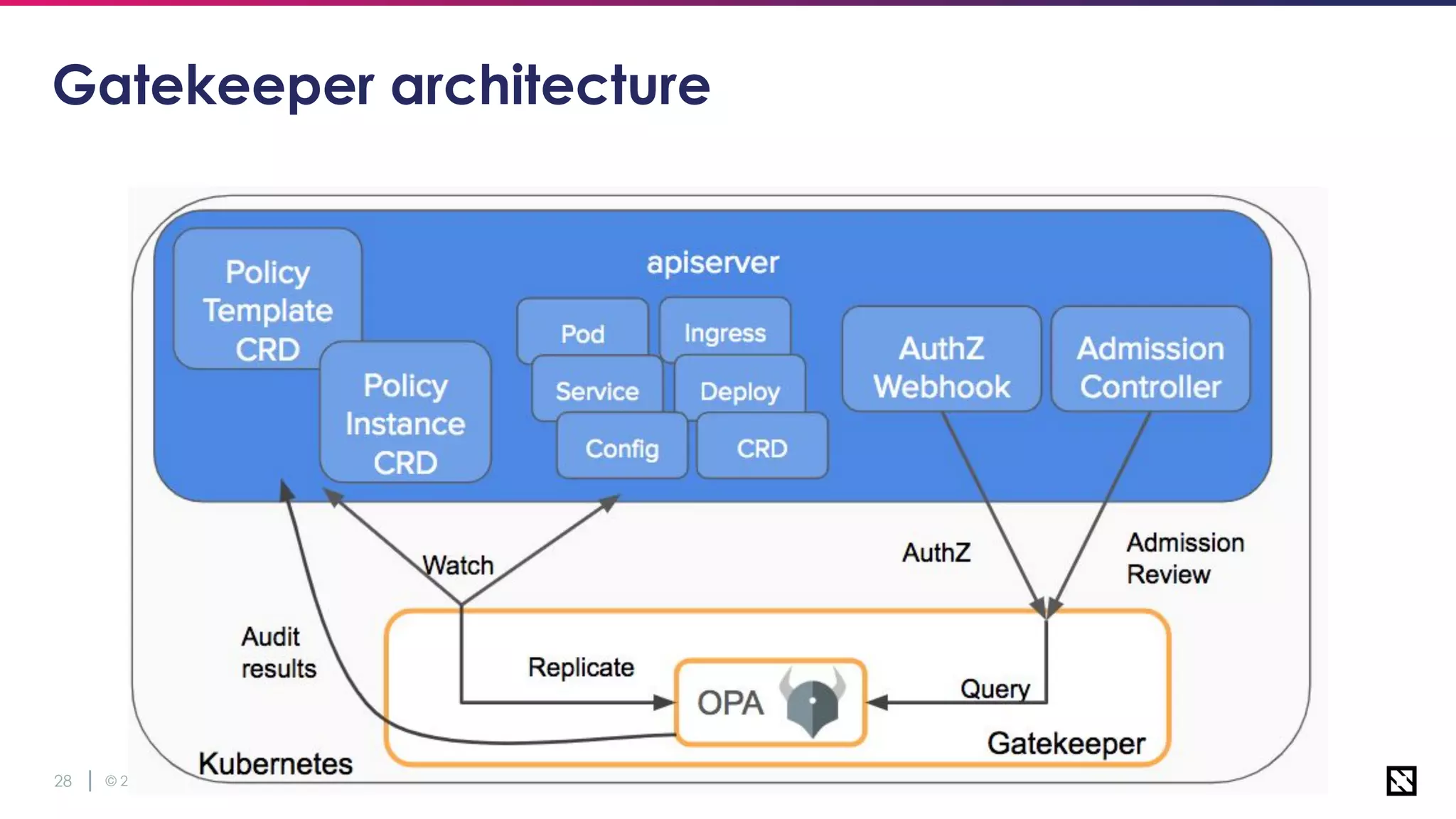
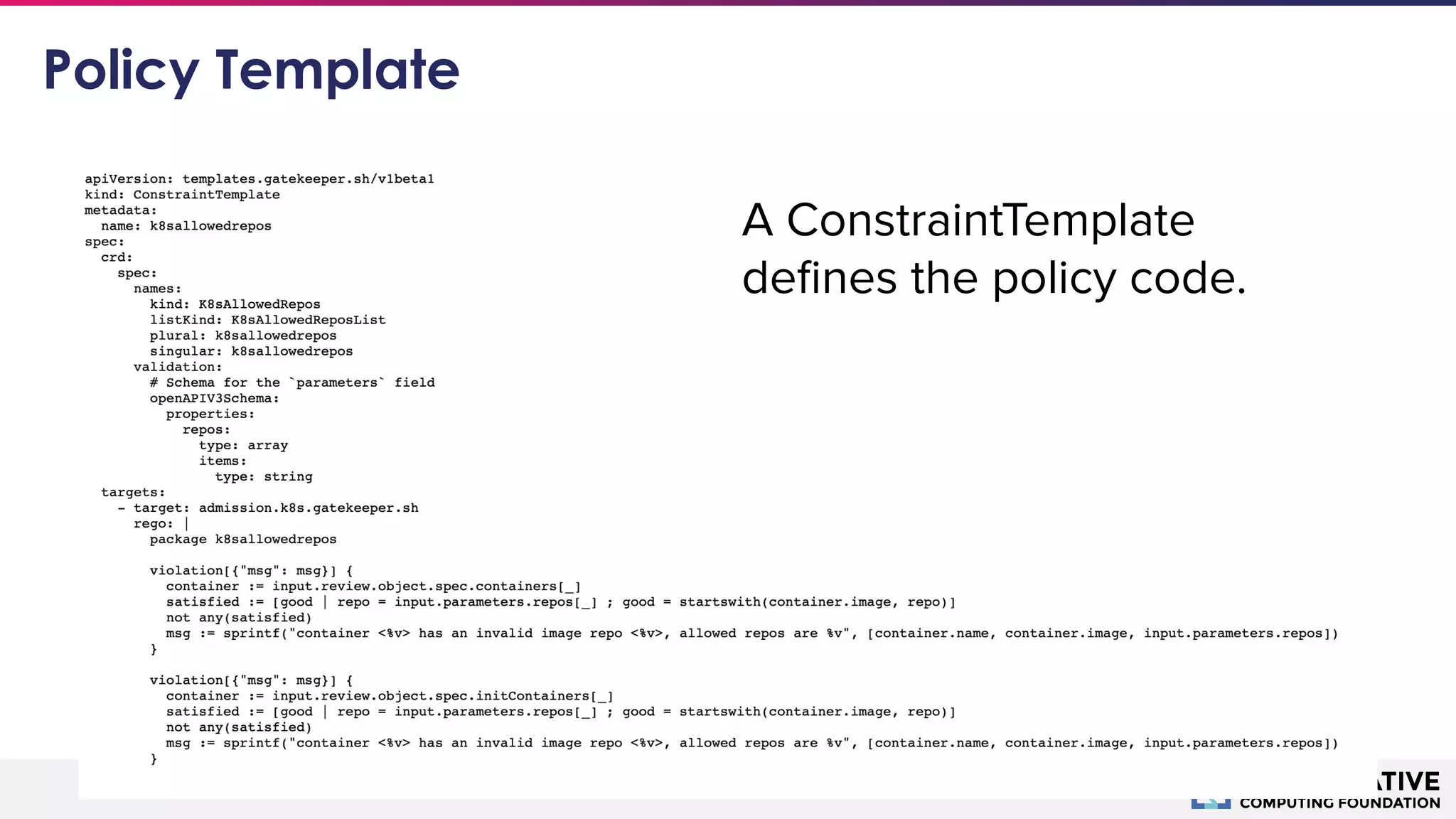
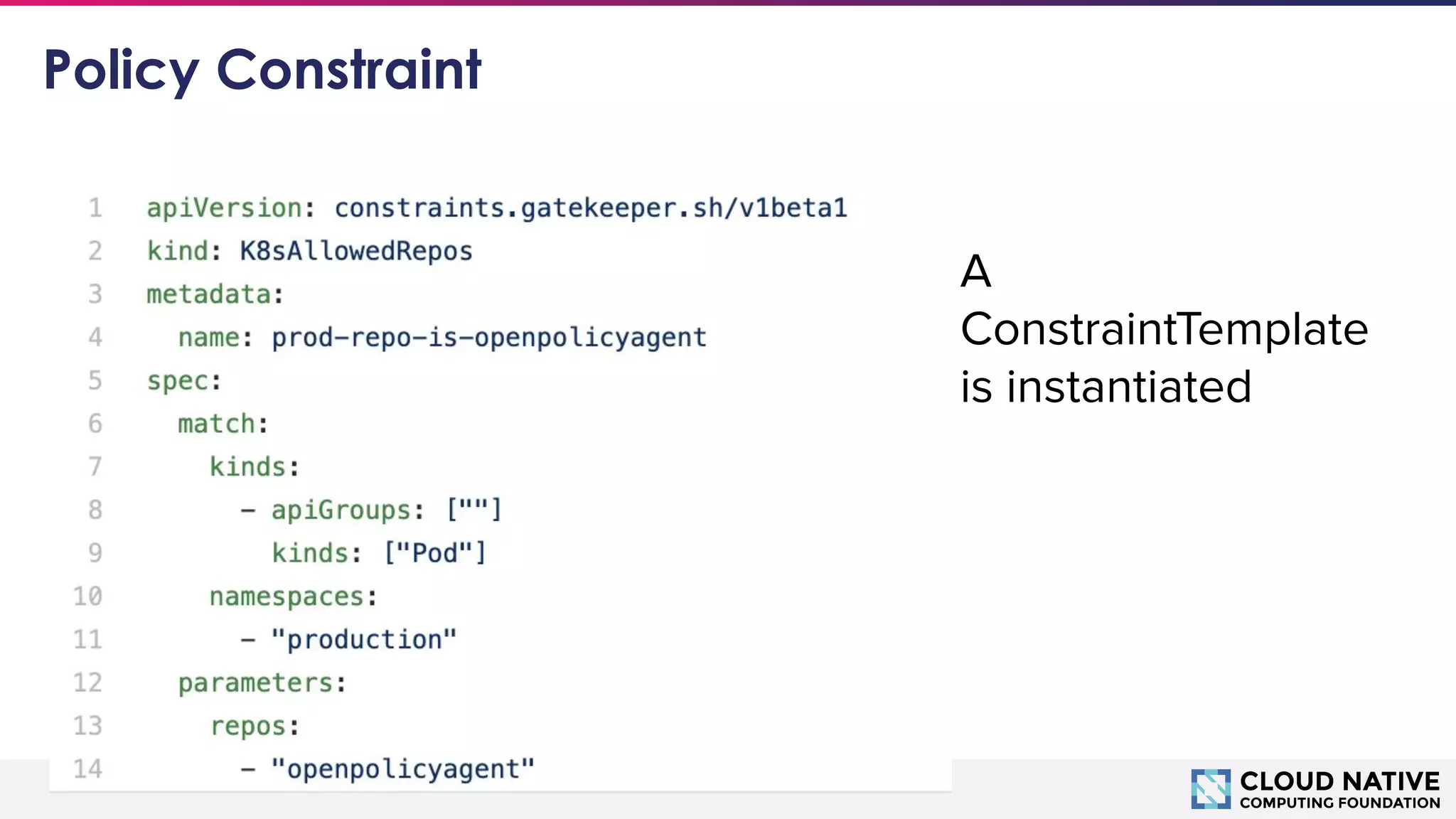
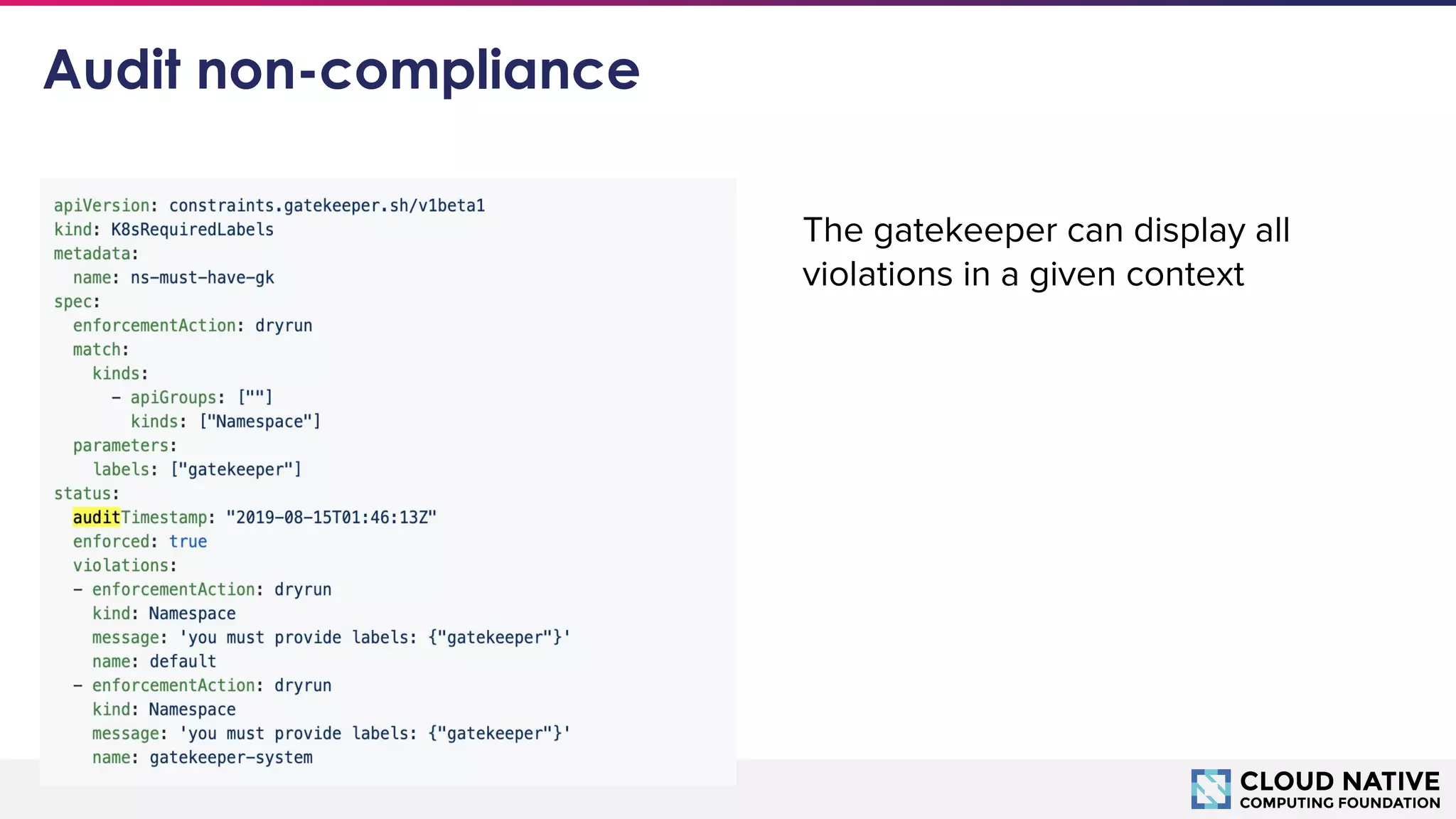
The document discusses microservices security focusing on Open Policy Agent (OPA) and service mesh architecture, emphasizing the importance of policies for access control and service communication in a cloud-native environment. It outlines the IAAA framework and introduces key concepts such as mutual TLS, identity propagation, and compliance requirements for Kubernetes resources. Key