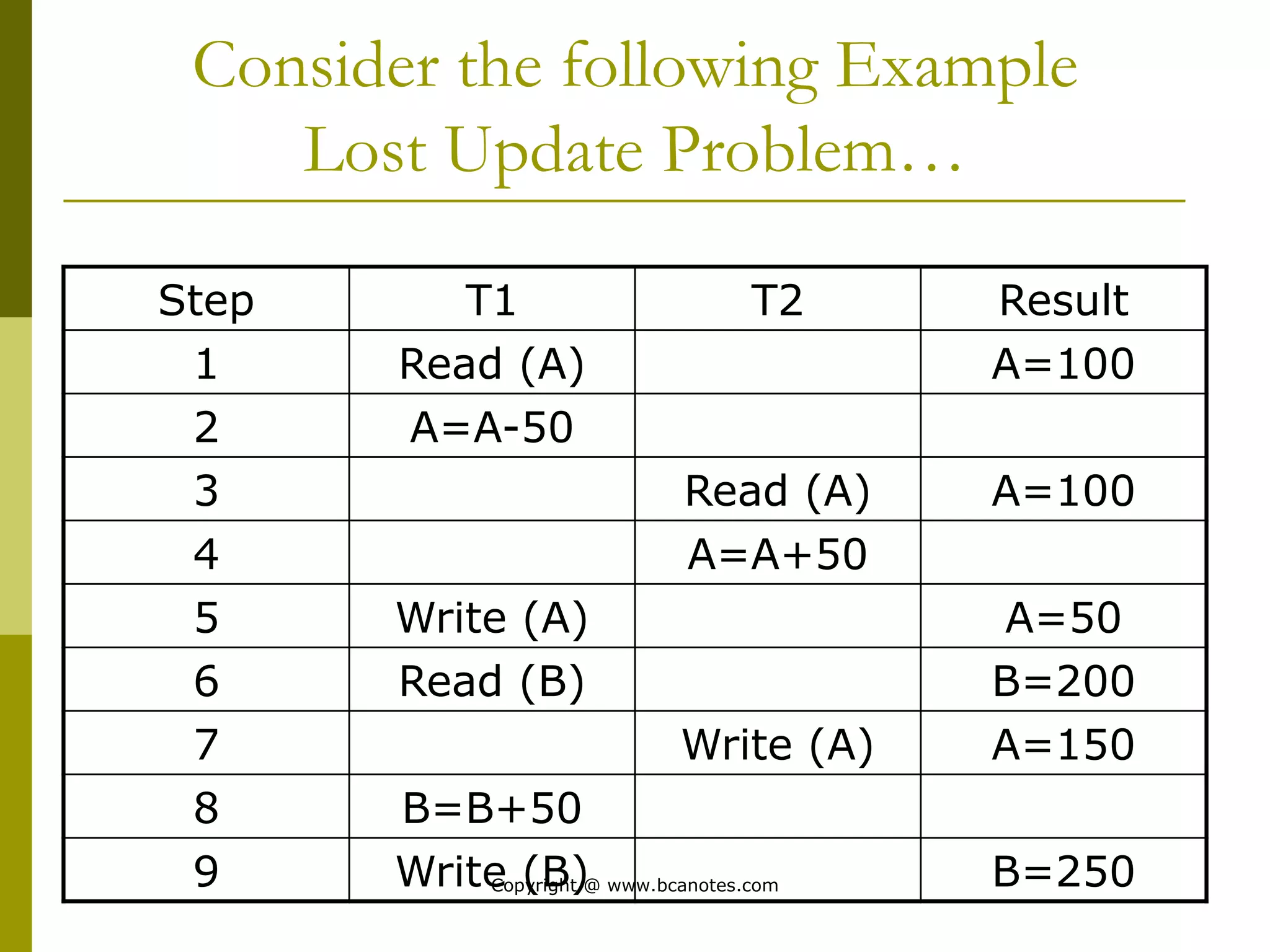
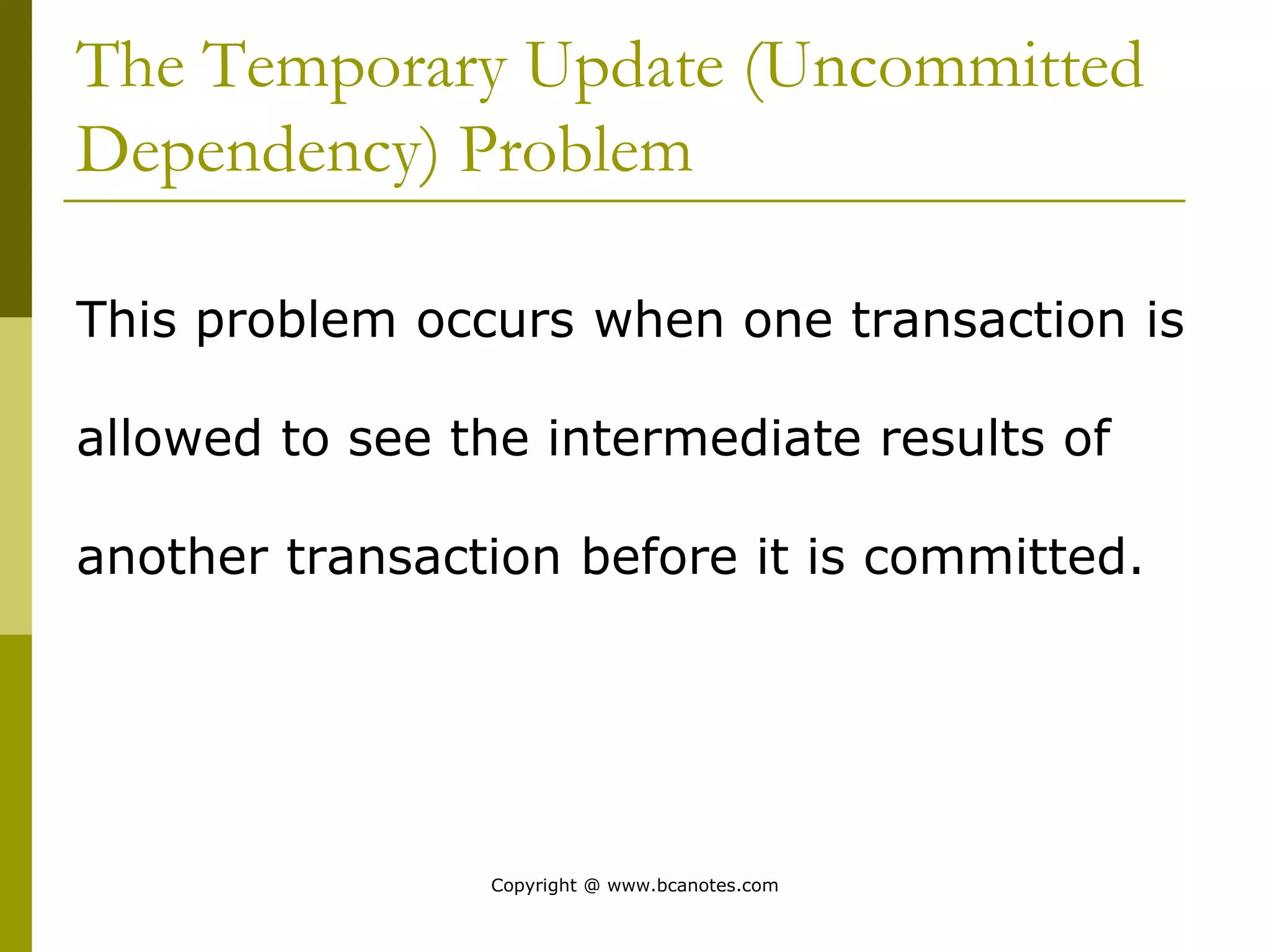
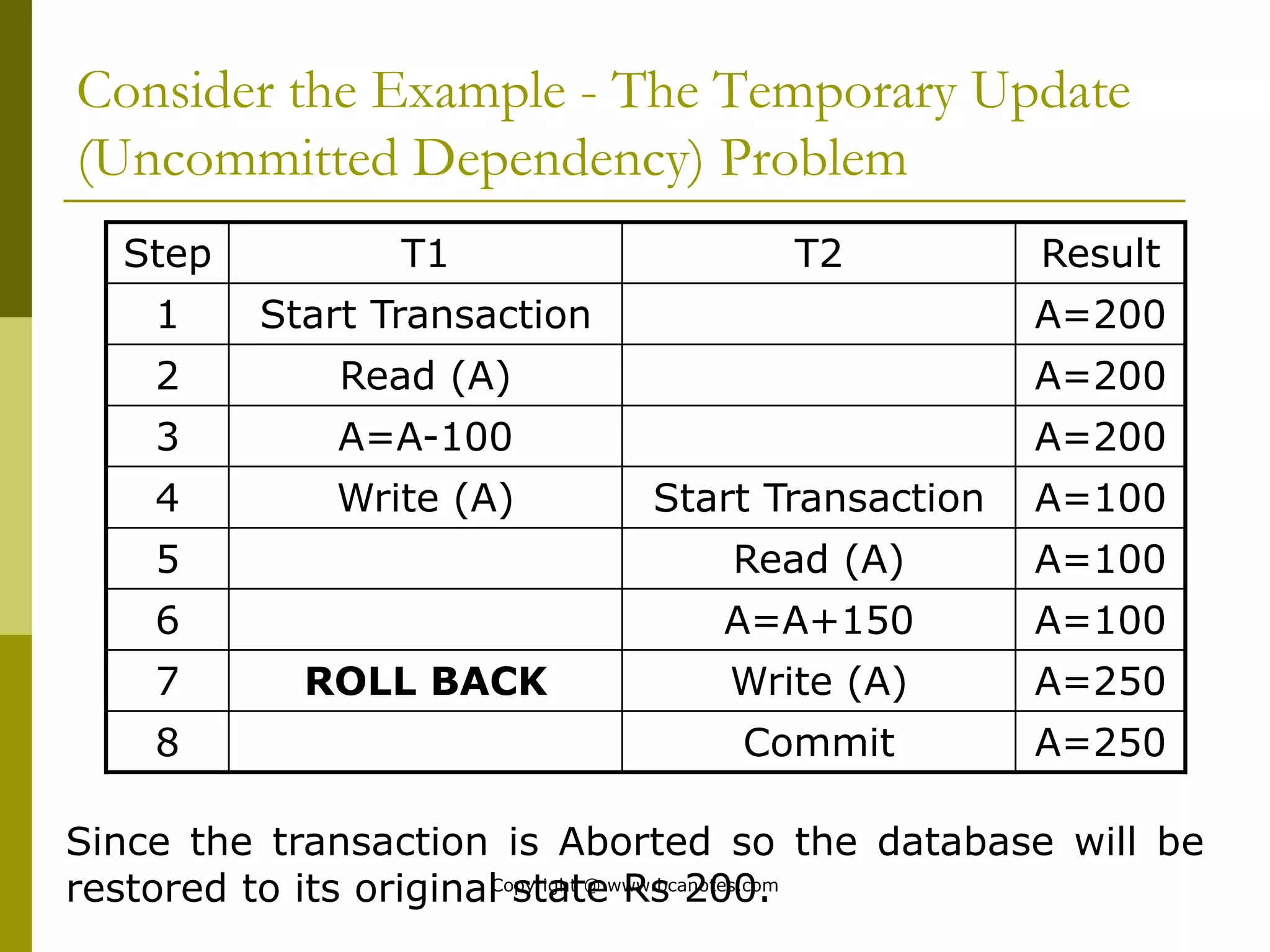
