Recommended
PDF
Slide ATBM TMĐT - Môn an toàn bảo mật thương mại điện tử.pdf
PPTX
PPTX
PPT
Basics of Information System Security
PDF
PPTX
PDF
Aula 05 - Importância do teste, auditoria e monitoramento
PPTX
Information and network security ins
PDF
MSc CS - I - 19PCSC203 - Cryptography and Network Security.pdf
PPT
CNS UNIT 1 NEW NEW UNIT has been s 1.ppt
PDF
Aula 01 - Fundamentos da segurança dos sistemas de informações
PPTX
Introduction to information security
PPTX
Chapter 1 information assurance and security
PPT
Lesson 2 Cryptography tools
PPTX
Information-Security_System_Notes__.pptx
PPT
Infomation System Security
PPTX
Cryptography Overview Presentation circa 2005
PPTX
Intro Foundations of Information Security.pptx
PDF
Slide Deck - CISSP Mentor Program Class Session 1
PPTX
Cryptography & Network Security.pptx
PPT
information security importance and use.ppt
DOCX
PPTX
Protecting Sensitive Data (and be PCI Compliant too!)
PPT
formintroduction to ISF.ppt ination security fundamentals
PPT
ODP
PDF
Defining Cryptography (Cryptography fundamentals 1/2)
PDF
Defining Cryptography (Cryptography fundamentals 1/2)
PDF
The voice of the rain poem class 11th.pdf
PPTX
Access partner report in Odoo 18.2 _ Odoo 19
More Related Content
PDF
Slide ATBM TMĐT - Môn an toàn bảo mật thương mại điện tử.pdf
PPTX
PPTX
PPT
Basics of Information System Security
PDF
PPTX
PDF
Aula 05 - Importância do teste, auditoria e monitoramento
PPTX
Information and network security ins
Similar to Chapter_09 crypto currency graphyic.pptx
PDF
MSc CS - I - 19PCSC203 - Cryptography and Network Security.pdf
PPT
CNS UNIT 1 NEW NEW UNIT has been s 1.ppt
PDF
Aula 01 - Fundamentos da segurança dos sistemas de informações
PPTX
Introduction to information security
PPTX
Chapter 1 information assurance and security
PPT
Lesson 2 Cryptography tools
PPTX
Information-Security_System_Notes__.pptx
PPT
Infomation System Security
PPTX
Cryptography Overview Presentation circa 2005
PPTX
Intro Foundations of Information Security.pptx
PDF
Slide Deck - CISSP Mentor Program Class Session 1
PPTX
Cryptography & Network Security.pptx
PPT
information security importance and use.ppt
DOCX
PPTX
Protecting Sensitive Data (and be PCI Compliant too!)
PPT
formintroduction to ISF.ppt ination security fundamentals
PPT
ODP
PDF
Defining Cryptography (Cryptography fundamentals 1/2)
PDF
Defining Cryptography (Cryptography fundamentals 1/2)
Recently uploaded
PDF
The voice of the rain poem class 11th.pdf
PPTX
Access partner report in Odoo 18.2 _ Odoo 19
PPTX
Repeat Orders_ Use Odoo Blanket Agreement
PPTX
10-12-2025 Francois Staring How can Researchers and Initial Teacher Educators...
PPTX
How to Track a Link Using Odoo 18 SMS Marketing
PPTX
Expected Revenue Report In Odoo 18 CRM
PDF
Micro Economics for class 12 and class 11
PPTX
Overview of how to Create a Model in Odoo 18
PPTX
How to Manage Package Reservation in Odoo 18 Inventory
PPTX
The Cell & Cell Cycle-detailed structure and function of organelles.pptx
PDF
Biology Practical Class 12th 2025 PDF(2)-2-52.pdf
PPTX
UNIT 1: COMMUNICATION SKILLS, BARRIERS TO COMMUNICATION, PERSPECTIVES IN COMM...
PPTX
Steve Hale - Developing Elite Young Goalkeepers 2024.pptx
PPTX
AN EXTREMELY BORING GENERAL QUIZ FOR UG.pptx
PDF
Risk management in Moroccan public hospitals_ a literature review
PDF
Multiple Myeloma , definition, etiology, PP, CM , DE and management
PPTX
Introduction-to-Anatomy-and-Physiology.pptx
PPTX
Growth & Development MILESTONES (ADOLESCENTS ).pptx
PPTX
PARENTAL ROUTES OF DRUGS ADMINISTRATION .pptx
PDF
Cultivating Greatness Pune's Best Preschools and Schools.pdf
Chapter_09 crypto currency graphyic.pptx 1. © 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Fundamentals of Information
Systems Security
Lesson 9
Cryptography
2. Page 2
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 2
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Learning Objective(s)
Explain how businesses apply
