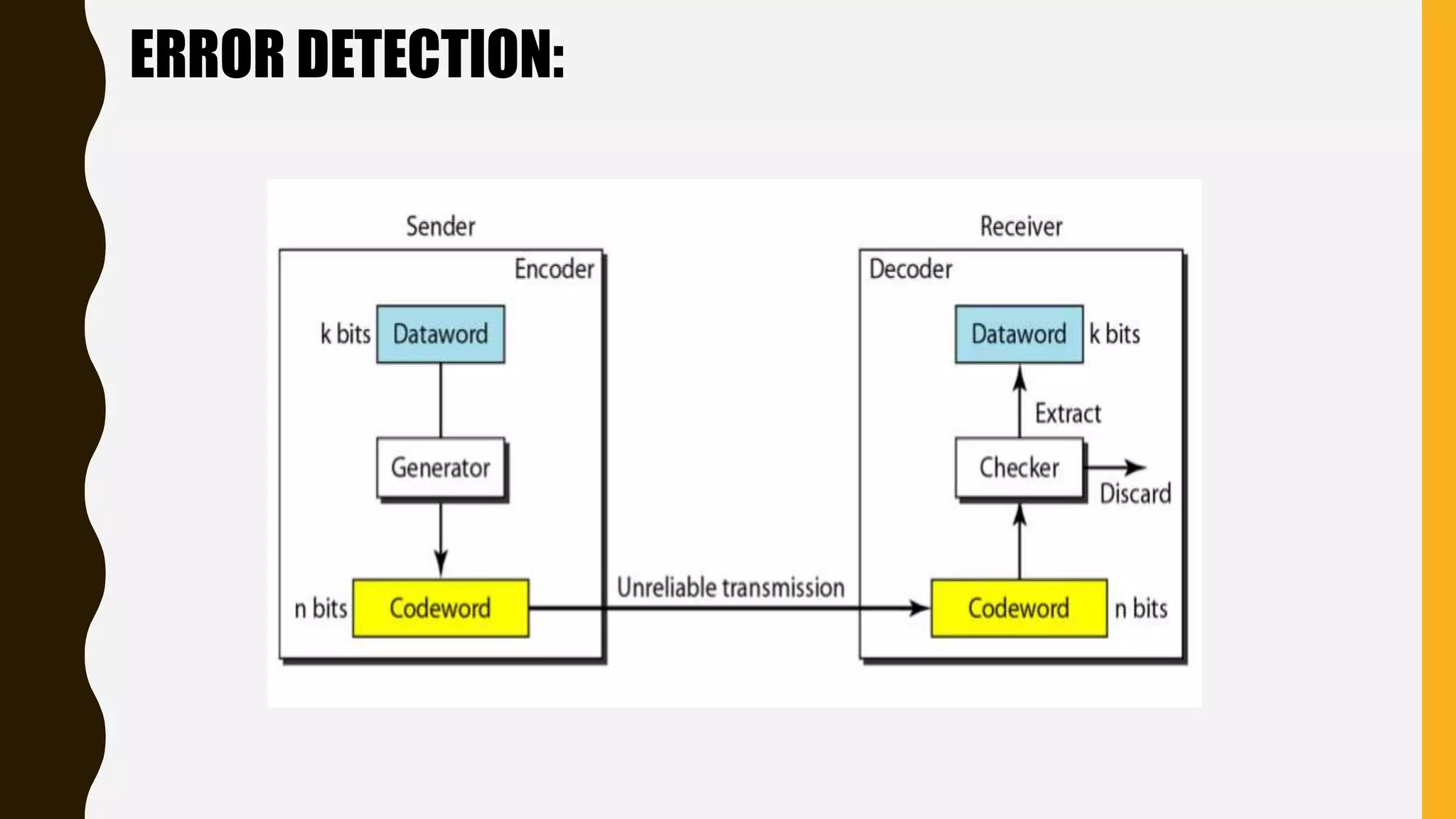
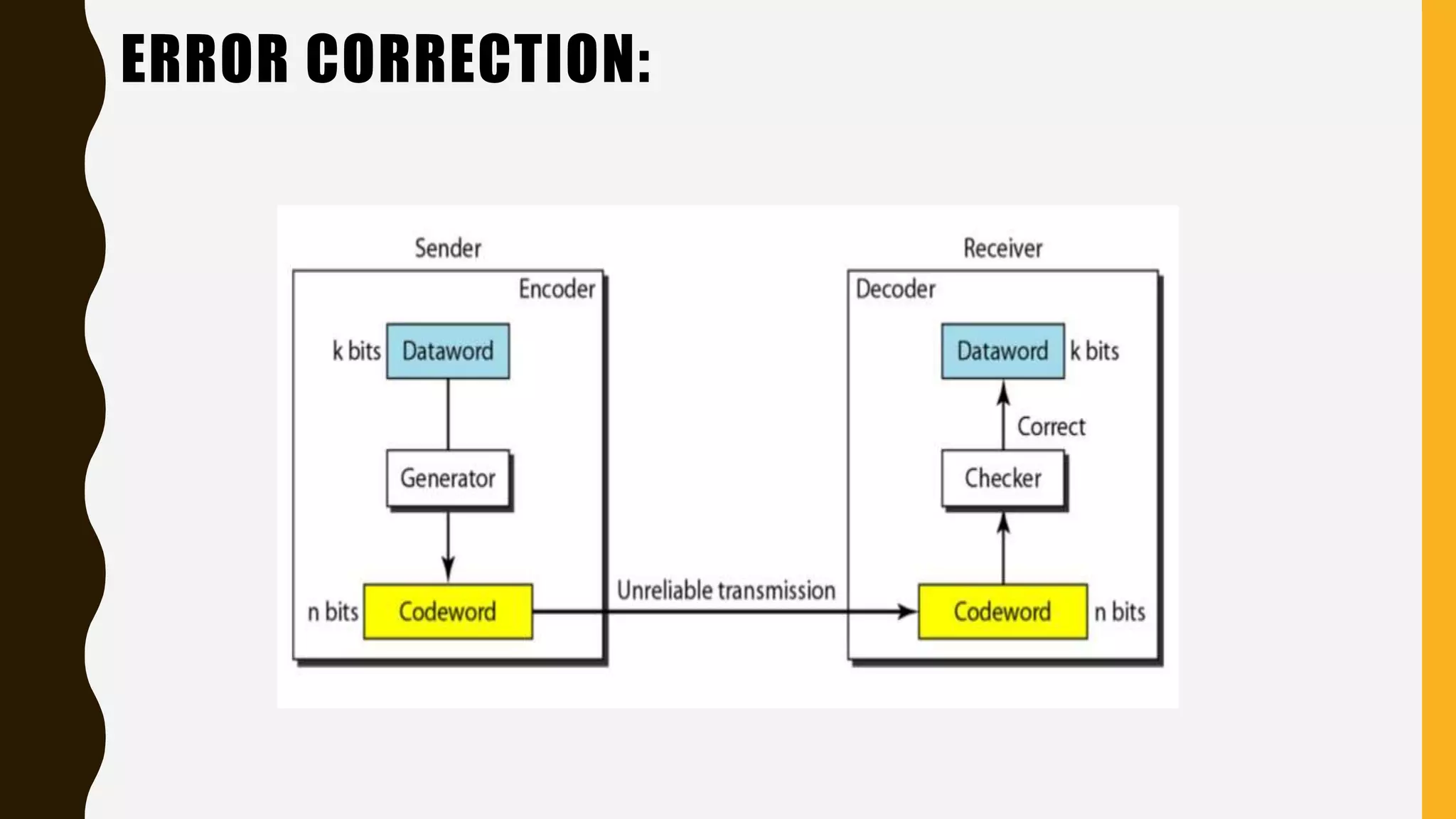
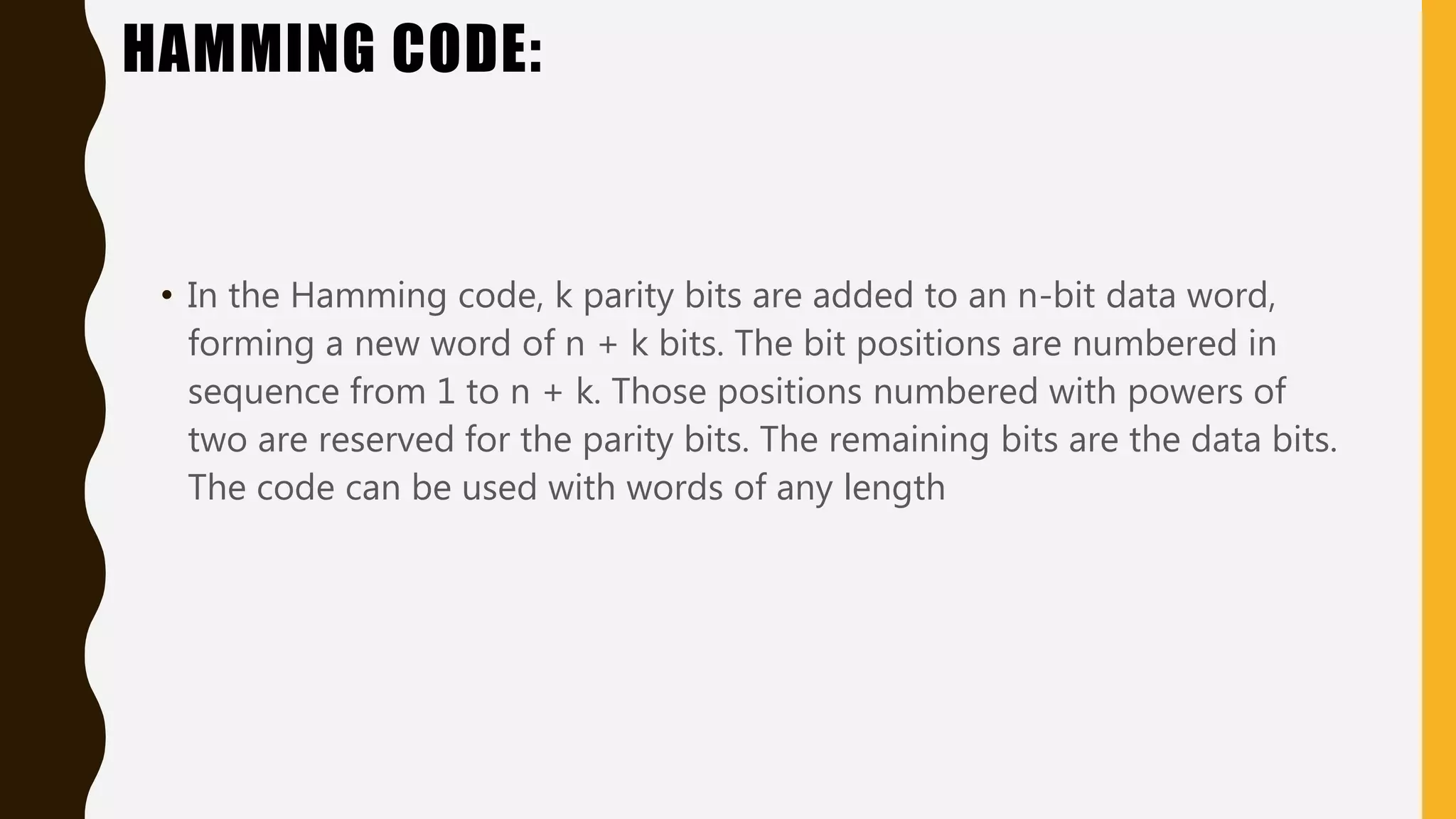
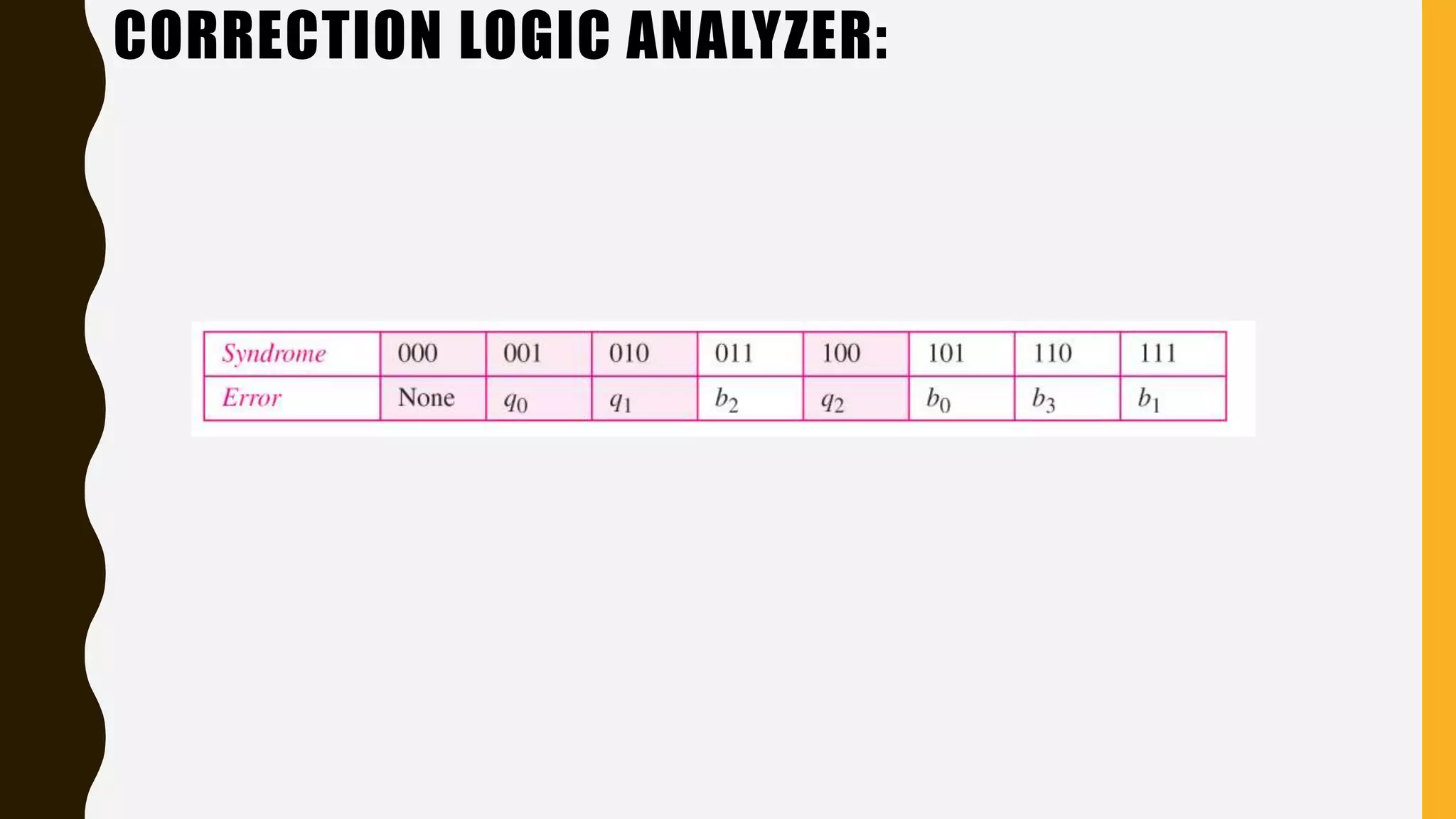
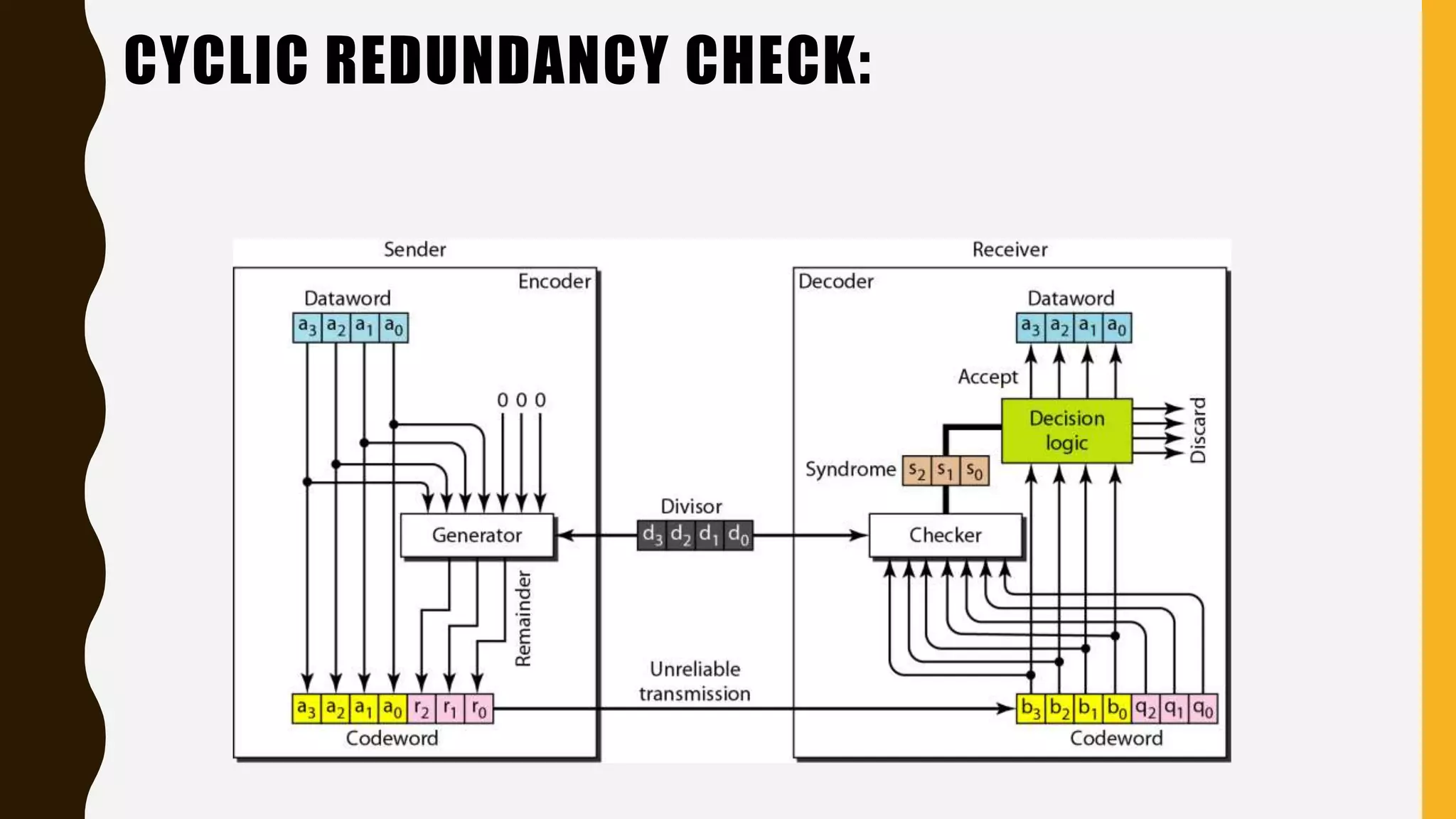
