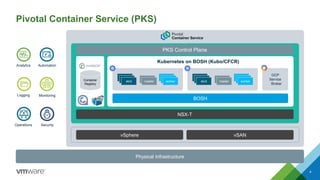
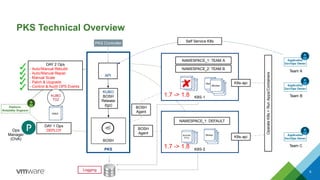
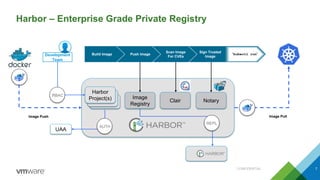
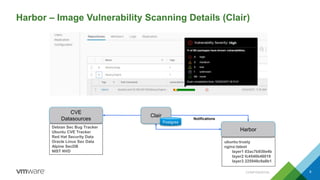
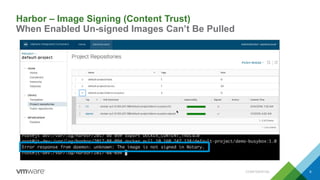
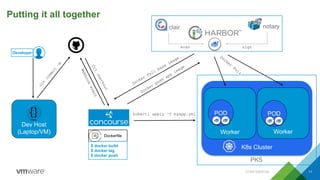
The document provides an overview of building developer pipelines using PKS, Harbor, Clair, and Concourse, highlighting their components and functions. It emphasizes the importance of security features like image vulnerability scanning and signing, and outlines the operational processes involved in managing Kubernetes applications. Additionally, the presentation includes a demo and discusses lessons learned for enhancing the development workflow and security.