The document covers confidentiality policies, particularly focusing on the Bell-LaPadula model, which establishes rules for information flow to prevent unauthorized disclosure. It explains security levels, information flow rules, and addresses the complexity of communication between subjects at different security levels. The lecture emphasizes the model's foundational role in multilevel security and its implications for maintaining confidentiality in computing systems.




![Fall 2023 Cp 633
Slide #5-9
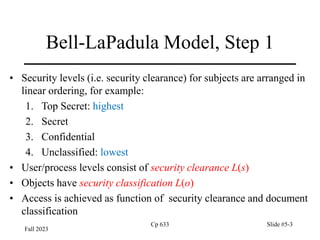
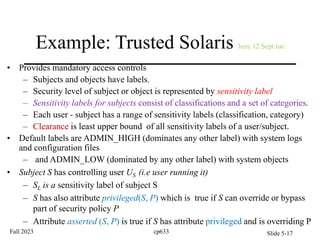
Security lattice by information categories
• Lattice is generated by categories NUC, EUR, and US.
• The lines represent the ordering relation induced by (subset of).
• The line is placed between A and B iff A B, and A≠B and there
exists no C so that A C B, A≠C, B≠C.
[NUC, EUR, US]
[NUC, EUR] [EUR, US]
[NUC, US]
[NUC] [EUR] [US]
Ø](https://image.slidesharecdn.com/ch5cp633-240604004038-1ee944a6/85/computer-security-presentation-chapter-5-9-320.jpg)

![Fall 2023 Cp 633 Slide #5-11
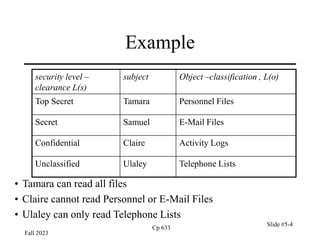
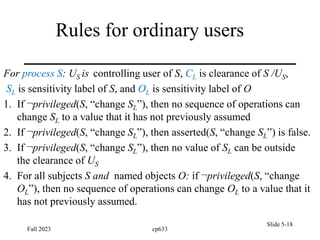
Levels and Ordering
• Relation of dominance is relation of partial ordering
• Security levels are partially ordered
– Any pair of security levels may be related by dom
• “dominates” serves the role of “greater than” in step 1
– “greater than” is a total ordering, though
(S, [NUC, EUR]) (S, [EUR, US])
(S, [NUC, US])
(S, [NUC]) (S, [EUR]) (S, [US])
(S, Ø)
(TS, [NUC, EUR]) (TS, [EUR, US])
(TS, [NUC, US])
(TS, [NUC]) (TS, [EUR]) (TS, [US])
(TS, Ø)
(TS, [NUC, EUR, US])
(S, [NUC, EUR, US])](https://image.slidesharecdn.com/ch5cp633-240604004038-1ee944a6/85/computer-security-presentation-chapter-5-11-320.jpg)






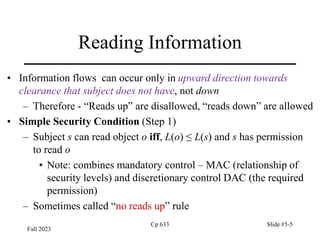
![Initial Assignment of Labels
• Each account is assigned a label range [user’s minimum label,
clearance] (note clearance is the upper bound of label range).
• On login, Trusted Solaris determines if the session is single-level
– If clearance = minimum label, this is single level account and session gets
that label
– If not, multi-level; user asked to specify clearance for session; must be in
the label range
– In multi-level session, user can change to any label in the range of the
session clearance to the minimum
• This is useful if user has several workspaces each with its own sensitivity
level.
– This is kind of role based access control.
Fall 2023 Cp633 Slide 5-20](https://image.slidesharecdn.com/ch5cp633-240604004038-1ee944a6/85/computer-security-presentation-chapter-5-20-320.jpg)