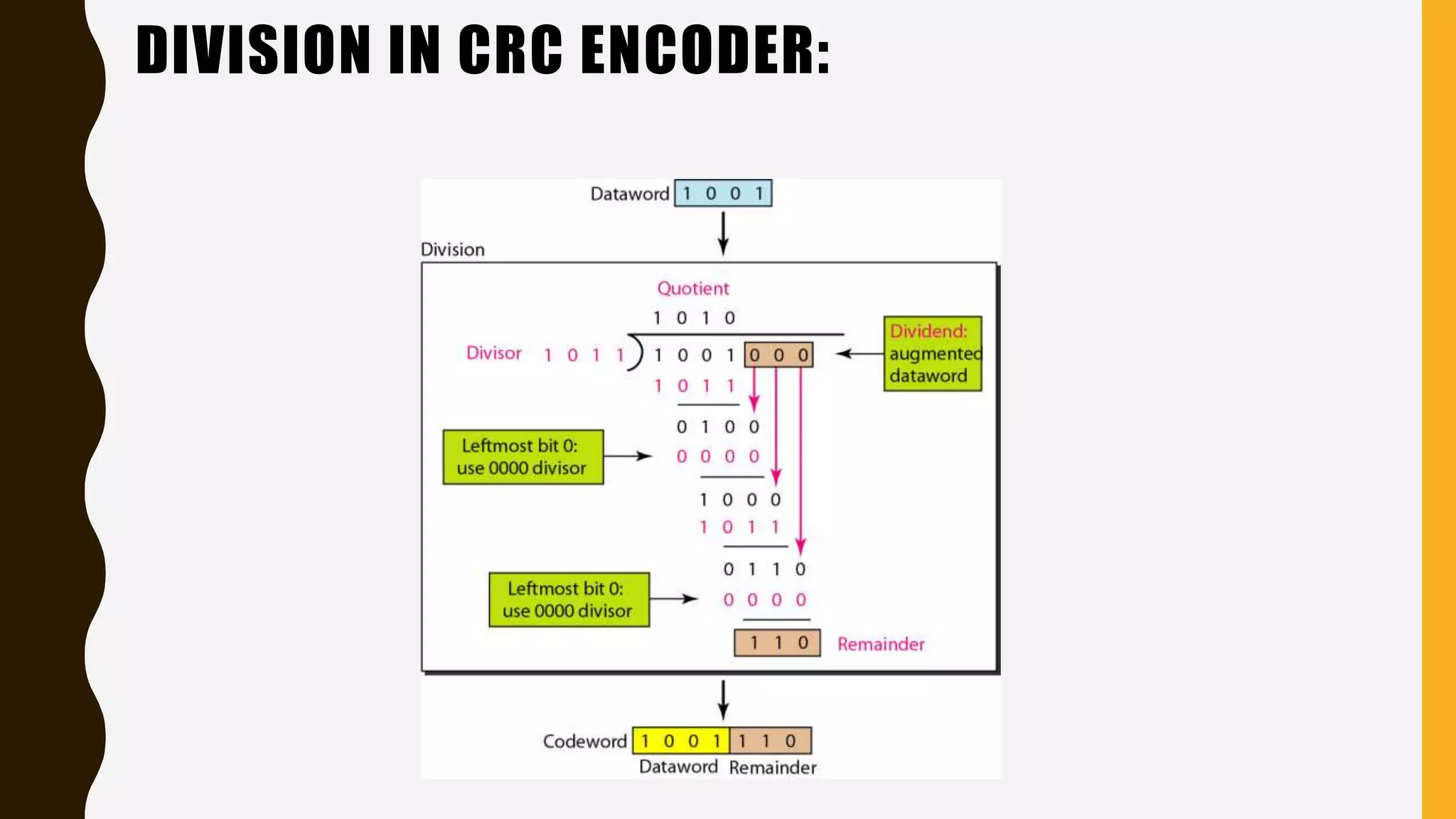
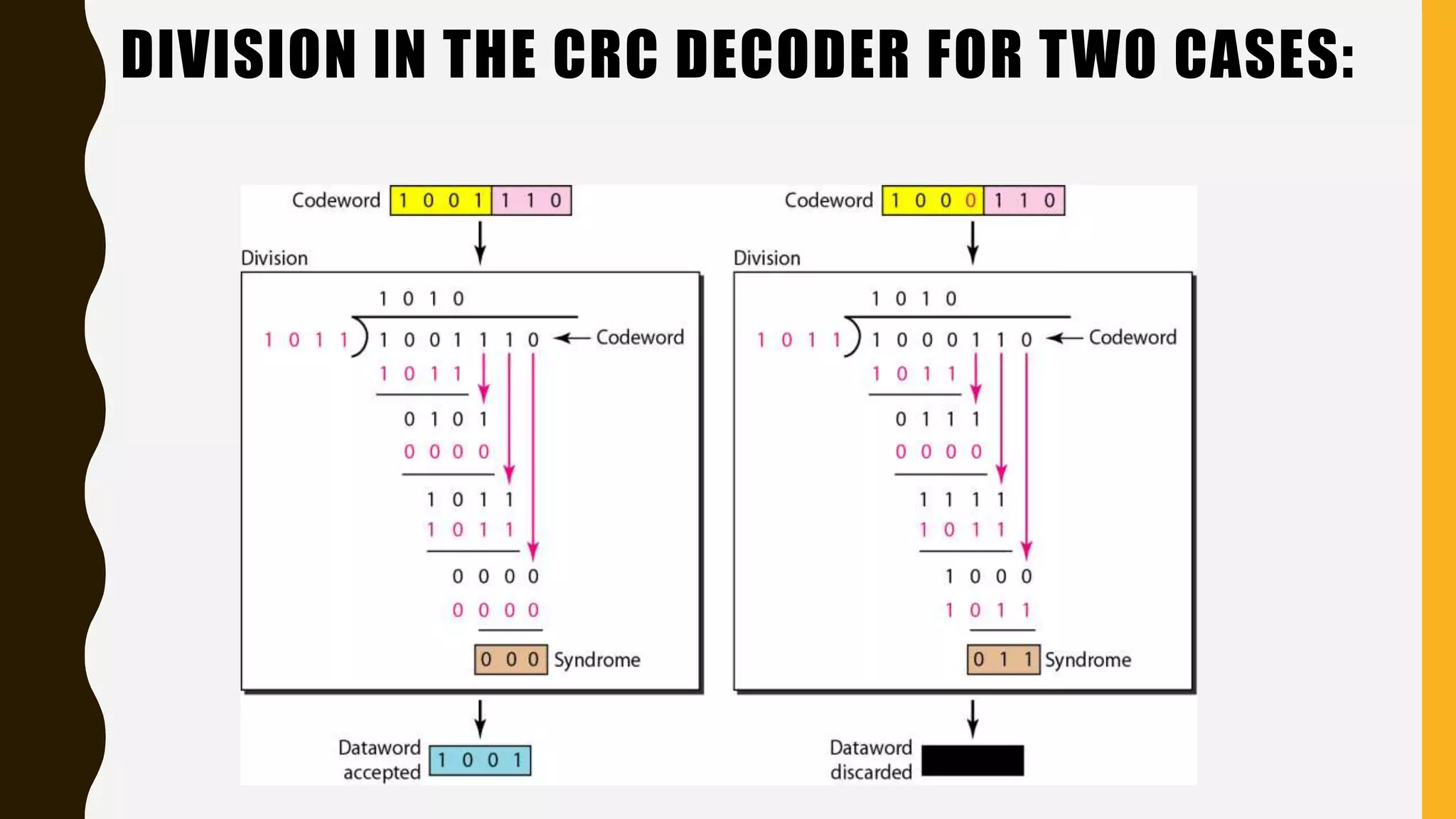
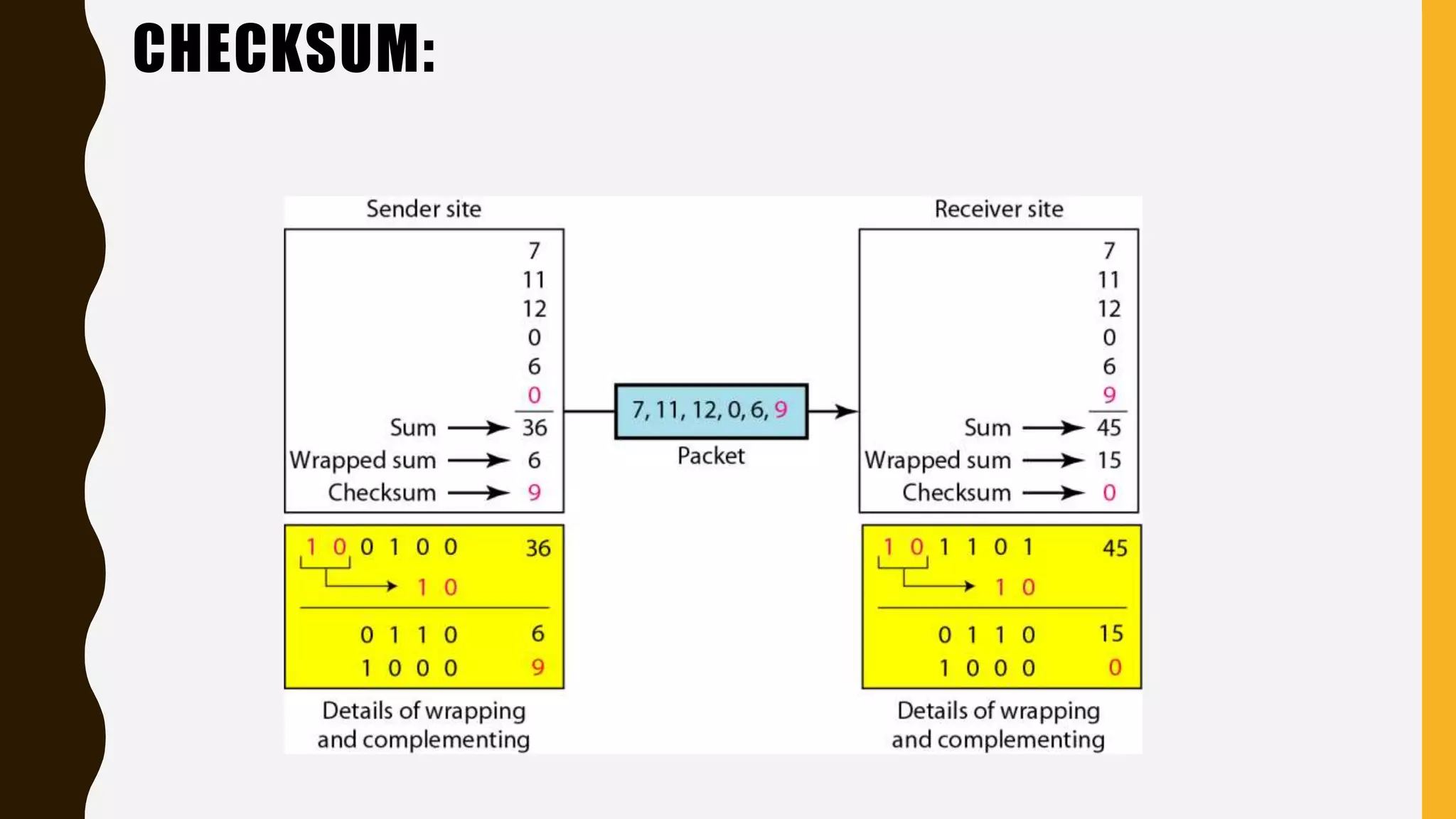
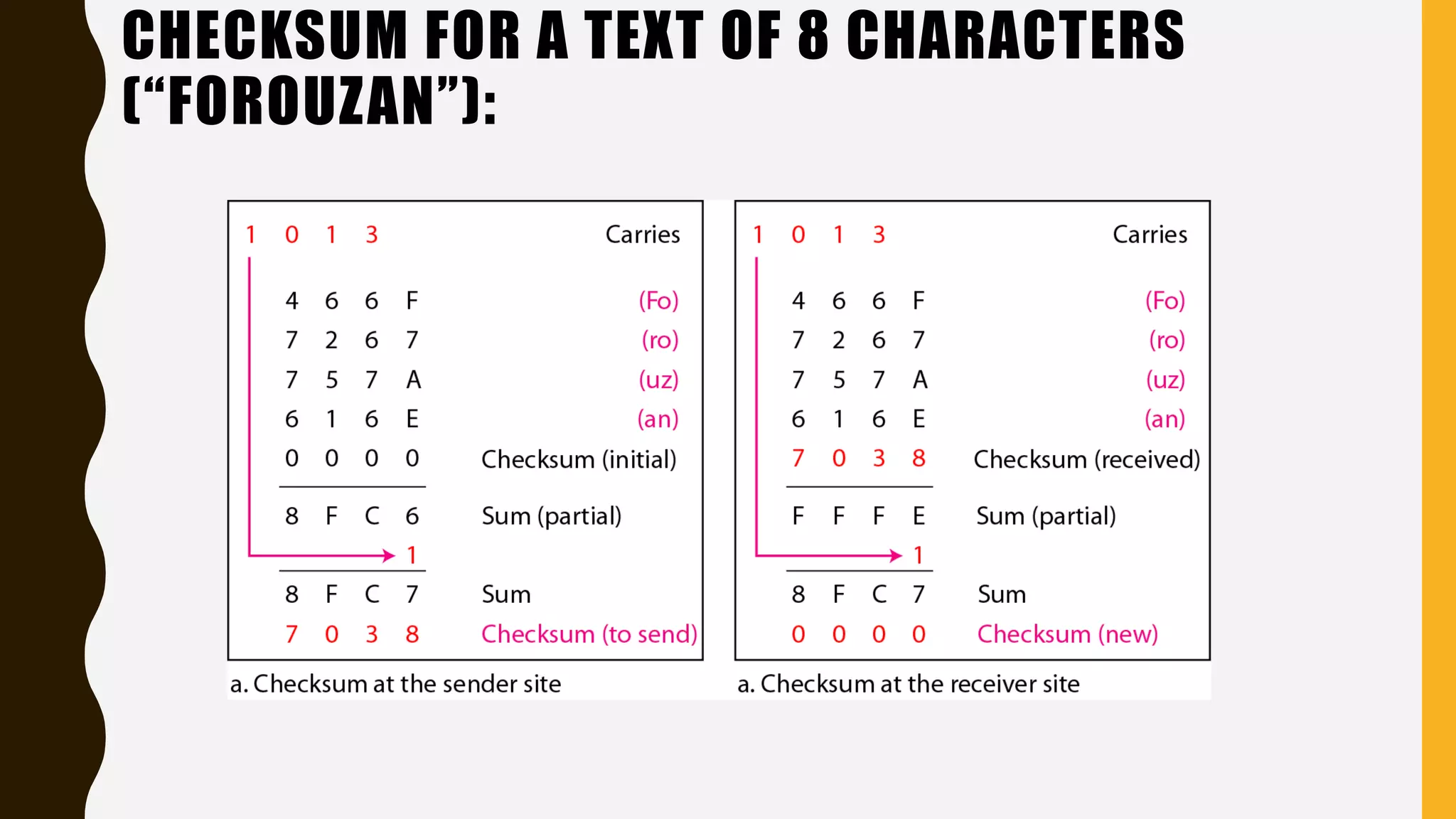
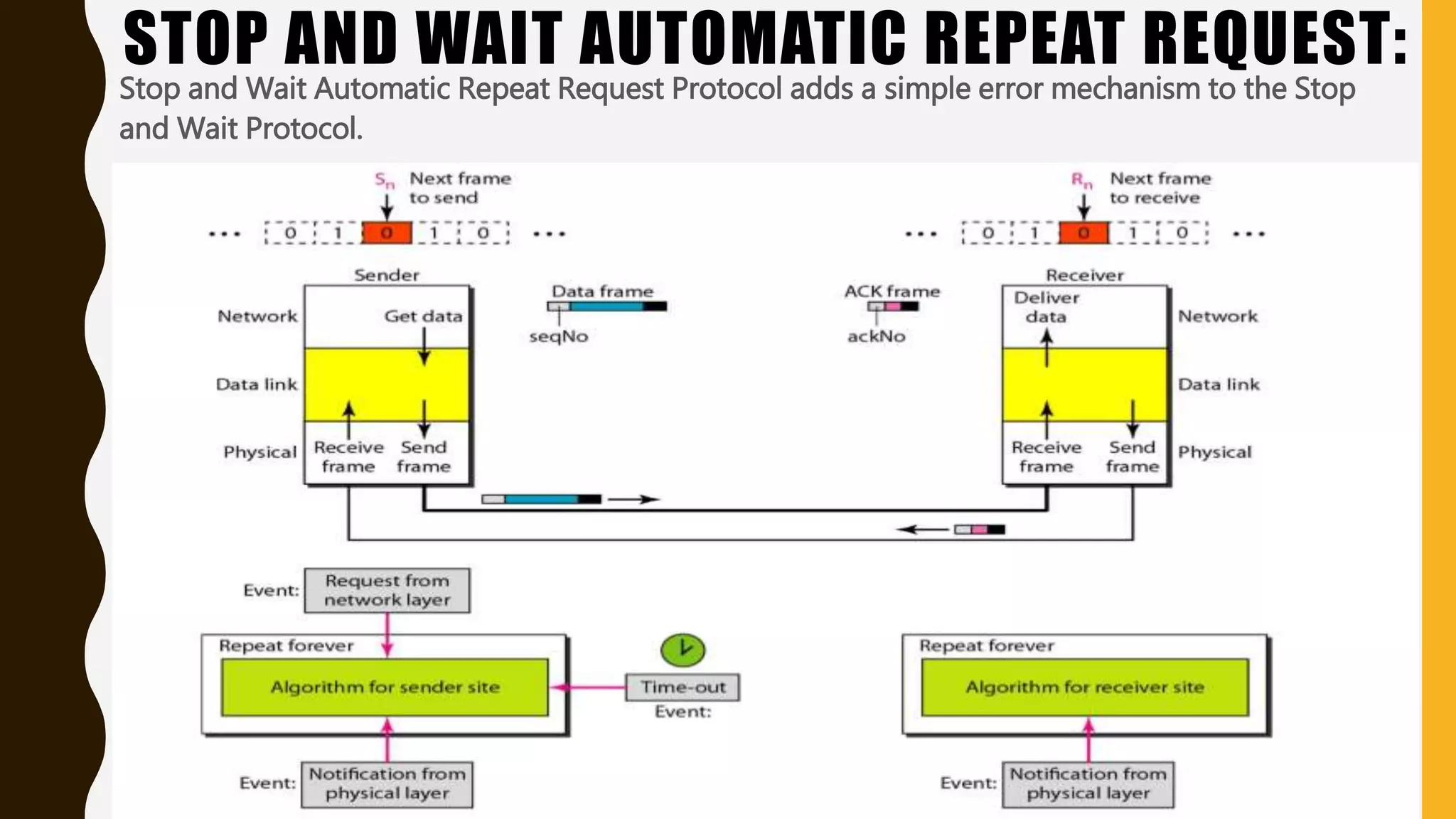
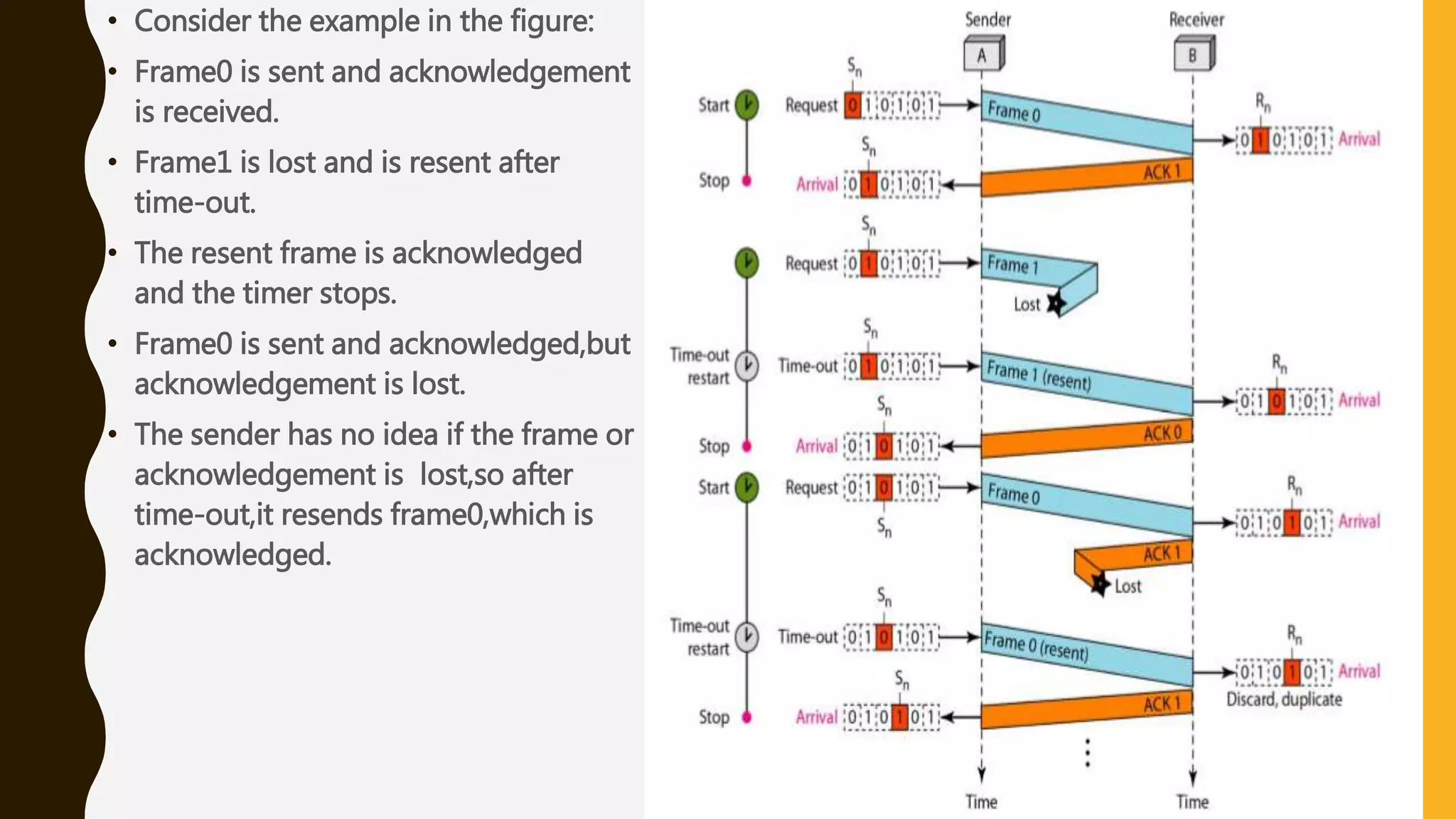