takeaways include the growing adoption of OPA for policy as code, specifically for user authorization, service mesh governance, and organizational compliance.










![© 2018 Cloud Native Computing Foundation23
Example: JWT Validation
package istio.authz
import input.attributes.request.http as http_request
import input.attributes.source.address as source_address
certificate = `-----BEGIN CERTIFICATE-----
MIICmzCC
-----END CERTIFICATE-----`
constraint = {
"cert": certificate,
"alg": "RS256",
"aud": "account"
}
jwt_string = jwt_token {
[jwt_token] := split(http_request.headers["x-access-token"], " ")
}
# Decode Token
parsed_token = token {
[jose, payload, sig] := io.jwt.decode(jwt_string)
token = {
"jose" : jose,
"payload" : payload,
"sig": sig
}
}
valid_token = payload {
[valid, header, payload] := io.jwt.decode(jwt_string)
}
valid_auds [valid_aud] {
valid_aud := parsed_token.payload.aud[_]
group := parsed_token.payload.groups[_]
required_roles[group]
io.jwt.verify_rs256(jwt_string, certificate)
}
required_roles[r] {
perm := role_perms[r][_]
perm.method = http_request.method
perm.path = http_request.path
}
role_perms = {
"/Normal": [
{"method": "GET", "path": "/"},
{"method": "GET", "path": "/productpage?u=normal"},
],
"/Moderators": [
{"method": "GET", "path": "/productpage?u=test"},
{"method": "GET", "path": "/"},
{"method": "GET", "path": "/api/v1/products"},
],
}
default allow = {
"allowed": false,
"headers": {"x-ext-auth-allow": "no"},
"body": "Unauthorized Request",
"http_status": 301
}
}
1
2
4
3](https://image.slidesharecdn.com/cncfmicroservicessecurity-200603234531/75/Cncf-microservices-security-23-2048.jpg)