without having to work directly on formal languages and description logic. How-
ever, research on providing more advanced editing and browsing services on these interfaces
to support the debugging and repairing process has not been investigated yet. Despite the
usefulness of providing justifications in the form of sets of OWL axioms, understanding the
reasons why entailments or inconsistencies are drawn from ontologies is still a key problem
for non-specialists. Even for specialists, having a more user-friendly view of ontology with
accessible explanations can be very helpful. Thus, this project seeks to develop a compu-
tational approach to generating accessible natural language explanations for entailments in
OWL ontologies in order to assist users in debugging and repairing their ontologies.
Methodology
Page 66 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-73-320.jpg)
![2010 CRC PhD Student Conference
The research approach is to identify common abstract patterns of justifications for entail-
ments in OWL ontologies. Having identified such patterns we will focus on generating
accessible explanations in natural languages for most frequently used patterns. A prelim-
inary study to work out the most common justification patterns has been carried out. A
corpus of eighteen real and published OWL ontologies of different expressivity has been
collected from the Manchester TONEs reposistory. In addition, the practical module devel-
oped by Matthew Horridge based on the research on finding all justifications for OWL-DL
ontologies [12, 7] has been used. Justifications are computed then analysed to work out the
most common patterns. Results from the study show that over the total 6772 justifications
collected, more than 70 percent of justifications belongs to the top 20 patterns. Study on
a larger and more general ontology corpus will be carried out in next steps. Moreover, a
user study is planned to investigate whether non-specialists perform better on a task when
reading accessible explanations rather than justifications in the form of OWL axioms.
The research on how to create explanations accessible for non-logicians is informed by studies
on proof presentations. In Natural Deduction [5], how a conclusion is derived from a set of
premises is represented as a series of intermediate statements linking from the premises to
the conclusion. While this approach makes it easy for users to understand how to derive
from one step to the next, it might cause difficulty to understand how those steps linked
together to form the overall picture of the proof. Structured derivations [2], a top-down
calculational proof format that allows inferences to be presented at different levels of detail,
seems to be an alternative approach for presenting proof. It was proposed by researchers
as a method for teaching rigorous mathematical reasoning [3]. Research on whether using
structured derivations would help to improve the accessibility of explanations as well as
where and how intermediate inferences should be added is being investigated.
Conclusion
Since the desire to open up OWL ontologies to a wide non-specialist audience has emerged,
several research groups have proposed interfaces to encode knowledge in semantics-based
CNLs. However, research on providing debugging and repairing services on these inter-
faces has not been investigated yet. Thus, this research seeks to develope a computational
approach to generating accessible explanations to help users in understanding why an entail-
ment follows from a justification. Research work includes identifying common abstract jus-
tification patterns and studying into generating explanations accessible for non-specialists.
References
[1] F. Baader and B. Suntisrivaraporn. Debugging SNOMED CT Using Axiom Pinpointing
in the Description Logic EL+. In KR-MED, 2008.
[2] R. Back, J. Grundy, , and J. von Wright. Structured Calculational Proof. Technical
report, The Australian National University, 1996.
[3] R.-J. Back and J. von Wright. A Method for Teaching Rigorous Mathematical Rea-
soning. In ICTMT4, 1999.
[4] A. Bernstein and E. Kaufmann. GINO - A Guided Input Natural Language Ontology
Editor. In ISWC, 2006.
Page 67 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-74-320.jpg)
![2010 CRC PhD Student Conference
[5] G. Gentzen. Untersuchungen uber das logische Schließen. II. Mathematische Zeitschrift,
¨
39:405–431, 1935.
[6] T. R. Gruber. A translation approach to portable ontology specifications. Knowledge
Acquisition, 5:199–220, 1993.
[7] M. Horridge, B. Parsia, and U. Sattler. Laconic and Precise Justifications in OWL. In
ISWC, pages 323–338, 2008.
[8] I. Horrocks, P. F. Patel-Schneider, and F. van Harmelen. From SROIQ and RDF to
OWL: The Making of a Web Ontology Language. J. Web Semantics, 1:7–26, 2003.
[9] Q. Ji, G. Qi, and P. Haase. A Relevance-Directed Algorithm for Finding Justifications
of DL Entailments. In ASWC, pages 306–320, 2009.
[10] K. Kaljurand and N. E. Fuchs. Verbalizing OWL in Attempto Controlled English. In
OWLED, 2007.
[11] A. Kalyanpur. Debugging and repair of OWL ontologies. PhD thesis, University of
Maryland, 2006.
[12] A. Kalyanpur, B. Parsia, M. Horridge, and E. Sirin. Finding All Justifications of OWL
DL Entailments. In ISWC, 2007.
[13] A. Kalyanpur, B. Parsia, E. Sirin, B. Cuenca-Grau, and J. A. Hendler. Swoop: A Web
Ontology Editing Browser. Journal of Web Semantics, 4:144–153, 2006.
[14] N. F. Noy and D. L. McGuinness. Ontology Development 101: A Guide to Creating
Your First Ontology. Technical report, Stanford University, 2001.
[15] N. F. Noy, M. Sintek, S. Decker, M. Crub´zy, R. W. Fergerson, and M. A. Musen.
e
Creating Semantic Web Contents with Prot´g´-2000. IEEE Intell. Syst., 16:60–71,
e e
2001.
[16] R. Power. Towards a generation-based semantic web authoring tool. In ENLG, pages
9–15, 2009.
[17] R. Power, R. Stevens, D. Scott, and A. Rector. Editing OWL through generated CNL.
In CNL, 2009.
[18] A. Rector, N. Drummond, M. Horridge, J. Rogers, H. Knublauch, R. Stevens, H. Wang,
and C. Wroe. OWL Pizzas: Practical Experience of Teaching OWL-DL: Common
Errors & Common Patterns. In EKAW, 2004.
[19] R. Schwitter and M. Tilbrook. Controlled Natural Language meets the Semantic Web.
In ALTW, pages 55–62, 2004.
[20] E. Sirin, B. Parsia, B. C. Grau, A. Kalyanpur, and Y. Katz. Pellet: A practical
OWL-DL reasoner. Journal of Web Semantics, 5:51–53, 2007.
[21] B. Suntisrivaraporn, G. Qi, Q. Ji, and P. Haase. A Modularization-based Approach to
Finding All Justifications for OWL DL Entailments. In ASWC, pages 1–15, 2008.
[22] D. Tsarkov and I. Horrocks. FaCT++ Description Logic Reasoner: System Description.
In IJCAR, volume 4130, pages 292–297, 2006.
Page 68 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-75-320.jpg)

![2010 CRC PhD Student Conference
The activity element refers to how active the researchers, institutions, and organizations are within
the field, for instance event attendance or organization, or the number and frequency of publications
and events. A tool that can be used to explore this is Faceted DBLP2 , a server interface for the
DBLP server3 which provides bibliographic information on major computer science journals and
proceedings [Ley 2002]. Faceted DBLP starts with some keyword and shows the result set along
with a set of facets, e.g. distinguishing publication years, authors, venues, and publication types.
The user can characterize the result set in terms of main research topics and filter it according to
certain subtopics. There are GrowBag graphs available for keywords (number of hits/coverage).
Popularity is about the interest that is displayed in a person, institution or organization, publica-
tion, topic, technology, or event. WikiCFP4 is a service that helps organize and share academic
information. Users can browse and add calls for papers per subject category, and users to add calls
for papers to their own personal user list. Each call for paper has information on the event name,
date, location, and deadline. WikiCFP also provides hourly updated lists of the most popular
categories, calls for papers, and user lists.
One indicator of topic popularity is the number of publications on a topic. There are many tools
that show the number of publications per topic per year. PubSearch is a fully automatic web mining
approach for the identification of research trends that searches and downloads scientific publications
from web sites that typically include academic web pages [Tho et al. 2003]. It extracts citations
which are stored in the tool’s Web Citation Database which is used to generate temporal document
clusters and journal clusters. These clusters are then mined to find their interrelationships, which
are used to detect trends and emerging trends for a specified research area.
Another indicator of popularity is how often a publication or researcher is cited. Citations can
also help identify relations between researchers through analysis of who is citing who and when,
and what their affiliations are. Publish Or Perish is a piece of software that retrieves and analyzes
academic citations [Harzing and Van der Wal 2008]. It uses Google Scholar5 to obtain raw citations,
and analyzes them. It presents a wide range of citation metrics such as the total number of papers
and citations, average number of citations per paper and author, the average number of papers per
author and year, an analysis of number of authors per paper, et cetera.
Topics, interests, and people evolve over time, and the makeup of the research community changes
when people and organizations enter or leave certain research areas or change their direction.
Some topics appear to be more established or densely represented in certain geographical areas,
for instance because a prolific institution is located there and has attracted several experts on a
particular topic, or because many events on a topic are held in that area. AuthorMapper6 is an
online tool for visualizing scientific research. It searches journal articles from the SpringerLink7
and allows users to explore the database by plotting the location of authors, research topics and
institutions on a world map. It also allows users to identify research trends through timeline graphs,
statistics and regions.