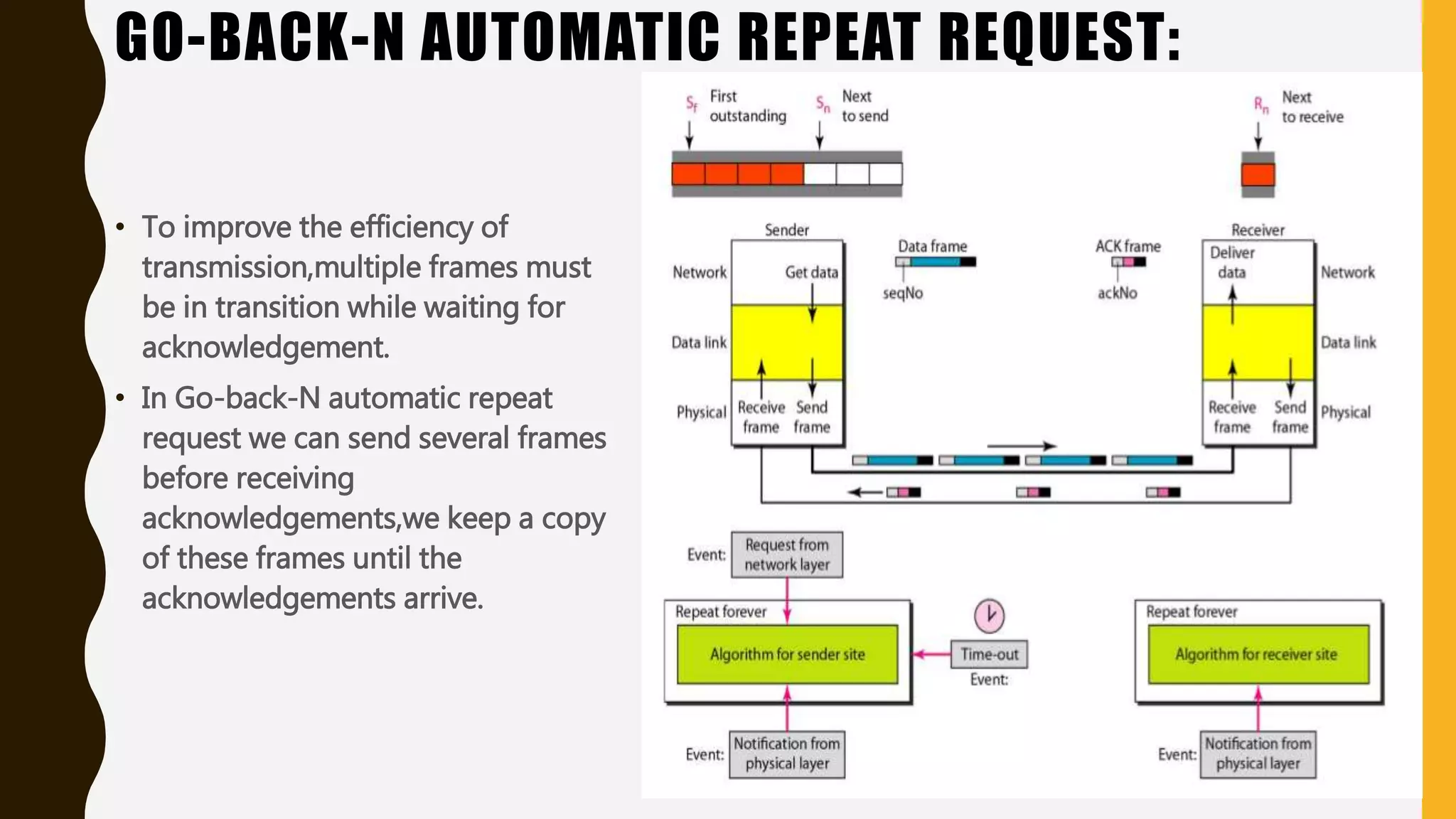
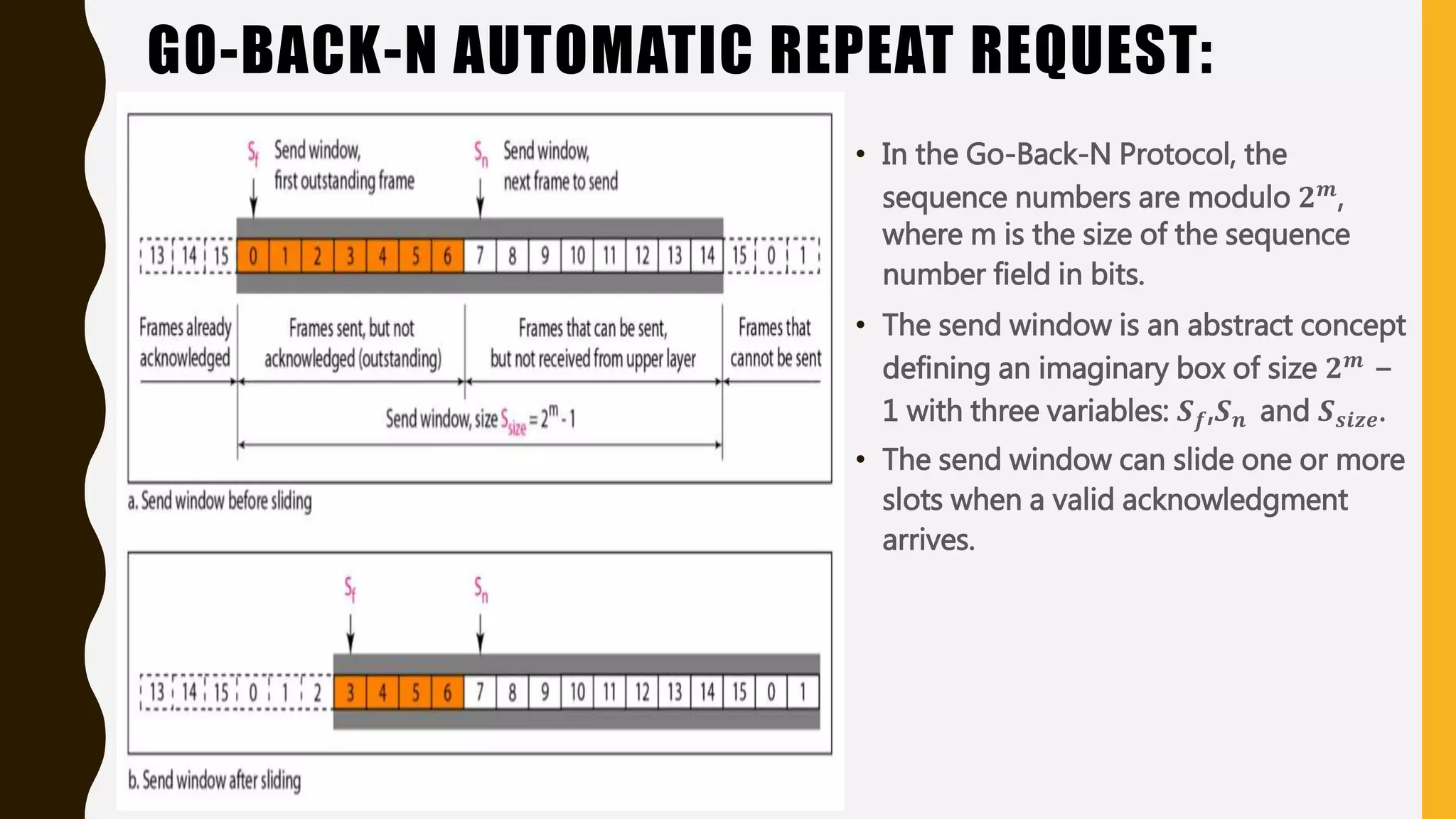
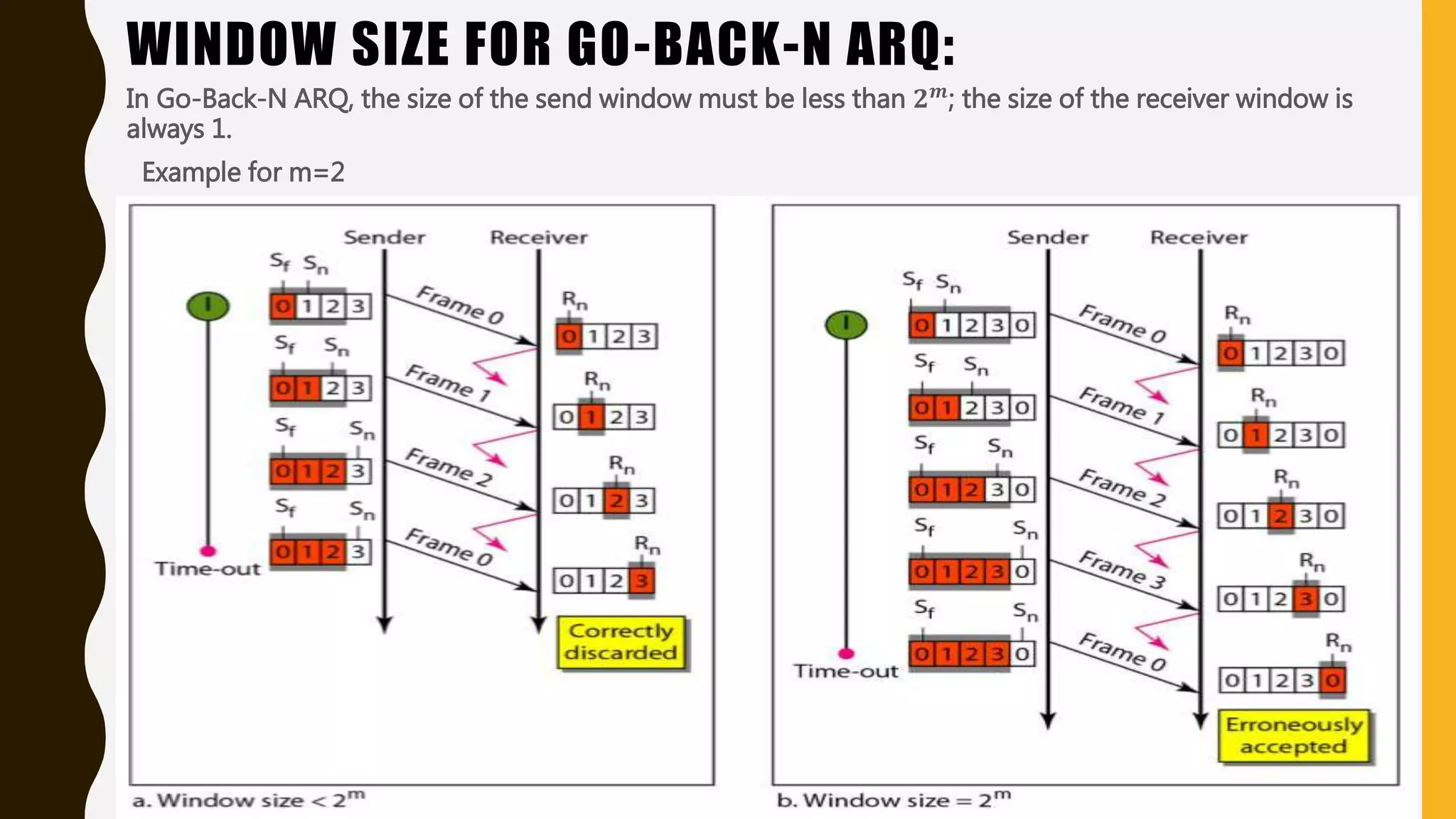
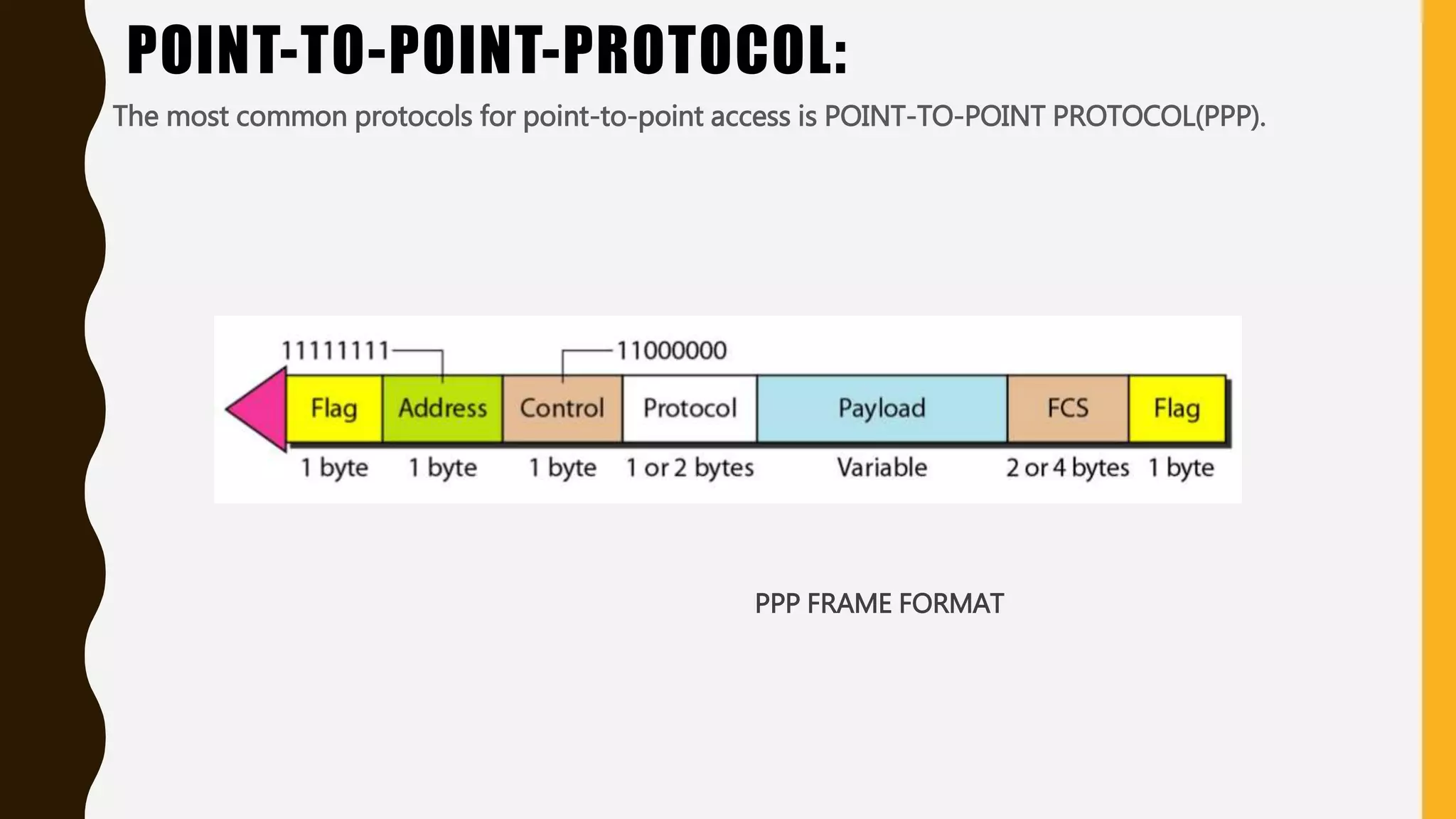
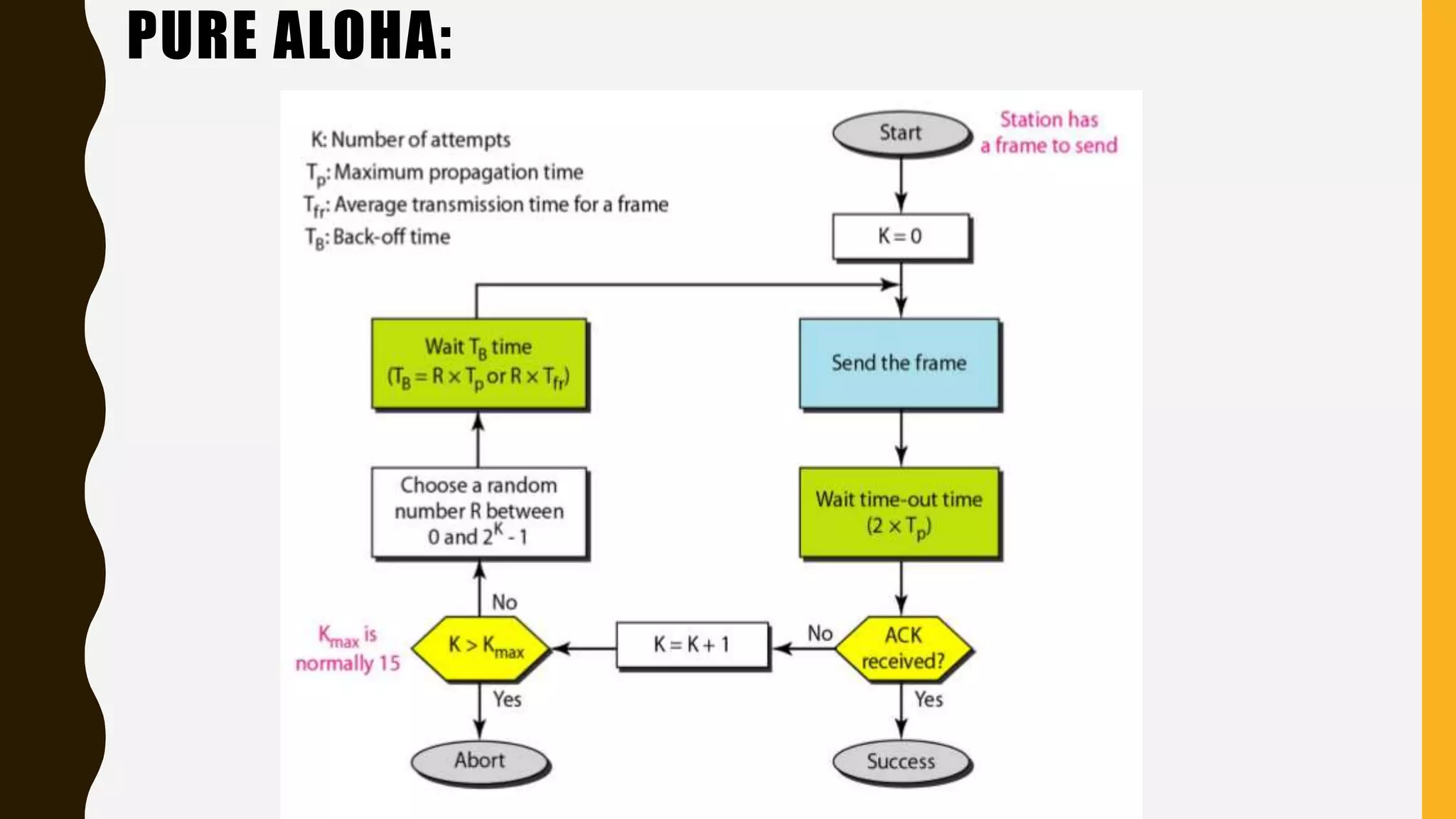