cryptography in maintaining information
security.
3. Page 3
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 3
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Key Concepts
Basics of cryptography
Business applications of cryptography
Symmetric and asymmetric key cryptography
Encryption mechanisms and techniques
Certificate and key management
4. Page 4
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 4
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
What Is Cryptography?
Unencrypted information—Information in
understandable form (plaintext or cleartext)
Encrypted information—Information in scrambled form
(ciphertext)
Encryption—The process of scrambling plaintext into
ciphertext
Decryption—The process of unscrambling ciphertext into
plaintext
Algorithm—A repeatable process that produces the same
result when it receives the same input
Cipher—An algorithm to encrypt or decrypt information
5. Page 5
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 5
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
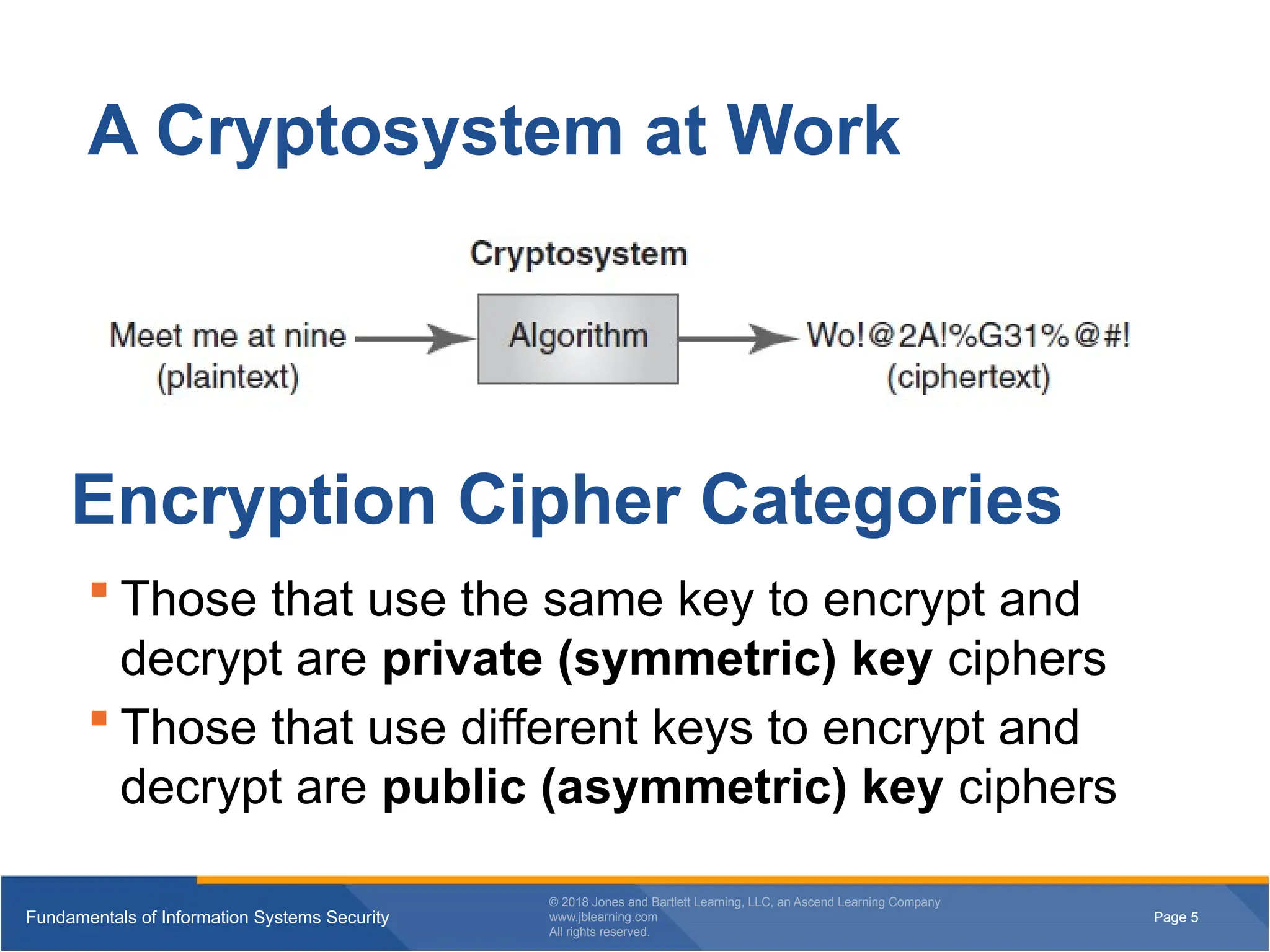
A Cryptosystem at Work
Those that use the same key to encrypt and
decrypt are private (symmetric) key ciphers
Those that use different keys to encrypt and
decrypt are public (asymmetric) key ciphers
Encryption Cipher Categories
6. Page 6
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 6
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Basic Cryptographic Principles
Keyspace—The number of possible keys
to a cipher
Open ciphers—Make it possible for
experts around the world to examine the
ciphers for weaknesses
Data Encryption Standard (DES)—The
most scrutinized cipher in history
7. Page 7
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 7
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
A Brief History of Cryptography
People have used cryptography to protect
information for at least 4,000 years
Steganography is the act of hiding
information
Cryptanalysis is breaking code
Cryptography was used in WWI and WWII
Symmetric and asymmetric key
cryptography introduced in 1976
8. Page 8
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 8
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
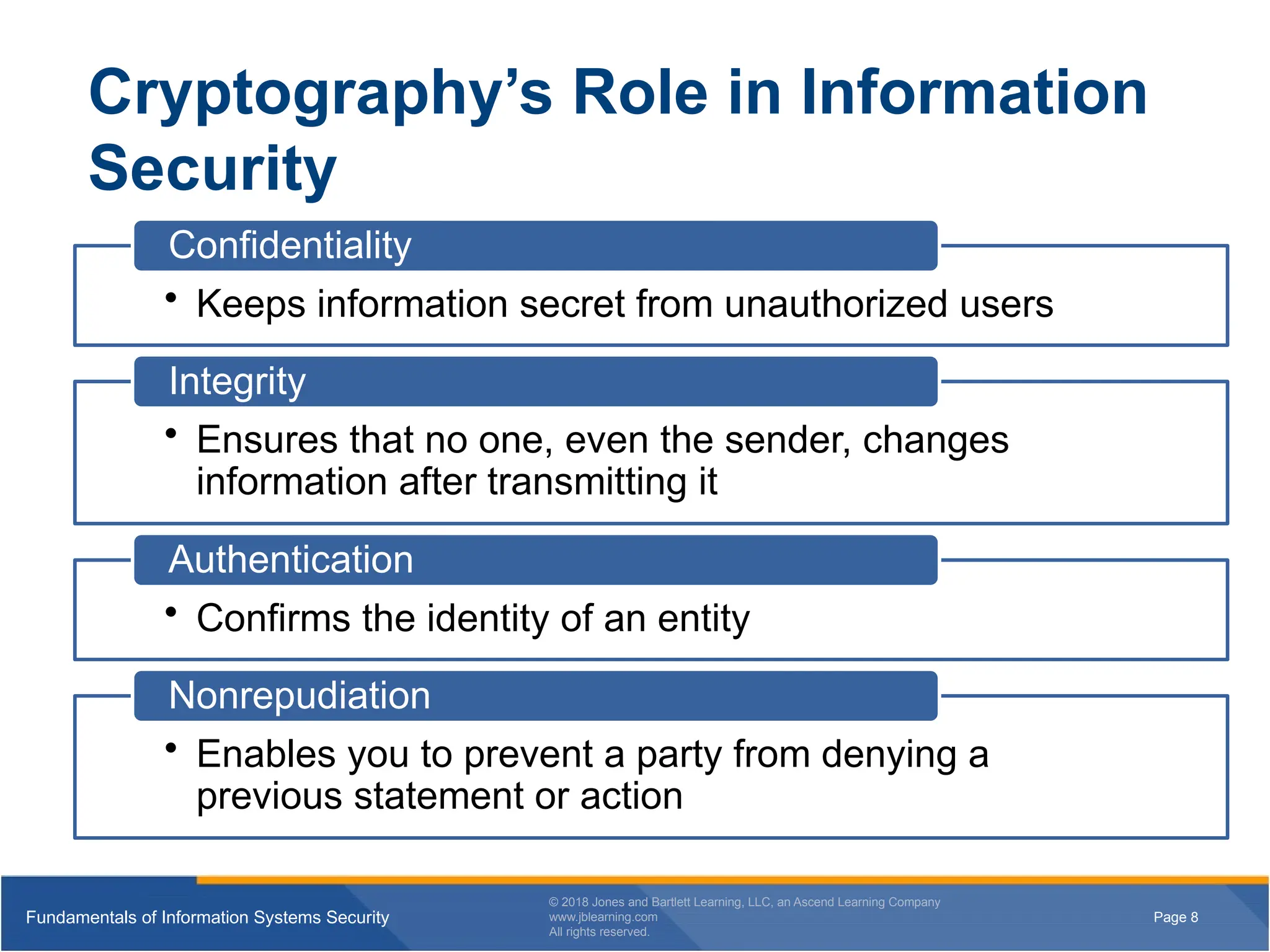
Cryptography’s Role in Information
Security
• Keeps information secret from unauthorized users
Confidentiality
• Ensures that no one, even the sender, changes
information after transmitting it
Integrity
• Confirms the identity of an entity
Authentication
• Enables you to prevent a party from denying a
previous statement or action
Nonrepudiation
9. Page 9
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 9
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Business and Security Requirements
for Cryptography
Internal security
• Confidentiality, privacy, integrity, and authorization
Security in business relationships
• Message authentication, signature, receipt and
confirmation, and nonrepudiation
Security measures that benefit everyone
• Anonymity, timestamping, revocation, and
ownership
10. Page 10
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 10
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
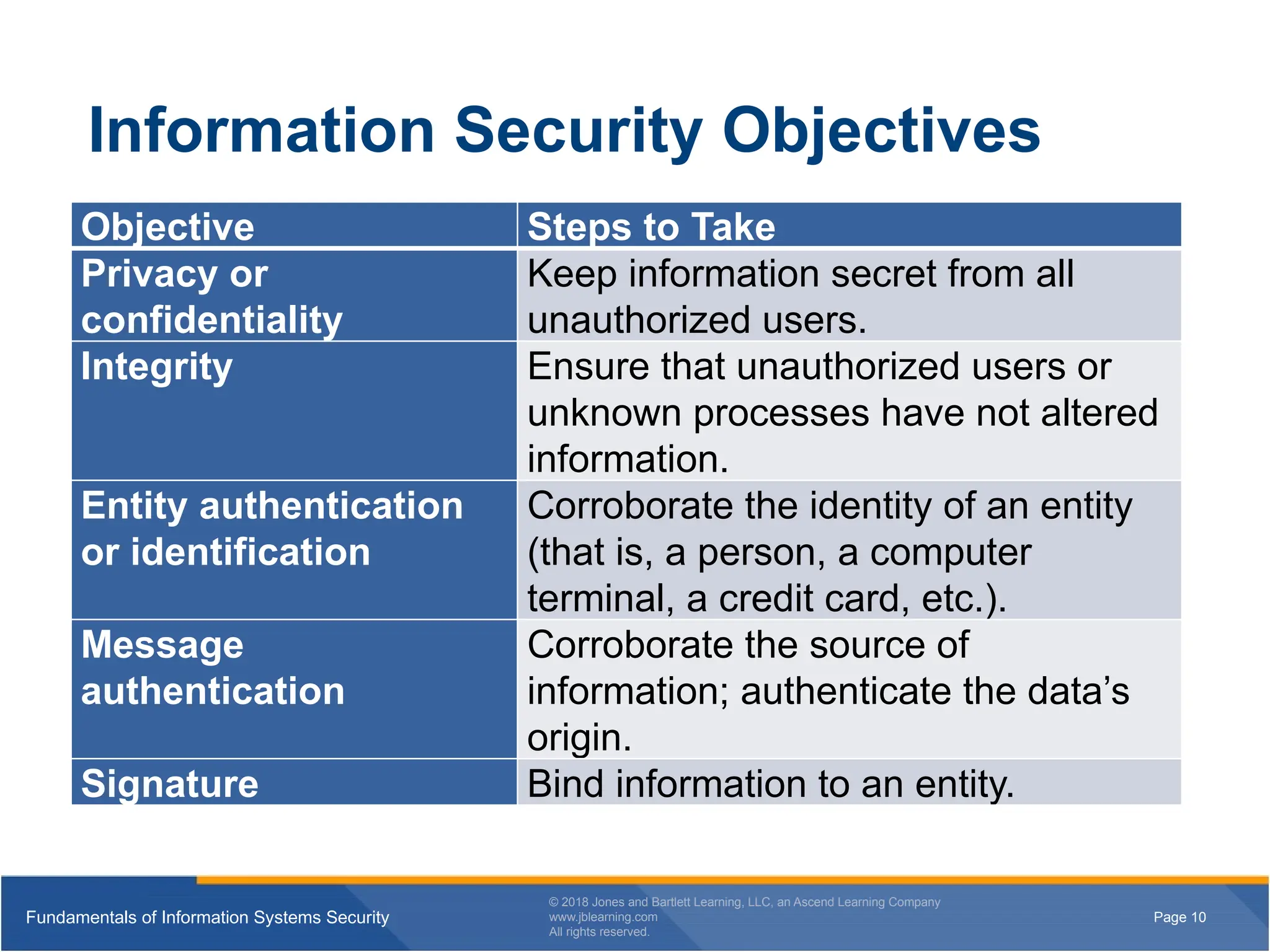
Information Security Objectives
Objective Steps to Take
Privacy or
confidentiality
Keep information secret from all
unauthorized users.
Integrity Ensure that unauthorized users or
unknown processes have not altered
information.
Entity authentication
or identification
Corroborate the identity of an entity
(that is, a person, a computer
terminal, a credit card, etc.).
Message
authentication
Corroborate the source of
information; authenticate the data’s
origin.
Signature Bind information to an entity.
11. Page 11
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 11
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
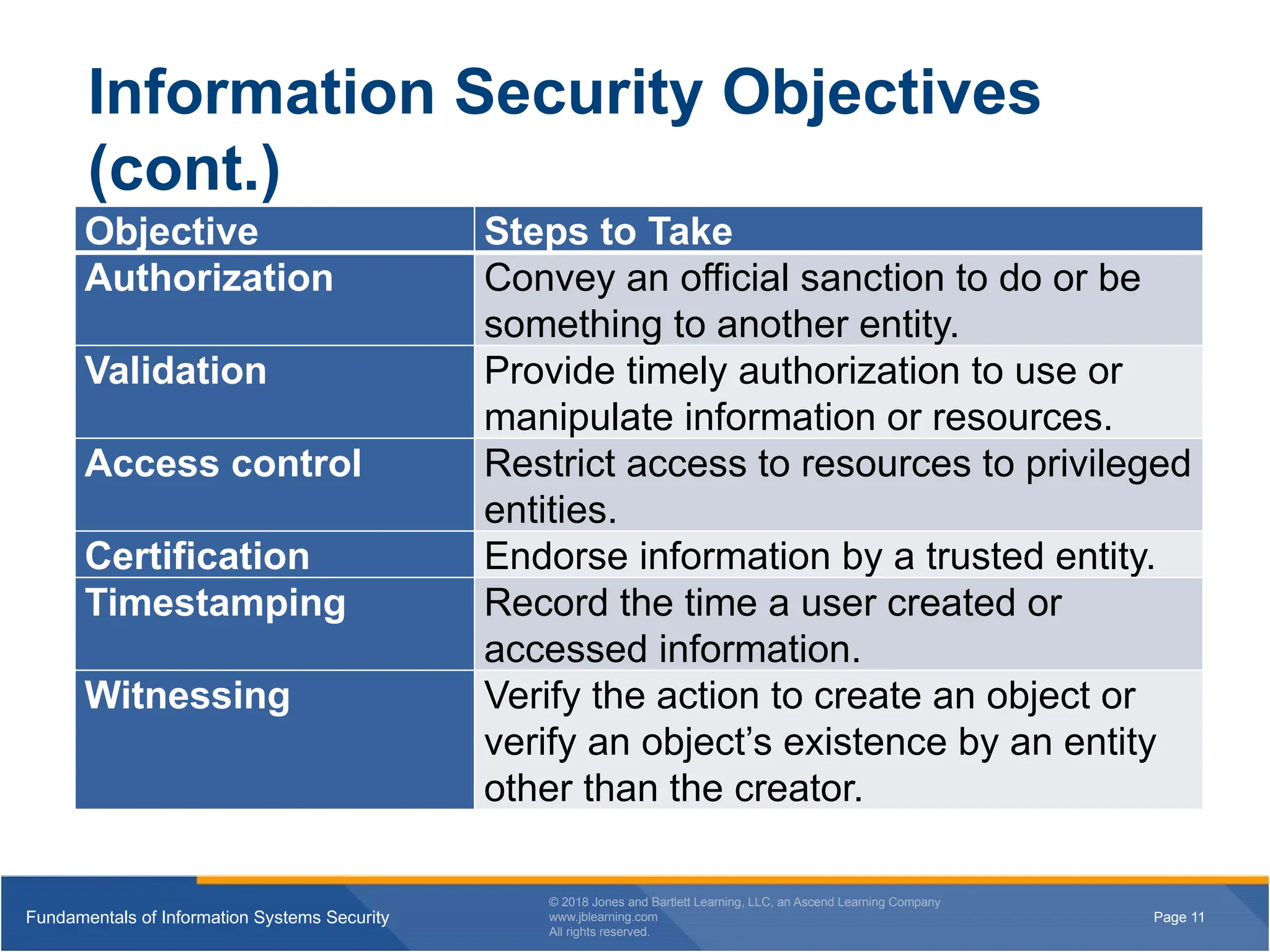
Information Security Objectives
(cont.)
