Cloud security part one
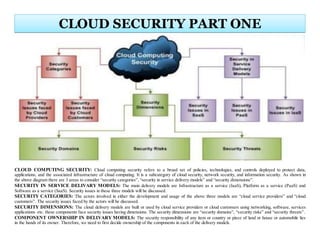
- 1. CLOUD COMPUTING SECURITY: Cloud computing security refers to a broad set of policies, technologies, and controls deployed to protect data, applications, and the associated infrastructure of cloud computing. It is a subcategory of cloud security, network security, and information security. As shown in the above diagram there are 3 areas to consider “security categories”, “security in service delivery models” and “security dimensions”. SECURITY IN SERVICE DELIVARY MODELS: The main delivery models are Infrastructure as a service (IaaS), Platform as a service (PaaS) and Software as a service (SaaS). Security issues in these three models will be discussed. SECURITY CATEGORIES: The actors involved in either the development and usage of the above three models are “cloud service providers” and “cloud customers”. The security issues faced by the actors will be discussed. SECURITY DIMENSIONS: The cloud delivery models are built or used by cloud service providers or cloud customers using networking, software, services applications etc. these components face security issues having dimensions. The security dimensions are “security domains”, “security risks” and “security threats”. COMPONENT OWNERSHIP IN DELIVARY MODELS: The security responsibility of any item or country or piece of land or house or automobile lies in the hands of its owner. Therefore, we need to first decide ownership of the components in each of the delivery models. CLOUD SECURITY PART ONE
- 2. OWNERSHIP OF SECURITY IN DELIVARY MODELS: In the below Picture “cloud security” in the dotted box shows the security responsibilities of IaaS(Network & Infrastructure) Example: You purchased a piece of land where roads, power and other facilities are provided. With that you are ready to construct house. The same way if a cloud provider provides network and infrastructure we are ready to build servers and machines for your application development PaaS(Application Development) Example: You rented a empty house. Now you have to furnish it to live. The same way if a cloud provider provides Operating System, Application stack, network and infrastructure we are ready to develop the application based our needs. SaaS(Users) Example: You rented a fully furnished house. Now you just walk in with your suitcase. The same way if a cloud provider provides ready to use software. You signup and start using. CUSTOMER SECURITY RESPONSIBILITY SERVICE PROVIDER SECURITY RESPOSABILITY CUSTOMER SECURITY RESPONSIBILITY SERVICE PROVIDER SECURITY RESPOSABILITY CUSTOMER SECURITY RESPONSIBILITY SERVICE PROVIDER SECURITY RESPOSABILITY CLOUD SECURITY each area the IaaS security responsibility is less with the service provider but more with the customer, in PaaS the security responsibility of service provider is little but more than the customer, in SaaS the security responsibility of service provider is high than the customer. To know why the security responsibility varies we need to look more closely how the component ownership varies in all the 3 areas including On-premises.