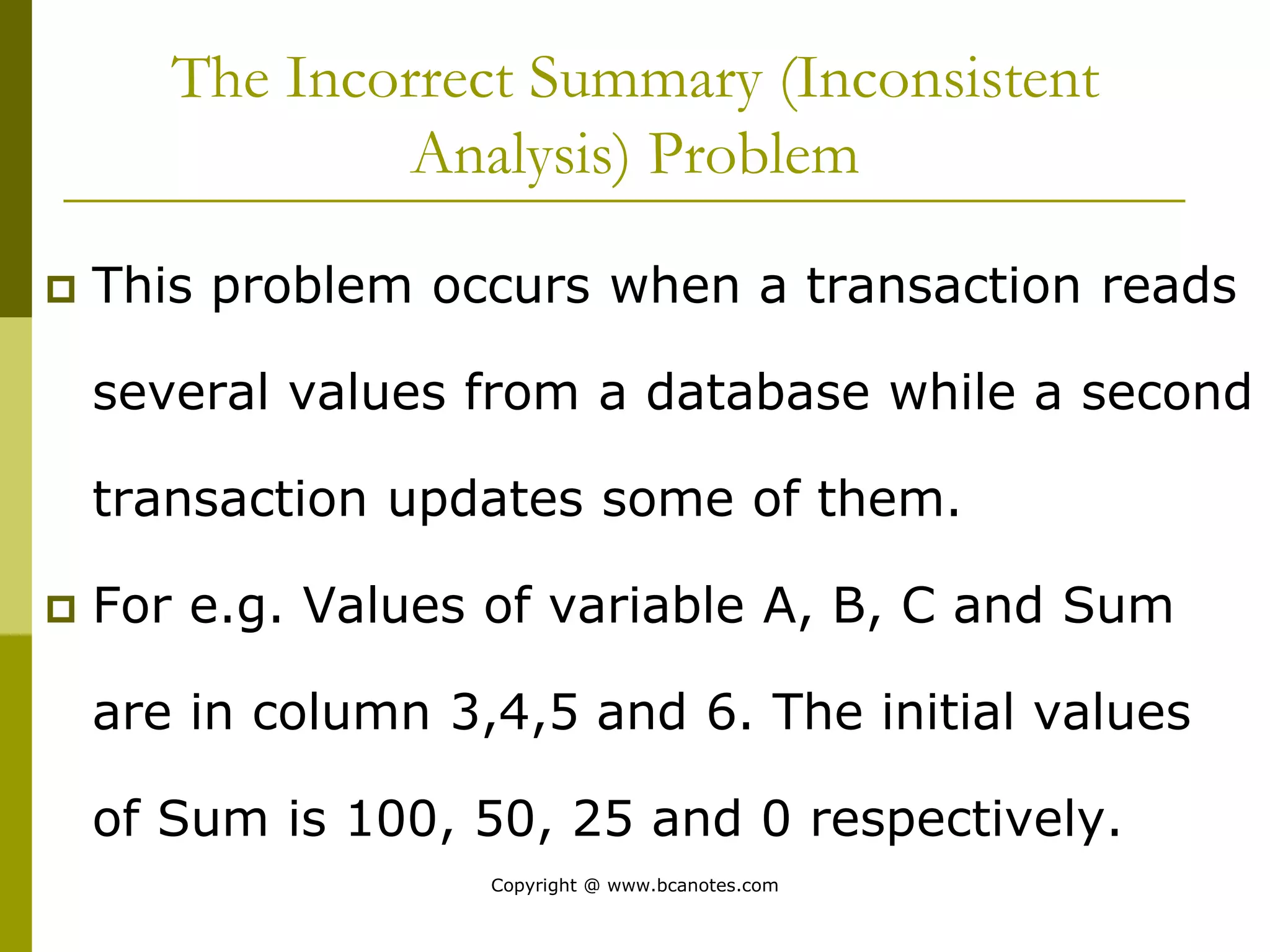
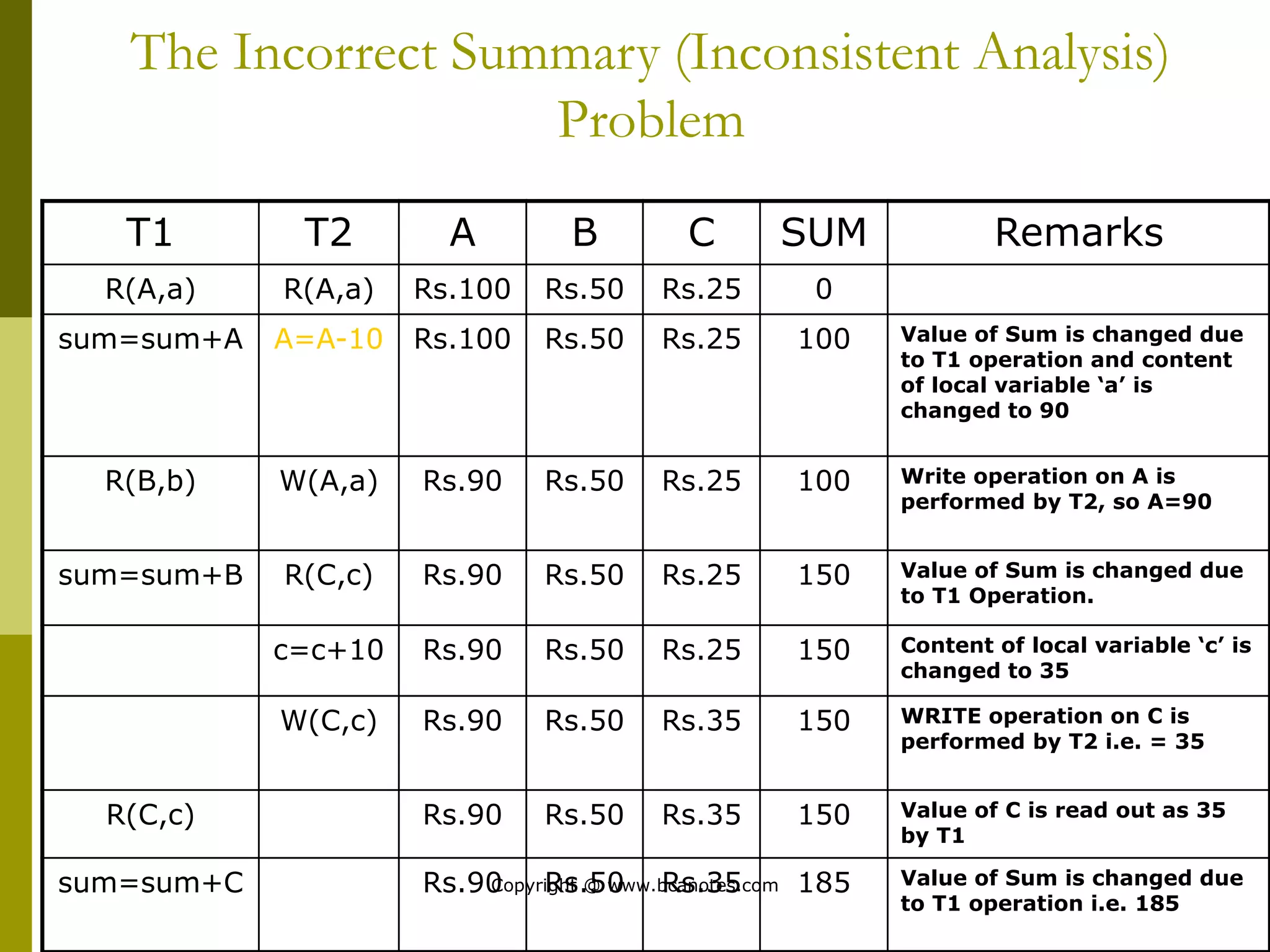
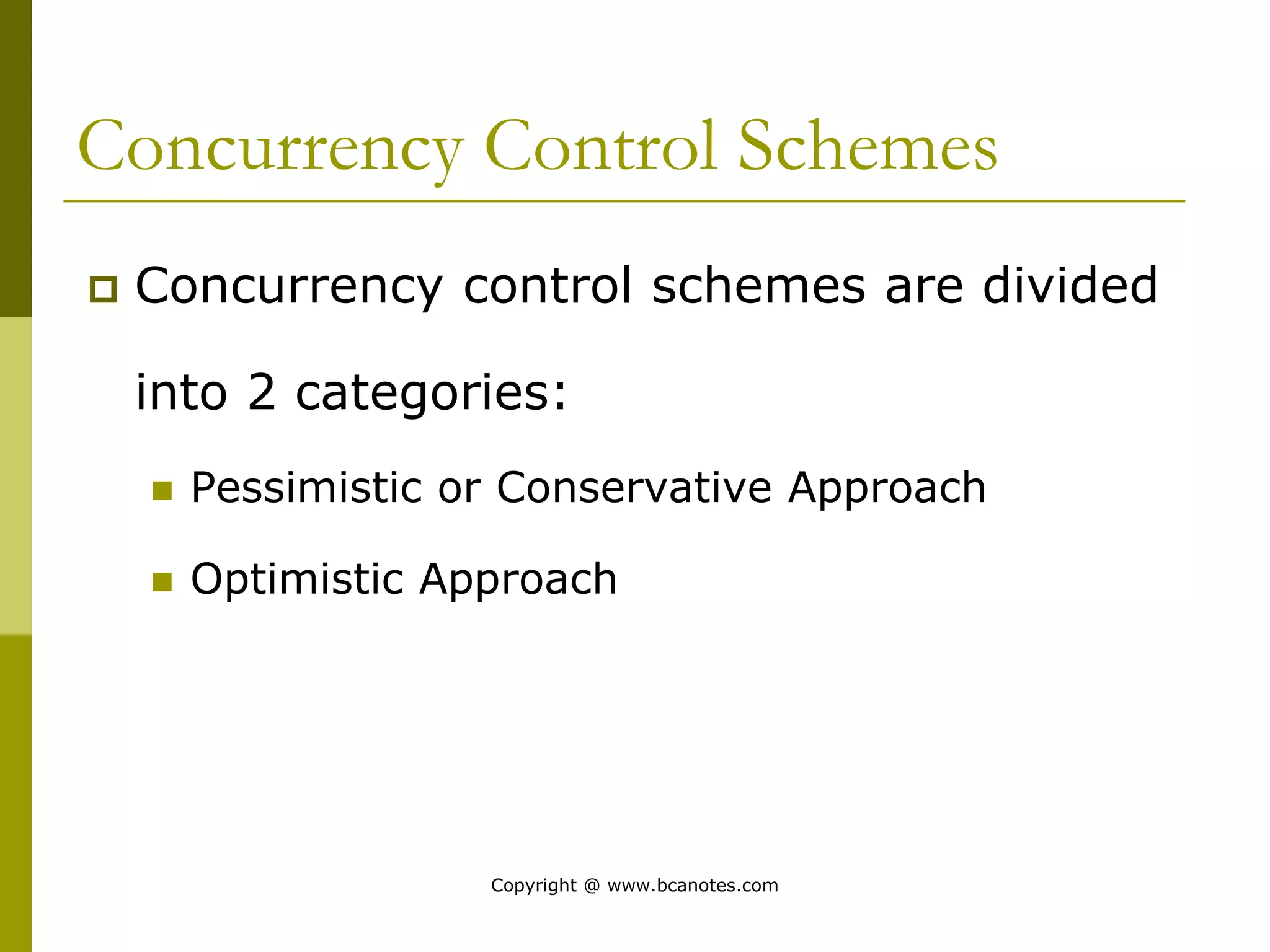
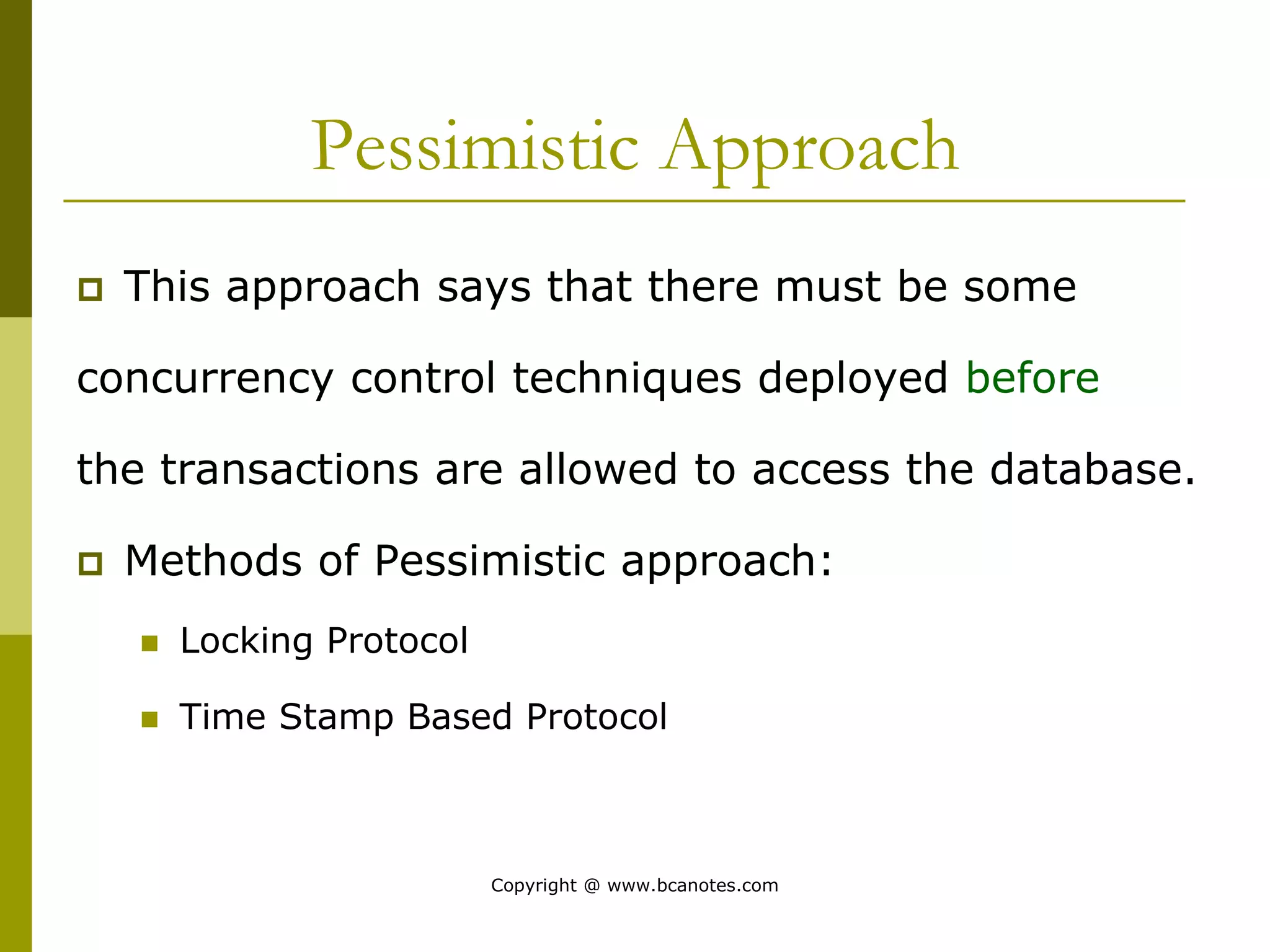