Keywords are an important indicator of a research area because they are the labels that have been
put on publications or events by the people and organizations within that research area. Google
2 http://dblp.l3s.de/
3 http://dblp.uni-trier.de/
4 http://www.wikicfp.com/
5 http://scholar.google.com/
6 http://www.authormapper.com/
7 http://www.springerlink.com/
Page 70 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-77-320.jpg)
![2010 CRC PhD Student Conference
Scholar is a subset of the Google search index consisting of full-text journal articles, technical re-
ports, preprints, thesis, books, and web sites that are deemed ’scholarly’ [Noruzi 2005, Harzing and
Van der Wal 2008]. Google Scholar has crawling and indexing agreements with several publishers.
The system is based on keyword search only and its results are organized by a closely guarded
relevance algorithm. The ’cited-by-x’ feature allows users to see by whom a publication was cited,
and where.
The availability of new studentships indicates that a research area is trying to attract new people.
This may mean that the area is hoping to expand, change direction, or become more established.
The availability of funding within a research area or topic is an indicator of the interest that
is displayed in it, or the level of importance it is deemed to have at a particular time. The
Postgraduate Studentships web site8 offers a search engine as well as a browsable list of study or
funding opportunities organized by subjects, masters, PhD/doctoral and professional doctorates
and a browsable list of general funders, funding universities and featured departments. The site
also lists open days and fairs.
The level of impact of the research carried out by a research group, institution, organization or
individual researcher leads to their establishment in the research community, which in turn could
lead to more citations and event attendance. The technologies element refers to the technologies
that are developed within an area of research, and their impact, popularity and establishment.
Research impact is on a small scale implemented into Scopus (http://www.scopus.com/), currently
a preview-only tool which, amongst other things, identifies and matches an organization with all
its research output, tracks how primary research is practically applied in patents and tracks the
influence of peer-reviewed research on web literature. It covers nearly 18,000 titles from over 5,000
publishers, 40,000,000 records, scientific web pages, and articles-in-press. A tool that ranks publi-
cations is DBPubs, a system for analyzing and exploring the content of database publications by
combining keyword search with OLAP-style aggregations, navigation, and reporting [Baid et al.
2008]. It performs keyword search over the content of publications. The meta data (title, author,
venue, year et cetera) provide OLAP static dimensions, which are combined with dynamic dimen-
sions discovered from the content of the publications in the search result, such as frequent phrases,
relevant phrases and topics. Based on the link structure between documents (i.e. citations) publi-
cation ranks are computed, which are aggregated to find seminal papers, discover trends, and rank
authors.
Finally, we would like to discuss a more generic tool, DBLife9 [DeRose et al. 2007, Goldberg and
Andrzejewski 2007, Doan et al. 2006], which is a prototype of a dynamic portal of current informa-
tion for the database research community. It automatically discovers and revisits web pages and
resources for the community, extracts information from them, and integrates it to present a unified
view of people, organizations, papers, talks, et cetera. For example, it provides a chronological
summary, has a browsable list of organizations and conferences, and it summarizes interesting new
facts for the day such as new publications, events, or projects. It also provides community statistics
including top cited people, top h-indexed people, and top cited publications. DBLife is currently
unfinished and does not have full functionality, but from the prototype alone one can conclude it
will most likely address quite a few elements from our framework.
8 http://www.postgraduatestudentships.co.uk/
9 http://dblife.cs.wisc.edu/
Page 71 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-78-320.jpg)


![Understanding technology-rich learning
spaces
Nadia Pantidi Yvonne Rogers Introduction
In the last few years, a substantial amount of funding
2010 CRC PhD Student Conference
The Open University, The Open University,
Walton Hall. Walton Hall. has been allocated to schools and universities in the
Milton Keynes, MK7 6AA Milton Keynes, MK76AA world, but especially the UK, for creating new
k.pantidi@open.ac.uk y.rogers@open.ac.uk ‘technology-rich’ learning spaces. These new spaces
Page 74 of 125
have been proposed as examples of future places for
Hugh Robinson supporting and enhancing informal and formal learning,
The Open University, collaboration, creativity and socialising [4]. However,
Walton Hall. little is known as to whether these claims are being
Milton Keynes, MK7 6AA realized in actual practice. This research is examining
h.m.robinson@open.ac.uk how and whether they are used, focusing on the
interdependence of physical space, furniture and
Abstract technology configuration.
A number of novel technology-rich learning spaces have
been developed over the last few years. Many claims have Background
been made in terms of how they can support and enhance Several studies of technology situated in educational
learning, collaboration, community participation, and settings have been carried out that focus on
creativity. This line of research is investigating whether understanding how technology affects users’ everyday
such learning spaces are living up to such claims. The life and vice versa; and whether the technology serves
approach is ethnographic; a number of field studies have the purposes it was designed for. Findings from these
been conducted examining how people use the spaces in studies have been mixed. For example, Brignull et al.
practice. Findings so far have shown that the positioning of [1] implemented Dynamo, a large multi-user
the technology, flexibility and a sense of ownership and interactive surface to enable the sharing and exchange
control over the technology are key issues. of a wide variety of digital media, in the common room
of a high school and report that users appropriated the
Keywords functionality of the display in a way that was consistent
Technology-rich learning spaces, ethnographic with the space’s previous use. Moreover, it did not
approach, designed and actual use
Copyright is held by the author/owner(s).](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-81-320.jpg)
![2
support other uses that the researchers expected. How do people interact with each other and the
Similarly, McDonald et al. [3], situated three proactive technology?
displays in an academic conference to augment the What insights emerge for the use of the
participants’ interactions; specifically to enhance the technology by understanding the use of the
feeling of community, facilitate social networking and physical space?
future collaborations. Findings from this study showed To address these questions, in situ ethnographic
that people appropriated the technology by extending studies have been carried out on three multi-purpose
its use in an innovative and fun way which conflicted technology-rich settings, called Dspace, Qspace,
with the common practices and social conventions Cspase. Dspace was designed as a technology-rich
already in place and thus, led to negative comments space set in a library on a university campus. It was
about the application. More dramatically, a study created as a creative play area for visitors to
evaluating the use of interactive whiteboards in UK experiment with and explore new ideas and share
2010 CRC PhD Student Conference
schools found no significant impact on the pupils’ knowledge; a space that brings together new
performance relating to the use of interactive technologies and ideas on how they could be used for
whiteboards [2]. learning and teaching now or in the future. Qspace, is a
Page 75 of 125
large space that was designed to support a variety of
Much research to date has focused on single technology planned learning activities (e.g. workshops) to enable
interventions, where a public display or interactive groups of individuals to come together within a high
whiteboard has been placed in a pre-existing space to technology environment to communicate their ideas
serve a specific purpose/functionality. However, there and generate their designs in a creative way. It is a
are learning spaces that have been designed from blank space that can be re-shaped physically and
scratch to be ‘technology-rich’ and where their spatial technologically depending on the activity that takes
and technological design is intended to be much place. The space was deliberately designed to be
broader (e.g. Saltire Center, CILASS). An assortment of technologically-rich as a means of promoting creativity
new technologies and furniture have been configured to and supporting collaboration in innovative ways.
create new learning spaces. This research focuses on Cspace, was designed as a study space for students to
how successful these multi-purpose spaces have been work together both during lab sessions and in their own
in supporting what they were designed for. The time. It is a flexible technology-rich working
questions addressed are: environment that allows multiple ‘study’ activities
including teaching, programming, hardware
What are the differences between anticipated
experimentation, and facilitated discussions.
and actual use (if any)?
What is the nature of the interactional work in Methodology
these novel spaces?
The method used is ethnographic involving participant
How do people behave and interact with the observation and semi-structured interviews. A series of
space? ethnographic studies was carried out in the different
settings throughout the last 18 months and will](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-82-320.jpg)

![4
way, the technology was patrolled and used by the out in three novel technology-rich learning spaces. Our
managers, and it was only ‘post hoc’ available to the findings so far suggest that for these spaces to support
actual users. informal and formal learning, collaboration, creativity
and socialising, issues such as the spatial arrangement,
Another critical element for successful technology-rich flexibility and accessibility of the technology need to be
learning spaces seems to be the physical arrangement considered. Future work involves further in situ studies
of the technology in the space; specific spaces or to a variety of similar settings with the aim to develop a
physical layouts bear established associations and set of design guidelines and concerns for those involved
etiquettes that can affect the way users interact with or in developing ‘learning spaces’ and ‘classrooms of the
appropriate the technology. For example, in Dspace it future’.
was found that despite the abundance of technology
and the many motivating cues and clues, its use was References
2010 CRC PhD Student Conference
limited. The technology was not experimented or [1] Brignull, H., Izadi, S., Fitzpatrick, G., Rogers, Y.,
played with in the ways planned for [5]. A plausible and Rodden, T. The introduction of a shared interactive
explanation for this, based on the collected data, has to surface into a communal space. Proc. CSCW 2004, ACM
Page 77 of 125
do with the positioning of the technology in the space; Press (2004).
most of the devices were placed on shelves (Figure 2),
creating the impression that they were for display only, [2] Hennessy, S., Deaney, R., Ruthven, K., and
thus discouraging potential users from interacting with Winterbottom, M. Pedagogical strategies for using the
them. interactive whiteboard to foster learner participation in
school science. Learning, Media and Technology, 32
(3), (2007), 283–301.