Objective Steps to Take
Authorization Convey an official sanction to do or be
something to another entity.
Validation Provide timely authorization to use or
manipulate information or resources.
Access control Restrict access to resources to privileged
entities.
Certification Endorse information by a trusted entity.
Timestamping Record the time a user created or
accessed information.
Witnessing Verify the action to create an object or
verify an object’s existence by an entity
other than the creator.
12. Page 12
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 12
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
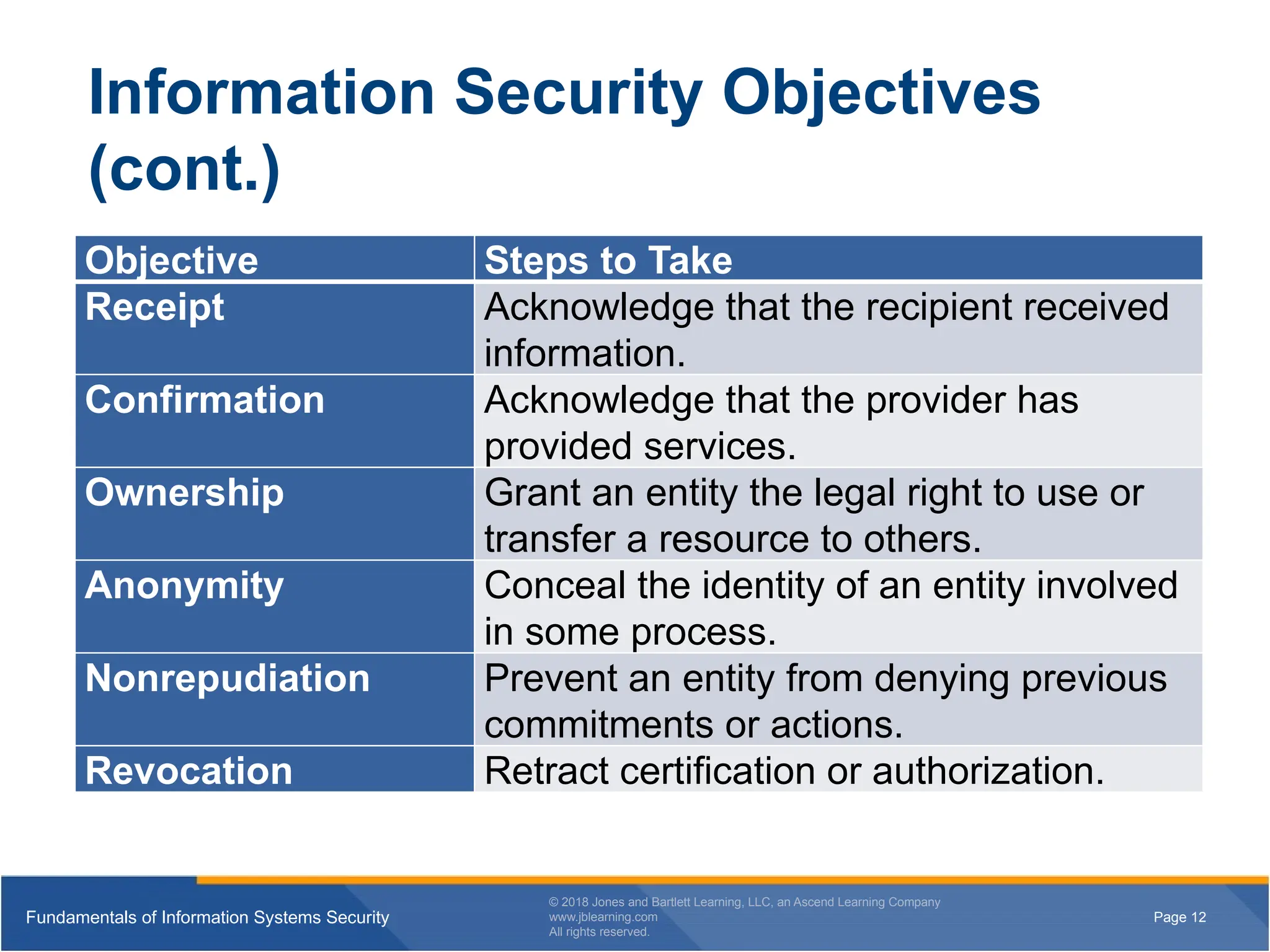
Information Security Objectives
(cont.)
Objective Steps to Take
Receipt Acknowledge that the recipient received
information.
Confirmation Acknowledge that the provider has
provided services.
Ownership Grant an entity the legal right to use or
transfer a resource to others.
Anonymity Conceal the identity of an entity involved
in some process.
Nonrepudiation Prevent an entity from denying previous
commitments or actions.
Revocation Retract certification or authorization.
13. Page 13
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 13
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
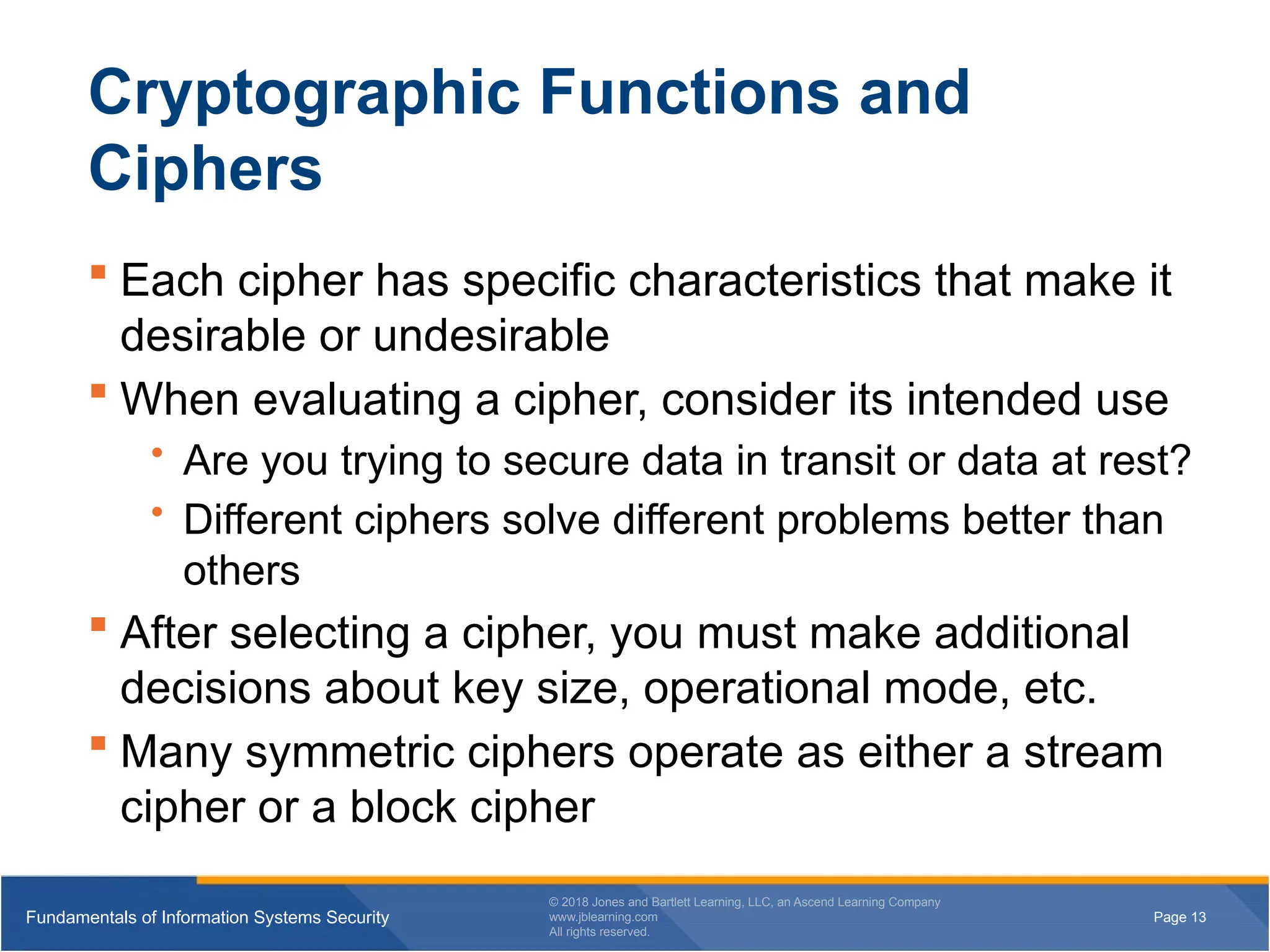
Cryptographic Functions and
Ciphers
Each cipher has specific characteristics that make it
desirable or undesirable
When evaluating a cipher, consider its intended use
• Are you trying to secure data in transit or data at rest?
• Different ciphers solve different problems better than
others
After selecting a cipher, you must make additional
decisions about key size, operational mode, etc.
