The document discusses security issues and threats in operating systems. It covers several topics:
1) Security must consider threats from outside the system and protect system resources from intruders attempting to breach security.
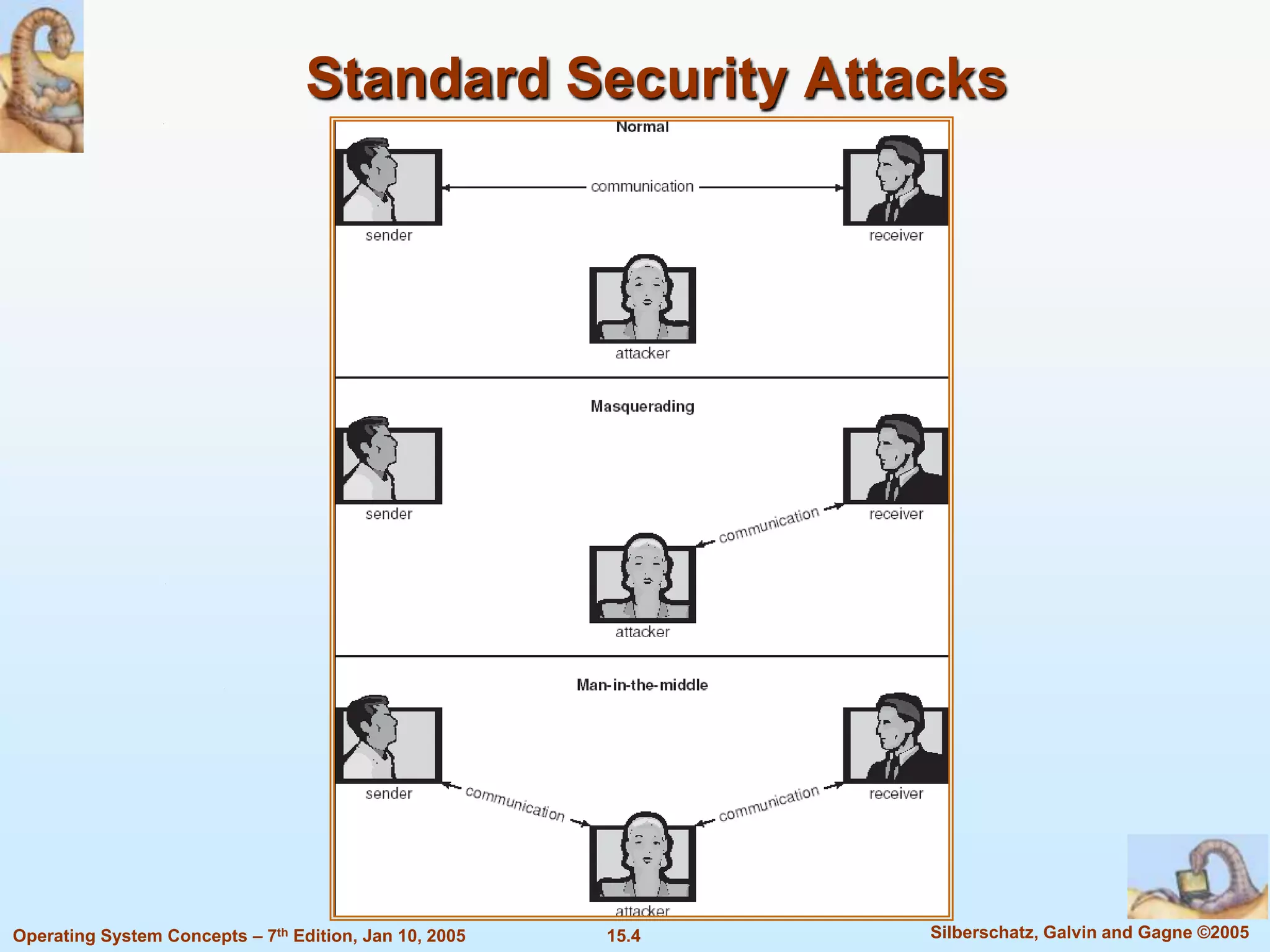
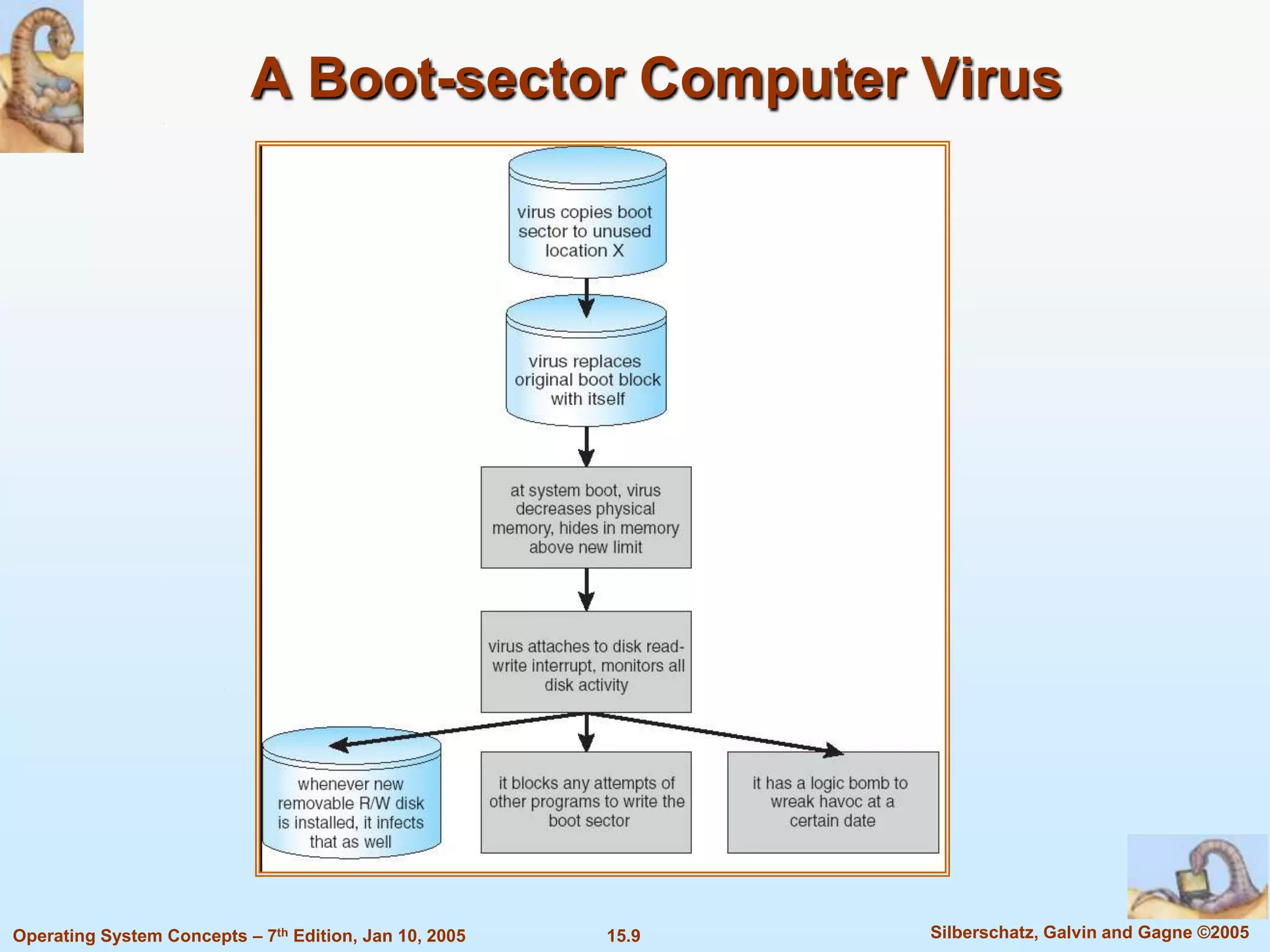