[3] McDonald, D.W., McCarthy, J.F., Soroczak, S.,
Nguyen, D.H., and Rashid, A.M. Proactive displays:
Supporting awareness in fluid social environments. ACM
Transactions on Computer- Human Interaction, 14 (4),
Article 16, (2008).
[4] Oblinger, D. Learning Spaces. Educause, 2006.
Figure 2. A collection of mobile phones for users to interact
with and experiment are displayed on shelves.
[5] Pantidi, N., Robinson, H.M., and Rogers, Y. Can
Conclusion technology-rich spaces support multiple uses?. Proc.
This paper discusses briefly a selection of findings British CHI Group Annual Conference on HCI (2), BCS
emerging from a series of ethnographic studies carried (2008), 135-138.](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-84-320.jpg)
![2010 CRC PhD Student Conference
How best to support scientific end-user software
development?
Aleksandra Pawlik
a.n.pawlik@open.ac.uk
Supervisors Dr. Judith Segal
Prof. Marian Petre
Prof. Helen Sharp
Department/Institute Computing
Status Full-time
Probation viva Before
Starting date October 2009
Introduction
End-user software development has received substantial amounts of attention within
both the academic and software engineering communities [1-3]. One of the sub-
groups that can be distinguished amongst end-user developers is that of scientific end-
user developers [4]. A particular set of characteristics differentiates scientists from
other end-user developers. Firstly, working in the field of science often necessitates
the use of various software packages on a daily basis. Secondly, scientists are familiar
with and utilize formal languages as well as particular modelling techniques.
Additionally, the majority of science degree curriculums offered by universities
contain at least one course in programming. Thus, many scientists have some
experience with coding at a relatively early stage of their academic and professional
career. In many cases, conducting a scientific research project means developing a
tailor-made software tool which will address a particular scientific problem. Therefore,
it may seem that scientists are “predisposed” to being effective and successful end-
user software developers more likely to produce a sustainable end-product software.
However, numerous problematic issues related to scientific end-user software
development have been reported by researchers in computing [5, 6], software
engineers [7] and scientists themselves [8]. For the purpose of my research project, I
will make the distinction between two different contexts within scientific end-user
software development:
- Limited Context: when software is developed (usually in a purely academic
environment) in order to address a specific problem within a particular project
which is being run by a limited group of anticipated users;
- Extended Context: when it is expected that the software will be reusable,
maintainable and flexible (i.e. potentially used by an extended group of as yet
undetermined users).
Scientific end-user software development needs, therefore, relevant and effective
support from the software development professionals’ community. Despite the fact
that some related help exists and is available [9], scientists who develop software and
software engineers who collaborate with them at various levels may find scientific
software development problematic. This indicates that the assistance and support
provided may need adjustments and improvements, an objective that may be
approached from different angles. First of all, it is essential to identify and examine
difficulties which may crop up during scientific end-user software development. The
second approach is to investigate and understand the origins of these problems.
Page 78 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-85-320.jpg)
![2010 CRC PhD Student Conference
Finally, we need to comprehend why the support available for scientific end-users
provided by the software development professionals’ community does not seem to be
working effectively and what steps should be taken to attempt to remedy this. I argue
that these steps need to involve observing the practices applied during scientific
software development in a number of different contexts.
In my PhD research project, I intend to focus on exploring the tools and methods
which scientific end-user developers employ in their work. The answer to the
question ”What techniques do scientific end-user developers use?” should allow me
to identify the ways in which scientists address issues that emerge during software
development. Additionally, I will pay special attention to the methods which scientific
end-user developers find successful. By “successful” I mean those that were
introduced and maintained during part or indeed the whole cycle of software
development, and which resulted in sustainable software. Thus, my second research
question is “What are the problematic and successful applications of tools and
techniques for supporting end-user software developers?". The results of my study
may potentially provide sufficient information which could be used to tailor and
improve ways of assisting scientific end-user development.
Background
A number of researchers investigated the characteristics and issues related to
scientific end-user development. For example, Segal [10] notes that the software
development process consists of short cycles and proposes an “iterative and
incremental” model of scientific software development which is a result of the fact
that the majority of scientific work remains experimental and is based on
approximation models. Moreover, some scientific projects involve tacit knowledge,
something which creates difficulties in establishing requirements and designing
software packages [11]. The experimental nature of these scientific projects, the
application of tacit knowledge and the approximations generated by mathematical
models create a further problem, that of software testing [12] [13].
Some problems are generated by the fact that many scientific end-user developers
make software within a very limited context of usage. The main aim of scientific
projects is to advance science, deliver and publish the findings. The resources (time,
finances and people) allocated to software development within the framework of a
scientific project tend to be insufficient [14]. Therefore, scientists’ reluctance to
apprehend, for example, object-oriented programming languages, and their preference
to implement code in Fortran seems justified. Moreover, by sticking with familiar
programming languages, scientific end-user developers reduce the risk of errors that
might result from the use of languages which are new or unfamiliar to them [6]. Since,
within the scientific working culture [5], software development is not made a high
priority, scientists who develop software packages do not, as a result, receive relevant
credit, something which tends to discourage them from putting more effort into
creating sustainable software [14]. Other factors which contribute to problems with
scientific end-user software development, such as lack of effective project
management or problems with the labour division, may dissuade developers from
making use of any version control systems or configuration management tools [15].
Page 79 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-86-320.jpg)
![2010 CRC PhD Student Conference
In fact, tailor-made resources relating directly to software engineering techniques and
methods supporting scientific end-user software development are available and being
continuously developed, mainly by software development professionals [16].
However, these resources only receive rather a poor uptake from the scientific
community, as scientists prefer to teach themselves from, for example, generic
textbooks, colleagues, the Internet, and so on [17] [6]. Additionally, as described by
Kelly [18], the chasm that divides the different approaches to software development
between the communities of scientific end-user developers and software development
professionals only serves to cause further discrepancies in the overall communication
between the two groups.
Methodology
I intend to investigate case studies of scientific end-user software development in
which various software engineering techniques and methods were used in covering
the following:
- The transition of turning purely academic (Limited Context) scientific software
packages into commercial ones;
- The transition of turning purely academic (Limited Context) scientific software
packages into open source (Extended Context) ones;
- The development of scientific software which directly involves software
development professionals (Extended Context).
Since this PhD research project is exploratory in nature, qualitative research methods
would seem to be the most appropriate. Moreover, studies in information systems are
highly context-dependent and interpretative [19], something which requires making
use of methods that allow researchers to investigate issues in depth. I will use
interviews and participant observation as the main methods of data collection. The
interviews will be conducted with both scientific end-user developers and software
development professionals who are directly involved, together with scientists, in
scientific software development teams. The former will constitute the majority of the
respondent group whilst interviews with software development professionals will aim
to provide additional information about the application of methods and techniques for
supporting scientific end-user development. Ideally the interviews will be combined
with participant observation enabling me to obtain a fuller picture of the process and
to perceive any issues related to scientific end-user development. Two things will be
crucial in the sampling of the case studies: being able to obtain maximum variation
within the sample, but also the ability to include convenient sampling (e.g. contacting
respondents, access to the fieldwork etc.), something which will doubtless have an
impact on the final construction of the set of case studies.
References
[1] B. A. Myers, M. M. Burnett, S. Wiedenbeck, A. J. Ko, and M. B. Rosson,
"End user software engineering: CHI: 2009 special interest group meeting," in
Proceedings of the 27th international conference extended abstracts on
Human factors in computing systems Boston, MA, USA: ACM, 2009.
[2] H. Lieberman, Paternò, F., Wulf, V., "End user development," Dordrecht, The
Netherlands: Springer, 2006.
Page 80 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-87-320.jpg)
![2010 CRC PhD Student Conference
[3] M. F. Costabile, P. Mussio, L. P. Provenza, and A. Piccinno, "End users as
unwitting software developers," in Proceedings of the 4th international
workshop on End-user software engineering Leipzig, Germany: ACM, 2008.
[4] J. Segal and S. Clarke, "Point/Counterpoint: Software Engineers Don't Know
Everything about End-User Programming," Software, IEEE, vol. 26, pp. 54-57,
2009.
[5] J. Segal, "Software Development Cultures and Cooperation Problems: A field
Study of the Early Stages of Development of Software for a Scientific
Community," Computer Supported Cooperative Work (CSCW), vol. 18, pp.
581-606, 2009.