Many symmetric ciphers operate as either a stream
cipher or a block cipher
14. Page 14
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 14
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Business-Security Implementations
General Classifications
• Authentication (non-PKI)
• Access control/authorization
• Assessment and audit
• Security management products
• Perimeter/network security/availability
• Content filtering
• Encryption
• Administration/education
• Outsource services/consultants
15. Page 15
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 15
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Cryptography Capabilities
Privacy or
confidentiality
Integrity
Entity authentication
or identification
Message
authentication
Signature
Access control
Certification
Timestamping
Witnessing
Ownership
Anonymity
Nonrepudiation
16. Page 16
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 16
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Types of Ciphers
• Rearranges characters or bits
of data
Transpositio
n ciphers
• Replaces bits, characters, or
blocks of information with
other bits, characters, or
blocks
Substitution
ciphers
17. Page 17
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 17
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
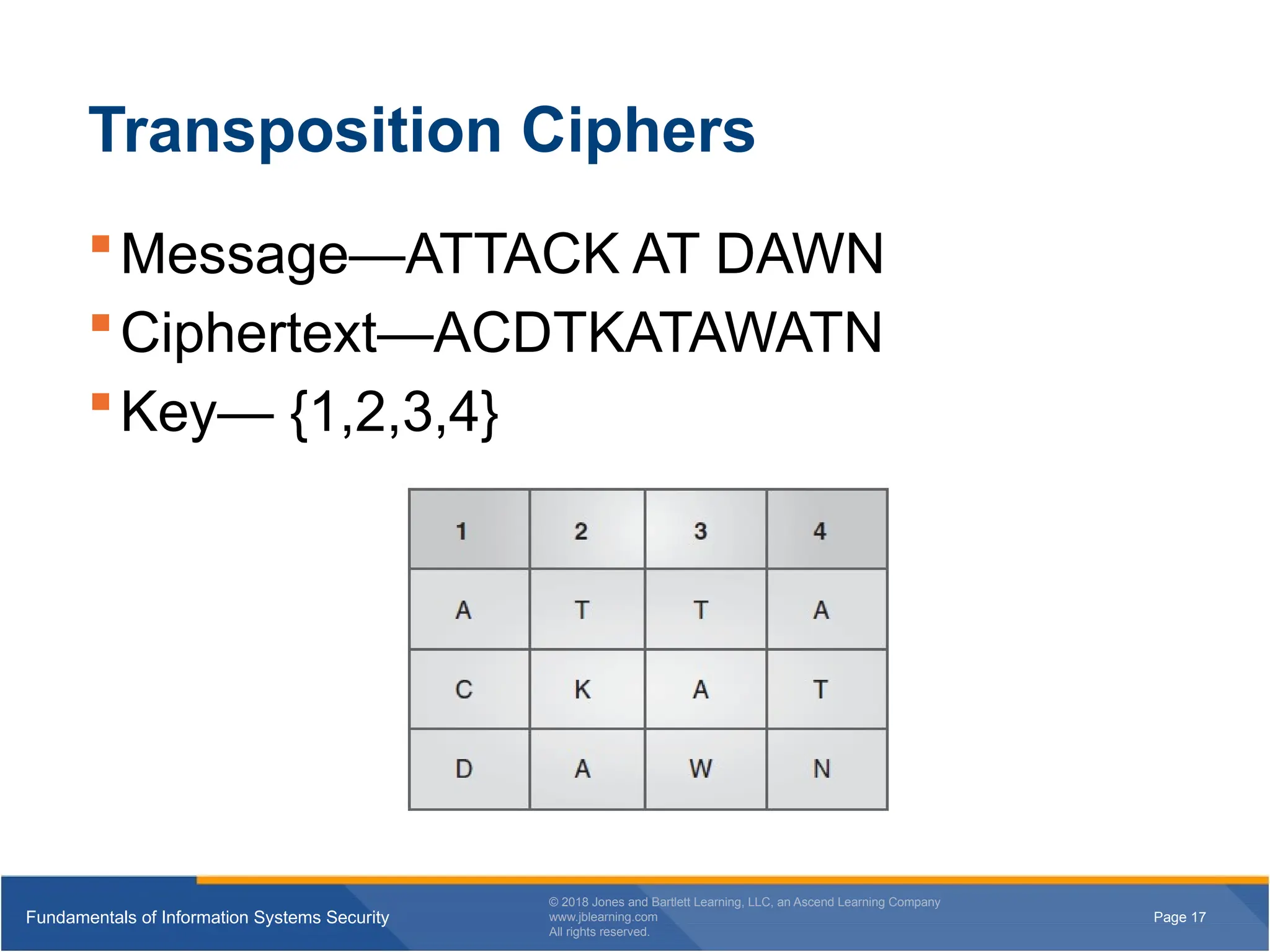
Transposition Ciphers
Message—ATTACK AT DAWN
Ciphertext—ACDTKATAWATN
Key— {1,2,3,4}
18. Page 18
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 18
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Substitution Ciphers
Caesar cipher—Each letter in the English alphabet a
fixed number of positions, with Z wrapping back to A
Keyword mixed alphabet cipher—Uses a cipher
alphabet that consists of a keyword, minus
duplicates, followed by the remaining letters of the
alphabet
Vigenère (vee-zhen-AIR) cipher—Encrypts every
letter with its own substitution scheme
Simple substitution cipher—Allows any letter to
uniquely map to any other letter
19. Page 19
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 19
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Symmetric and Asymmetric Key
Cryptography
Symmetric key ciphers use the same key to
encrypt and decrypt
Asymmetric key ciphers have four key properties:
• Two associated algorithms that are inverses of each
other exist
• Each of these two algorithms is easy to compute
• It is computationally infeasible to derive the second
algorithm if you know the first algorithm
• Given some random input, you can generate
associated key pairs that are inverses of each other
20. Page 20
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 20
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Cryptanalysis and Public Versus
Private Keys
You can break a cipher in two ways:
• Analyzing the ciphertext to find the plaintext or key
• Analyzing the ciphertext and its associated plaintext to
find the key
Four basic forms of cryptographic attack
• Ciphertext-only attack (COA)
• Known-plaintext attack (KPA)
• Chosen-plaintext attack
• Chosen-ciphertext attack
21. Page 21
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 21
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
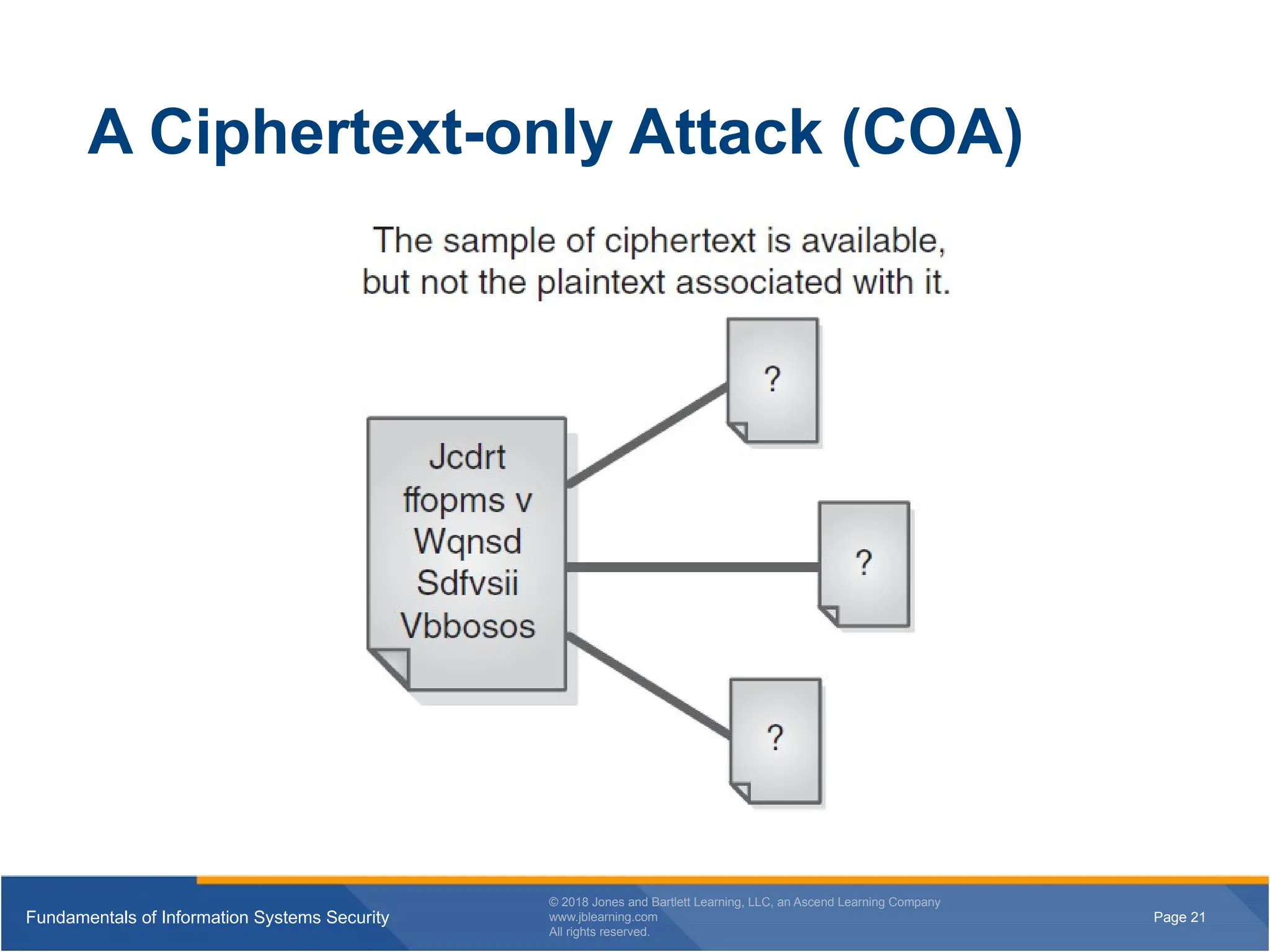
A Ciphertext-only Attack (COA)
22. Page 22
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 22
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
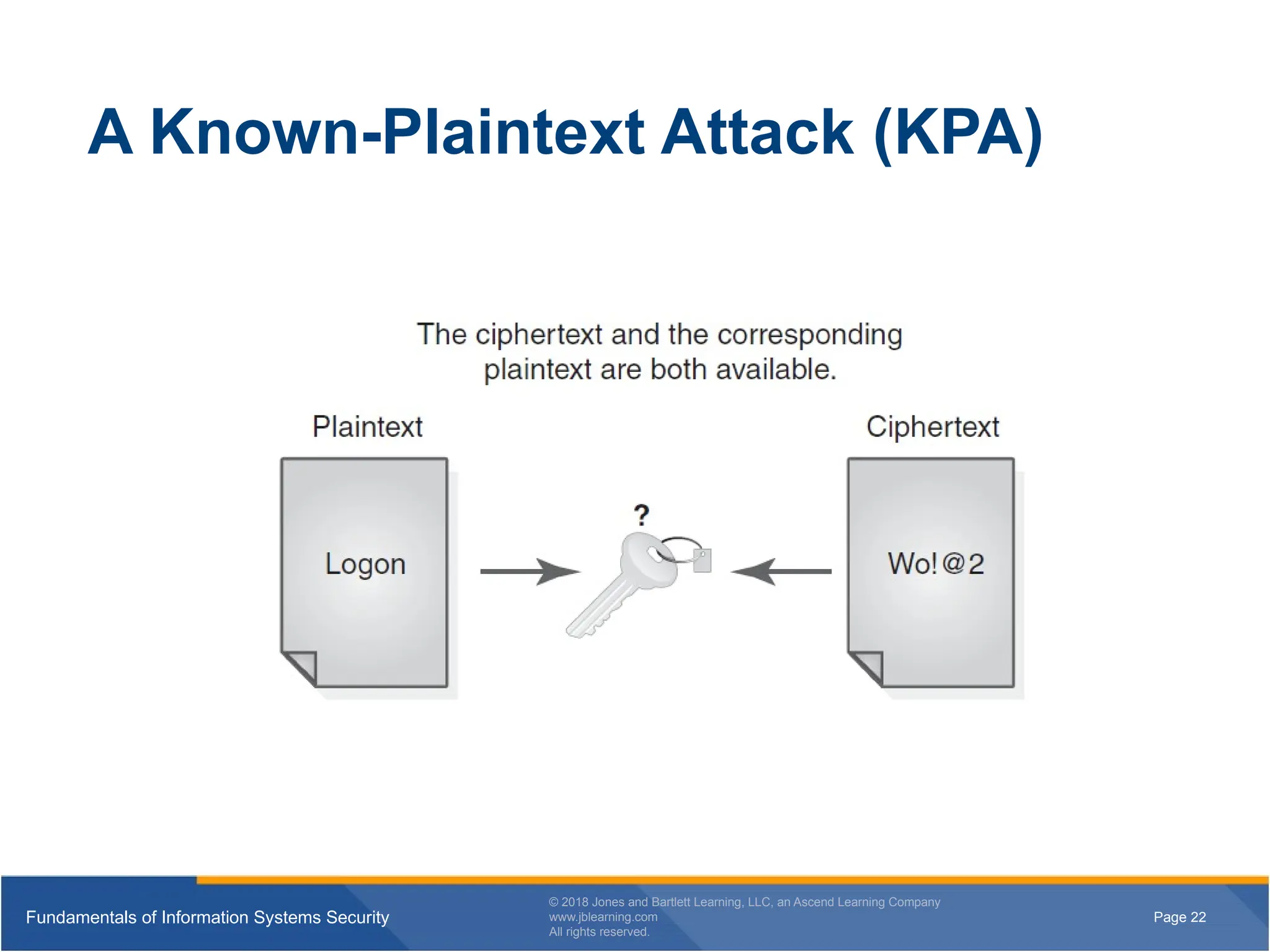
A Known-Plaintext Attack (KPA)
23. Page 23
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 23
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Keys, Keyspace, and Key
Management
Key
• A value that is an input to a cryptosystem
Keyspace
• The set of all possible keys
Key management
• One of the most difficult and critical parts of a
cryptosystem
24. Page 24
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 24
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
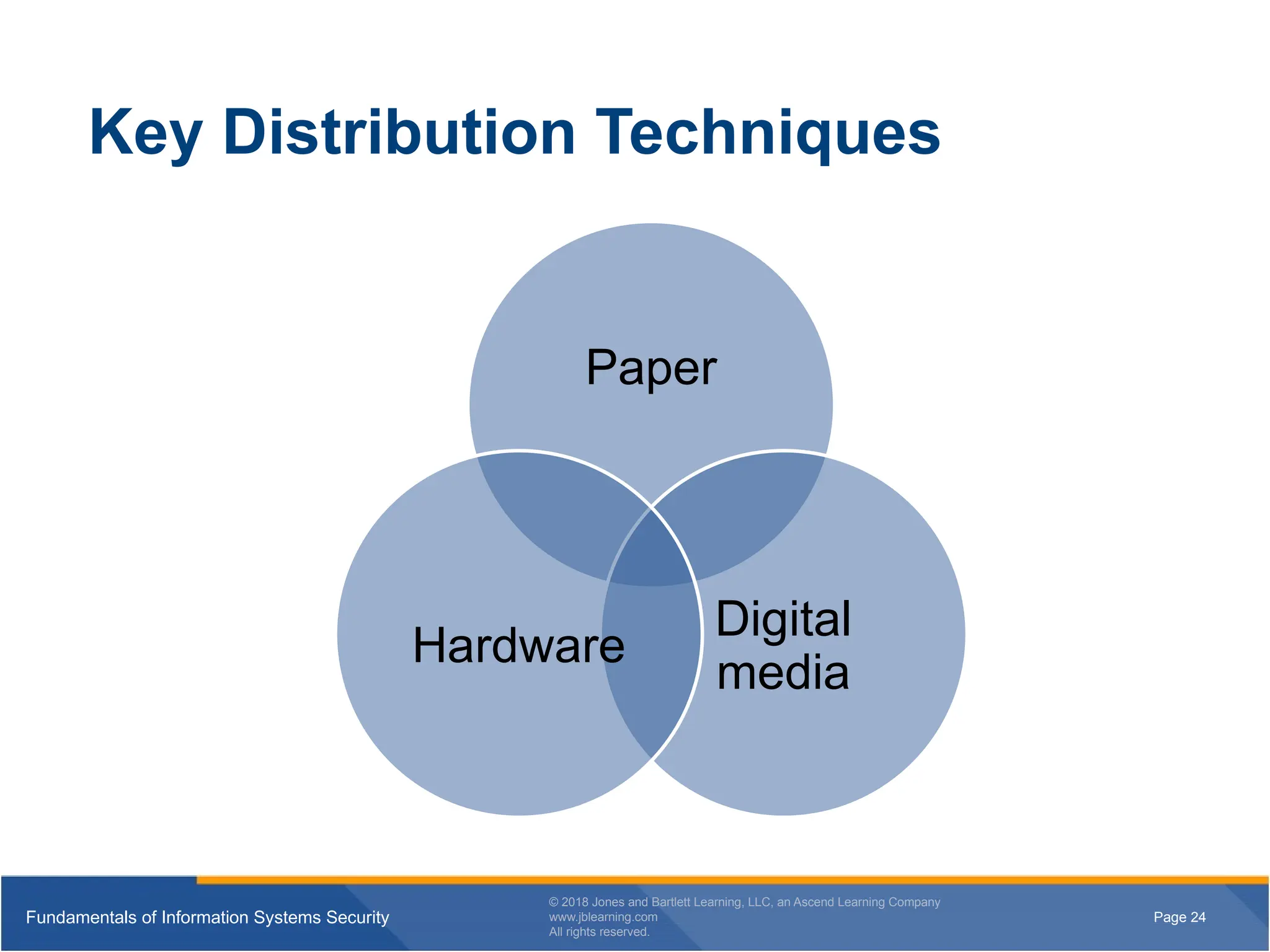
Key Distribution Techniques
Paper
Digital
media
Hardware
25. Page 25
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 25