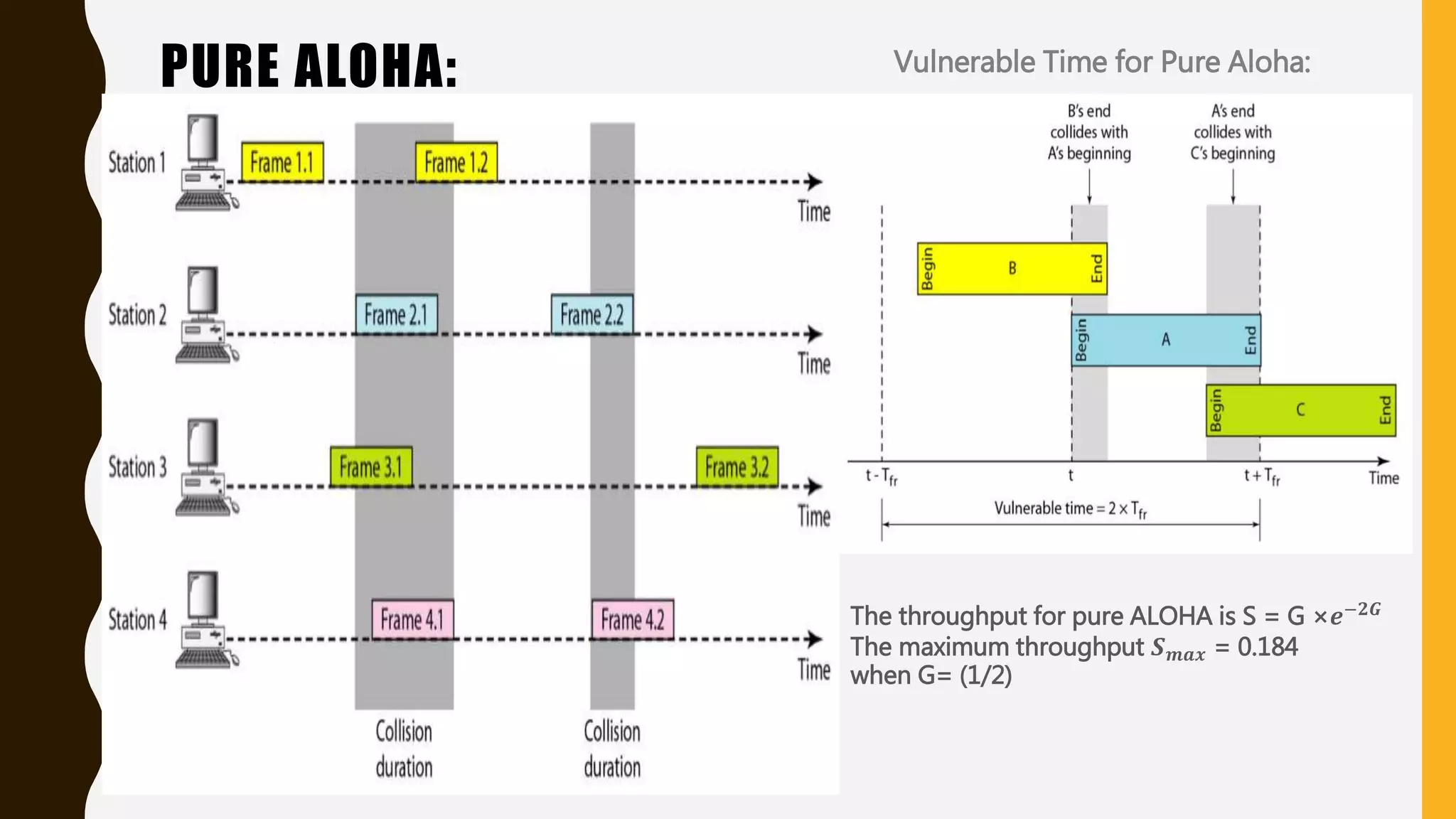
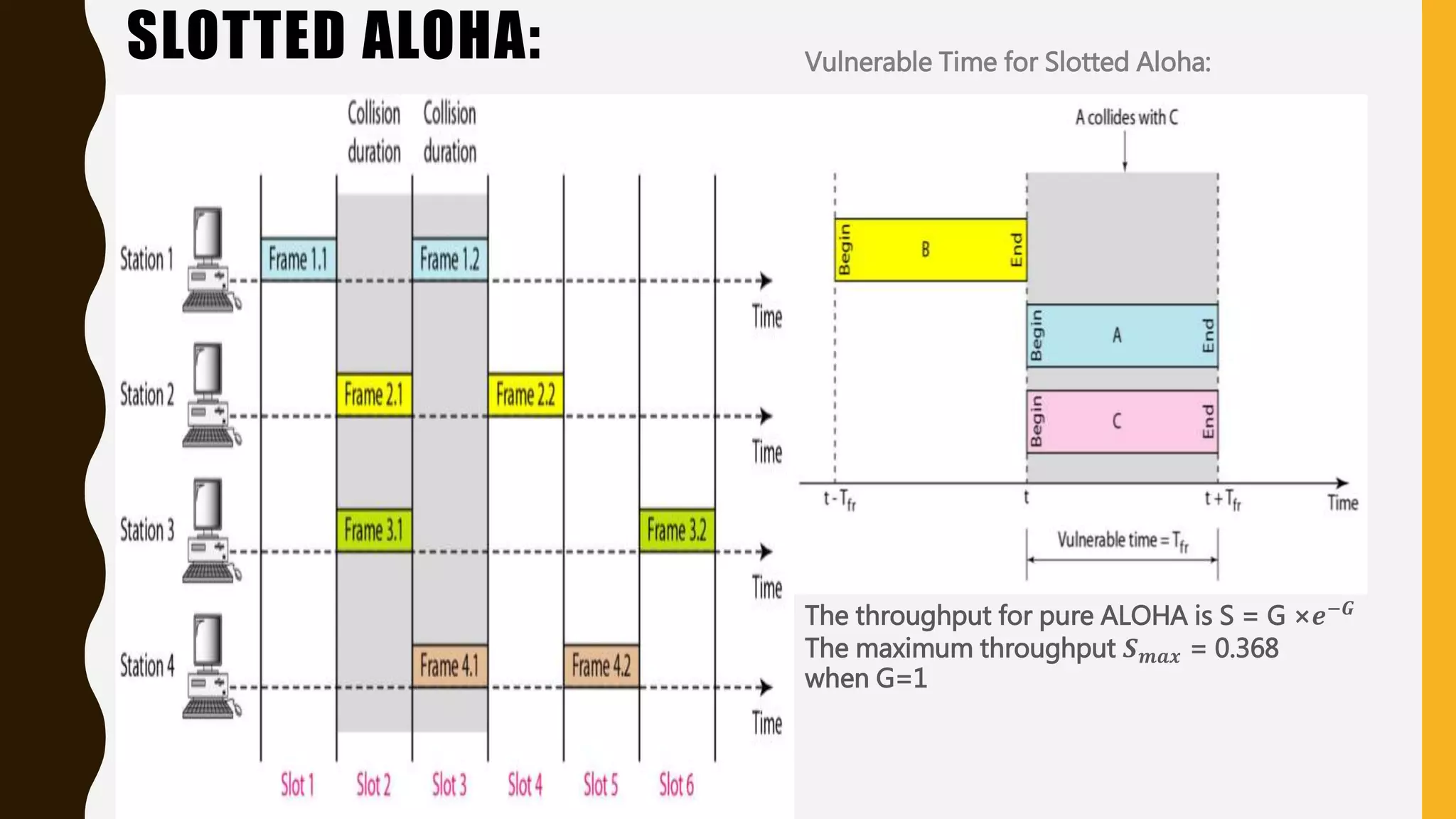
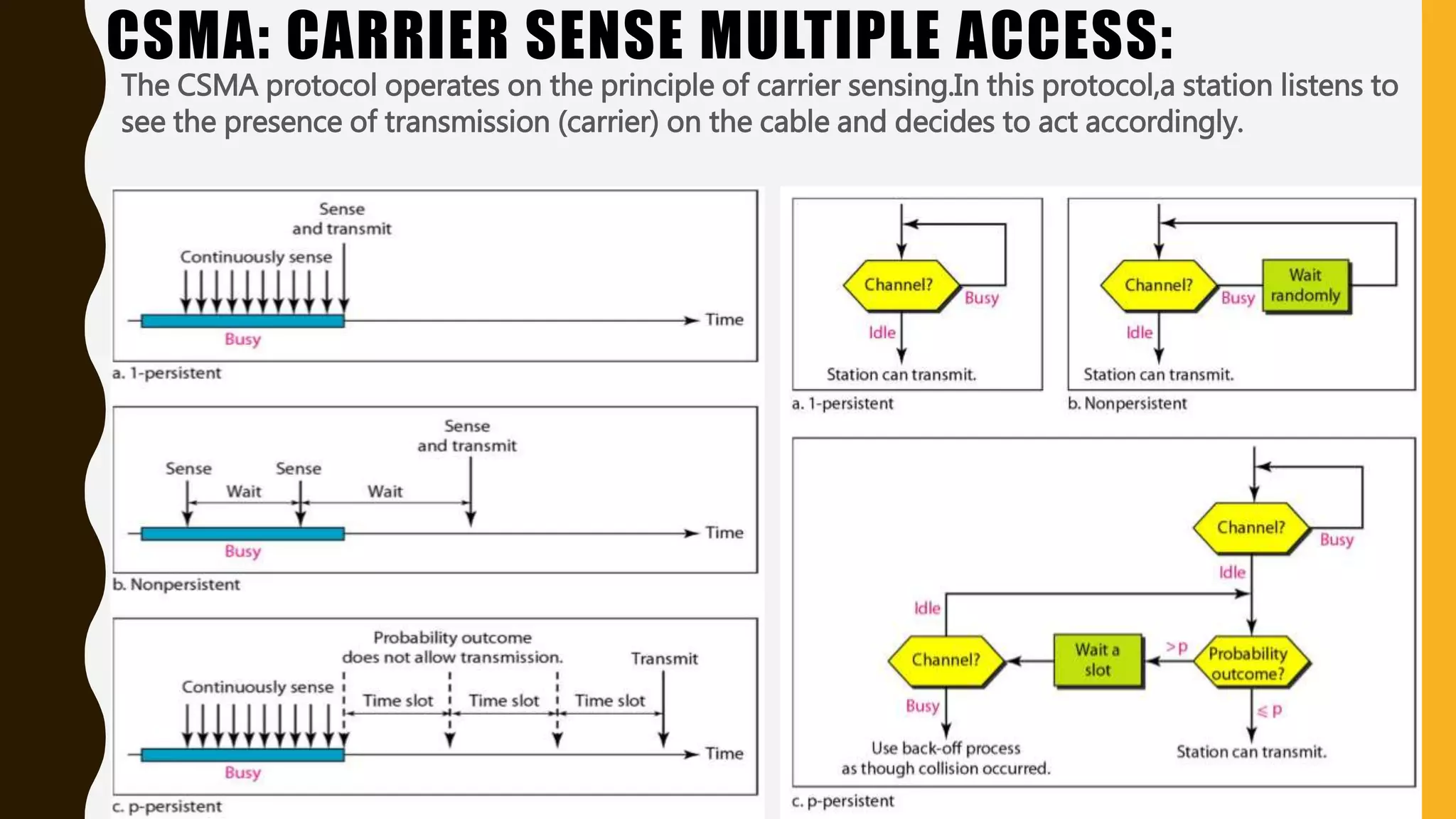
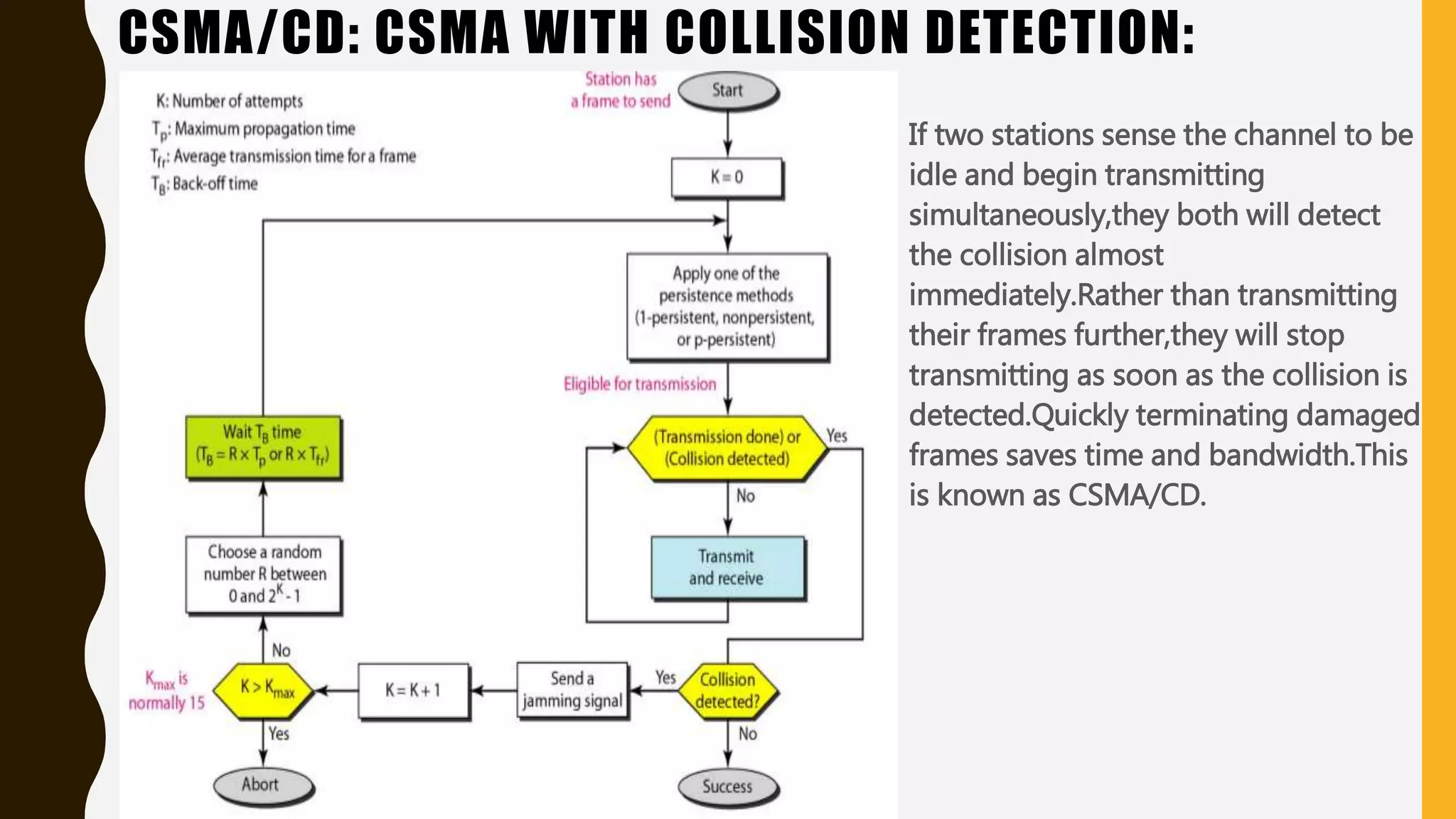
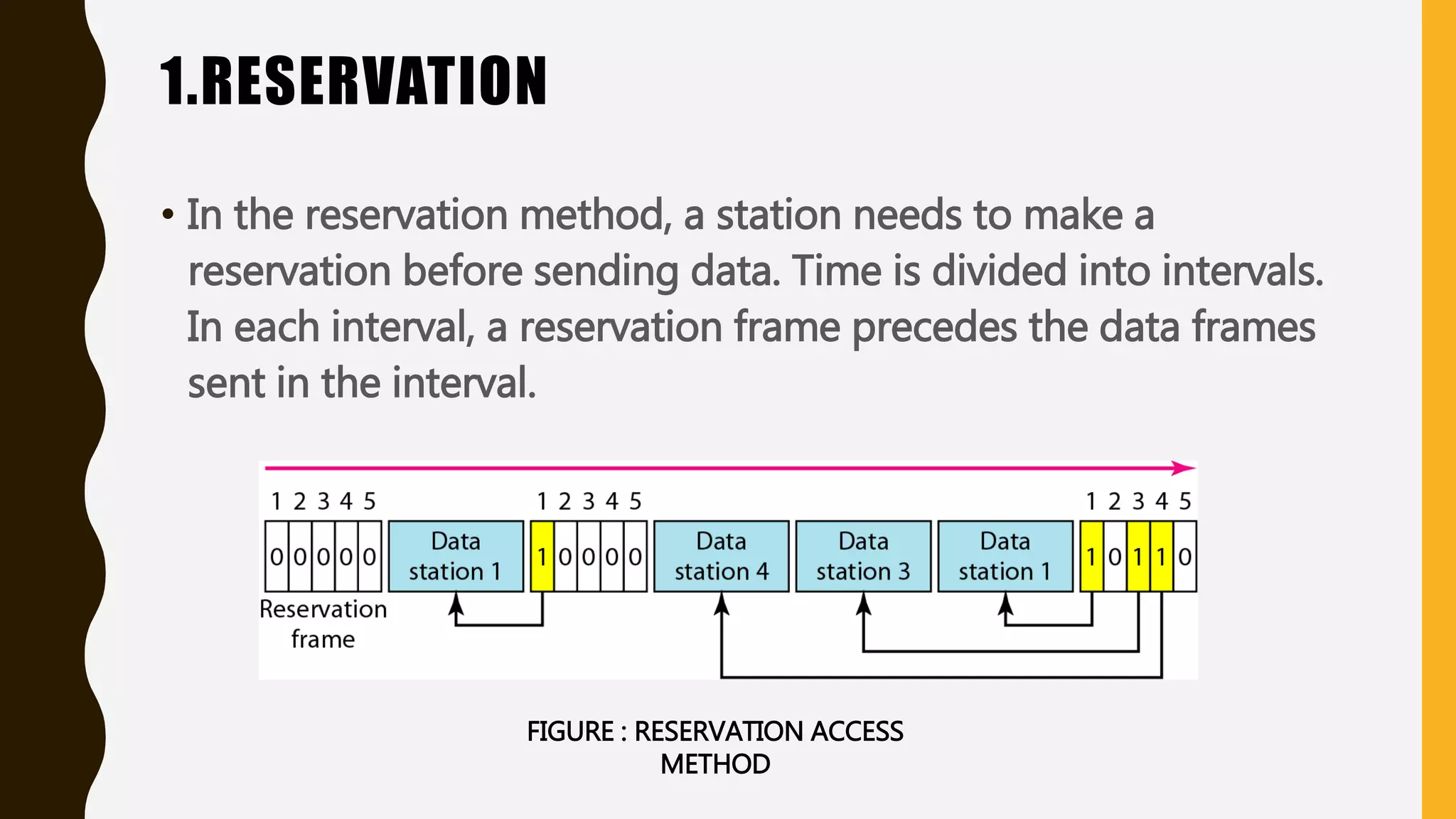