[6] R. Sanders and D. Kelly, "Dealing with risk in scientific software
development," Software, IEEE, pp. 21-28, 2008.
[7] V. R. Basili, D. Cruzes, J. C. Carver, L. M. Hochstein, J. K. Hollingsworth, M.
V. Zelkowitz, and F. Shull, "Understanding the high-performance-computing
community: A software engineer's perspective," Software, IEEE, vol. 25, pp.
29-36, 2008.
[8] C. Rickett, S. Choi, C. Rasmussen, and M. Sottile, "Rapid prototyping
frameworks for developing scientific applications: A case study," The Journal
of Supercomputing, vol. 36, pp. 123-134, 2006.
[9] G. Wilson, "Those Who Will Not Learn From History," Computing in Science
and Engineering, vol. 10, p. 5, 2008.
[10] J. Segal, "Models of scientific software development," in Workshop on
Software Engineering in Computational Science and Engineering, Leipzig,
Germany, 2008
[11] S. Thew, A. Sutcliffe, R. Procter, O. de Bruijn, J. McNaught, C. C. Venters,
and I. Buchan, "Requirements Engineering for E-science: Experiences in
Epidemiology," Software, IEEE, vol. 26, pp. 80-87, 2009.
[12] D. Hook and D. Kelly, "Testing for trustworthiness in scientific software," in
Proceedings of the 2009 ICSE Workshop on Software Engineering for
Computational Science and Engineering: IEEE Computer Society, 2009.
[13] S. Easterbrook and T. Johns, "Engineering the Software for Understanding
Climate Change," Computing in Science and Engineering, vol. 26, 2009.
[14] "Reporting Back - Open Middleware Infrastructure Institute Collaboration
Workshops 2010," http://www.omii.ac.uk/wiki/CW10ReportingBack, 2010.
[15] M. Vigder, "End-user software development in a scientific organization," in
Proceedings of the 2009 ICSE Workshop on Software Engineering
Foundations for End User Programming: IEEE Computer Society, 2009.
[16] "Software Carpentry - an intensive introduction to basic software development
practices for scientists and engineers," http://software-carpentry.org/.
[17] G. Wilson, "How Do Scientists Really Use Computers?," American Scientist,
vol. 97, pp. 360-362, 2009.
[18] D. Kelly, "A software chasm: Software engineering and scientific computing,"
Software, IEEE, p. 120, 2007.
[19] H. K. Klein and M. D. Myers, "A set of principles for conducting and
evaluating interpretive field studies in information systems," MIS Quarterly,
vol. 23, p. 67(2), 1999.
Page 81 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-88-320.jpg)
![2010 CRC PhD Student Conference
Non-Cooperation in
Computational Models of Dialogue
Brian Plüss
b.pluss@open.ac.uk
Supervisors Paul Piwek
Richard Power
Department/Institute Computing Department
Status Fulltime
Probation viva After
Starting date 01/10/08
This research is aimed at finding a computable description (i.e., a computational
model) of non-cooperative conversational behaviour in political interviews.
Most approaches to finding computational models of dialogue behaviour are based on
a strong notion of cooperation between the dialogue participants (DPs). Researchers
have proposed models based on DP's intentions (Cohen and Levesque, 1991),
regarded dialogue as a game with strict rules guiding the speaker's actions and the
hearer's interpretation of those actions (Power, 1979), or addressed conversation as
the joint construction of goal-oriented plans that are shared by DPs (Grosz and Sidner,
1990). These models successfully explain dialogue situations in which DPs recognise
each other's intentions and, at least to a certain extent, accept each other's goals when
deciding on their actions. These assumptions are theoretically grounded (Grice, 1975;
Clark and Shaefer, 1989) and also practically sound: dialogue models are usually
implemented in the form of dialogue systems, built for the purpose of providing a
service to their users. Take, for instance, the following exchange from the TRAINS
dialogue system (Ferguson et al. 1996):
User I need to get to Detroit, Syracuse, and Montreal.
System Ok.
User Let's send the trains from Chicago to Detroit.
System Ok. [draws route from Chicago to Detroit via Toledo] But the terminal
at Toledo is delaying traffic due to bad weather. Trains will take an
additional five hours to move through there. [highlights Toledo red]
User That's ok. Now let's go from Atlanta up to Syracuse.
System Please tell me a route to use to get from Atlanta to Syracuse.
User Go via Charleston and Pittsburgh.
(...)
System No problem. [draws route]
User That's great.
System I hope it was helpful.
In this scenario, failure to cooperate, either on the side of the system or of the user, is
against the premises on which the system is conceived and used. In everyday
Page 82 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-89-320.jpg)








![2010 CRC PhD Student Conference
new type of data that has yet to be fully explored nor exploited when modelling
users.
The work presented here combines the mining of social graphs that occur in
Flickr with visual content and metadata analysis to provide better personalised
photo recommender mechanisms and the following experiment and its analysis
are a major component in my overall thesis.
Interaction Scenario
In order to address this research question, multiple experiments have been car-
ried out, one of which I present here:
Envisage an incoming stream of photos made available to a user. In
systems of a scale similar to Flickr, this could be thousands of im-
ages per second. Can a system that uses cues from the social, visual
and semantic aspects of these images perform better than one that
uses the more traditional approach of using only semantic informa-
tion, according to specifically defined objective metrics? How does
performance vary between users?
An experiment was carried out that mines data from the social communities in
Flickr, from the visual content of images and from the text based metadata and
uses a machines learning mechanism to merge these signals together to form a
classifier that, given a candidate image and prospective viewing user, decides
whether the user would label that image as a ‘Favourite’2 - see Figure 1.
Related Work
The significant influence that our peers can have on our behaviour online has
been studied by researchers such as Lerman and Jones[3], and the particular
interaction that occurs between users and visual media in particular in the
work of Nov et al.[4]and Kern et al[2]. Their insights into the importance of
understanding more about a user in order to best fulfil their information need
supports the hypothesis that this kind of information can be usefully exploited
to improve systems that try to match that need to a data set supported by social
interaction. Here I extend their ideas by incorporating this valuable social data
into a complementary multimodal framework that takes advantage of multiple
types of data.
The use of social interaction features in the work of Sigurbjörnsson and van
Zwol[7] and Garg and Weber[1] inspired my more comprehensive feature set
and its analysis. Their findings that aggregating data generated from online
communities is valuable when suggesting tags is important and I believe also
transfers to recommendation in general as well as to the specific task of recom-
mending images. In fact, I demonstrated this in previous work on social media
tag suggestion[6].
I use some of the human perception based visual features outlined in the
work of San Pedro and Siersdorfer[5], as these have been shown to work well
in similar experimental scenarios and cover a range of visual classes. I extend
them further with a selection of other high performing visual features.
2A binary label Flickr users can use to annotate an image they like.
Page 92 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-99-320.jpg)

![2010 CRC PhD Student Conference
System Accuracy + Prec. + Rec. - Prec. - Rec.
Textual 0.87 0.48 0.18 0.88 0.97
Visual 0.88 1.00 0.09 0.88 1.00
Social 0.92 0.80 0.56 0.94 0.98
Textual+Visual 0.88 0.62 0.27 0.90 0.97
Textual+Social 0.92 0.77 0.62 0.94 0.97
Visual+Social 0.93 0.89 0.56 0.94 0.99
Text+Vis.+Soc. 0.93 0.84 0.62 0.94 0.98
Table 1: Accuracy, precison and recall for various combinations of features using
the experiments most realistic scenario data set. Photos labelled as ‘Favourites’
are positive examples, and those that are not are negative examples. Higher
numbers are better.
• As is typical in this style of information retrieval experiment, we can trade-
off between precision and recall depending on our requirements. As we are
interested in high precision in this particular experiment, we see that the
combination of the Visual+Social and Text+Visual+Social runs
give good precision without sacrificing too much recall.
References
[1] Nikhil Garg and Ingmar Weber. Personalized, interactive tag recommenda-
tion for flickr. In Proceedings of the 2008 ACM Conference on Recommender
Systems, pages 67–74, Lausanne, Switzerland, October 2008. ACM.
[2] R. Kern, M. Granitzer, and V. Pammer. Extending folksonomies for image
tagging. In Workshop on Image Analysis for Multimedia Interactive Services,
2008, pages 126–129, May 2008.
[3] Kristina Lerman and Laurie Jones. Social browsing on flickr. In Proceedings
of ICWSM, December 2007.
[4] Oded Nov, Mor Naaman, and Chen Ye. What drives content tagging: the
case of photos on flickr. In Proceeding of the twenty-sixth annual SIGCHI
conference on Human factors in computing systems, pages 1097–1100, Flo-
rence, Italy, 2008. ACM.
[5] Jose San Pedro and Stefan Siersdorfer. Ranking and classifying attractive-
ness of photos in folksonomies. In WWW, Madrid, Spain, April 2009.
