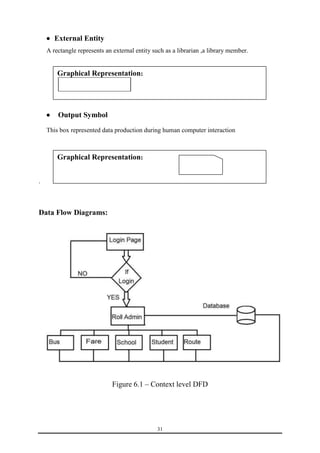
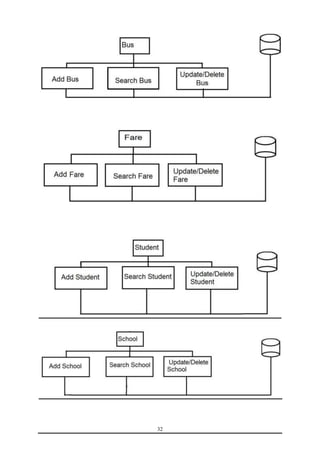
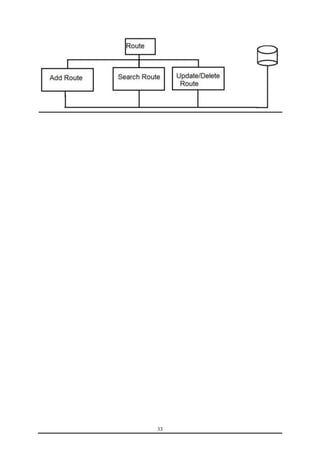
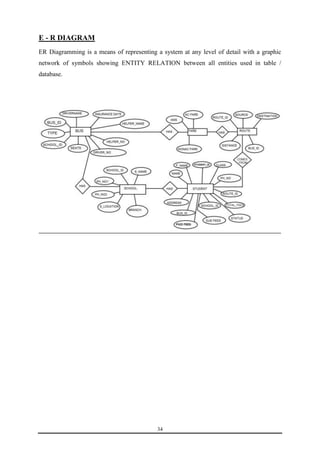
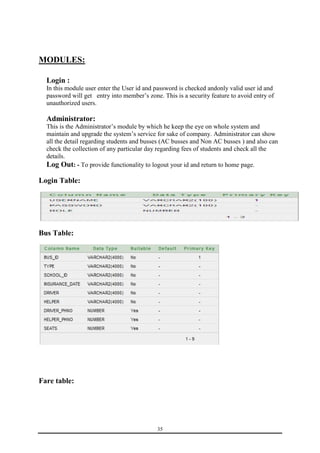
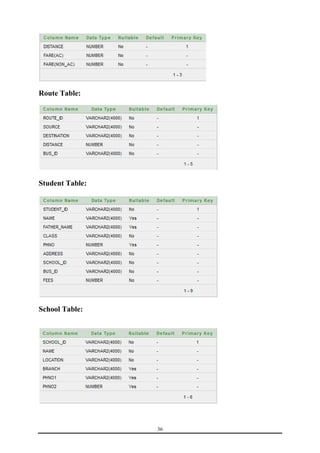
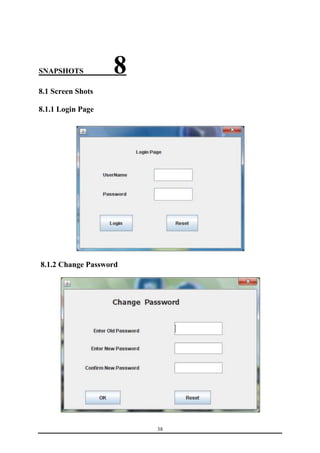
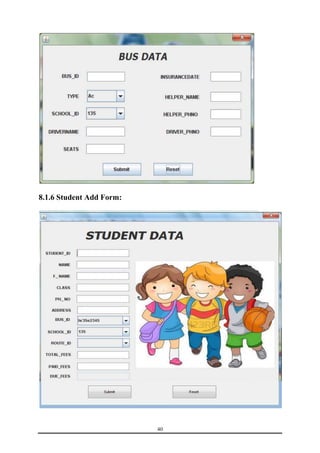
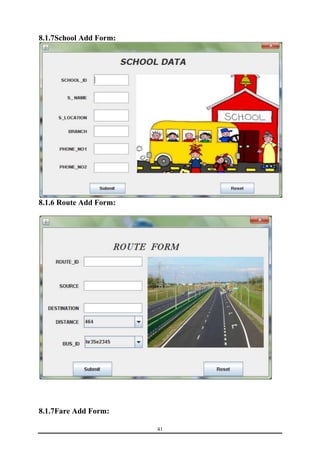
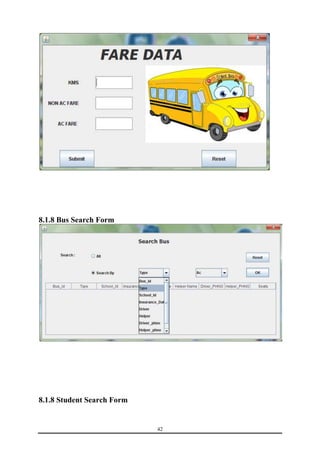
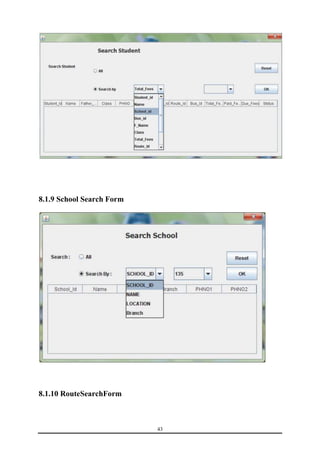
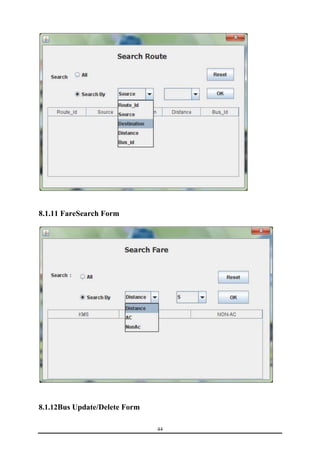
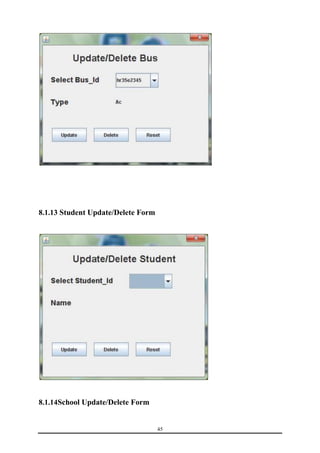
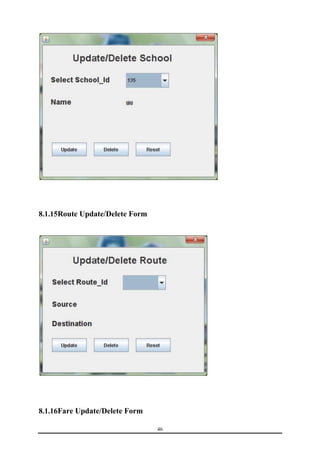
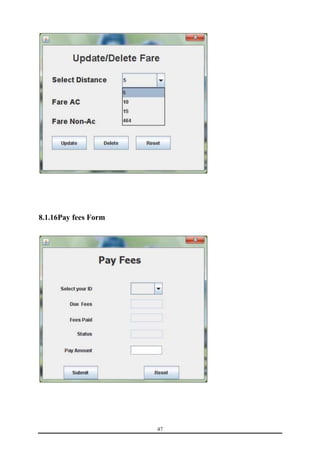
