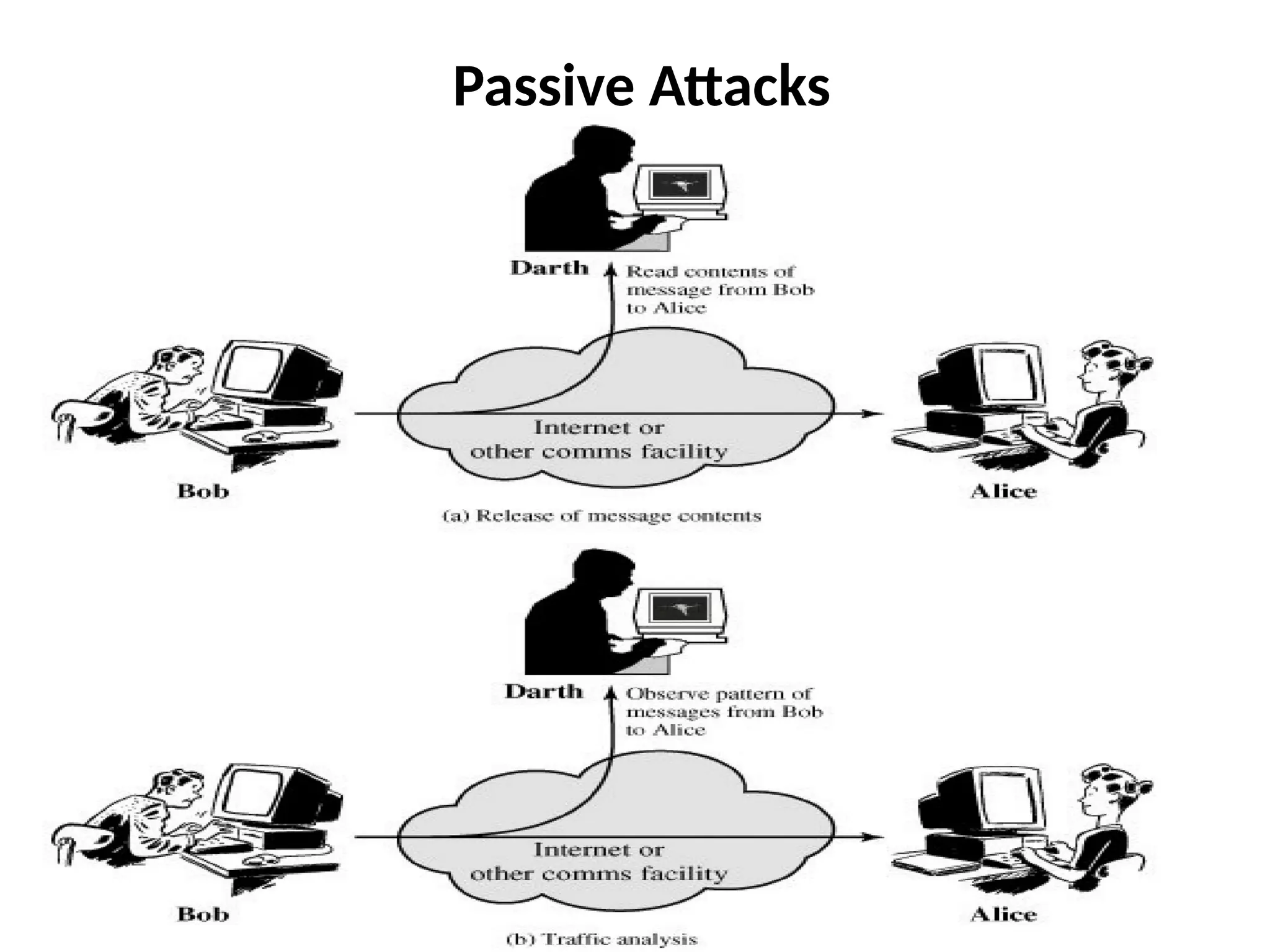
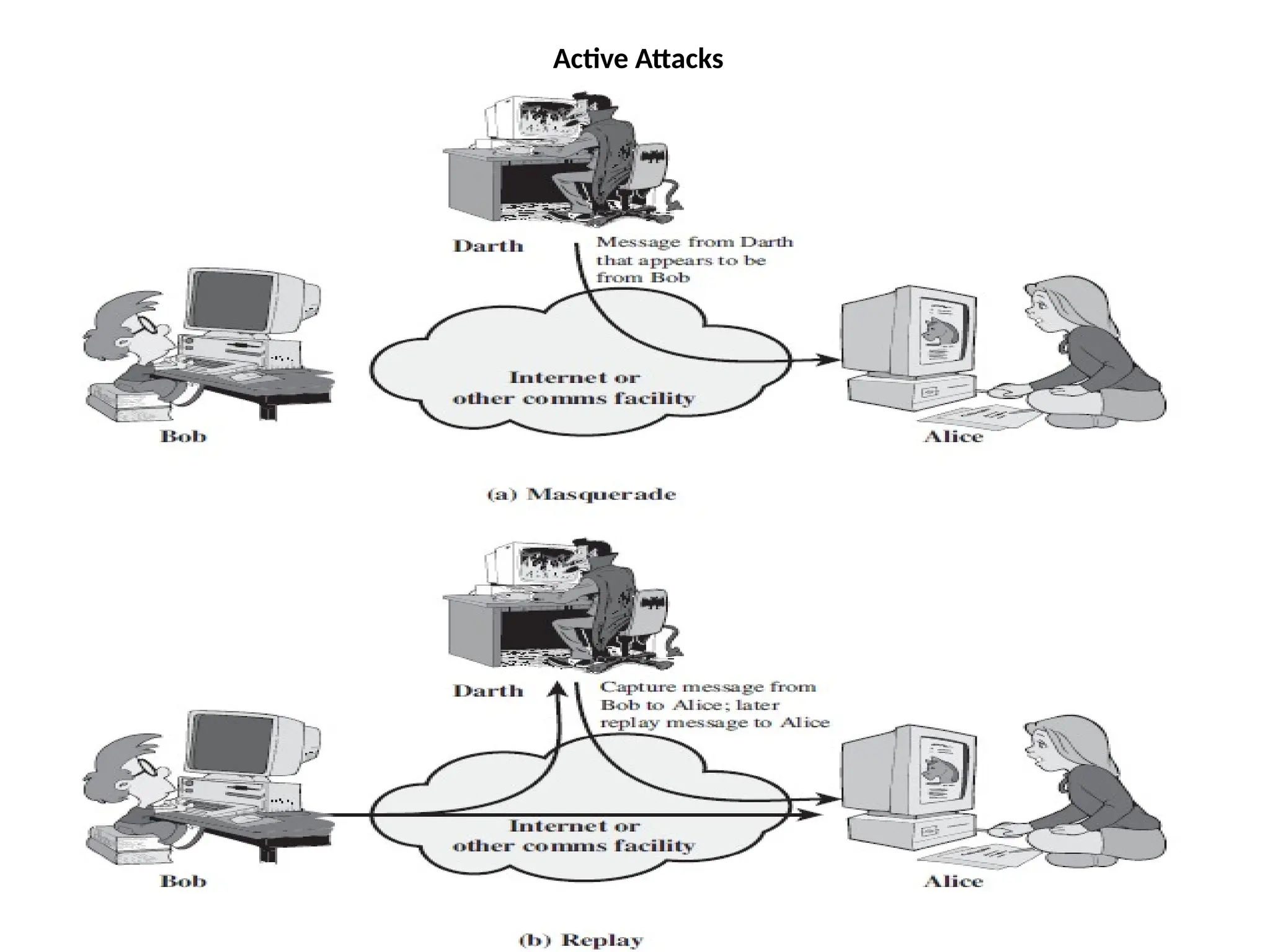
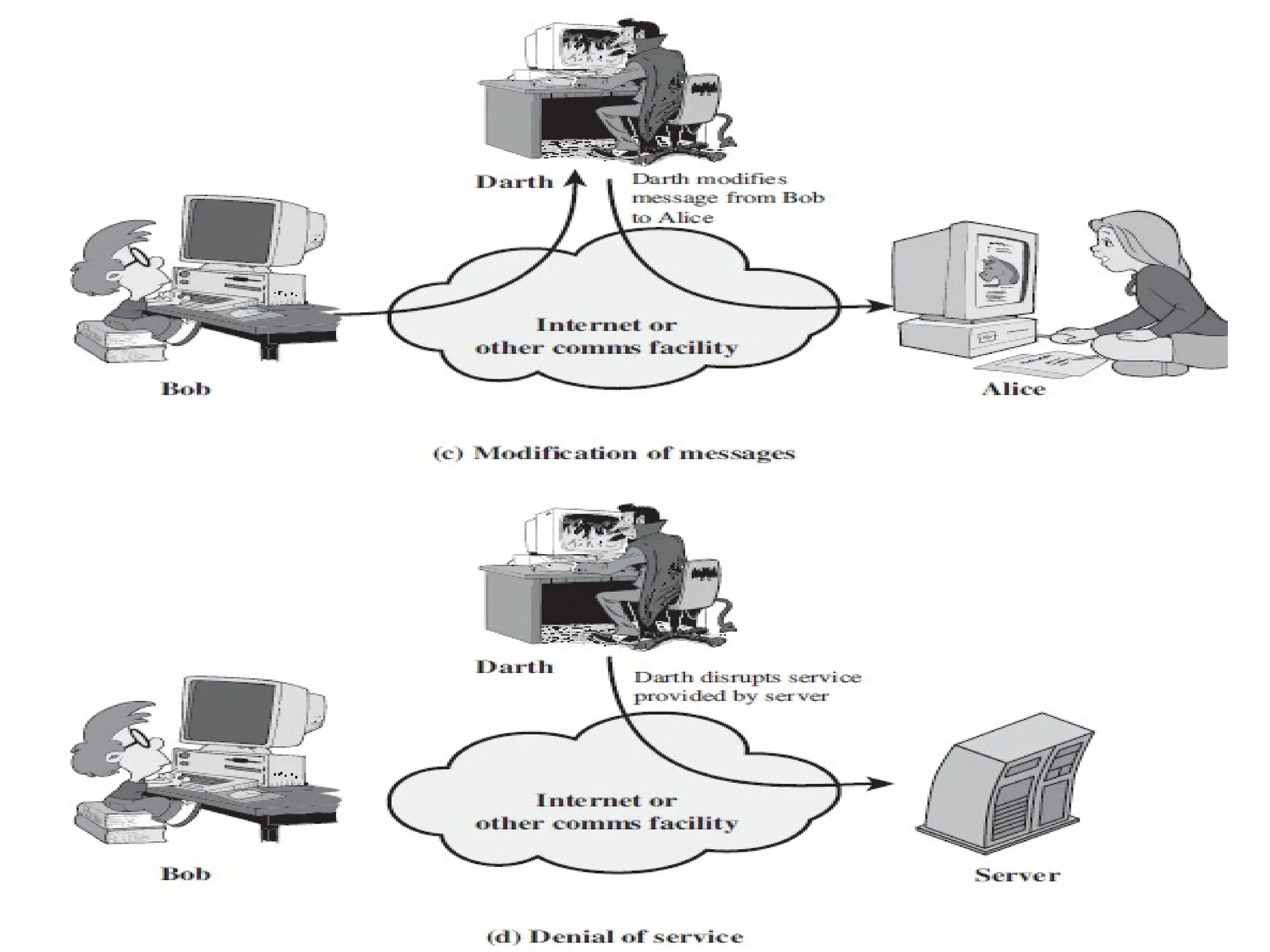
The document discusses threats and attacks on system security, distinguishing between potential threats and deliberate attacks that exploit vulnerabilities. It categorizes attacks into passive attacks, which involve eavesdropping on information without altering it, and active attacks, which modify data or disrupt services. Passive attacks can include message content release and traffic analysis, while active attacks can involve masquerading, replaying data, modifying messages, and denial of service.