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Key Distribution Techniques
Paper distribution requires no technology to use However, it does
require a person to do something to install the key This human role
can introduce errors or give a disgruntled person a chance to
compromise a system
Digital distribution can be in the form of CDs or email Note that you
must protect the keys in transit Some form of secure transmission
must be used
You can distribute a key via hardware with a Personal Computer
Memory Card International Association ( card, a smart card, or a plug-
in module
The advantage is that you transfer the keys directly from the key
transport mechanism into the crypto device without anyone viewing
them No copies exist outside of these components
26. Page 26
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 26
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
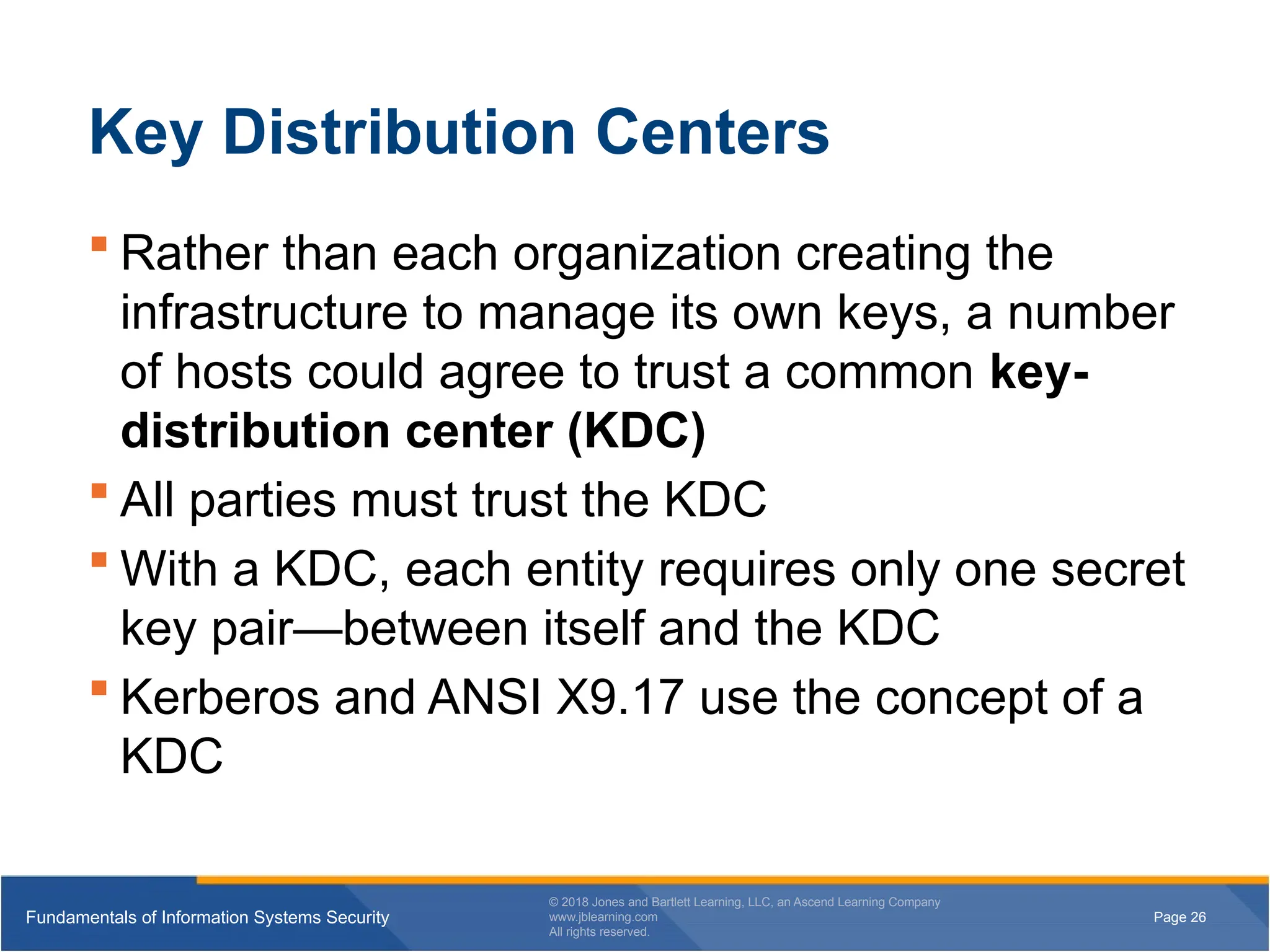
Key Distribution Centers
Rather than each organization creating the
infrastructure to manage its own keys, a number
of hosts could agree to trust a common key-
distribution center (KDC)
All parties must trust the KDC
With a KDC, each entity requires only one secret
key pair—between itself and the KDC
Kerberos and ANSI X9.17 use the concept of a
KDC
27. Page 27
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 27
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
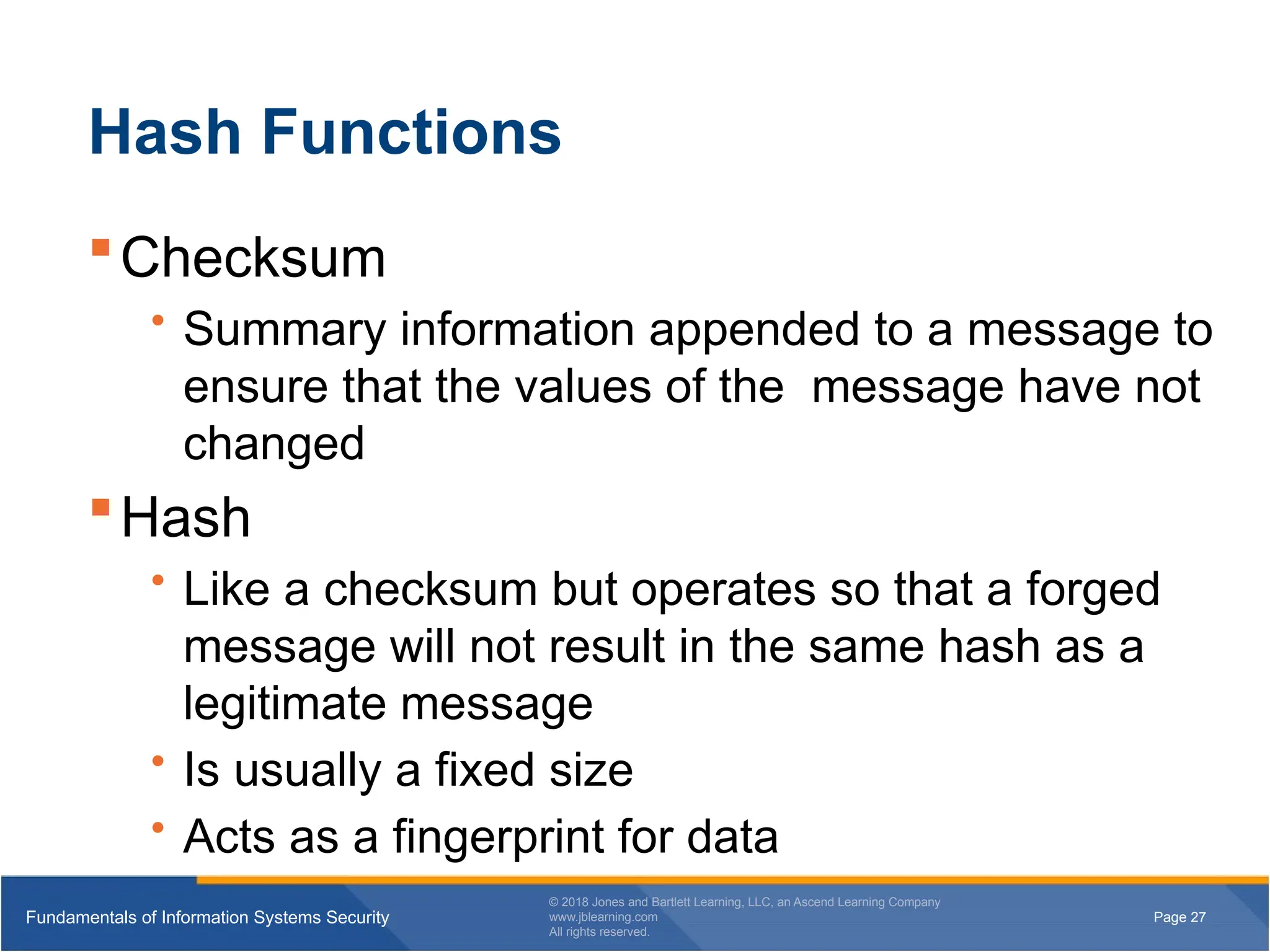
Hash Functions
Checksum
• Summary information appended to a message to
ensure that the values of the message have not
changed
Hash
• Like a checksum but operates so that a forged
message will not result in the same hash as a
legitimate message
• Is usually a fixed size
• Acts as a fingerprint for data
28. Page 28
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 28
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
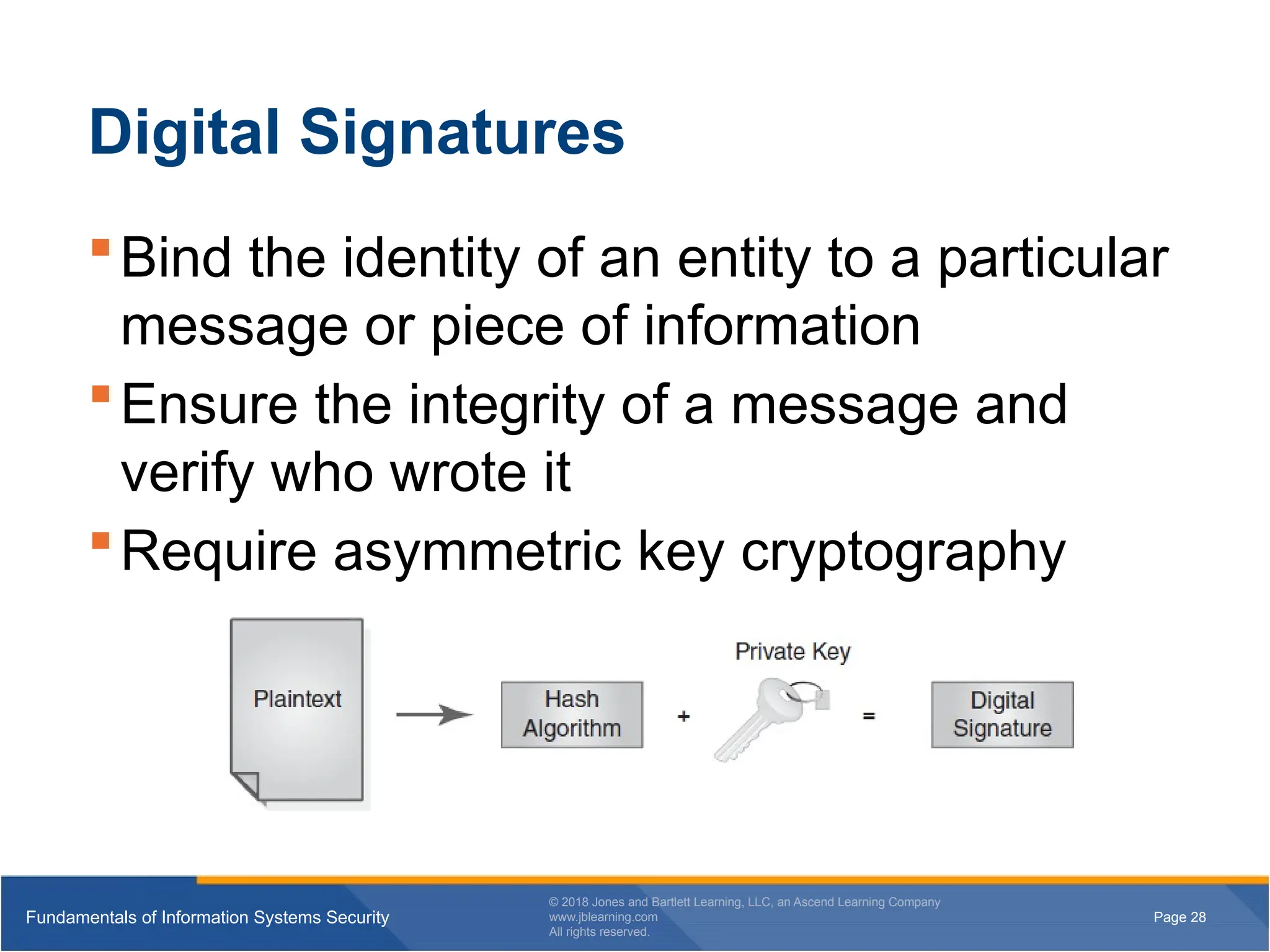
Digital Signatures
Bind the identity of an entity to a particular
message or piece of information
Ensure the integrity of a message and
verify who wrote it
Require asymmetric key cryptography
29. Page 29
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 29
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
How a Digital Signature Works
30. Page 30
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 30
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Cryptographic Applications and
Uses in Information System Security
Security product and service categories:
• Anti-malware
• Forensics
• ID management
• Messaging safeguards
• Patch management
• Perimeter defenses
• Transaction security (digital certificates, secure file
transfer)
• Wireless security
31. Page 31
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 31
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Cryptographic Applications and
Uses in Information System Security
Authentication tools include tokens, smart
cards, biometrics, passwords, and password
recovery
Access control and authorization includes
firewalls, timestamping, single sign-on, identity
management, and mobile device security
Assessment and auditing tools include
vulnerability-assessment scanners, penetration
testing tools, forensic software, and log analyzers
32. Page 32
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 32
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Cryptographic Applications and
Uses in Information System Security
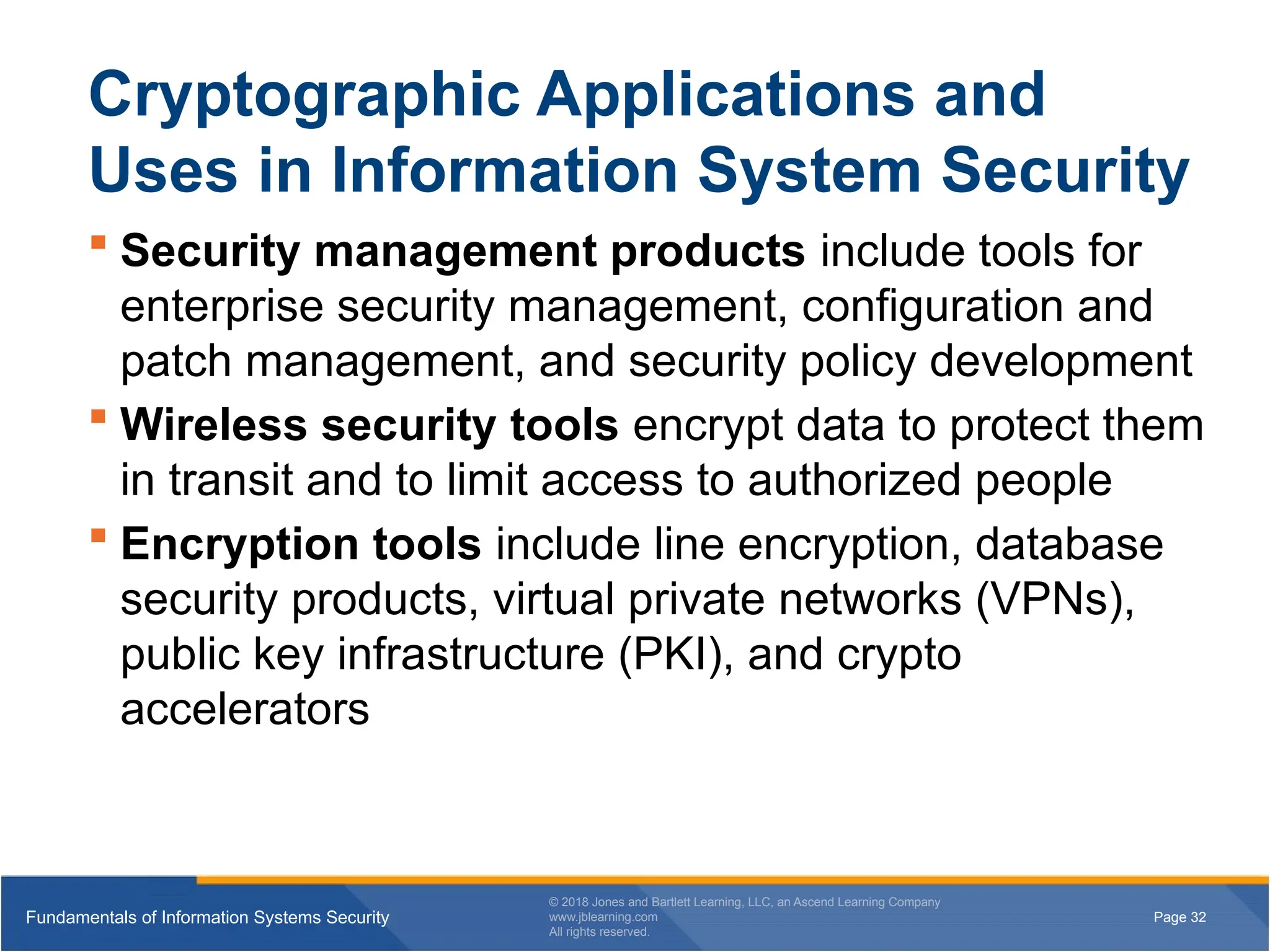
Security management products include tools for
enterprise security management, configuration and
patch management, and security policy development
Wireless security tools encrypt data to protect them
in transit and to limit access to authorized people
Encryption tools include line encryption, database
security products, virtual private networks (VPNs),
public key infrastructure (PKI), and crypto
accelerators
33. Page 33
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 33
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Symmetric Key Standards
