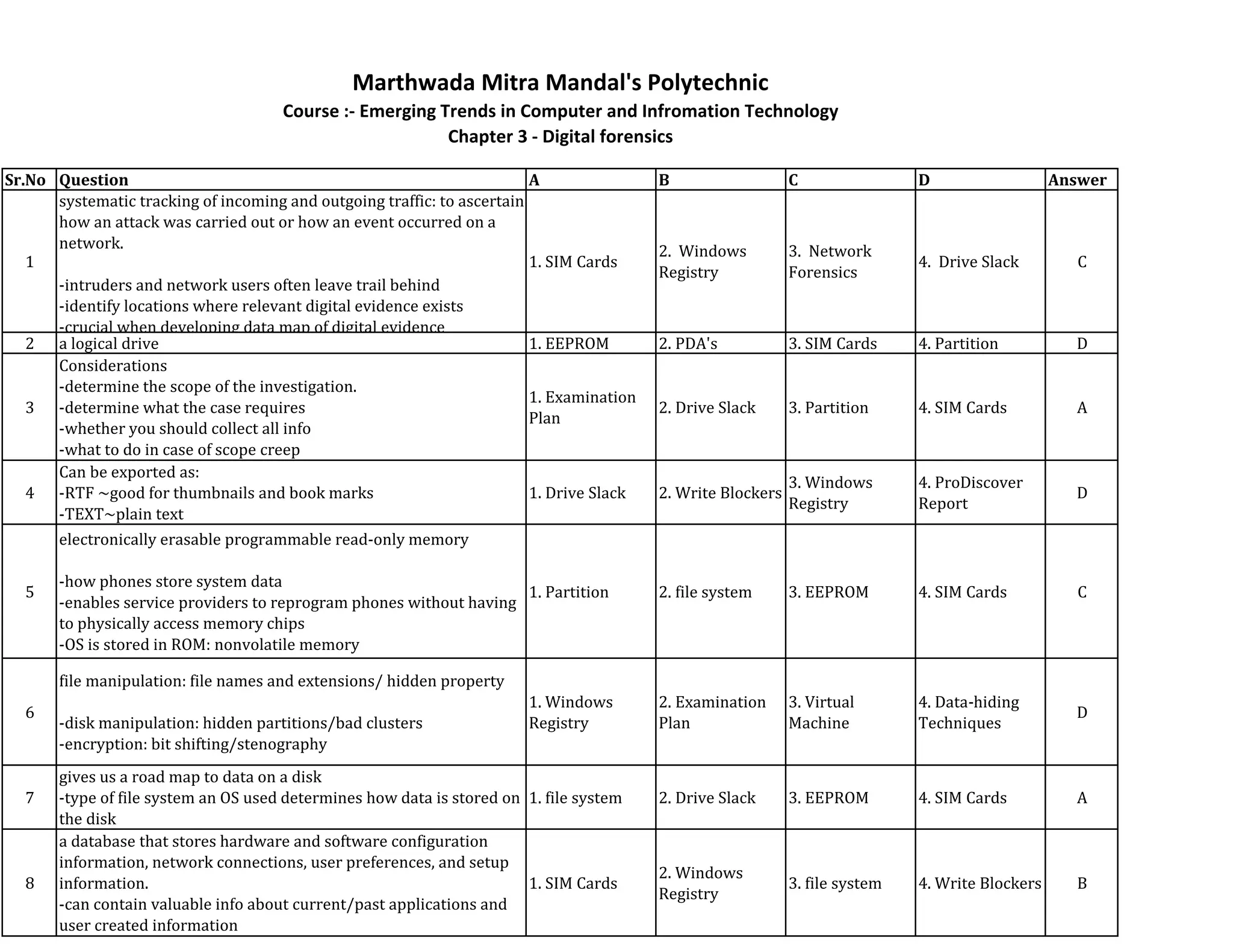
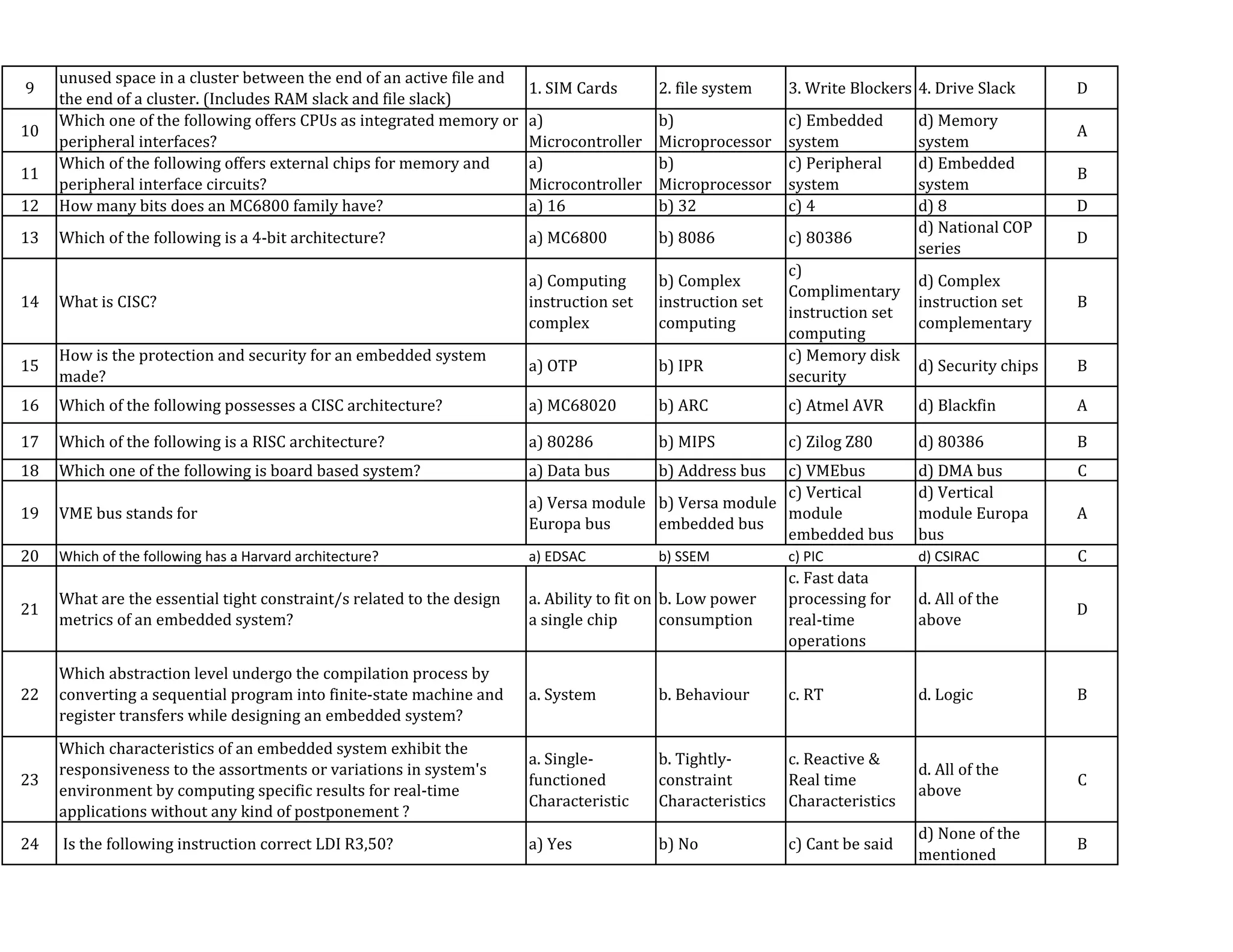
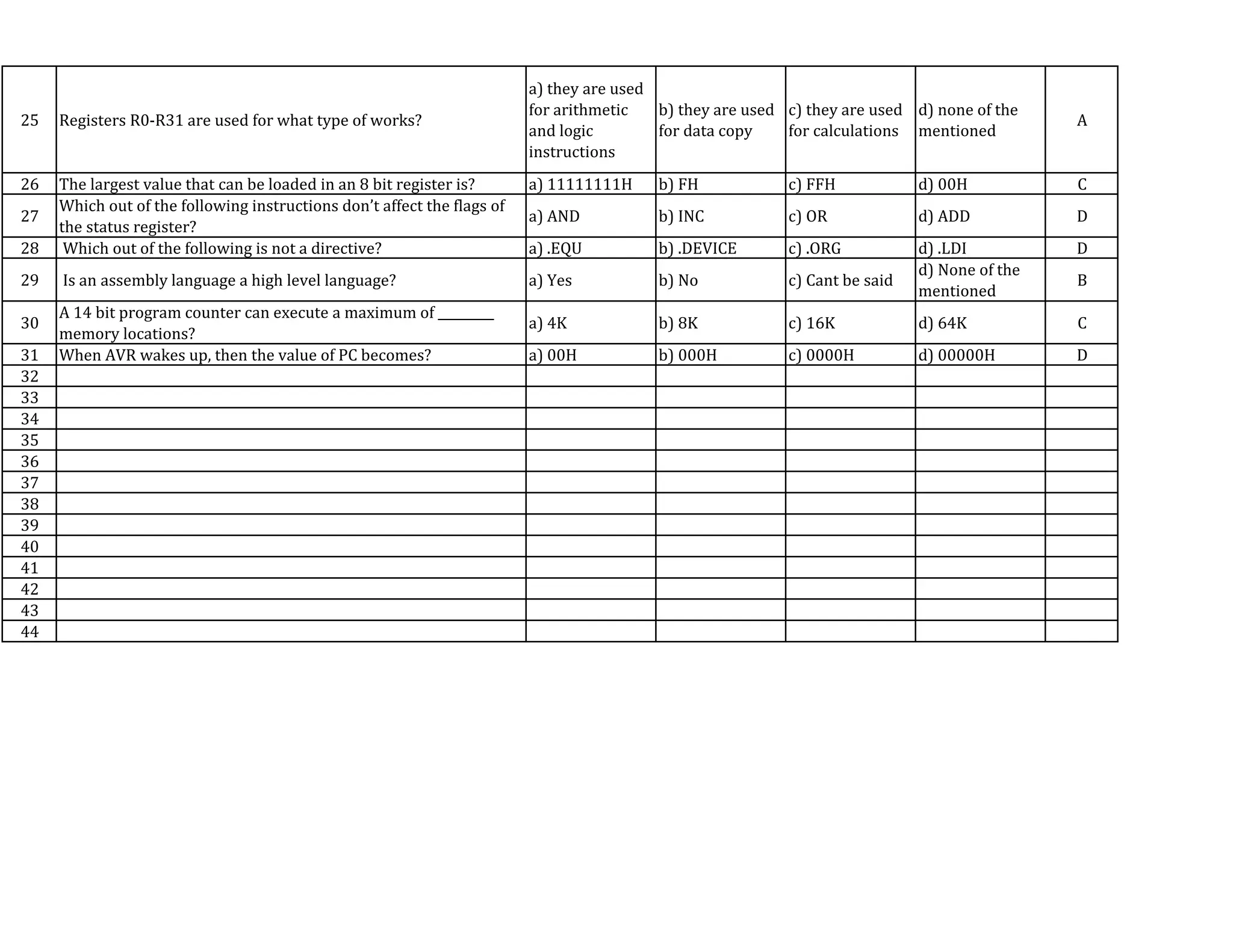
This document contains a quiz on digital forensics and embedded systems. It includes 43 multiple choice questions covering topics like digital evidence collection, drive slack, Windows registry, microcontrollers, RISC vs CISC architectures, VME bus, embedded system design constraints, assembly language, AVR registers and program counter. The questions test knowledge of technical concepts and terminology in these subject areas.