[6] Adam Rae, Roelof van Zwol, and Börkur Sigurbjörnsson. Improving tag
recommendation using social networks. In 9th International conference on
Adaptivity, Personalization and Fusion of Heterogeneous Information, April
2010.
[7] Roelof van Zwol. Flickr: Who is looking? In IEEE/WIC/ACM Inter-
national Conference on Web Intelligence, pages 184–190, Washington, DC,
USA, 2007. IEEE Computer Society.
Page 94 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-101-320.jpg)
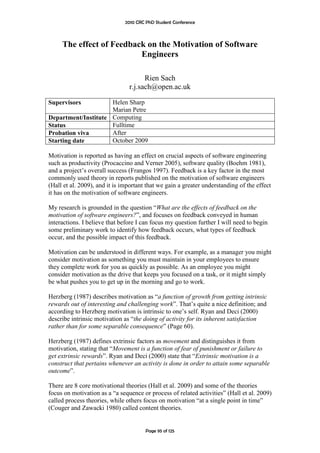


![2010 CRC PhD Student Conference
Using Business Process Security Requirements for IT
Security Risk Assessment
Stefan Taubenberger
stefan.taubenberger@web.de
Supervisors Bashar Nuseibeh
Jan Jürjens
Charles Haley
Department/Institute Computing
Status Part-time
Probation viva After
Starting date October 2007
Companies and governmental organizations are suffering from information
technology (IT) risks caused by malicious or negligent events and by inappropriate
process designs related to authorization, access control or segregation of duties.
Examples of such events are the loss of two data discs of 25 million child benefit
records in the UK or the trading losses at Société Générale. Many quantitative and
qualitative methods and toolkits for IT security risk analysis have been developed
using e.g. Bayesian probability, Fuzzy theories, Courtney, the Livermore risk analysis
methodology (LRAM)… all of which are based on probabilities and events as risk is
defined e.g. in ISO 27002 as a “combination of the probability of an event and its
consequence” ([3], p. 2). But with these traditional risk analysis approaches, IT risks
often cannot be determined reliably and with precision. Because security events are
difficult to identify in a way that guarantees correctness and completeness of this
process, since the methods provide only general descriptions how to identify them [7].
Probabilities in practice are difficult to estimate with sufficient degree of precision and
reliability as statistical data is missing or outdated [6] and influenced by perception [5].
IT security risk assessment approaches using business process models and security
requirements provide a way which may overcome these limitations. The usage of
security requirements as well as business or critical assets for risk assessment is not
new and in general described in the ISO 27000 series as well as implemented in
approaches like Octave Allegro [1].
However, existing standards and approaches like the ISO 27000 series or Octave
Allegro referring to or utilizing security requirements are based on events/threats and
probabilities. Threat based approaches face limitations regarding precision and
reliability as they base on probabilities/impact estimates as well as on correct event
identification. Furthermore, these approaches do not determine the risk of non-
adherence or correct implementation of requirements. Other approaches using security
requirements without threats determine best security solutions for processes [2] or
analyse process security [4] but do not determine risks. Approaches that determine
security solutions or analyze process security are limited as they do not evaluate the
security risk of the current implementation. In addition, most risk assessment
approaches omit risks originating from the business process design and data flow as
well as do not consider any security dependencies as the all evaluate single
Page 98 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-105-320.jpg)


![2010 CRC PhD Student Conference
References
[1] Richard Caralli, James Stevens, Lisa Young, and William Wilson. Introducing
OCTAVE Allegro: Improving the Information Security Risk Assessment Process. The
Software Engineering Institute, 2007.
[2] Peter Herrmann and Gaby Herrmann. Security requirement analysis of business
processes. Electron Commerce Research, 6:305– 335, 2006.
[3] International Organization of Standardization (ISO). ISO 27002 Information
technology - Security techniques - Code of practice for information security
management, International Organization of Standardization (ISO), 2005.
[4] Alexander W. Roehm, Guenther Pernul, and Gaby Hermann. Modelling secure
and fair electronic commerce. In Proceeding 14th Annual Computer Security
Applications Conference, Phoenix, Arizona, Dec. 7-11, 1998. IEEE Computer Society
Press, 1998.
[5] Andrew Stewart. On risk: perception and direction. Computers & Security,
23:362–370, 2004.
[6] Lili Sun, Rajendra Srivastava, and Theodore Mock. An information systems
security risk assessment model under Dempster-Shafer theory of belief functions.
Journal of Management Information Systems, 22(4):109 –142, 2006.
[7] Stilianos Vidalis. A critical discussion of risk and threat analysis methods and
methodologies. Technical Report CS-04-03, University of Glamorgan, Pontypridd,
2004.
Page 101 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-108-320.jpg)
![2010 CRC PhD Student Conference
Distilling Privacy Requirements for Mobile Applications
Keerthi Thomas
k.thomas@open.ac.uk
Supervisors Prof. Bashar Nuseibeh
Dr. Arosha Bandara
Mr. Blaine Price
Department/Institute Computing
Status Part-time
Probation viva After
Starting date Oct. 2008
As mobile computing applications become commonplace, eliciting and analysing users’
privacy requirements associated with these applications is increasingly important. Such
mobile privacy requirements are closely linked to both the physical and socio-cultural context
in which the applications are used.
Previous research by Adams and Sasse [1] has highlighted how system designers, policy
makers and organisations can easily become isolated from end-users’ perceptions of privacy
in different contexts. For mobile applications, end-users’ context changes frequently and
Mancini et al.’s observations of such users [2] suggest that changes in users’ context result in
changes in the users’ privacy requirements. Omitting these privacy requirements not only
affects the user’s privacy but also has an impact on how well the system is adopted or utilised.
Moreover, the design of technologies influencing privacy management is often considered
and addressed as an afterthought [3], when in fact the guarantees and assurances of privacy
should have been included in the design right from the outset. The aim of my research is
therefore to ensure that privacy requirements of mobile systems are captured early, together
with the specification of the possible variations in these systems’ operating context.
Privacy requirements have been analysed from different perspectives by the requirements
engineering community. Anton et al. [4] explored the role of policy and stakeholder privacy
values, Breaux and Anton [5] modelled requirements based on privacy laws such as HIPAA,
and Cranor et al. [6] represented her requirements using privacy policies of various online
organisations. Some researchers have modelled privacy as part of a wider modelling effort.
For example, Yu and Cysneiros [7] characterised privacy as a non-functional requirement in
i* using OECD guidelines [8], and Kalloniatis et al. [9] described a security engineering
method to incorporate privacy requirements early in the system development process.
However, I am not aware of any work that specifically focuses on the challenges of
understanding the privacy requirements associated with mobile computing applications.
Eliciting end-user privacy requirements for mobile applications is both sensitive and
difficult. Questionnaires do not reveal the ‘real’ choices end-users make because the decisions
are influenced by the emerging context in a particular situation. Shadowing users for long
hours is neither practical nor useful as the experience of being under observation is likely to
change the behaviour of the users in ways that invalidate any observed behaviours that relate
to privacy. Mancini et al.’s prior work [2] showed that privacy preferences and behaviours in
relation to mobile applications are closely linked to socio-cultural, as well as to physical,
boundaries that separate different contexts in which the applications are used. From the
literature survey carried out earlier, I am not aware of any requirements engineering process
that specifically supported the elicitation of privacy requirements for mobile or context-aware
systems. Given the complexities and the need to elicit privacy requirements for mobile
systems, the aim of my research is therefore to address the following questions:
Page 102 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-109-320.jpg)
![2010 CRC PhD Student Conference
(i) What are the end-user privacy requirements for mobile applications?
(ii) How can privacy requirements be elicited for mobile applications? What elicitation
techniques, requirement models and analysis methods are needed in the privacy
requirements engineering process?
To address these research questions, I present a systematic approach to modelling privacy
requirements for mobile computing applications where I demonstrate how requirements are
derived (“distilled”) from raw empirical data gathered from studying users of mobile social
networking applications. I propose the use of a user-centric privacy requirements model that
combines relevant contextual information with the users’ interaction and privacy perceptions
of the mobile application. The development of this model was informed by empirical data
gathered from my previous studies of mobile privacy [2]. Finally, I validate my work by using
the model as the basis for extending existing requirements modelling approaches, such as
Problem Frames. I show how the extended Problem Frames approach can be applied to
capture and analyse privacy requirements for mobile social networking applications.
References
[1] Adams, A. and Sasse, M.A., Privacy issues in ubiquitous multimedia environments: Wake sleeping
dogs, or let them lie? in Proc. of INTERACT ’99, Edinburgh, 1999, pp. 214-221J.
[2] Mancini, C., et al., From spaces to places: emerging contexts in mobile privacy. in Proc. of the
11th Int, Conf. on Ubiquitous computing, Orlando, FL, 2009, pp. 1-10.
[3] Anton, A.I. and Earp, J.B., Strategies for Developing Policies and Requirements for Secure
Electronic Commerce Systems. in 1st ACM Workshop on Security and Privacy in E-Commerce,
Athens, Greece, 2000, pp. unnumbered pages.