Data Encryption Standard (DES)
Triple DES (3DES)
International Data Encryption Algorithm (IDEA)
CAST
Blowfish
Advanced Encryption Standard (AES)
RC2
RC4
34. Page 34
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 34
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Wireless Security
Wireless products have built-in security, the default
configuration generally doesn’t enable it; they expect
customers to enable it
802.11 wireless security (Wi-Fi) provides wireless
communications at transmission speeds from 11 Mbps for
802.11b, to over 780 Mbps for 802.11ac, and 100 Gbps
for 802.11ay
802.11 wireless protocols allow encryption through Wired
Equivalent Privacy (WEP) or Wi-Fi Protected Access
(WPA)
• WEP has limitations and shouldn’t be used
35. Page 35
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 35
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
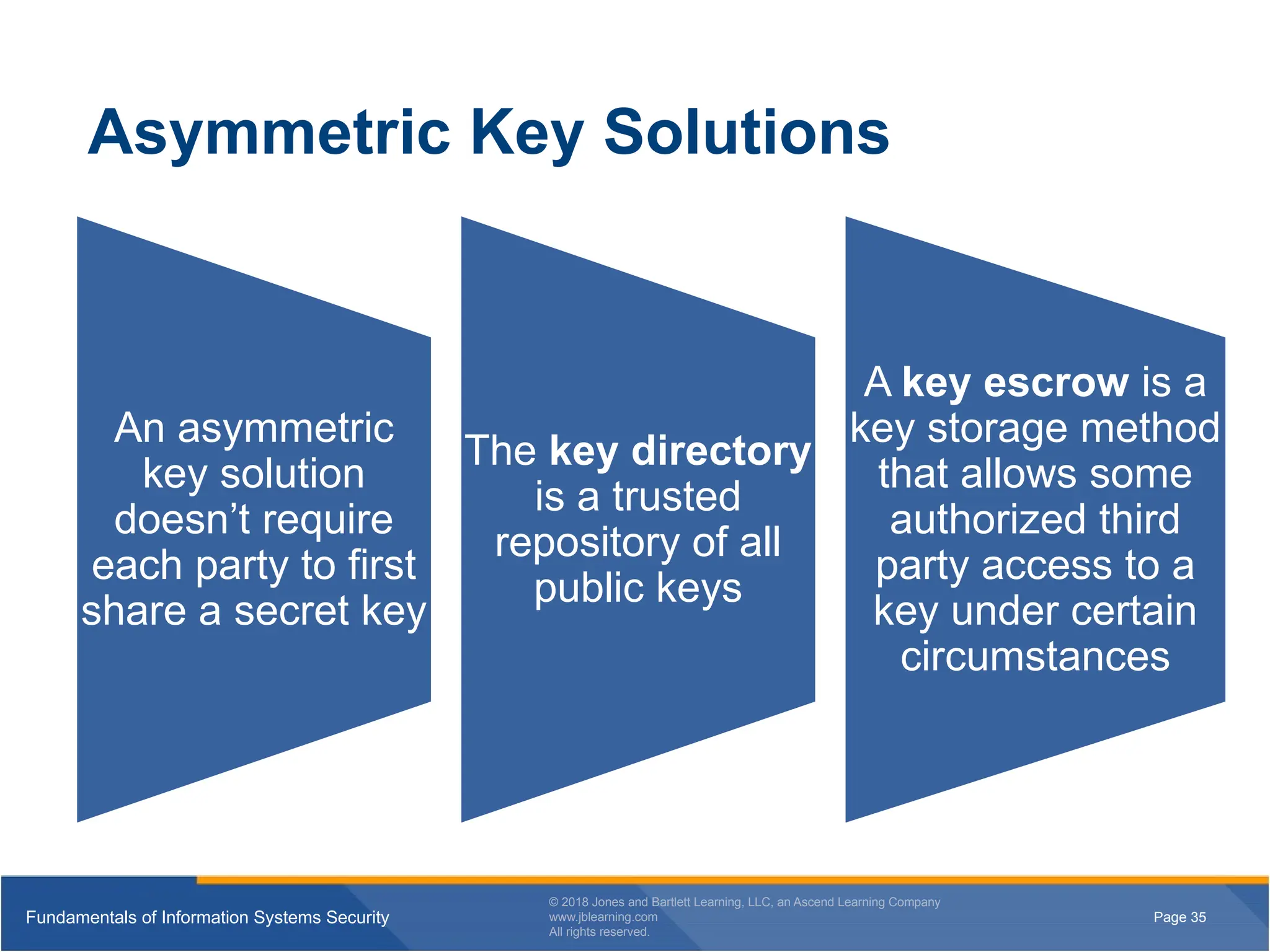
Asymmetric Key Solutions
An asymmetric
key solution
doesn’t require
each party to first
share a secret key
The key directory
is a trusted
repository of all
public keys
A key escrow is a
key storage method
that allows some
authorized third
party access to a
key under certain
circumstances
36. Page 36
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 36
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Asymmetric Key Solutions
The SSL Handshake Protocol consists of two
phases: server authentication and an optional client
authentication
Digital signatures verify a person’s identity or that
person’s association with a message
A certificate authority (CA) vouches for the validity
of a credential, and maintains a list of invalid, or
revoked, certificates in either a certificate revocations
list (CRL) or by maintaining the data to support the
newer online certificate status protocol (OCSP)
37. Page 37
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 37
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Hash Function and Integrity
Hash functions:
• Help detect forgeries
• Compute a checksum of a message
• Combine the checksum with a cryptographic function
so that the result is tamperproof
A hash is:
• A checksum designed so that no one can forge a
message in a way that will result in the same hash as
a legitimate message
• Usually a fixed size, resulting in a hash value, which is
larger than checksum values
38. Page 38
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 38
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Hashing Algorithms
MD5 message digest algorithm—Takes an input of any
arbitrary length and generates a 128-bit message digest
that is computationally infeasible to match by finding
another input
Secure Hash Algorithm (SHA-1)—Produces a 160-bit
hash from a message of any arbitrary length
Hash message authentication code (HMAC)—A hash
function that uses a key to create the hash, or message
digest
RACE Integrity Primitives Evaluation Message Digest
(RIPEMD)—A collection of functions that provide hash
values for a wide range of applications
39. Page 39
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 39
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
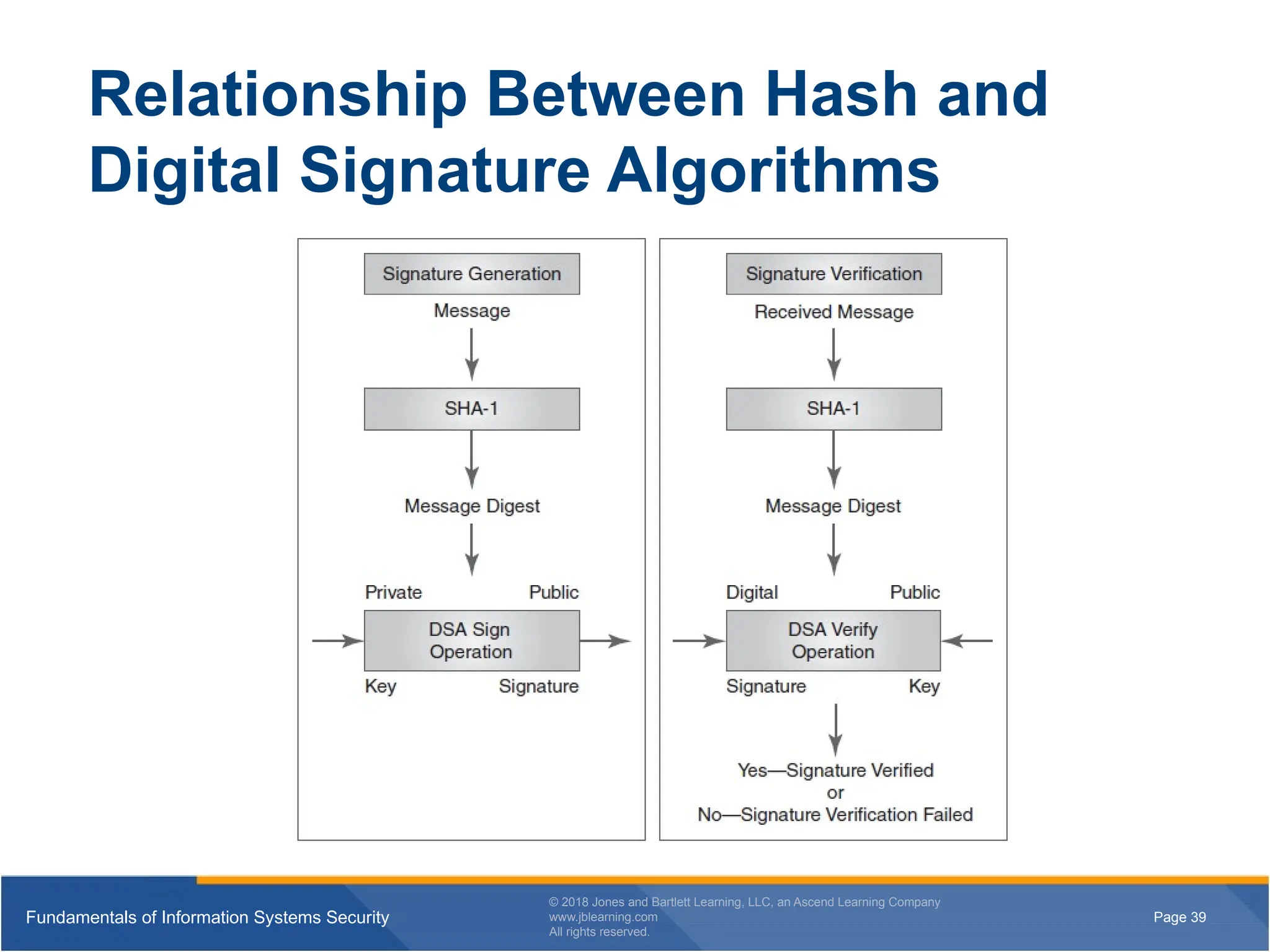
Relationship Between Hash and
Digital Signature Algorithms
40. Page 40
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 40
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Digital Signatures and
Nonrepudiation
A digitized signature is an
image of a physical signature
stored in digital format
A digital signature is a
combination of a strong hash
of a message, which acts as a
fingerprint
41. Page 41
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 41
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Conditions for Proving
Nonrepudiation
An effective asymmetric key algorithm
A strong hash function
A means to apply the private encryption key to the hash
value to produce a digital signature
A tamperproof or trusted third-party timing device
An agreed-upon protocol for validating digital signatures
A secure key management and distribution system
