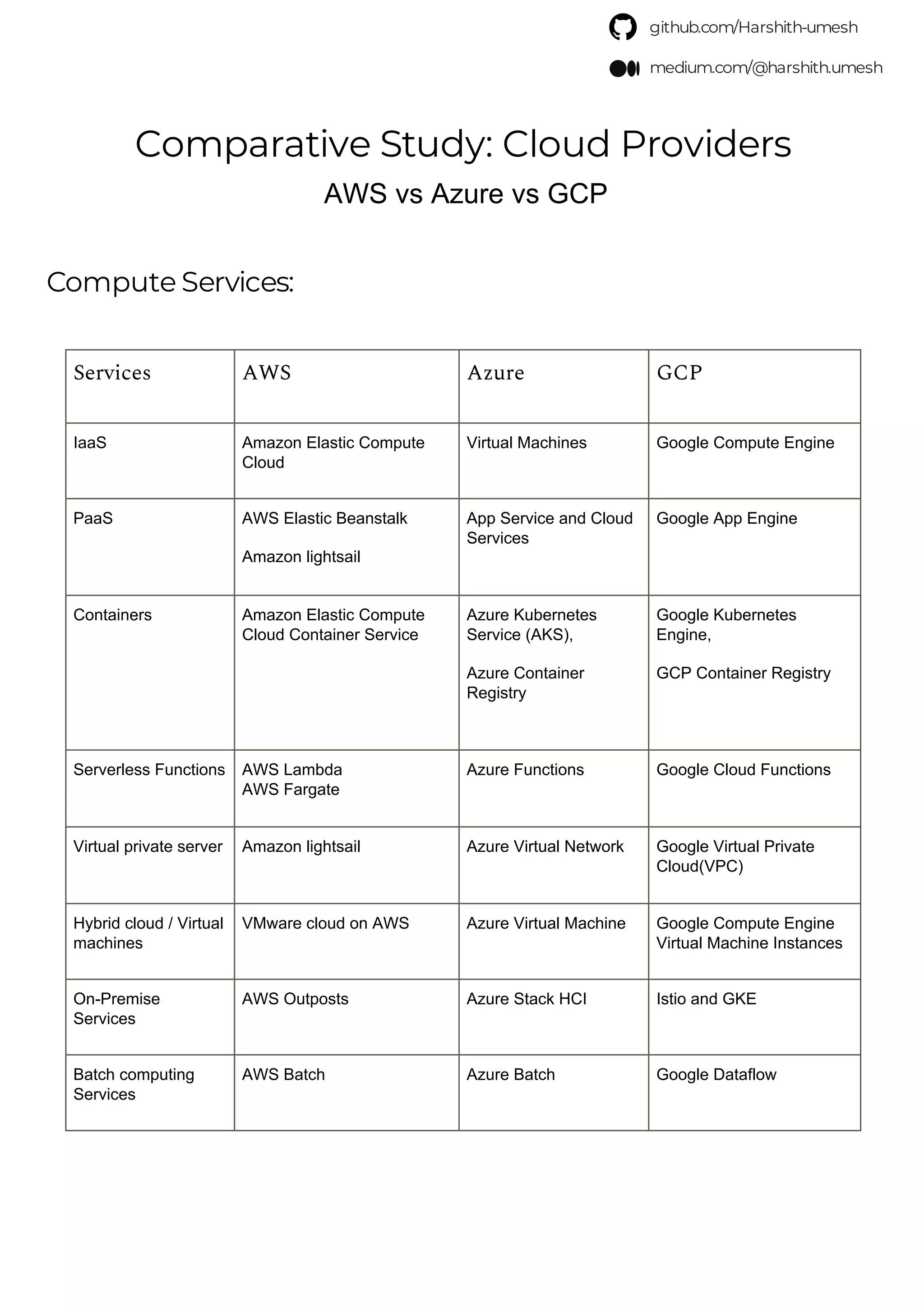
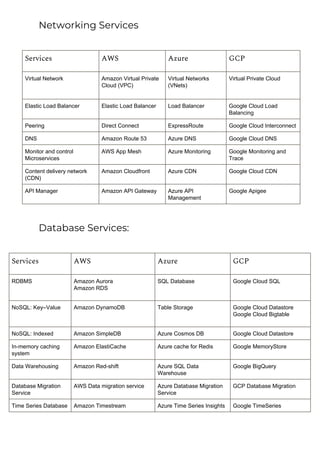
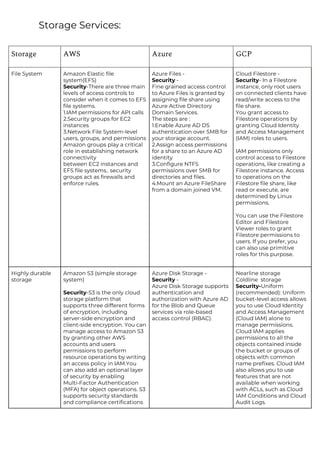
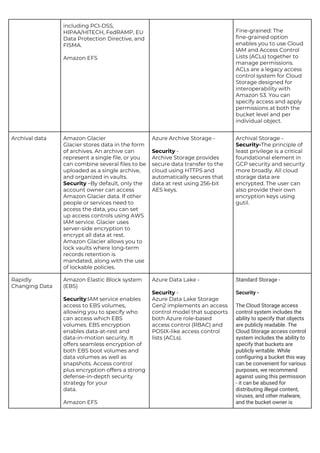
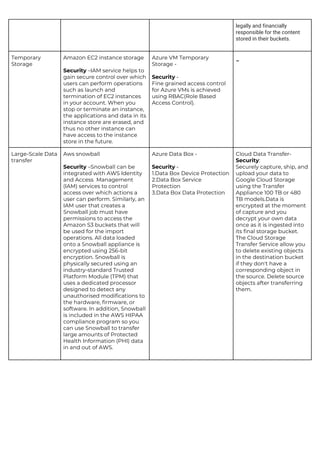
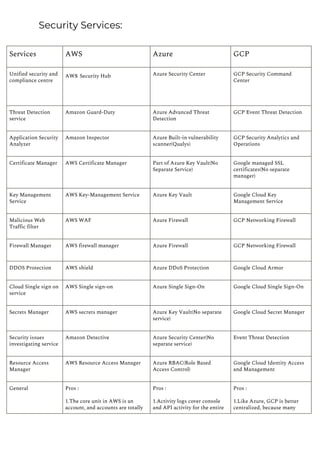
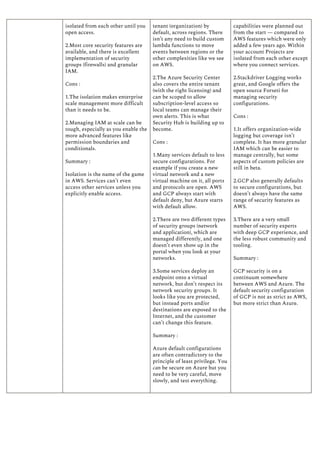
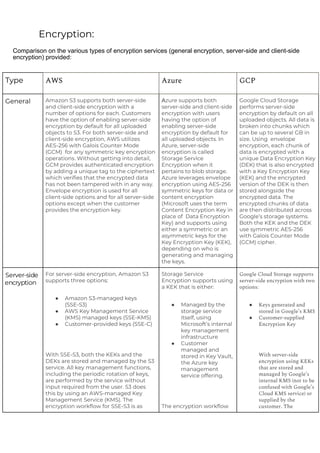
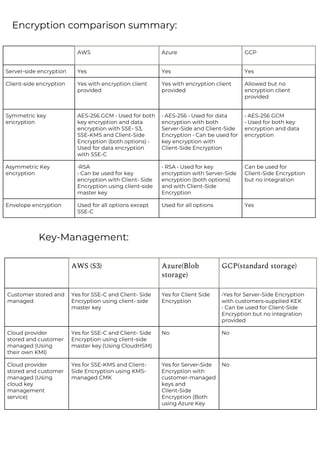
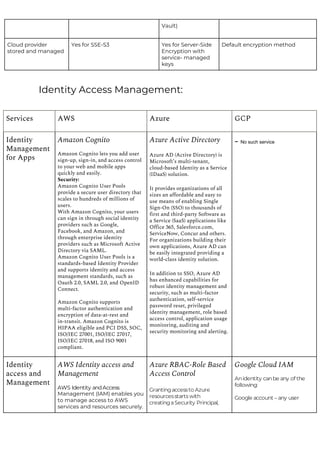
