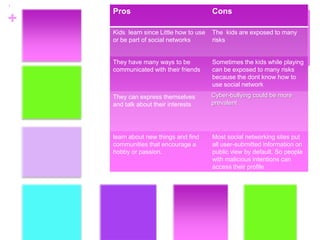
Cyberbullying involves the use of electronic devices and communication tools to bully or harass others. The document outlines some common tactics used by cyberbullies such as pretending to be other people online, spreading lies and rumors, and posting embarrassing pictures without consent. Kids who experience cyberbullying may engage in risky behaviors and have lower self-esteem. The document provides tips for parents to help prevent cyberbullying, such as being aware of their kids' online activities, using privacy settings appropriately, and establishing clear rules for technology use.


![+
The National Crime Prevention Association
lists tactics often used by teen
cyberbullies.[16]
Pretend they are other people online to trick
others
Spread lies and rumors about victims
Trick people into revealing personal
information
Send or forward mean text messages
Post pictures of victims without their consent
Cyberbullying can happen 24 hour 7 days a
week, it can happen any time.](https://image.slidesharecdn.com/converstation-130511235024-phpapp01/85/Converstation-3-320.jpg)