A public key repository with an assured level of integrity
Key escrow to be able to produce public keys from
reluctant parties
Procedures to handle disputes
42. Page 42
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 42
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Principles of Certificates and Key
Management
The best key management system in the
world does not protect against a brilliant
cryptanalyst if the encryption algorithm itself
has any weaknesses
43. Page 43
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 43
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Modern Key Management
Techniques
Advanced Encryption Standard (AES)
Internet Protocol Security (IPSec)
The Internet Security Association and Key Management Protocol
(ISAKMP)
Extensible Markup Language (XML) key management
specification (XKMS)
Managed public key infrastructure (PKI)
American National Standards Institute (ANSI) X9.17
44. Page 44
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page 44
Fundamentals of Information Systems Security
© 2018 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Summary
Basics of cryptography
Business applications of cryptography
Symmetric and asymmetric key
cryptography
Encryption mechanisms and
techniques
Certificate and key management
Editor's Notes #10 Security objectives from the Handbook of Applied Cryptography
#11 Security objectives from the Handbook of Applied Cryptography
#12 Security objectives from the Handbook of Applied Cryptography
#13 Stream cipher—Encrypts one byte (or bit) at a time
Block cipher—Encrypts an entire block of data at a time
#15 • Privacy or confidentiality. Cryptography scrambles information so that only someone with the right cipher and key can read it. Note that this person could include a clever cryptanalyst.
• Integrity. Cryptography protects integrity by providing checksums or hashes. You can compare these with a known table of good values to prove that the data have not changed.
• Entity authentication or identification. Someone’s ability to encode or decode a message means that person has the cryptographic key or has the ability to calculate the key. If a business relationship requires that this key remain secret, possession is proof of valid identity.
• Message authentication. Similar to entity authentication, a coded message with a private key proves who the message’s writer is. Again, this stipulation should be part of any business contract or formal relationship.
• Signature. Cryptography can provide a way to make a digital signature. This can prove that a given person sent a specific message.
• Access control. This involves encrypting privileged resources or data so that only authorized people can decrypt them and enforce access to them.
• Certification. A trusted entity can certify a message or data by adding a cryptographic checksum and a digital signature.
• Timestamping. Using asymmetric key cryptography, a trusted device can issue timestamps that attackers cannot forge. Timestamping binds a hash of the timestamped information with the output of a secure, reliable clock.
• Witnessing. A third party can add a cryptographic checksum to data to prove that those data exist in a given format at a particular time.
• Ownership. This refers to a cryptographic hash created by an owner and added to the data, then submitted to a trusted third party for corroboration. This identifies an entity as the data’s owner.
• Anonymity. Using cryptography, you can conceal the identity of an entity by passing information in an encrypted format that monitors cannot interpret. In addition, using a series of encrypted hops and getting rid of logs can provide an entity with anonymous presence on the Internet.
• Nonrepudiation. An asymmetric key signature of data, agreed to as part of a business relationship, can prove the sender’s identity to the receiver.
#24 Paper distribution requires no technology to use. However, it does require a person to do something to install the key. This human role can introduce errors or give a disgruntled person a chance to compromise a system.