[4] Anton, A.I., Earp, J.B., Alspaugh, T.A., and Potts, C., The Role of Policy and Stakeholder Privacy
Values in Requirements Engineering. in Proc. of the 5th IEEE Int. Symp, on Requirements
Engineering, 2001, pp.138.
[5] Breaux, T.D. and Anton, A.I., Mining rule semantics to understand legislative compliance. in Proc.
of the 2005 ACM workshop on Privacy in the electronic society, Alexandria, VA, USA, 2005, pp.
51 - 54
[6] Cranor, L.F., 1998. The platform for privacy preferences. Communications of ACM 42 (2), 48–55.
[7] Yu, E. and L.M. Cysneiros. Designing for Privacy and Other Competing Requirements. in 2nd
Symp. on Requirements Engineering for Information Security (SREIS'02). 2002. Raleigh, North
Carolina.
[8] “Inventory of instruments and mechanisms contributing to the implementation and enforcement of
the OCDE privacy guidelines on global networks” Head of Publications Services, OECD, 2 rue-
André-Pascal, 75775 Paris Cedex 16, France.
[9] Kalloniatis, C., Kavakli, E., and Gritzalis, S. Addressing privacy requirements in system design:
the PriS method Requirements Engineering, Springer London, 13 (3). pp. 241-255.
Page 103 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-110-320.jpg)
![2010 CRC PhD Student Conference
Understanding the Influence of 3D Virtual Worlds on Perceptions of
2D E-commerce Websites
Minh Q. Tran
Centre for Research in Computing
The Open University
m.tran@open.ac.uk
Supervisors
Dr. Shailey Minocha Prof. Angus Laing
Centre for Research in Computing Business School
The Open University Loughborough University
s.minocha@open.ac.uk a.w.laing@lboro.ac.uk
Dr. Darren Langdridge Mr. Dave Roberts
Department of Psychology Centre for Research in Computing
The Open University The Open University
d.langdridge@open.ac.uk d.roberts@open.ac.uk
Department: Computing
Status: Full-time
Probation viva: Passed July 2009
Starting date: October 2008
Introduction
The aim of our research is to understand consumers’ experiences in 3D virtual worlds (VWs) and how
those experiences influence consumers' expectations of 2D e-commerce websites. As consumers
become familiar with the affordances and capabilities of 3D VWs, do their expectations of 2D e-
commerce websites change? The outcome of this research project will be an understanding of
consumers’ experiences in 3D VWs and 2D e-commerce websites. Furthermore, design guidelines will
be developed for e-commerce in 3D VWs and for the integration of 3D VWs with 2D e-commerce
websites.
3D Virtual Worlds
3D VWs are online, persistent, multi-user environments where users interact through avatars [2].
Avatars are digital self-representations of users. Through avatars, users can walk in simulated physical
spaces, talk to other avatars and interact with the environment. This opens up different possibilities for
interaction; both in terms of human-computer interaction (HCI) and also business-to-consumer (B2C)
interactions. Users may be able to browse through virtual markets, shop with their friends and interact
in real-time with vendors [10]. These features suggest shopping in 3D VWs may be more immersive
compared to shopping on websites [7].
E-commerce in Second Life
Second Life (SL) is a 3D VW. SL does not cost any money to use. It is also an open-ended platform;
users of SL are encouraged to create their own content and design their own activities. Users can sell
any content (objects, scripts, animations) that they make. Content can also be bought from others. As a
consequence, SL has developed its own virtual economy [6], including having virtual stores to shop
from (Figure 1).
Figure 1. Stores in Second Life.
Page 104 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-111-320.jpg)
![2010 CRC PhD Student Conference
Currently, the economy in SL mainly involves virtual items, such as virtual clothes, avatar models,
homes and land. However, there is potential for real business, involving real world items. Some
companies, such as Coca-Cola and Adidas, have already used SL to advertise their products [12]. As
the popularity of 3D VWs grows, more companies will likely make use of 3D VWs for their e-
commerce beyond marketing and advertising. 3D VWs has the potential to become a platform for
buying and selling real items, just as websites are today. However, successful implementation of e-
commerce in 3D VWs will require an understanding of what influences the user experience [11].
Research Objectives
The goal of this research is to investigate affordances of 3D VWs and their influence on consumer’s
perceptions and expectations of 2D e-commerce websites. This understanding will be used to develop
guidelines for designing positive e-commerce experiences in 3D VWs and 2D e-commerce websites.
The research questions are:
RQ1: What are consumers’ experiences in 3D VWs?
RQ2: What are consumers’ perceptions and expectations of 2D e-commerce websites who
have experience in VWs?
RQ3: What are the differences in expectations and behaviours between consumers in 3D VWs
and 2D e-commerce websites?
Online Service Encounter
Consumers’ experiences are based on what occurs during the service encounter. The service encounter
refers to all interactions between a consumer and a service provider for the exchange of a product or
provision of a service. According to the service encounter model, a full understanding of the experience
involves looking at what happens before, during and after a purchase (Figure 1).
Figure 2. Model of the service encounter [3].
Furthermore, consumers now have the option between different commerce channels (websites, high
street, telephone, etc.). Therefore, consumers’ experiences are not based only on the performance of
individual channels, but also how well the channels are integrated to provide a positive and seamless
experience. This research focuses on two commerce channels in particular, 3D VWs and 2D websites.
Affordances of 3D VWs
3D VWs support the service encounter in different ways compared to 2D websites. For example,
having products rendered in 3D can improve product ‘diagnosticity’ [8]. Diagnosticity refers to how
easily a consumer can judge a product to fit their needs. An interactive 3D model of products gives
users more information about its form and function. Therefore, users may be able to make informed
purchase decisions when shopping in VWs because they have a better idea of what the product is like.
Another advantage is the multi-user and synchronous environment. VWs produce the sense ‘being
there’, also referred to as ‘presence’ [13]. A sense of ‘being there’ with others is also possible because
avatars are located in the same virtual space; users can ‘see’ each other. As a result, the e-commerce
experience has a social dimension that is not experienced when shopping on websites.
Affordances of 2D Websites
Websites have their own advantages that VWs do not. Presently, websites can provide more
information compared to VWs as they use text effectively [5]. The advantage of text is that it can
describe many details about a product, such as specifications and warranties, which cannot be easily
conveyed through images or 3D models. The web also has the advantage of being faster than 3D VWs
because of its low bandwidth and CPU requirements.
Page 105 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-112-320.jpg)
![2010 CRC PhD Student Conference
Methodology
The methodology of this research project is empirical and qualitative. Three studies involving users are
planned (Figure 3). The first two studies are based on in-depth interviews. The interviews will be
conducted in SL. During the interviews, participants are encouraged to describe their own shopping
experiences in detail and from their own subjective viewpoint. The interview technique is based on
phenomenology [4]. Phenomenological interviews, and subsequent phenomenological analysis, allow
the researcher to obtain the structure and content of experience. During the interviews, each participant
is asked to describe the pre-purchase, purchase and post-purchase interactions from a service encounter.
The data consists of descriptions of shopping experiences, including behaviours, thoughts and feelings.
For this project, data analysis includes both descriptive phenomenological analysis [4] and a general
thematic analysis [1]. A descriptive phenomenological analysis of each interview produces use cases
(or individually structured narratives). Thematic analysis produces a set of themes relating to
affordances and user experience. The use cases and themes provide grounding to reason about design
implications and design guidelines. Design guidelines will be validated through a third study. The
guidelines will be evaluated by users who have experience creating content in 3D VWs and websites.
Part of the validation study will involve making the guidelines usable for the intended audience of
designers and marketers.
Figure 3. Project methodology
Preliminary Findings
The first study is now complete. A list of themes based on affordances and use cases are being
compiled. The aim is to provide a comprehensive list of affordances in 3D VWs for designers to think
about when designing e-commerce systems. The long-term goal is to provide guidance on how to best
use these affordances to create positive experiences. Some affordances identified so far are the ability
to:
• navigate through 3D environments facilitated by the spatial metaphor in a 3D VW
• browse pre-arranged displays similar to a real-world store
• interact with others in real-time as avatars
• blend the 3D virtual world experience with 2D websites
Through further analysis, a set of use qualities and their design implications will be derived. Use
qualities relate to emotional aspects (sensations, feelings, meaning-making) [9]. For example, some use
qualities that characterize the 3D virtual world experience are:
Page 106 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-113-320.jpg)









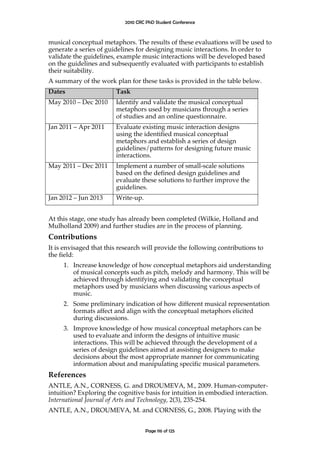

![2010 CRC PhD Student Conference
Issues and techniques for collaborative music making
on multi-touch surfaces
Anna Xambó
a.xambo@open.ac.uk
Supervisors Robin Laney
Department/Institute Department of Computing
Status Visiting research student (4 months)
Probation viva -
Starting date -
A range of applications exist for collaborative music making on multi-touch
surfaces. Some of them have been highly successful, but currently there is no
systematic way of designing them, to maximize collaboration for a particular
user group. We are specially interested in applications that will engage
novices and experts. Traditionally the challenge in collaborative music
instruments is to satisfy the needs of both [1]. For that purpose, we developed
a collaborative music making prototype for multi-touch surfaces and evaluated
its creative engagement.
