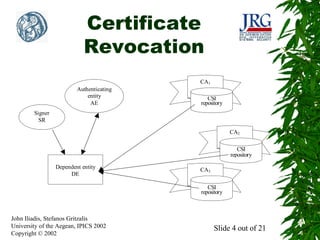
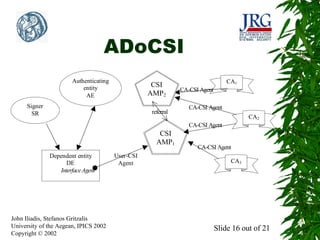
This document presents an alternative mechanism for disseminating certificate status information called ADoCSI (Alternative Dissemination of Certificate Status Information). ADoCSI uses software agents to retrieve and validate certificate status information on behalf of dependent entities in a transparent manner. The document outlines some of the problems that need to be addressed when using agents for certificate status information, such as how to protect agents and the information they carry from unauthorized modification. It also provides an overview of the components involved in ADoCSI, including agent meeting places, certificate authority agents, and an interface agent.