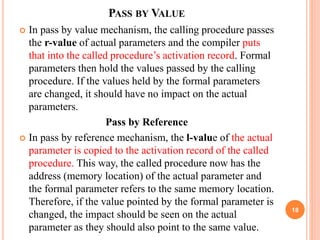
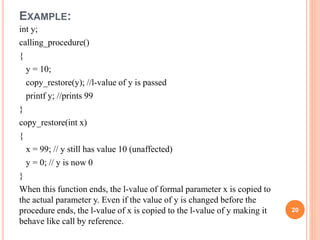
This document discusses runtime environments and compiler design. It contains the following key points:
- A runtime environment provides services like memory allocation, libraries, and environment variables to allow programs to execute. It maps program elements like names and identifiers to actual memory locations.
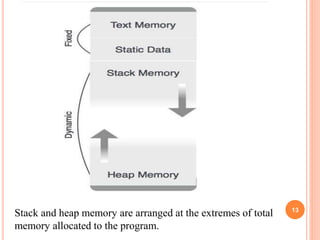
- Programs use stack allocation for procedure calls and return addresses. Variables use heap allocation which dynamically allocates and frees memory as needed.
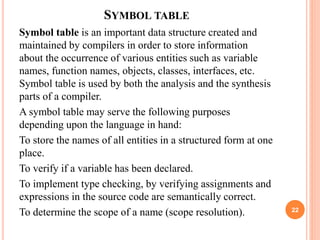
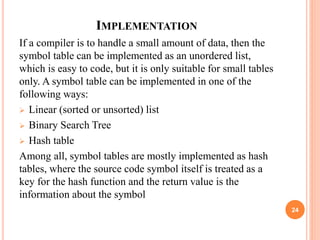
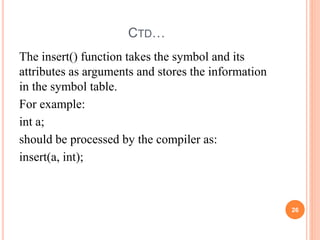
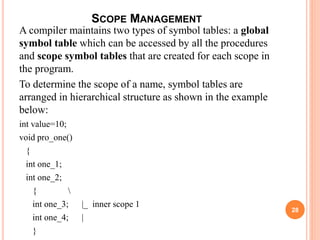
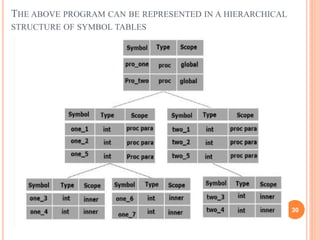
- Symbol tables stored information about program elements to check scopes, declarations, and types. They are typically implemented as hash tables for efficient lookups. Scope is determined by nested symbol tables.