Applications for musical multi-touch surfaces are not new. A pioneering work
is the ReacTable [2, 3], which allows a group of people to share control of a
modular synthesizer by manipulating physical objects on a round table. Iwai’s
Composition on the Table [4] allows users to create music and visuals by
interacting with four tables which display switches, dials, turntables and
sliders. Stereotronic Multi-Synth Orchestra [5] uses a multi-touch interface
based on a concentric sequencer where notes can be placed. What is less
addressed is the evaluation of creative engagement in these applications.
There are numerous theoretical accounts of the nature of emotional
engagements with art and artefacts. Current models are based on a
pragmatist view, which conceptualises the aesthetic and affective value of an
object as lying not in the object itself, but in an individual’s or a group’s rich
set of interactions with it [6, 7]. In the context of pleasurable creative
engagement and the collective composition of music, Bryan-Kinns et al. [8]
see attunement to others’ contributions as the central principle of creative
engagement. The phenomena of personal full immersion in an activity, also
known as ’fow’ [7], has been extended to groups as means of heightening
group productivity [9].
Our approach is, frst, to study the issues and techniques of multi-user
instruments and multi-touch applications in general, second, to design a
simple application in an initial attempt to clearly analyse some of these issues,
and third, to evaluate its creative engagement. For that purpose, a prototype
was built which allowed groups of up to four users to express themselves in
collaborative music making using pre-composed materials. By
keeping the prototype minimal, we were able to investigate the essential
aspects of engaging interaction.
Case studies were video recorded and analysed using two techniques derived
from Grounded Theory (GT) and Content Analysis (CA). For the GT, which is
a qualitative research method employed in the social sciences that derives
theoretical explanations from the data without having hypotheses in mind [10],
we adopted an open coding strategy of identifying key moments of the video
Page 118 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-125-320.jpg)
![2010 CRC PhD Student Conference
interactions; grouping the codes by concepts and generating general
explanations from the categorization of the concepts. Given that this approach
is based on creative interpretation, we added more evidence by
complementing GT with CA. Content Analysis (CA) is defned by Holsti (1969)
as ”any technique for making inferences by objectively and systematically
identifying specifed characteristics of messages” [10]. This defnition includes
content analysis of text, videos, music or drawings. There are varied
approaches to CA using quantitative, qualitative or both techniques. Our
approach is derived from ethnographic content analysis or qualitative content
analysis [11], an approach to documents that emphasises the role of the
investigator in the construction of the meaning of texts. We took same steps
as in the open coding, but in the frst step we used instead structured codes to
help us identify key points of the video-recorded interactions.
The case study protocol was the following: The users were expected to
perform three musical tasks of different character as well as an informal
discussion in order to generate suffcient data to analyse several aspects of
behaviours using the prototype. A questionnaire was also conducted and
evaluated. The main focus of the analysis was on the evaluation of the
collaborative interactions enabled by the prototype. The questions we wanted
to address were:
1. What were the modes participants found to collaborate with one
another;
2. What were the diffculties that participants encountered and the extent
to which they found the exercise engaging;
3. What was the degree of satisfaction at the end result.
From transcription of the video speech and behaviours, and then the process
of open coding, we identifed the following concepts: collaboration, musical
aesthetics, learning process and system design. After that, we analysed the
same data using the nomenclature chosen from two existing theoretical
frameworks. The frst one is a general framework of tangible social interaction
which includes the concepts of tangible manipulation, spatial interaction,
embodied facilitation or expressive representation [12]. The second one is
focused on the engagement between participants in music collaboration,
which considers the following features: mutual awareness, shared and
consistent representations, mutual modifability and annotation [8]. We found
that some of the content analysed was already discussed in the open coding
process, which provides consistency. Data was also collected using a
questionnaire, which was designed to probe such issues as how aware each
participant had been of other instruments; the diffculty of the tasks, and how
much they felt they had enjoyed and concentrated on them; and the extent to
which they considered they had operated as a team and felt part of a
collaborative process. Responses were recorded using numerical scores, but
the questionnaire also asked for qualitative feedback on how participants
organised themselves as a group and the nature of any rules they created.
We also recorded anonymously the participants age, gender, previous
experience, love of music, and the instrument they had been allocated on the
table.
Within a user-centered design approach of active participation of users in the
process of designing the prototype, the most prominent aspects that have
emerged as enhancements of multi-touch applications in music collaboration
are:
• Responsiveness. The responsiveness determines the perceived
emotiveness. This parameter should be adequately related to the
Page 119 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-126-320.jpg)
![2010 CRC PhD Student Conference
application performance in terms of time and computer resources used.
A consistent audiovisual feedback will enhance the perceived response
of the application.
• Shared vs. individual controls. Both shared and individual spaces are
needed. Shared features would strength mutual awareness and mutual
modifability. Individual spaces would strength personal opinion,
musical identity and musical expression.
The fndings of this study help us understand engagement in music
collaboration. Qualitative video analysis and the questionnaires provide
indication of participants having mutual engaging interaction in terms of being
engaged with the music collaboratively produced and also being engaged with
others in the activity. High degree of satisfaction at the end result is evidenced
mostly by the gestural mode. The evidence found of participants exchanging
ideas constantly indicates that the prototype strongly facilitates conversation,
which, as noted earlier, is important in terms of group productivity.
In the future, we are interested in how many, and what type of, affordances
such applications should offer in order to maximise engagement. We are also
interested in validating our evaluation method. To that end, there is scope to
improve the responsiveness of the prototype and to redesign the distribution
of shared and individual controls. Furthermore, there is a plan to add
individual continuous controls for sound parameter modifcations in order to
encourage a process-oriented composition. The mutual experience might be
enhanced and collaboration deepened, by adding common controls, as well. A
balance between adding more features and keeping simplicity must be kept in
order to attract both novices and experts alike.
[1] T. Blaine and S. Fels, “Collaborative musical experiences for novices,”
Journal of New Music Research, vol. 32, no. 4, pp. 411–428, 2003.
[2] S. Jordà, M. Kaltenbrunner, G. Geiger, and R. Bencina, “The reacTable*,”
in Proceedings of the International Computer Music Conference (ICMC 2005),
(Barcelona, Spain), 2005.
[3] S. Jordà, G. Geiger, M. Alonso, and M. Kaltenbrunner, “The reacTable:
Exploring the synergy between live music performance and tabletop tangible
interfaces,” in TEI ’07: Proceedings of the 1st international conference on
Tangible and embedded interaction, (New York, NY, USA), pp. 139–146, ACM,
2007.
[4] T. Iwai, “Composition on the table,” in International Conference on
Computer Graphics and Interactive Techniques, SIGGRAPH: ACM Special
Interest Group on Computer Graphics and Interactive Techniques, ACM,
1999.
[5] http://www.fashionbuddha.com/, 15/3/2010.
[6] M. Blythe and M. Hassenzahl, The semantics of fun: differentiating
enjoyable experiences, pp. 91–100. Norwell, MA, USA: Kluwer Academic
Publishers, 2004.
[7] M. Csikszentmihalyi, Beyond Boredom and Anxiety: Experiencing Flow in
Work and Play. Jossey-Bass, 1975.
Page 120 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-127-320.jpg)
![2010 CRC PhD Student Conference
[8] N. Bryan-Kinns and F. Hamilton, “Identifying mutual engagement,”
Behaviour and Information Technology, 2009.
[9] K. Sawyer, Group Genius: The Creative Power of Collaboration. Basic
Books, 2007.
[10] J. Lazar, J. Feng, and H. Hochheiser, Research Methods in Human-
Computer Interaction. Wiley, 2010.
[11] D. L. Altheide, “Ethnographic content analysis,” Qualitative Sociology, vol.
10, pp. 65–77, 1987.
[12] E. Hornecker and J. Buur, “Getting a grip on tangible interaction: A
framework on physical space and social interaction,” in CHI ’06: Proceedings
of the SIGCHI conference on Human Factors in computing systems, (New
York, NY, USA), pp. 437–446, ACM Press, 2006.