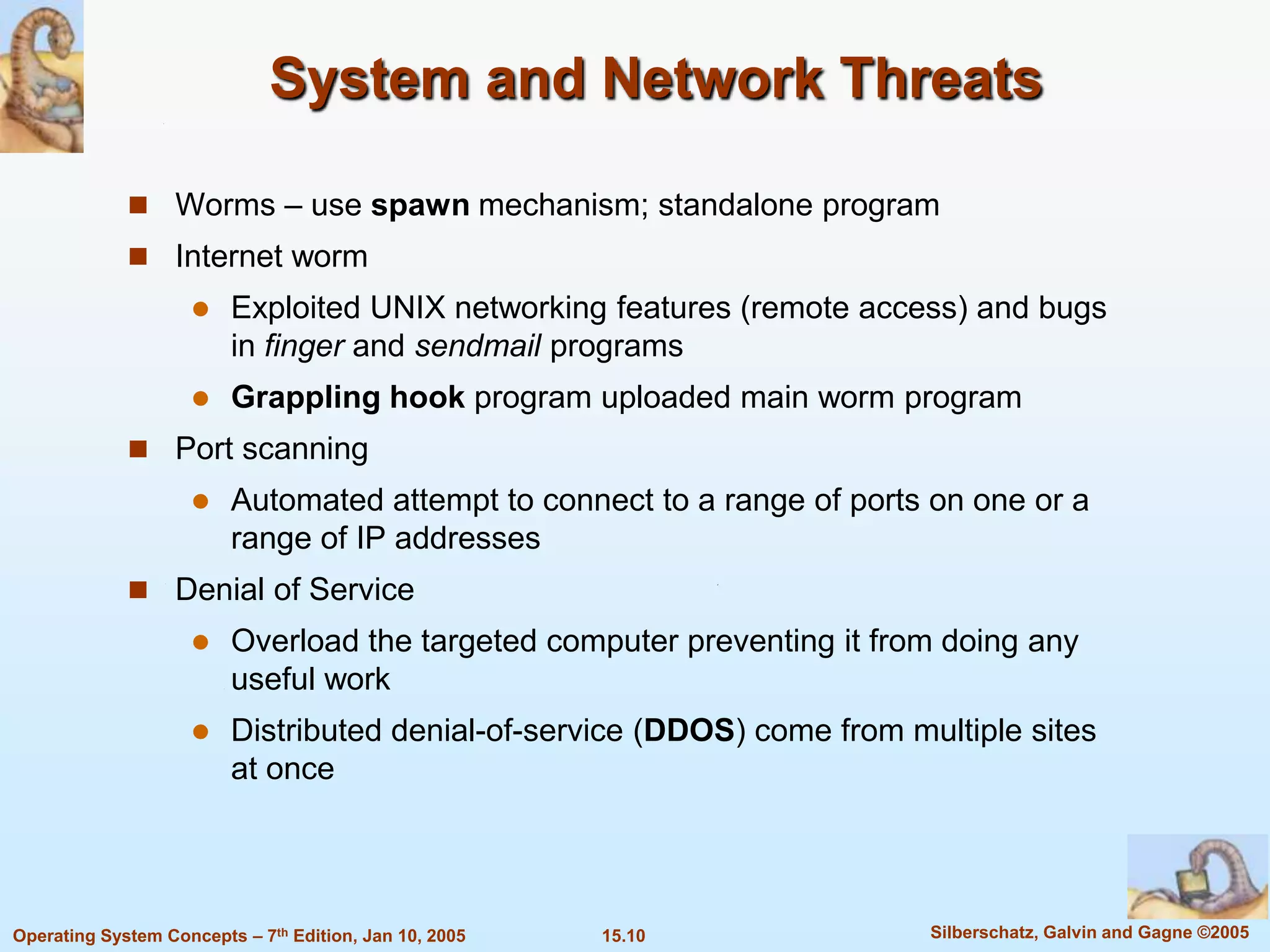
2) Common security violations include breaches of confidentiality, integrity, availability, and denial of service attacks.