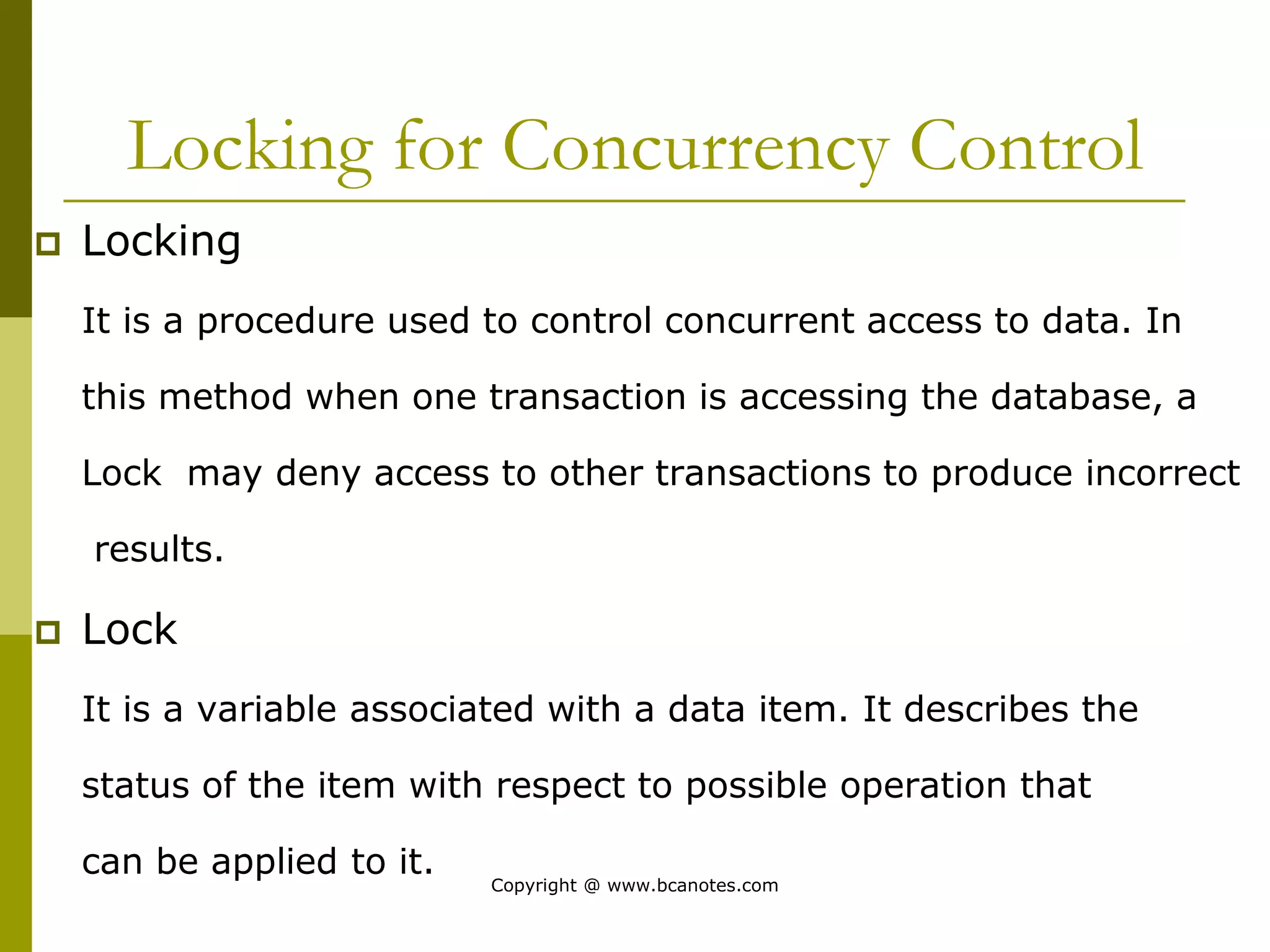
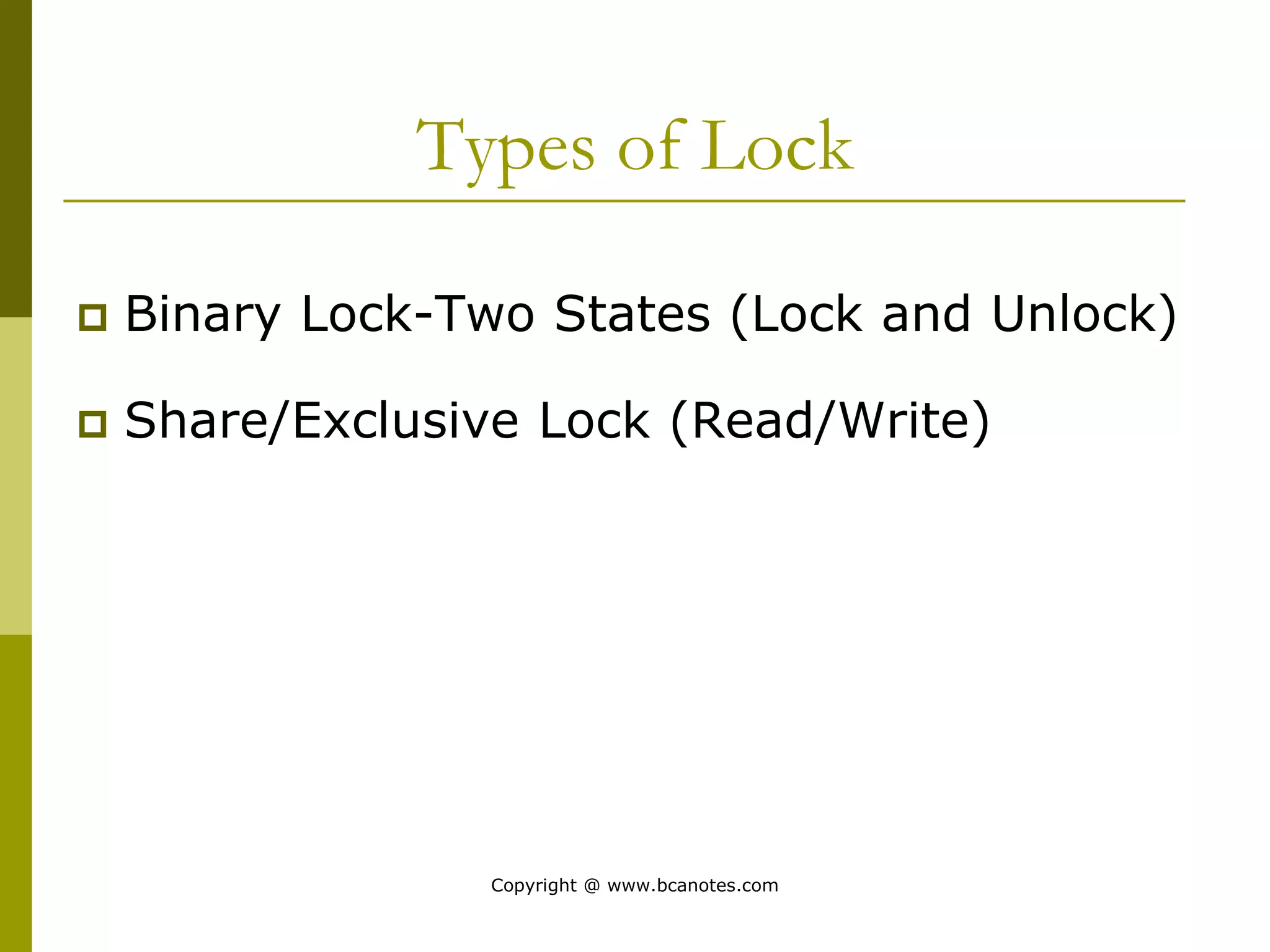
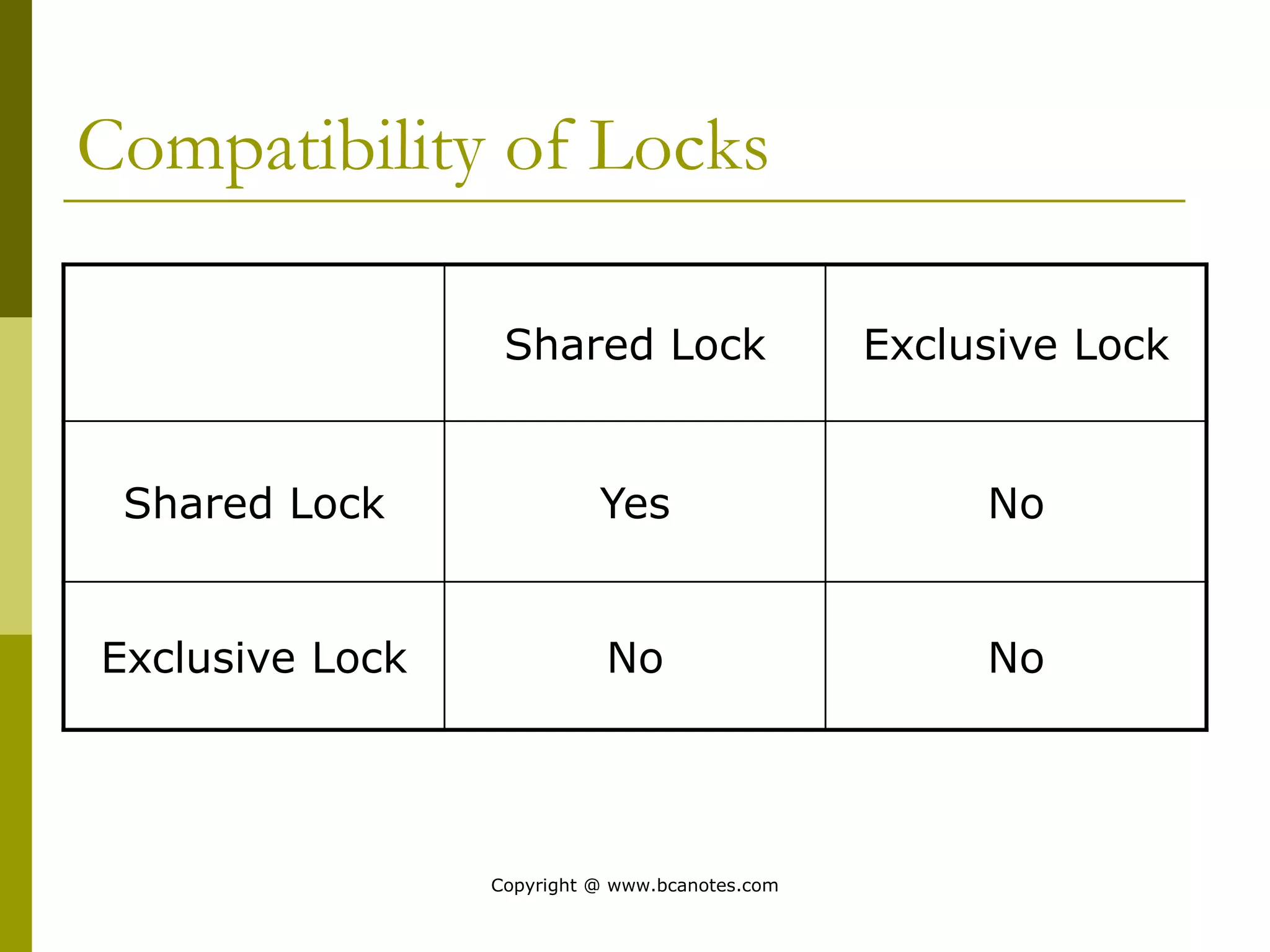