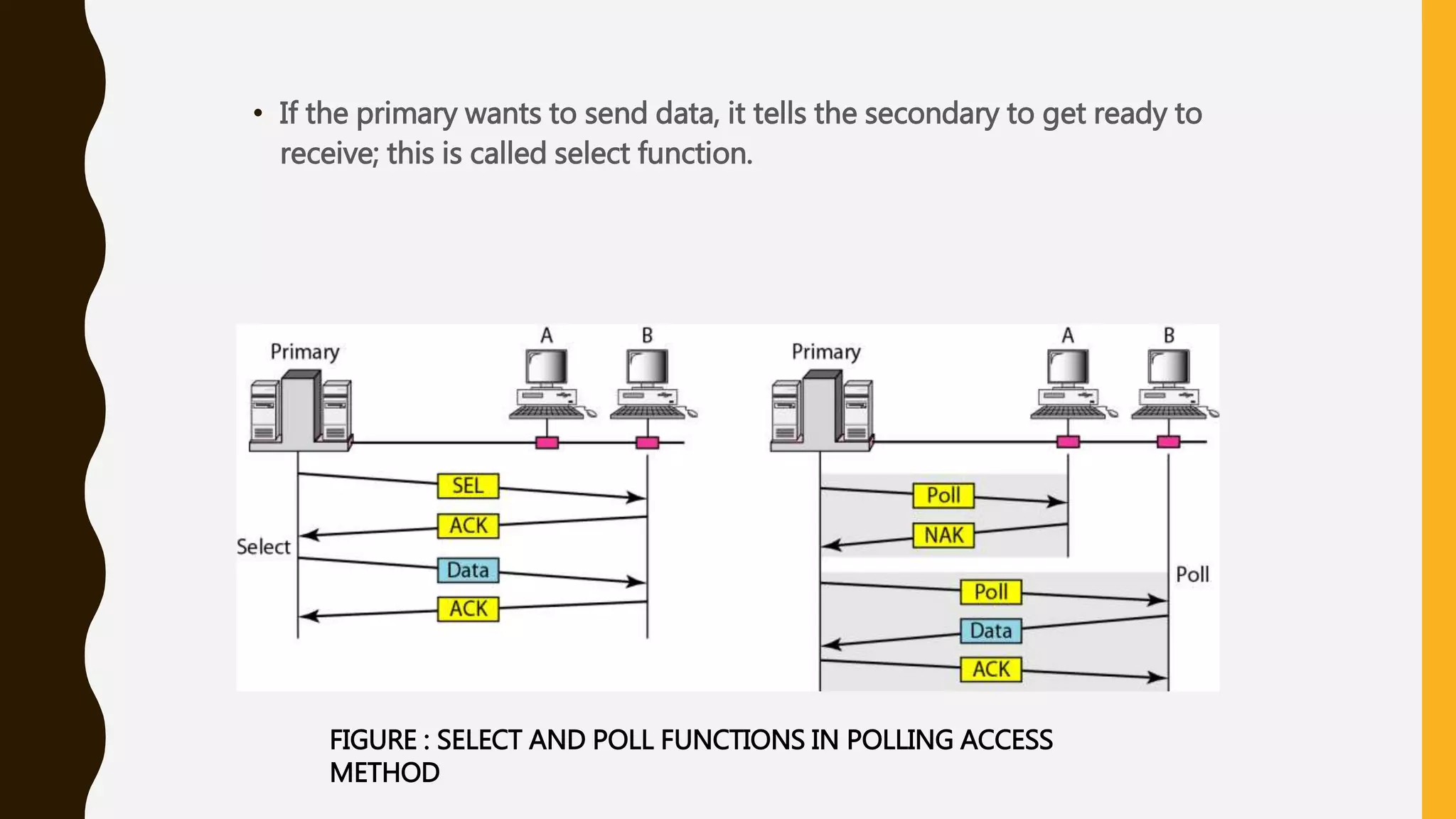
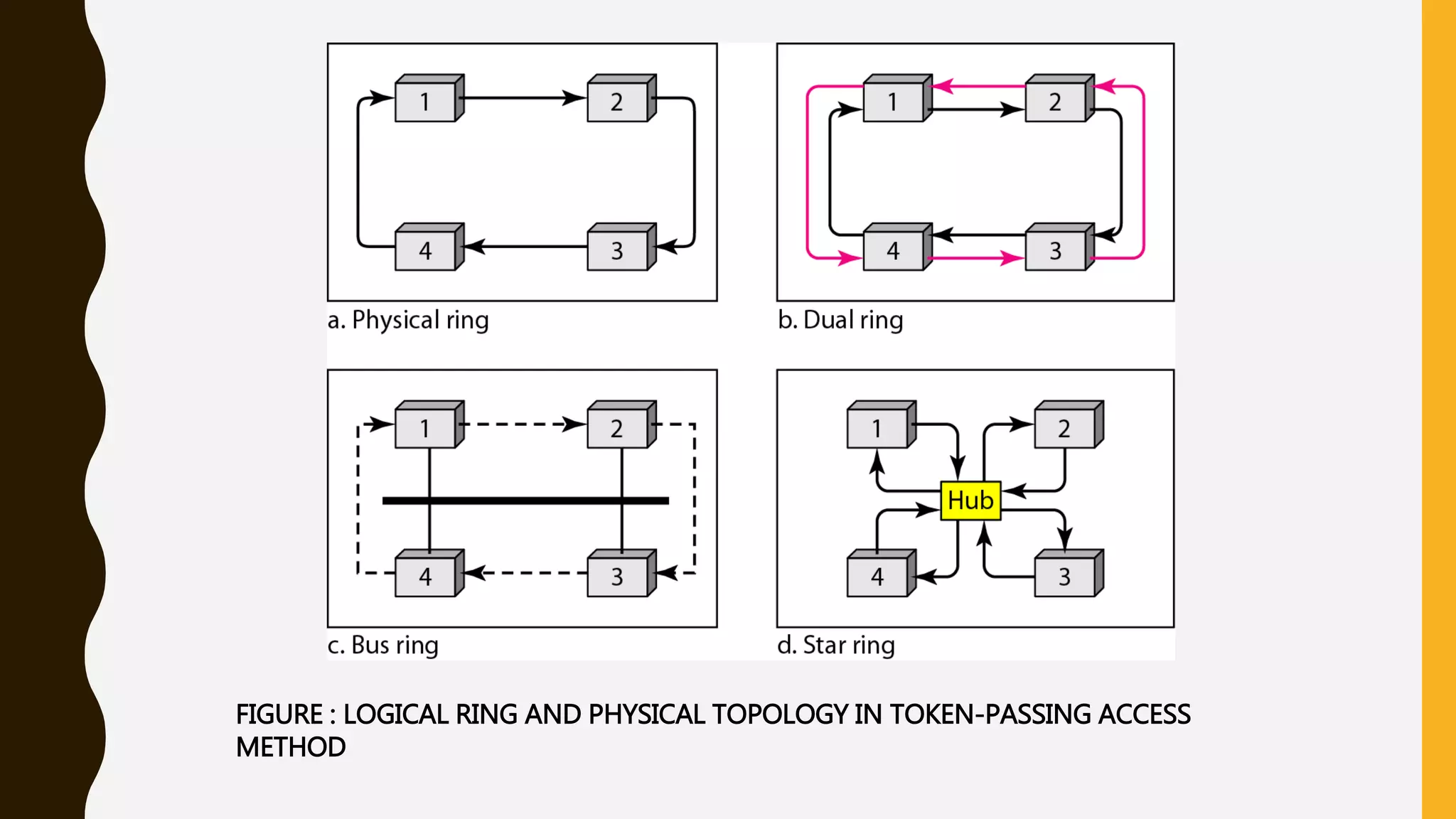
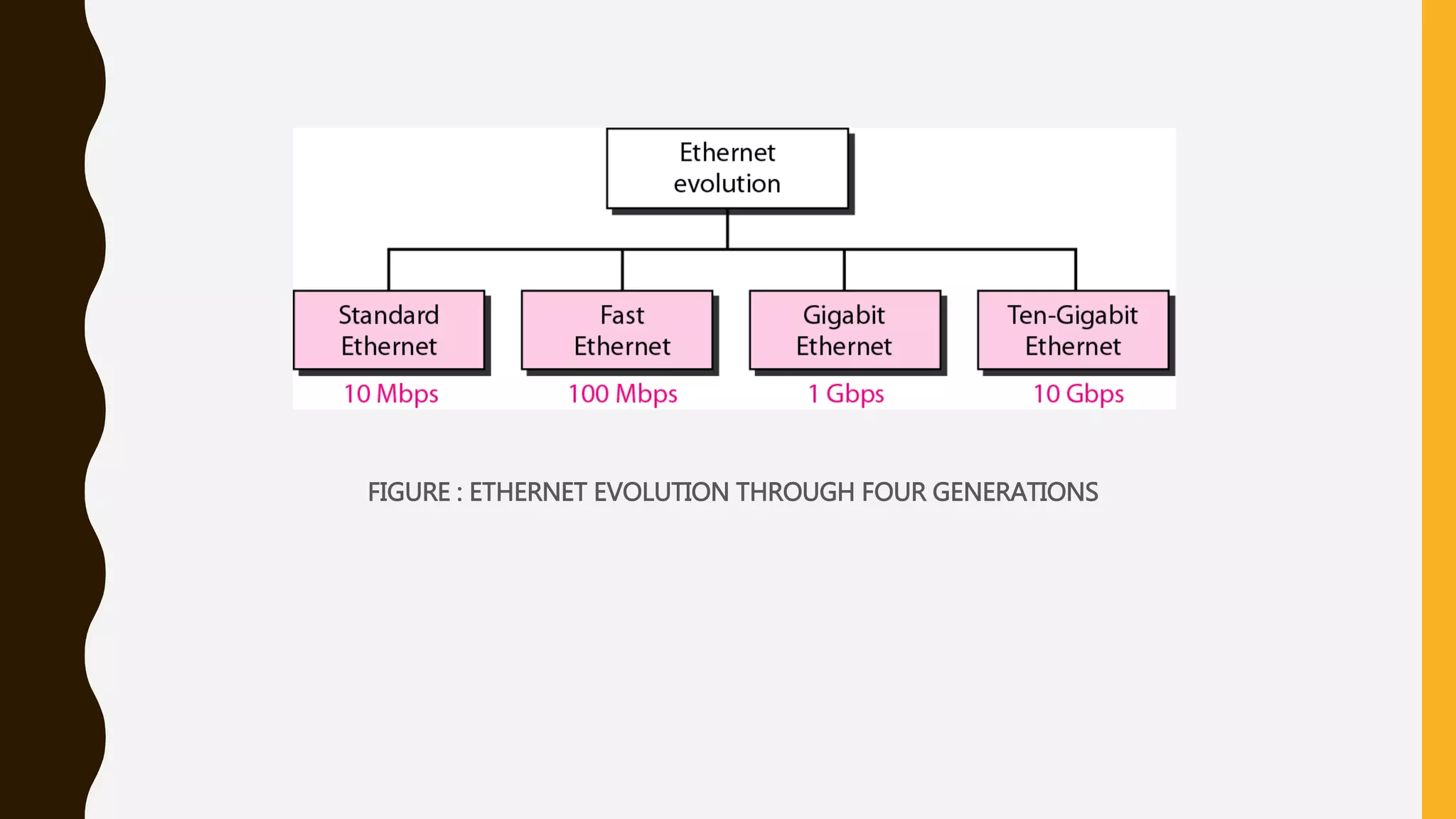
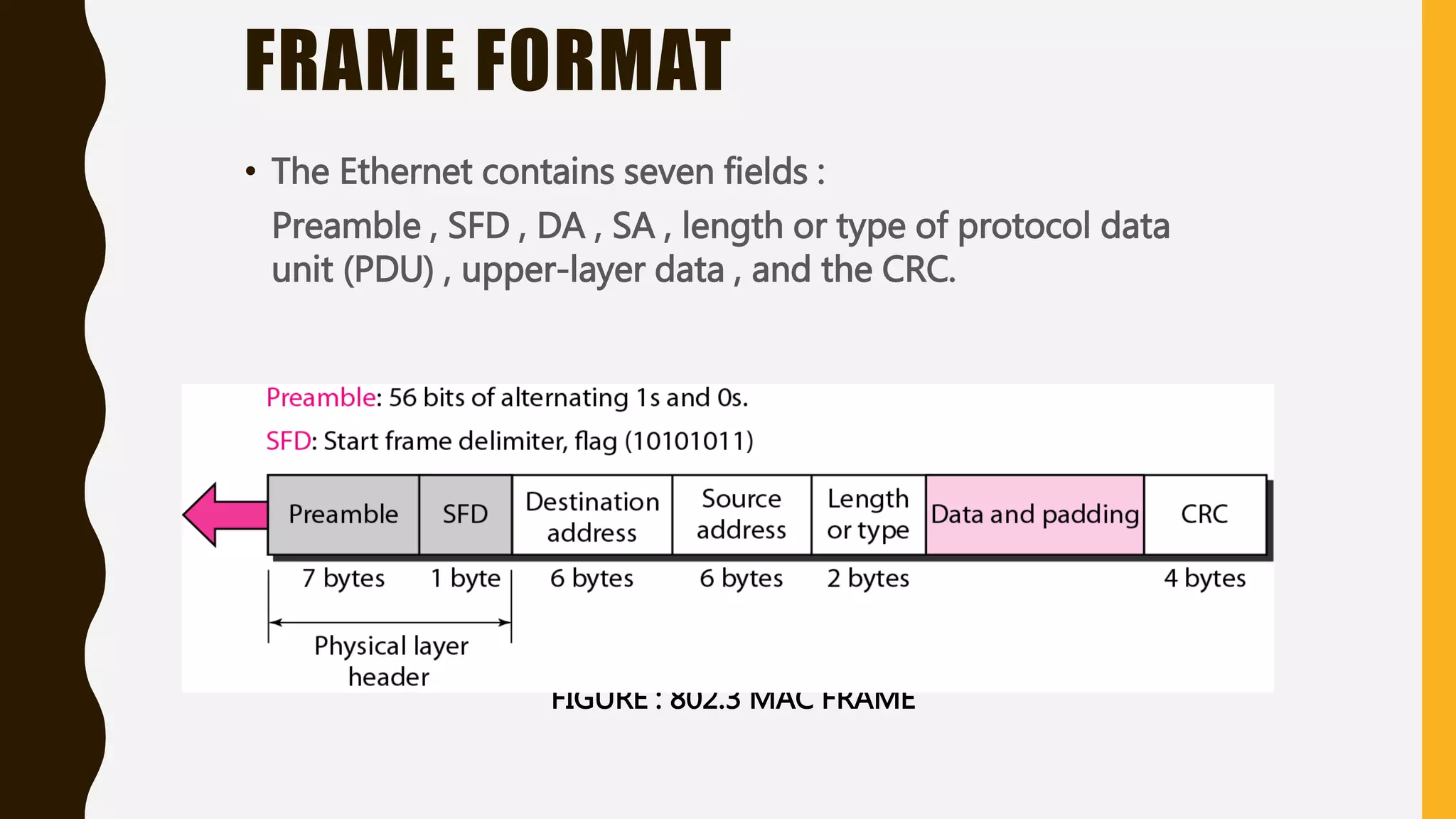
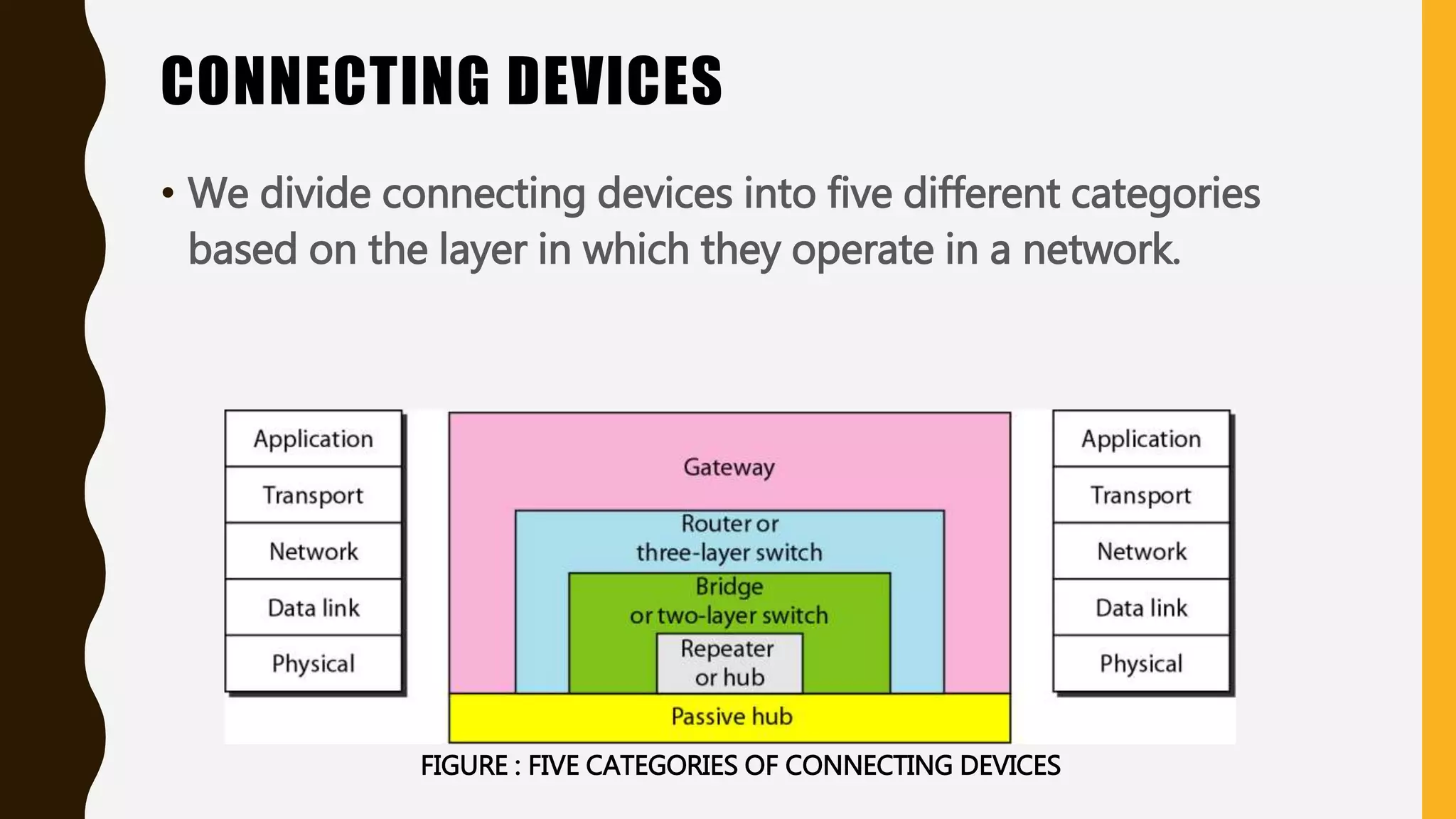
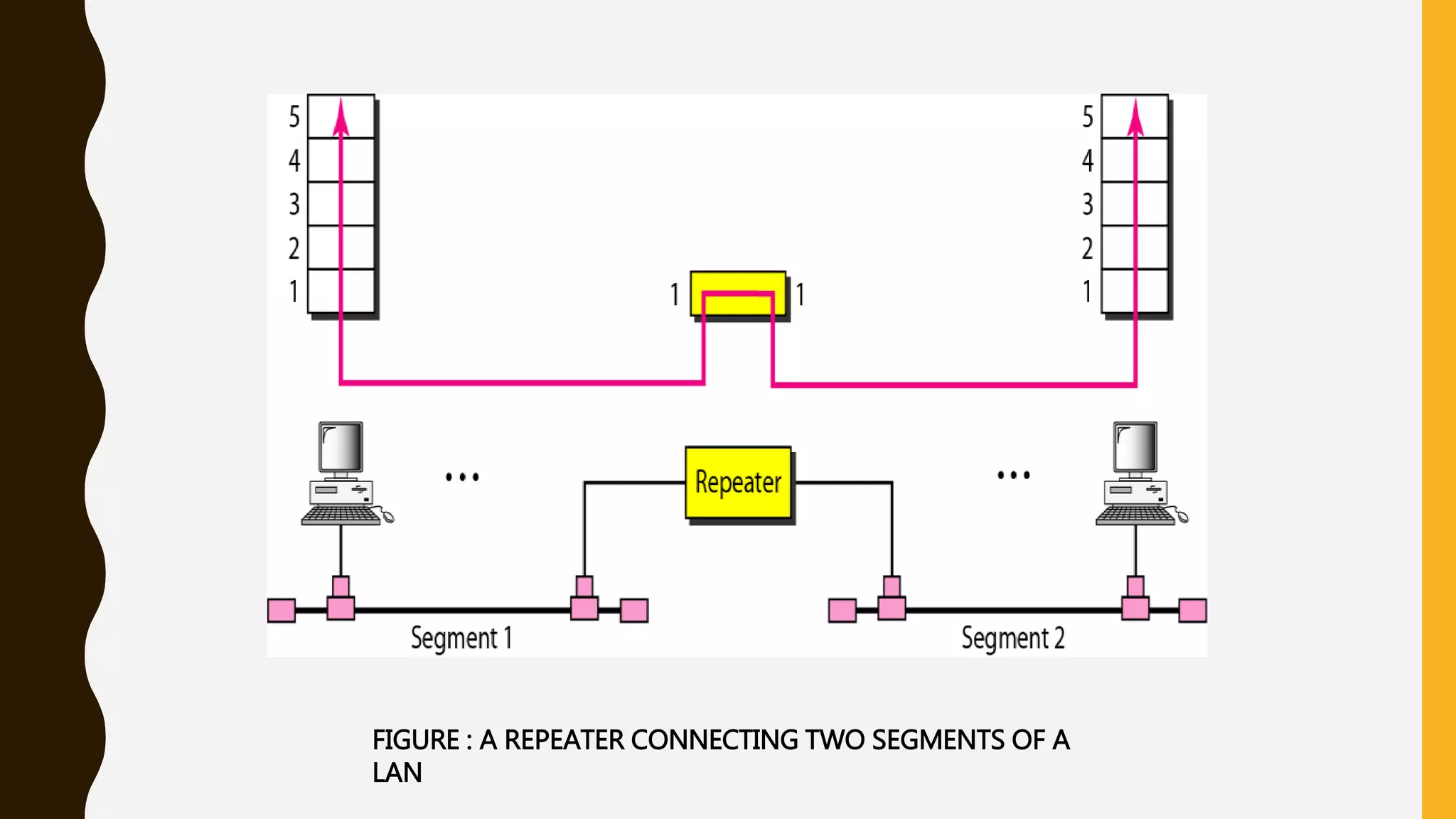