Page 121 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-128-320.jpg)
![2010 CRC PhD Student Conference
A Release Planning Model to Handle Security
Requirements
Saad Bin Saleem
Center of Research in Computing, Open University
s.b.saleem@open.ac.uk
Basic information
Supervisors: Dr. Charles Haley
Dr. Yijun Yu
Professor Bashar Nuseibeh
Professor Anne De Roeck
Department: Computing
Status: Full-time Research Student
Probation Viva: Probably in November, 2010
Starting Date: Joined OU at 1st February 2010
Background
Nowadays usage of computer technology is growing rapidly and almost everybody in the world is
depending on computer systems [1]. More and more people and organizations are using computer
systems to process, store and manage their highly sensitive data [2]. Any loss, theft and alteration of
this data from computer systems can cause a serious incident, which may consequently cause to
human disasters. Therefore, proper security of computer systems is very important to avoid any kind
of unlikely events.
Software is an important component of any computer system and a software security failure can cause
malfunction of overall system [1]. It is reported by many scientists and engineers that software
security related problems are increasing over the years and secure software development is still a
challenging area for software community [3, 4].
For the development of secure software, an early inclusion of security concerns in the Software
Development Life Cycle (SDLC) is suggested by many researchers [1, 4]. They consider that it will be
very helpful to improve overall software security and can be useful to solve common security threats
at design and architecture level [1, 4]. For this purpose, understanding of security requirements at
early stages of SDLC is very important, as security requirements are ignored in most of the cases [5,
6]. It is also considered that software security is much related to confidentiality, availability and
integrity [7]. But in some cases security is much more than that and depends on many other constraints
like stakeholders, etc [6, 7]. To elicit all kinds of security requirements, a systematic procedure named
Security Requirements Engineering (SRE) is suggested in the literature [5]. This process insures that
elicited security requirements should be complete, consistent and easy to understand [5].
A Requirement Engineering (RE) process consists of many stages from elicitation to requirements
validation and Release Planning (RP). RP is considered an important phase of RE in bespoke and
market driven software development. RP is divided into two major subtypes named as strategic RP
and operational RP [9, 12]. The idea of selecting an optimum set of features or requirements to deliver
in a release is called strategic RP or road-mapping and it is performed at product level [9, 10]. On the
other hand allocation of resources for realization of a product is called operational RP and performed
to decide when a product release should be delivered [10].
In the RP process, it is a common phenomenon to select as much functional requirements or features
in a release and deliver to customer or market as soon as possible [11]. In this way, there is a chance
Page 122 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-129-320.jpg)
![2010 CRC PhD Student Conference
to compromise some quality requirements in general and security requirements in particular which
consequently lead to compromise with many threats to software [15]. Some existing models of RP
deals with quality requirements as technical constraints in general (hard constraints) but not
specifically consider these requirements for prioritization with other functional requirements [11, 12, 9
and 15]. Therefore, identifying and fixing any security concerns during selection of requirements for a
release, and before deciding time to delivery, can make software less prone to security failures. It can
also help in delivering incremental security as organizations cannot hundred percent claim about the
security of software product and always need to improve further.
Based on the above discussion, it is observed that security requirements needs to be consider in RP for
better product strategies and delivery of secure software to customer. So, there is a need to align
security requirements with RP by developing a model which treats security requirements separately
for strategic and operational RP to release secure software
Current research in SRE is aiming to improve existing methods to elicit, analyze, specify, validate and
manage security requirements [3, 13]. Like Charles et al have proposed a framework for eliciting
security requirements and highlighted some further research directions in the area [3]. Similarly in
RP, Ruhe et al have extended the existing approach Evolve+ with three parameters (time dependent
value functions, flexible release dates, and adjusted time dependent resource capacities) for more
improved planning. Saad & Usman had identified the need to improve existing models of RP
according to the needs of Industry [8].
So, this study will contribute in the SRE & RP research, as purpose of this study is to develop a model
which treats security requirements in conjunction with functional requirement for strategic and
operational RP. The research will be conducted in three phases. In first phase, impact of security
requirements on strategic and operational RP will be analyzed. In second phase of research a model
will be developed based on the results of first phase. In third phase, the developed model will be
validated to verify model’s effectiveness.
Research Questions
Following are preliminary research questions based on the purpose of study.
RQ1. What existing practices are in the literature to deal security requirements for strategic and
operational RP?
RQ2. What are implications of security requirements on strategic and operational RP as compare to
functional requirements and/or other quality requirements?
RQ3. Which is an appropriate mechanism for developing a model to treat security requirements
as separate requirements instead constraints for prioritization of functional requirements?
RQ4. What kind of other constraints the model should consider for developing strategic and
operational RP?
RQ5. To what extent the proposed model is effective?
Research Methodology
Qualitative and quantitative research methodologies will be selected to conduct the research in two
different stages [14]. The literature review and Industrial Interviews will be used as strategies of
inquiry in first stage of research. For example, literature review will be used to know existing practices
to deal security requirements during strategic and operational RP, to analyze existing models of
strategic and operational RP and to identify any constraints that should be consider for strategic and
operational RP based on security and all other kinds of requirements. Similarly, industrial interviews
will be used beside with literature review to know any implications of security requirements on
strategic and operational RP. In second stage of research, Industrial Interviews and experiments will
be adopted as strategies of inquiry to validate the model’s functionality.
Page 123 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-130-320.jpg)
![2010 CRC PhD Student Conference
References
[1] Mc-Graw, G “Software Security”, IEEE Computer Society (Privacy and Security), 2004
[2] C. Irvine, T. Levin, J. Wilson, D. Shifflet, & B. Peireira, “An Approach to Security Requirements
Engineering for a High Assurance System”, Journal of Requirements Engineering Journal, Vol. 7,
No. 4, pp.192-206, 2002
[3] Haley, B. C., Laney, R., Moffett, J., Nuseibeh, B., "Security Requirements Engineering: A
Framework for Representation and Analysis," IEEE Transactions on Software Engineering, vol.34,
no.1, pp.133-153, 2008
[4] Hassan, R., Bohner, S., and El-Kassas, S., “Formal Derivation of Security Design Specifications
From Security Requirements”, In Proceedings of the 4th Annual Workshop on Cyber Security and
information intelligence Research: Developing Strategies To Meet the Cyber Security and information
intelligence Challenges Ahead, pp.1-3, 2008
[5] Mellado, D., Fernández-Medina, E., & Piattini, M., “Applying a Security Requirements
Engineering Process”, Computer Security–ESORICS, Springer, pp. 192-206, 2006
[6] B. H. Cheng and J. M. Atlee, "Research Directions in Requirements Engineering," Future of
Software Engineering, (FOSE07), pp. 285-303, 2007
[7] A. Avizienis, J. C. Laprie, B. Randell, and C. Landwehr, "Basic Concepts and Taxonomy of
Dependable and Secure Computing," IEEE Transactions on Dependable and Secure Computing,
vol. 1, no. 1, pp. 11-33, 2004
[8] Saleem, B. S., Shafique. M.U., “A Study on Strategic Release Planning Models of Academia &
Industry”, Master Thesis, Blekinge Institute of Technology, Sweden, pp.1-81, 2008
[9] Al-Emran, A., Pfahl, D., “Operational Planning, Re-planning and Risk Analysis for Software
Releases”, Proceedings of the 8th International Conference on Product Focused Software Process
Improvement (PROFES), pp. 315-329, 2007
[10] Ruhe, G., Momoh, J., "Strategic Release Planning and Evaluation of Operational Feasibility, "In
Proceedings of the 38th Annual Hawaii International Conference on System Sciences (HICSS), vol.9,
pp. 313b, 2005
[11] Tondel, I.A.; Jaatun, M.G.; Meland, P.H., "Security Requirements for the Rest of Us: A Survey",
IEEE Software, vol.25, no.1, pp.20-27, 2008
[12] Ngo-The, A., and Ruhe, G., “A Systematic Approach for Solving the Wicked Problem of
Software Release Planning”, Soft Comput, vol. 12, no.1, pp. 95-108, 2007
[13] Jing-Song Cui; Da Zhang, "The Research and Application of Security Requirements Analysis
Methodology of Information Systems”, 2nd International Conference on Anti-counterfeiting, Security
and Identification, pp.30-36, 2008
[14] Creswell, W. J., Research Design: Qualitative, Quantitative, and Mixed Method Approaches,
Second Edition, Thousand Oaks: Sage, pp.1-246, 2003
Page 124 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-131-320.jpg)
![2010 CRC PhD Student Conference
[15] Svahnberg, M., Gorschek, Feldt, R., Torkar, R., Saleem, B. S., and Shafique, U. M., “A
systematic review on strategic release planning models,” Information and Software Technology, vol.
52, no.3, pp. 237-248, 2010
[16] Elroy, J., and Ruhe, G., “When-to-release decisions for features with time-dependent value
functions,” To be Appeared in Journal of Requirements Engineering, 2010
Page 125 of 125](https://image.slidesharecdn.com/conferenceproceedings-100528083319-phpapp01/85/CRC-Conference-proceedings-132-320.jpg)