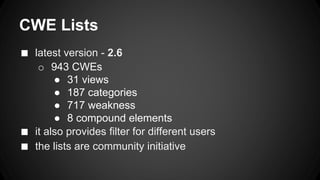
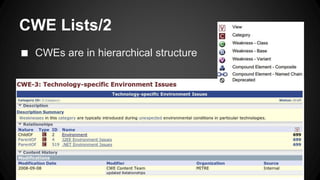
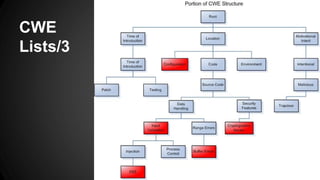
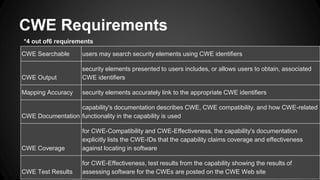
The document discusses the Common Weakness Enumeration (CWE), which provides a list of common software weaknesses. It describes CWE as a standard for describing weaknesses, and notes that CWE works with CVE to map vulnerabilities to specific weaknesses. The document also outlines the CWE process, lists, overviews, requirements, and lists 10 organizations with CWE-compatible security tools.