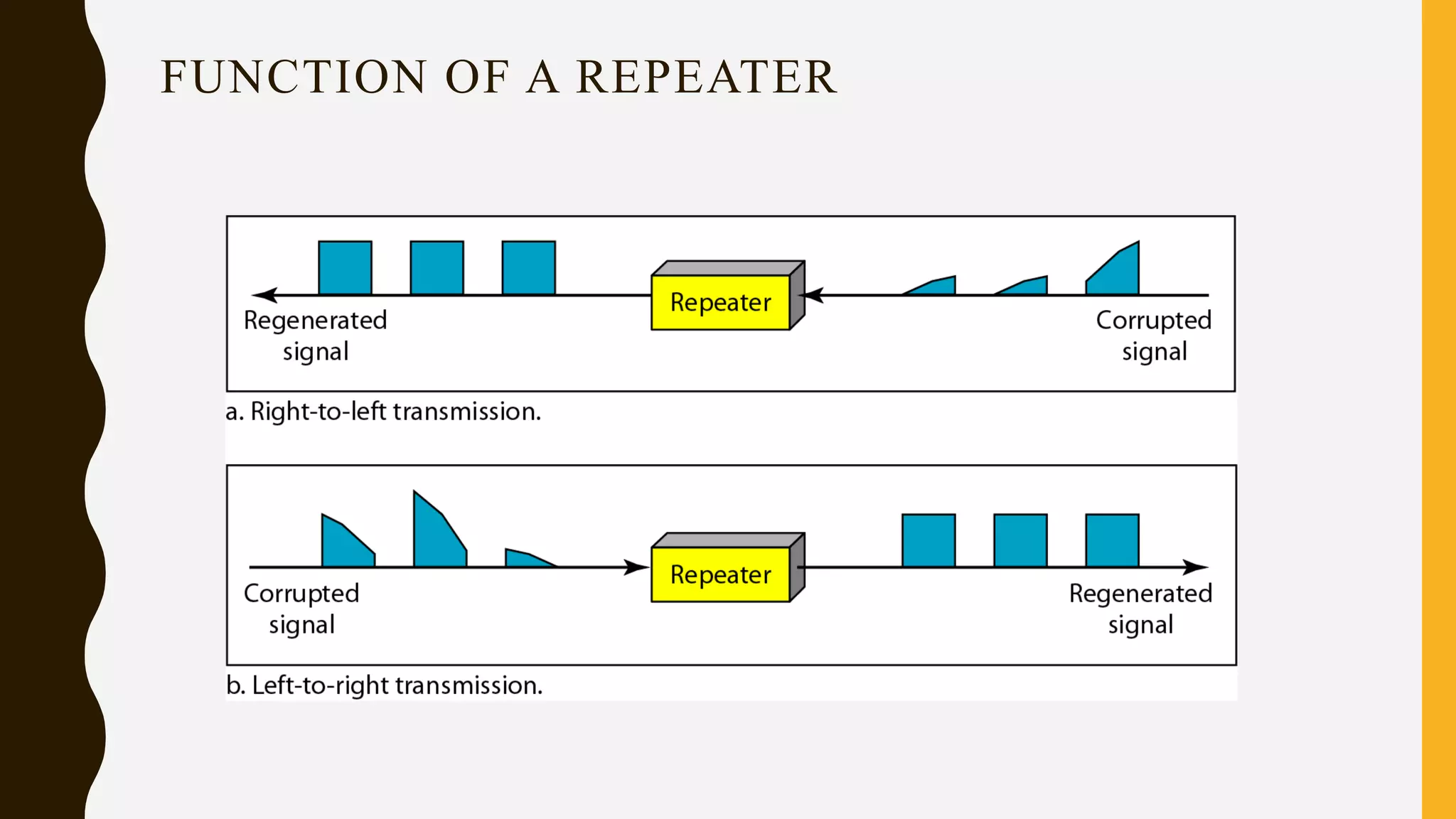
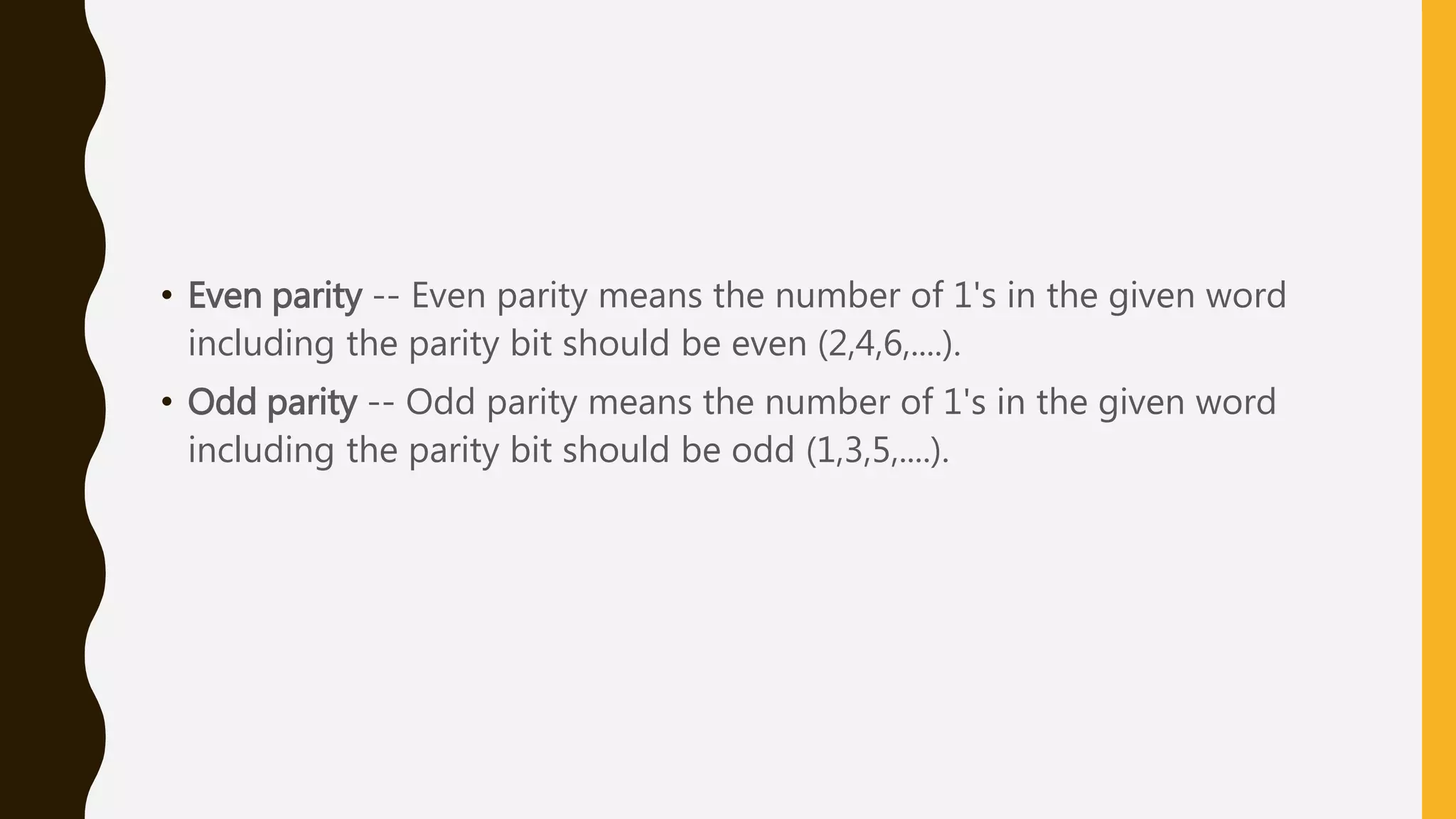The document discusses various aspects of the data link layer and error detection and correction mechanisms used for reliable communication, including types of errors like single bit and burst errors. It explains techniques such as block coding, simple parity-check, Hamming code, and cyclic codes, along with automatic repeat requests (ARQ) methods like stop-and-wait and go-back-n. Additionally, it covers access methods like point-to-point protocols, random access techniques, and the role of connecting devices such as hubs, bridges, routers, and gateways in networks.