Digital distribution can be in the form of CDs or email. Note that you must protect the keys in transit. Some form of secure transmission must be used. For physical media, tamperproof cases and registered mail give some level of assurance. For electronic distribution, a higher-level key, known as a key-encrypting key, must protect the keys in transit and storage. This, of course, requires that you first distribute the key-encrypting key by some alternate secure mechanism. You should use key-encrypting keys only to encrypt other keys, not data. Excessive use of any key could lead to it being compromised.
You can distribute a key via hardware with a Personal Computer Memory Card International Association (PCMCIA) card, a smart card, or a plug-in module.
The advantage is that you transfer the keys directly from the key-transport mechanism into the crypto device without anyone viewing them. No copies exist outside of these components.
#33 • Data Encryption Standard (DES). IBM originally developed DES as the Lucifer algorithm. The NSA modified it and issued it as a national standard in 1977. FIPS PUB 46-3 updated its definition. It uses a 56-bit key and operates on 64-bit blocks of data. The algorithm is better for hardware use than for software, and it can rapidly encrypt lots of data. The DES algorithm is in the public domain. DES was once a state-of-the-art algorithm, but with rapid advances in hardware capabilities and attack methods, attackers can now crack it in as little as a few days. It is no longer a secure algorithm.
• Triple DES (3DES). Triple DES is a protocol that consists of three passes of DES (encrypt, decrypt, encrypt) using multiple keys. It increases the keyspace from 56 to 112 or 168 bits, depending on whether two or three keys are used. Triple DES is computationally secure because of the underlying security of the DES algorithm and the vastly increased keyspace. Note that using the same key three times produces the same result as single DES. It, too, is contained in FIPS PUB 46-3 and is in the public domain.
• International Data Encryption Algorithm (IDEA). Like DES, this block cipher operates on 64-bit blocks. It uses a 128-bit key and runs somewhat faster than DES on hardware and software. Ascom-Tech AG holds a patent for IDEA but it is free for noncommercial use.
• CAST. The CAST algorithm is a substitution-permutation algorithm similar to DES. Unlike DES, its authors made its design criteria public. This 64-bit symmetric block cipher can use keys from 40 to 256 bits. RFC 2144 describes CAST-128; RFC-2612 describes CAST- 256. Although it is patented (U.S. patent 5,511,123), its inventors, C. M. Adams and S. E. Tavares, made it available for free use.
• Blowfish. Blowfish is a 64-bit block cipher that has a variable key length from 32 to 448 bits. It is much faster than DES or IDEA. Blowfish is a strong algorithm that has been included in more than 150 products as well as v2.5.47 of the Linux kernel. Its author, Bruce Schneier, placed it in the public domain. Schneier’s Twofish was a candidate for the Advanced Encryption Standard.
• Advanced Encryption Standard (AES). Also known as Rijndael (RAIN-doll), AES is a block cipher. Vincent Rijmen and Joan Daemen designed AES, and FIPS PUB 197 published it as a standard. The AES algorithm can use cryptographic keys of 128, 192, and 256 bits to encrypt and decrypt data in blocks of 128 bits. The cipher also can operate on variable block lengths. It is both strong and fast.
• RC2. RC2 is a variable key-size block cipher designed by Ronald Rivest (RC stands for Ron’s Code). RC2 operates as a drop-in replacement for DES and operates on 64-bit blocks. It uses a salt value as part of its encryption routine to make cryptanalysis more difficult. RSA Security owns it.
• RC4. Produced by RSA Security, RC4 is a variable key-size stream cipher with byte-oriented operations. Internet browsers often use RC4 to provide an SSL connection.