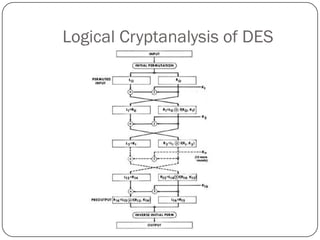
This document discusses combinatorial design problems and approaches to solving them. It introduces combinatorial problems and challenges like huge search spaces. Methods covered include modeling problems as constraint satisfaction problems (CSPs) and using constraint propagation to reduce the search space. Specific problems discussed include ternary Steiner systems, Hamming distance optimization, and modeling the Data Encryption Standard (DES) cipher as a SAT problem for cryptanalysis.





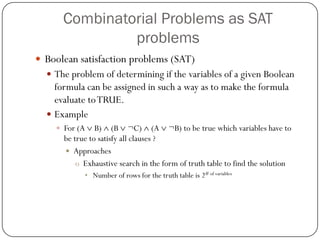
![Constraint satisfaction problem (CSP) vs. Generate & Test
15 variables [V1,..,V15] all taking values in the domain {1,..,15}
V1<V2, V2<V3, …, V14<V15
Generate & Test Approach
Enumerating all possible assignments
1515= 437,893,890,380,859,375 possibility
109assignments/second computer would need 14 years to find solution](https://image.slidesharecdn.com/503be31d-3ffb-4a82-934f-0374a1507d90-141209163947-conversion-gate01/85/Combinatorial-Problems2-6-320.jpg)








![Hamming Distance Optimization problem
How to model this ?
Using set variables (Si) to represent code words (Ci)
The element x is in the set Si iffthe code Cihas a 1 at position x
[0000]->S={}
[1000]->S={1}
[0100]->S={2}
[1100]->S={1,2}](https://image.slidesharecdn.com/503be31d-3ffb-4a82-934f-0374a1507d90-141209163947-conversion-gate01/85/Combinatorial-Problems2-17-320.jpg)
![Hamming Distance Optimization problem
Example
a(4,1,1)
How many code words of length 4 , minimal distance of 1 and weight 1 ?
[1000]S = {1}
[0100]S = {2}
[0010]S = {3}
[0001]S = {4}
Answer = 4](https://image.slidesharecdn.com/503be31d-3ffb-4a82-934f-0374a1507d90-141209163947-conversion-gate01/85/Combinatorial-Problems2-18-320.jpg)