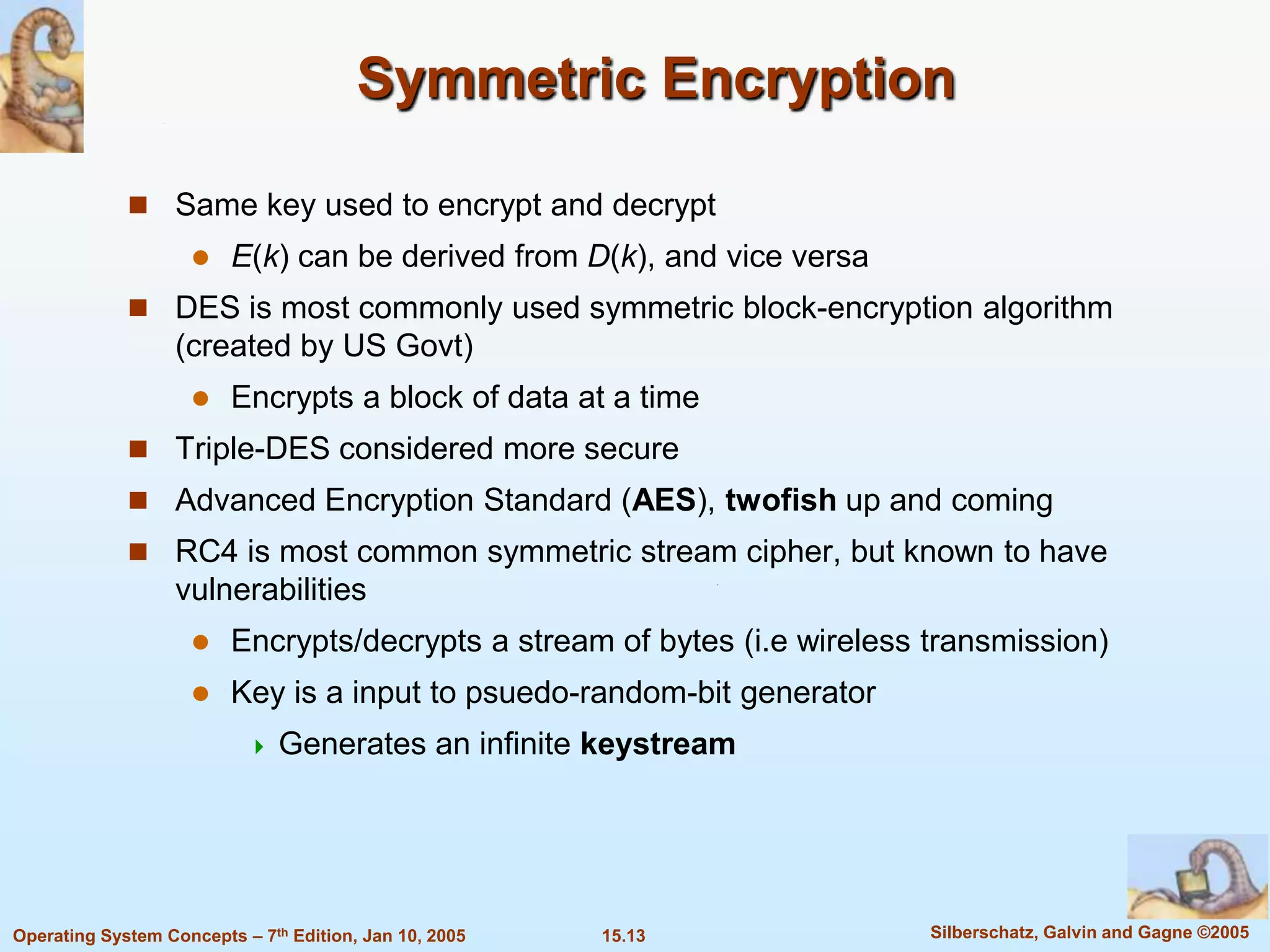
3) Effective security requires measures at the physical, human, operating system, and network levels as the system is only as secure as its weakest link.