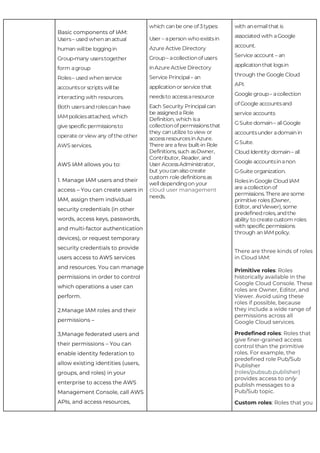
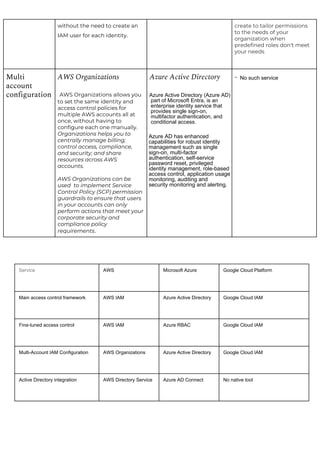
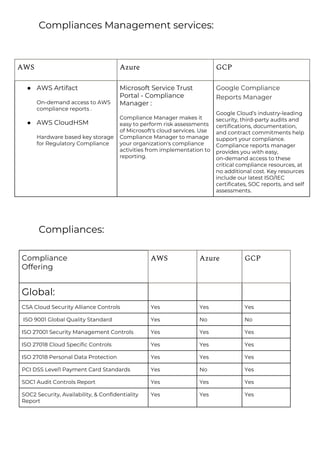
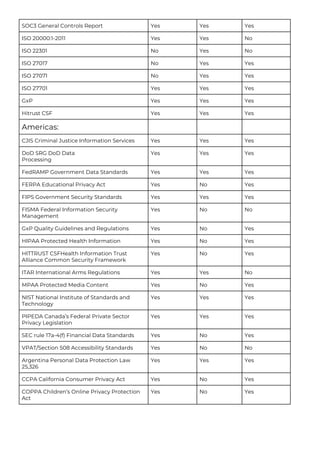
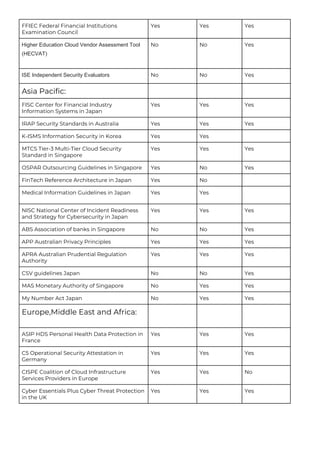
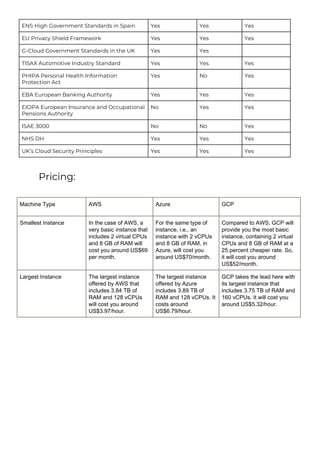
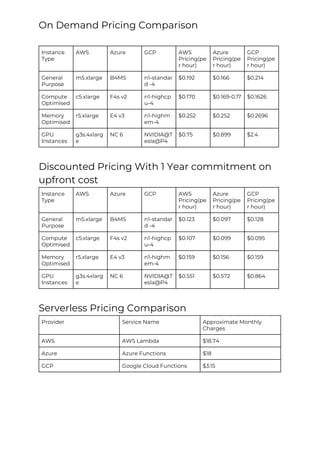
This document provides a comparison of services offered by major cloud providers AWS, Azure and GCP across various categories like compute, storage, databases, networking, security etc. It lists and briefly describes the analogous services offered by each cloud provider within each category. For example, for compute it lists EC2, Lightsail and ECS for AWS, Virtual Machines and AKS for Azure and Compute Engine and GKE for GCP. The document acts as a one-stop reference for understanding the services landscape across different cloud providers.