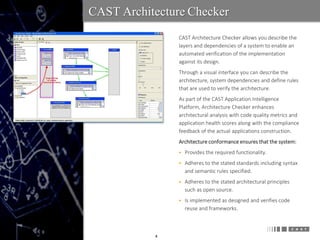
The document discusses the challenges and complexities of software architecture, emphasizing the importance of integration and adherence to architectural principles for system integrity. It introduces the CAST Architecture Checker, a tool that automates compliance verification against design specifications, enhancing code quality and application health. It advocates for early detection of architectural errors to mitigate risks and reduce maintenance costs in software development.