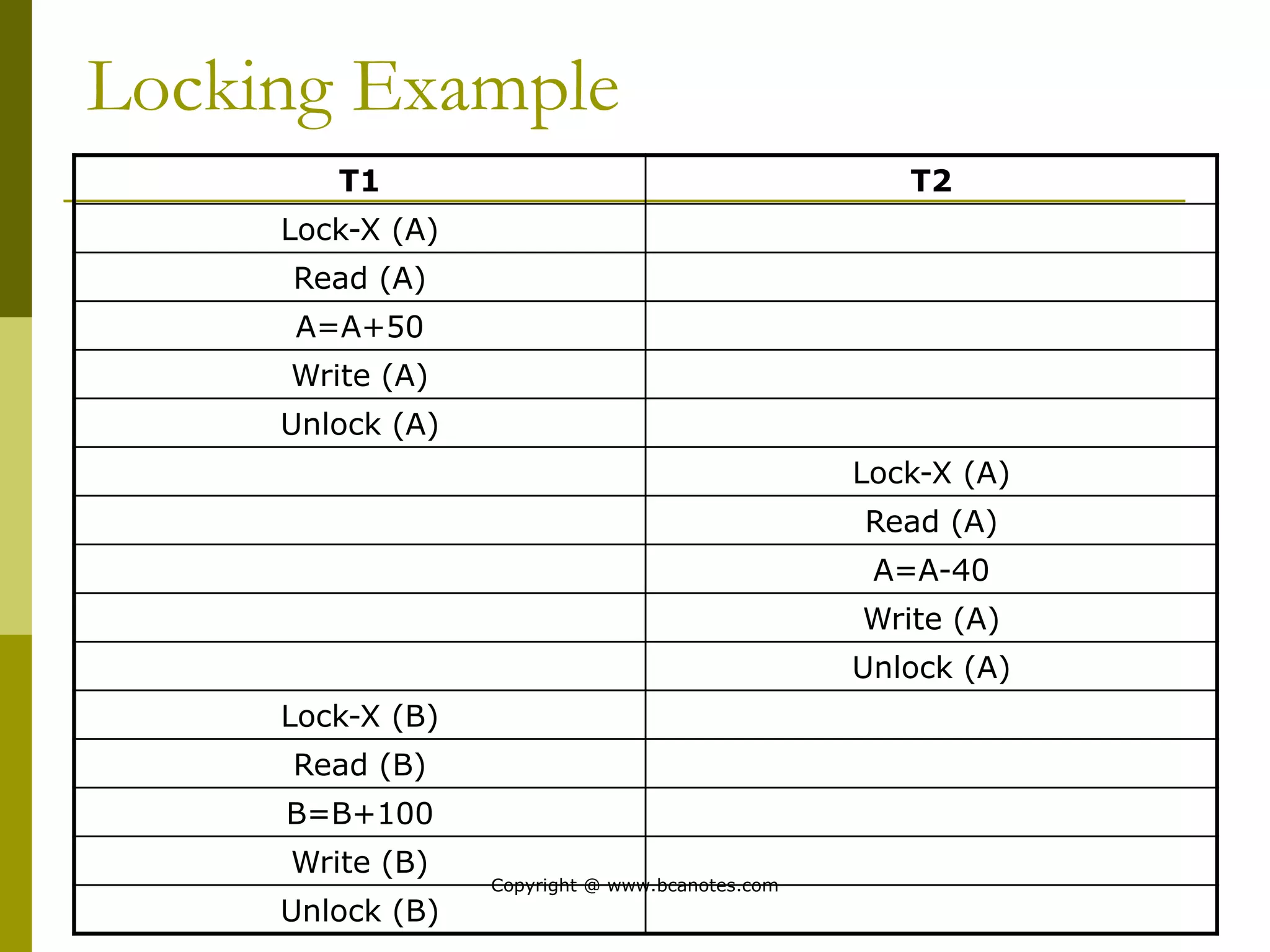
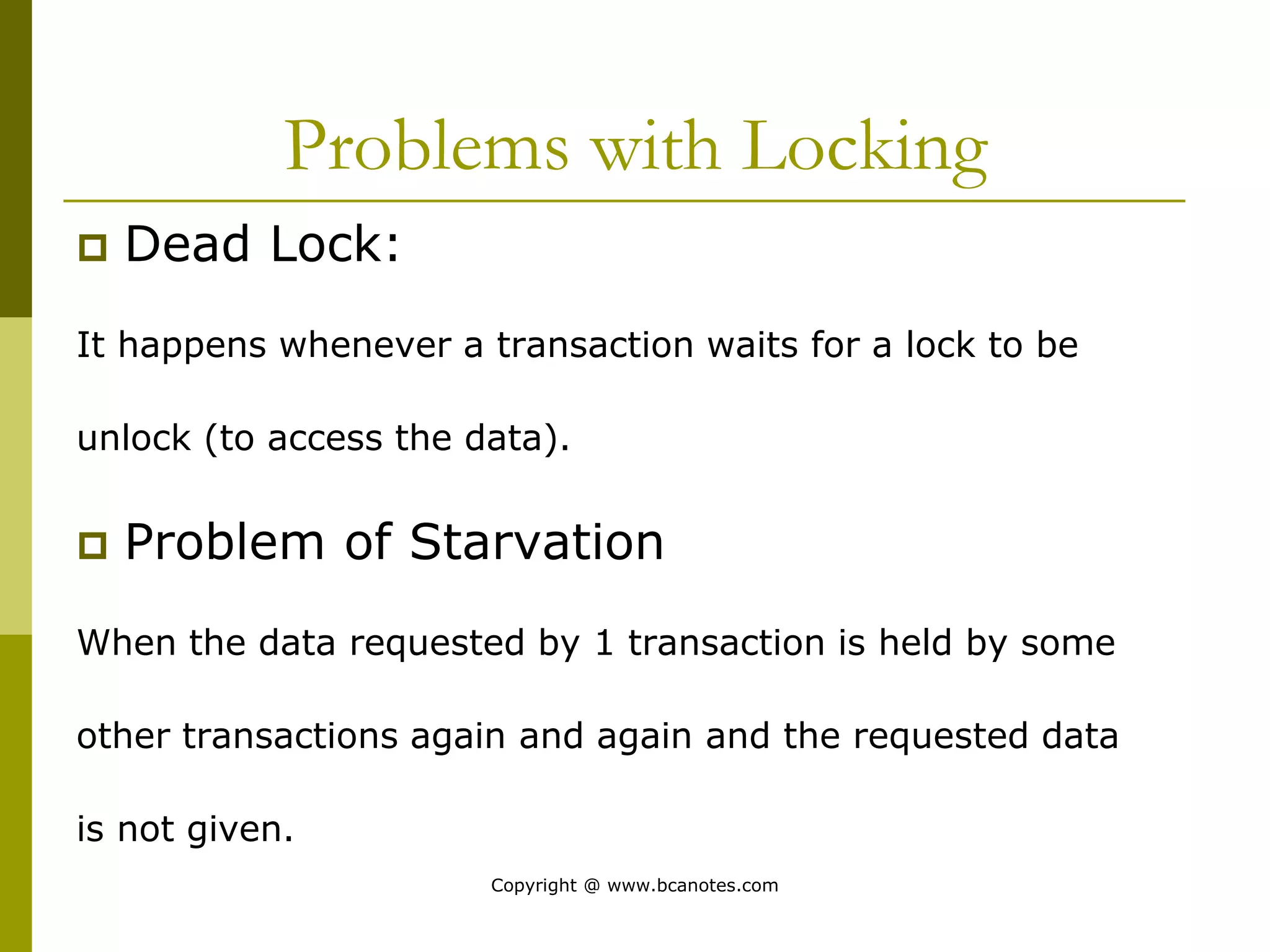
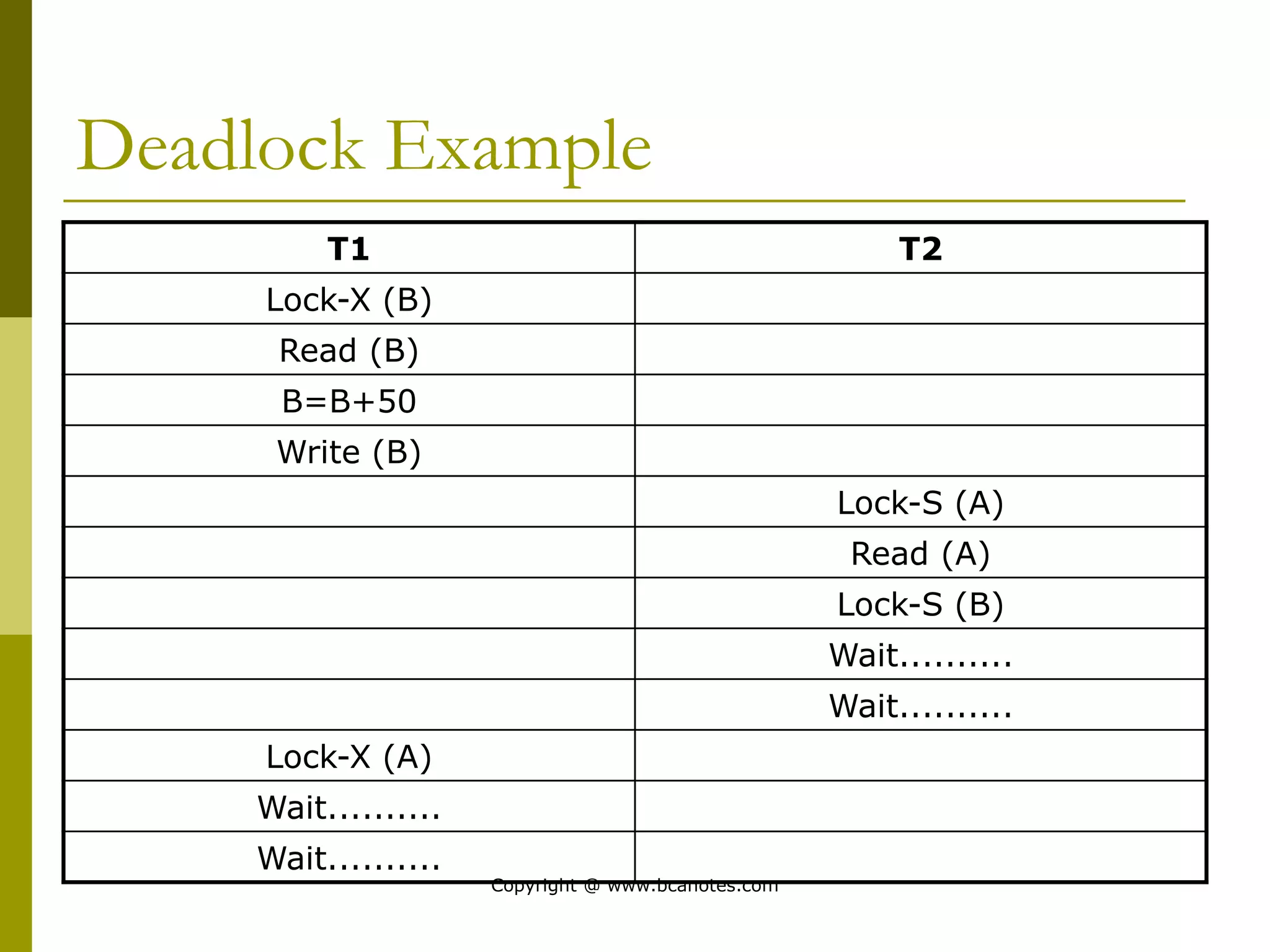
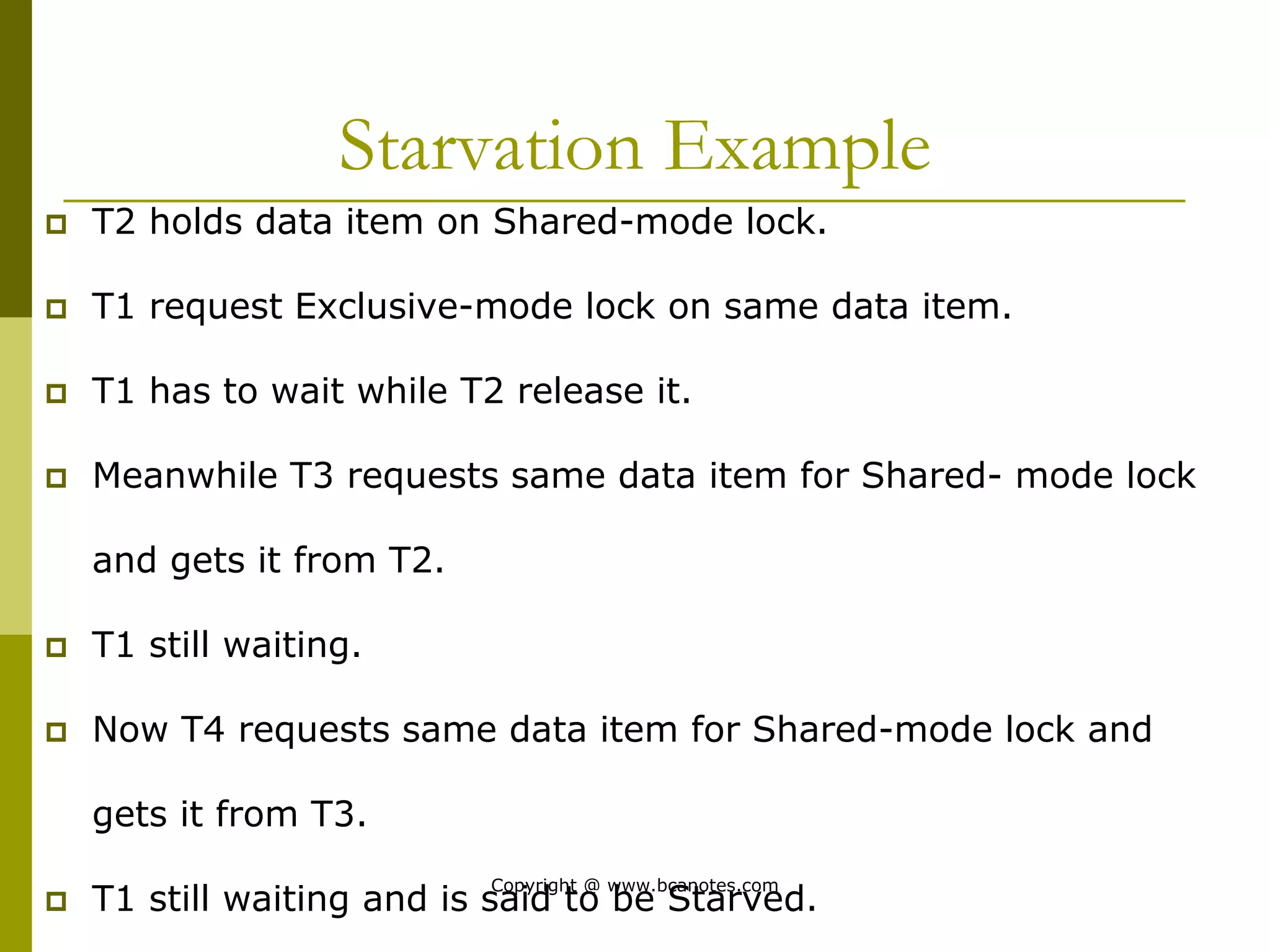
