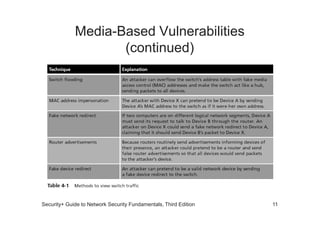
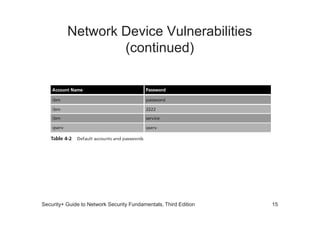
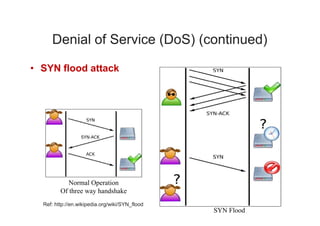
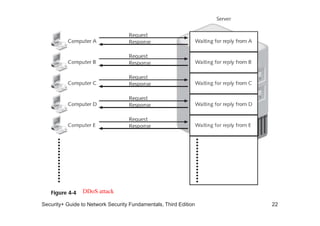
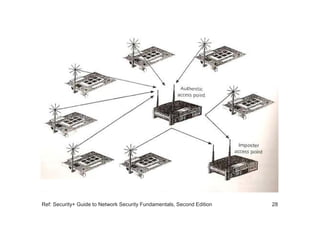
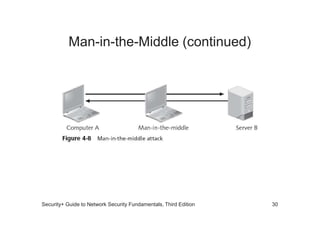
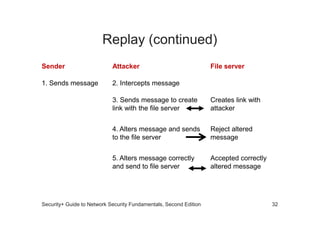
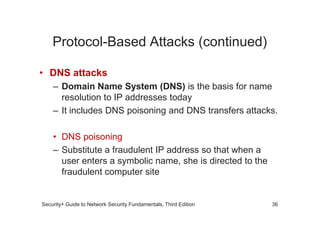
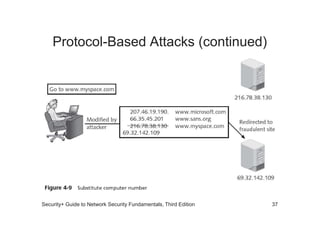
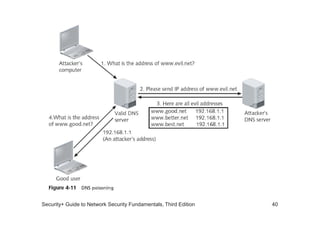
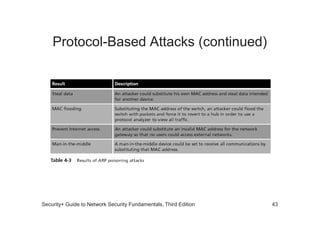
The document discusses network vulnerabilities, categorized into media-based and device-based vulnerabilities. It details various methods of network attacks, including denial of service, spoofing, and man-in-the-middle attacks, alongside prevention strategies for each. Additionally, it highlights how both legitimate and malicious tools can be utilized to monitor network traffic, emphasizing the importance of strong security practices.