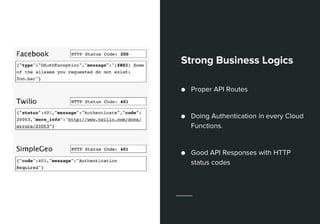
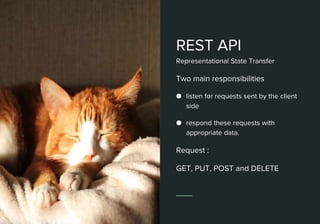
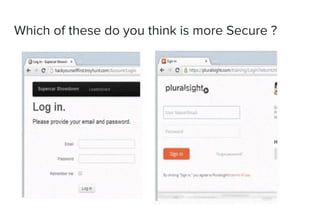
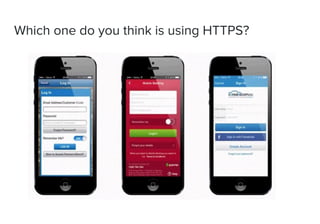
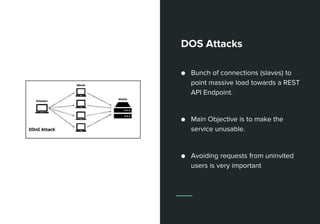
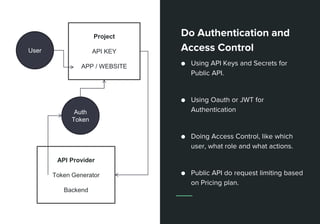
This document discusses web APIs and REST APIs. It provides examples of common web APIs like weather, Google Maps, and Twitter APIs. It then discusses security concerns around REST APIs like data interception, DDoS attacks, and farming. It recommends using HTTPS, authentication, access control, and JSON Web Tokens (JWTs) for security. It also mentions the importance of format checking, strong business logic, and proper API design.












![More on JWT
Header
{
"alg":“RSA256",
"typ":“JWT"
}
Payload
{
"token-type": "access-token",
"username": "snoopy",
"animal": "beagle",
"iss":
"https://demo.com/oauth2/token",
"scopes": [“twitter”, "mans-best-
friend"],
"exp": 1474280963,
"iat": 1474279163,
"jti": "66881b068b249ad9"
}
DTfSdMzIIsC0j8z3icRdYO1GaMGl6j
1I_2DBjiiHW9vmDz8OAw8Jh8DpO
32fv0vICc
0hb4F0QCD3KQnv8GVM73kSYaO
EUwlW0k1TaElxc43_Ocxm1F5IUNZ
vzlLJ_ksFX
GDL_cuadhVDaiqmhct098ocefuv0
8TdzRxqYoEqYNo
Signature
RSA256( base64UrlEncode( header ) + “.“ + base64UrlEncode( payload ) , secret )](https://image.slidesharecdn.com/webapisecurity-190725160226/85/Web-api-security-19-320.jpg)