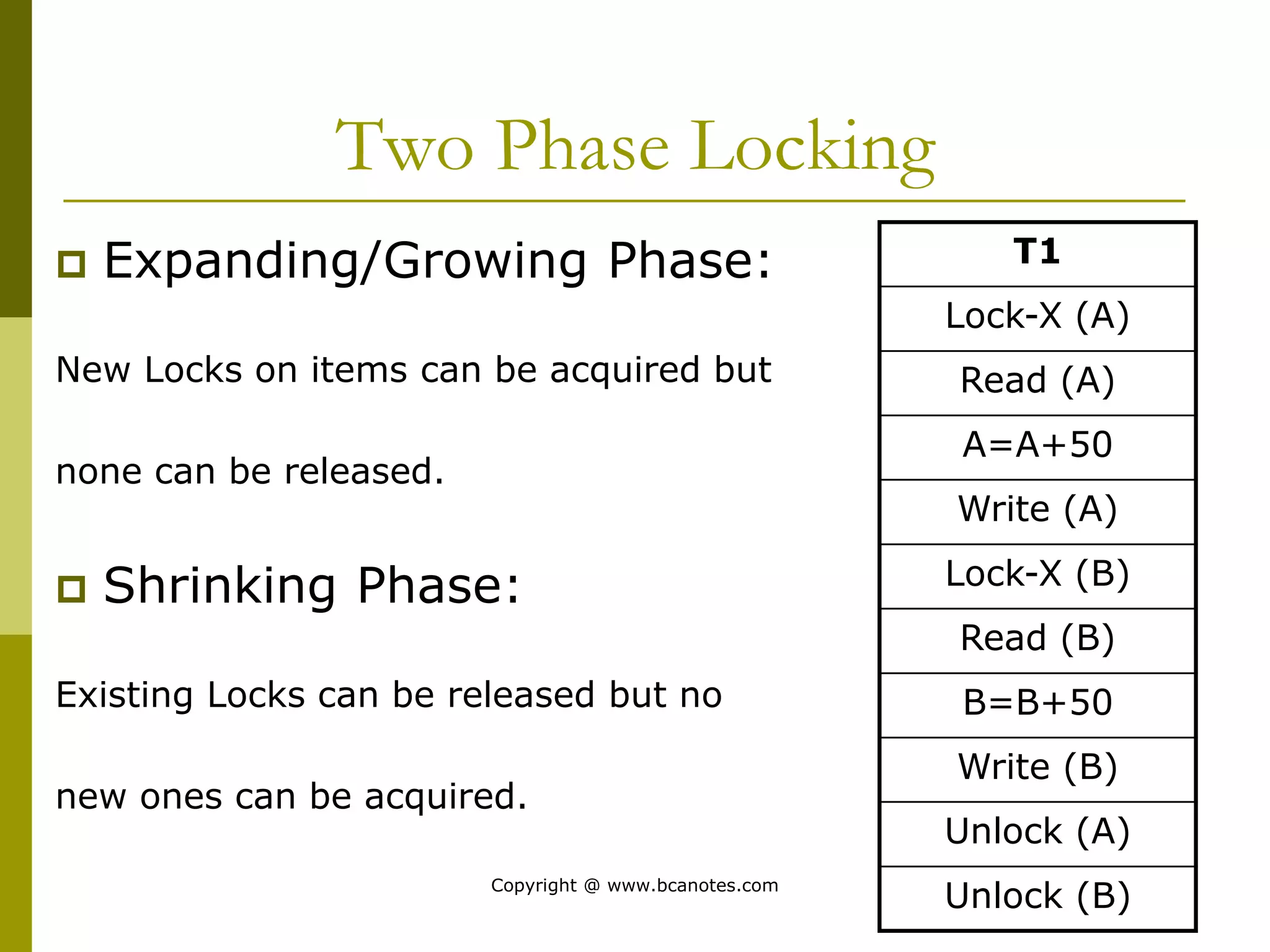
Concurrency control techniques are used to ensure that multiple transactions submitted by various users do not interfere with one another in a way that produces incorrect results. There are two main approaches: pessimistic and optimistic. The pessimistic approach uses locking protocols and time stamp ordering to prevent conflicts before transactions run. The optimistic approach allows transactions to run without synchronization and then validates their results to detect conflicts before committing changes.