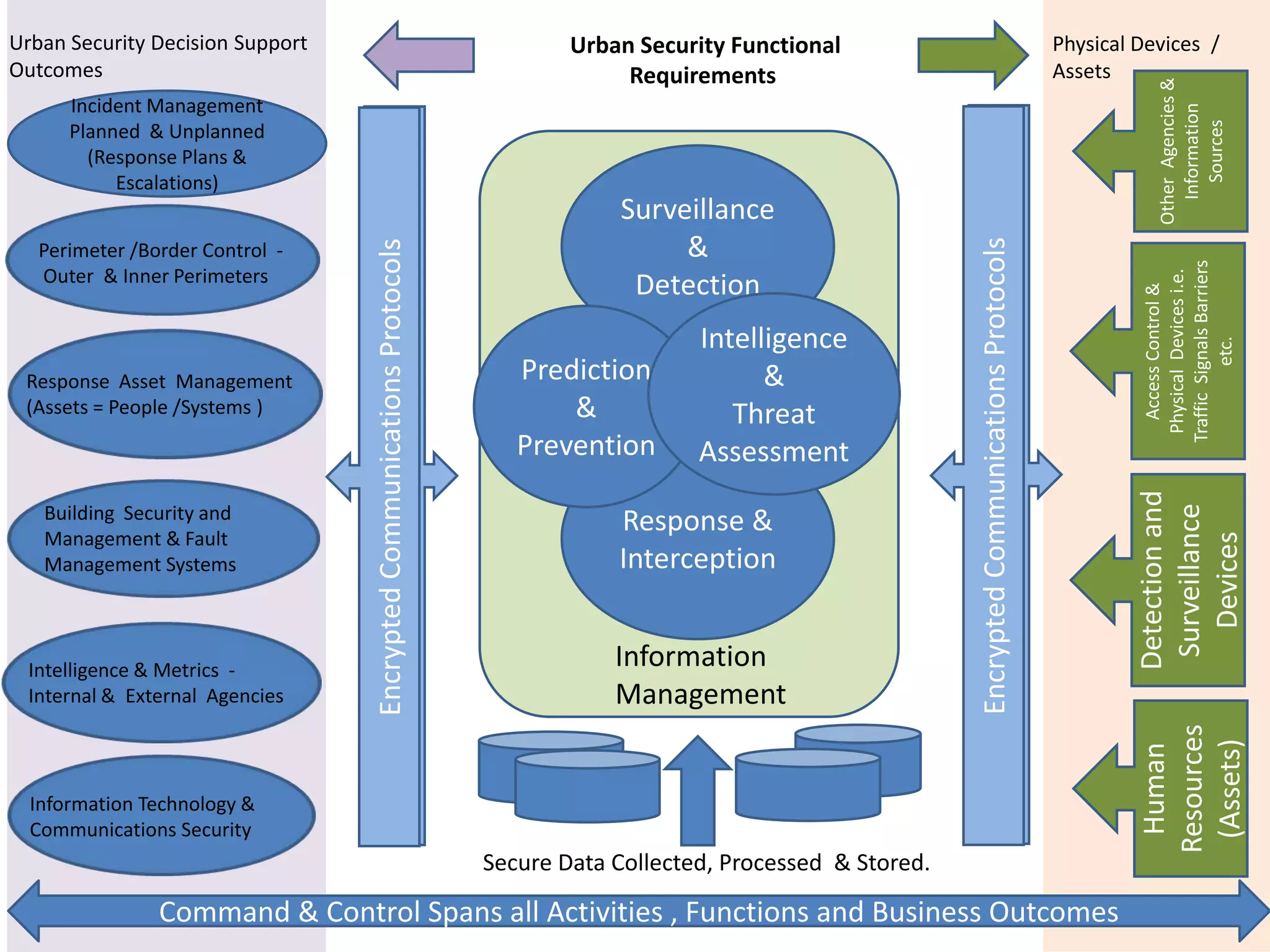
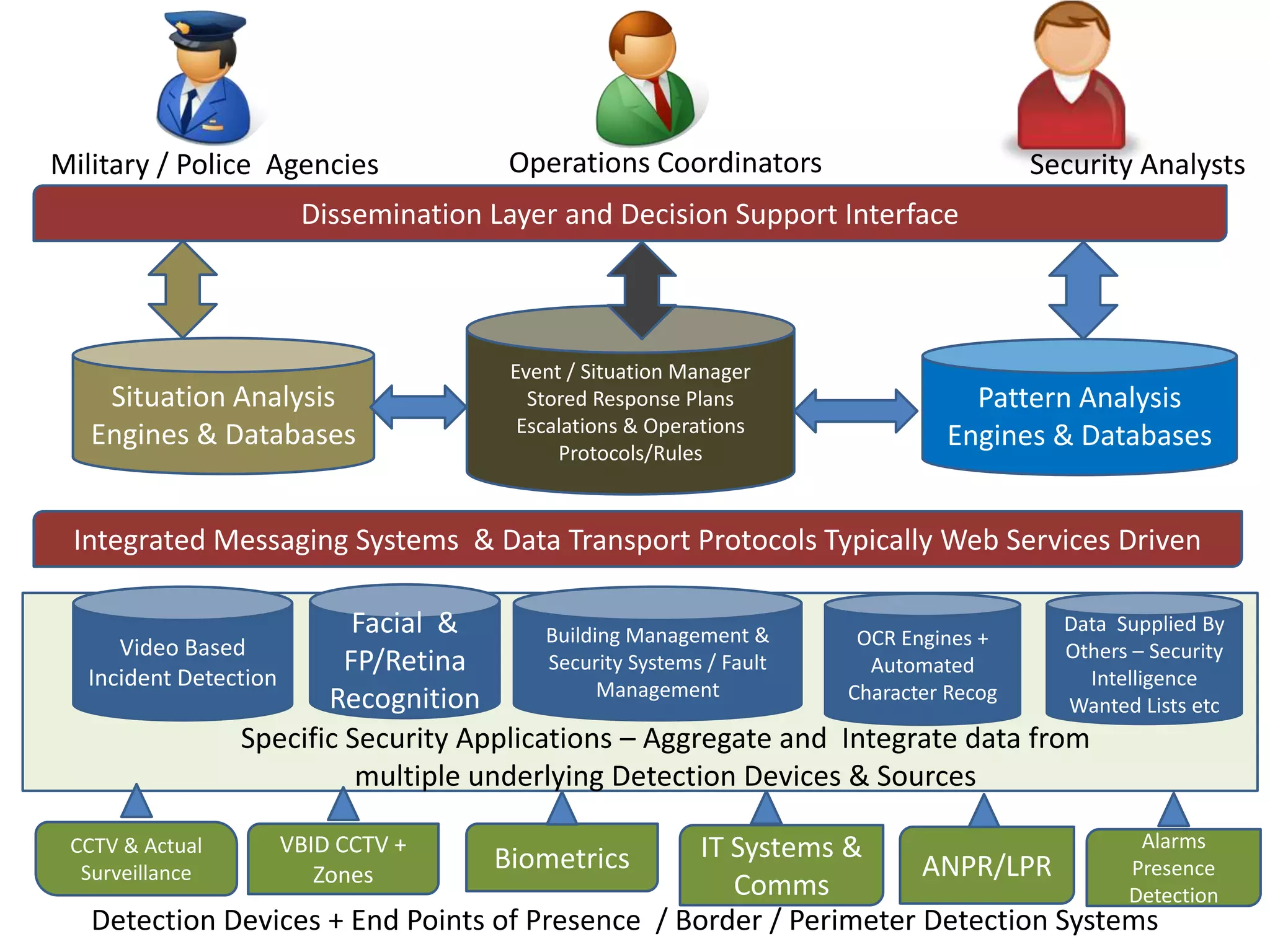
The document outlines the key components and functions of an urban security decision support system, including physical security devices and assets, incident management protocols, encrypted communications, surveillance and detection systems, perimeter control, intelligence analysis, response management of assets like people and systems, building security management, information management with internal and external agencies, IT and communications security, command and control spanning all activities, and a dissemination layer and decision support interface. The system utilizes detection devices, surveillance cameras, biometrics, databases, and analytics to monitor incidents and threats and support response decisions.