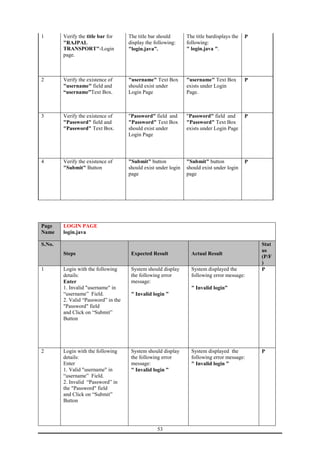
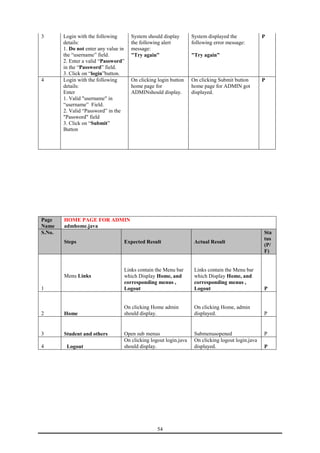
This document is a training report submitted by Sumit Jain to fulfill the requirements for a Bachelor of Technology degree in Computer Science and Engineering. It describes a training project completed at Lio Technologies under the guidance of Mr. Rahul Sharma. The report includes an introduction to the company, objectives of the project, system analysis, feasibility study, software requirements specification, system design, screenshots, testing, implementation, maintenance, security, and conclusions.