Why cyber security is a priority for your retail business
•
0 likes•51 views
Our integrated security solution help retailers from a barrage of cyber threats, allowing them to continue operations without the worry or fear of an interruption to service.
Report
Share
Report
Share
Download to read offline
Recommended
SD-WAN iFLX-Brochure

SD-WAN iFLX solution gives you operational simplicity, application-level prioritization, and visibility, integrated security, enhanced overall business application environment as well as the much-needed resilience at an affordable price point.
Build a Workspace of the Future

TTBS can help you setup a complete digital workspace that offers best-in-class connectivity, collaboration and security at low costs.
With simple-to-use interfaces, our solution is easy for organisations to implement and use. Smartflo is a cloud based communication
suite that boosts digital connectivity, streamlines business processes and delivers better customer experience.
Manufacturing Sector - Building The Industry 4.0 Environment

While the manufacturing sector was already shifting towards the Industry 4.0 landscape, the pandemic compelled it to innovate and adopt digital solutions at an accelerated pace.
Cloud Computing Security

Cloud security is a must have. Also, an expectation AND a business accelerator.
But what really changes with cloud ? Cloud is not more or less secure : the security posture evolves..
Orange Business Live 2013 M2M breakout

M2M breakout presentation shared at Orange Business Live, Prague, June 2013. More information about M2M at http://oran.ge/12luzgR
Enabling Telcos to lead Digital Transformation using 5G

One of the most discussed topic amongst CSPs/DSPs and IT service providers is – How can Telcos enable 5G for their customers, use cases and monetization. A Collective effort towards industry 4.0
I tried to answer (or at least address) all these pressing questions in this article. Also, talked about 5G concepts and business fitment of 5G into Telcos.
Recommended
SD-WAN iFLX-Brochure

SD-WAN iFLX solution gives you operational simplicity, application-level prioritization, and visibility, integrated security, enhanced overall business application environment as well as the much-needed resilience at an affordable price point.
Build a Workspace of the Future

TTBS can help you setup a complete digital workspace that offers best-in-class connectivity, collaboration and security at low costs.
With simple-to-use interfaces, our solution is easy for organisations to implement and use. Smartflo is a cloud based communication
suite that boosts digital connectivity, streamlines business processes and delivers better customer experience.
Manufacturing Sector - Building The Industry 4.0 Environment

While the manufacturing sector was already shifting towards the Industry 4.0 landscape, the pandemic compelled it to innovate and adopt digital solutions at an accelerated pace.
Cloud Computing Security

Cloud security is a must have. Also, an expectation AND a business accelerator.
But what really changes with cloud ? Cloud is not more or less secure : the security posture evolves..
Orange Business Live 2013 M2M breakout

M2M breakout presentation shared at Orange Business Live, Prague, June 2013. More information about M2M at http://oran.ge/12luzgR
Enabling Telcos to lead Digital Transformation using 5G

One of the most discussed topic amongst CSPs/DSPs and IT service providers is – How can Telcos enable 5G for their customers, use cases and monetization. A Collective effort towards industry 4.0
I tried to answer (or at least address) all these pressing questions in this article. Also, talked about 5G concepts and business fitment of 5G into Telcos.
Cloud Managed Mobility

Looking back over the past decade on the technologies that have had the most significant business impacts, mobility and the cloud would certainly be among top contenders.
The place where mobility and the cloud come together—called Cloud-Managed Mobility—is having an even bigger impact.
If you have any questions, please reach us at questions@coranet.com.
Leveraging mobility - turning enterprise wireless into a business enabler

Mobility is no longer about the provisioning of remote access or BYOD. Mobility is about enabling organisations to communicate with customers in different ways, create new revenue streams, reduce infrastructure costs and obtain a competitive advantage in the market, without compromising on security or manageability.
Ericom Connect datasheet 

Whether you require workforce mobility, extreme scalability or an easy, out-of-the-box connection broker, Ericom Connect offers it all — in one secure, robust access management solution that is easy to deploy and use.
Connect features 100% web-based administration, powerful reporting for business insight and an advanced grid architecture that is capable of supporting thousands of hosting servers and hundreds of thousands of user sessions.
For more information, visit: http://j.mp/Ericom-Connect
Twitter and ibm form strategic relationship

Quick recap of the IBM and Twitter relationship and effects
Discussion paper: ”The coming obsolescence of the enterprise network” 

A new Ericsson discussion paper suggests the demand for accessibility and flexibility is changing enterprises attitude towards their networks, moving the focus from protecting the perimeter of the enterprise network to protecting the business-critical data and application environment. It opens up opportunities for telecom operators to provide as-a-service offering. Read the paper and talk to Ericsson to find more about, for example, how to address this transformation, what a winning strategy looks like for operators, what bundled offerings are like to gain most market traction.
The Relevance of IoT and 5G for Multicloud - Vodafone and IBM join Forces

Cloud drives digitization. But what's preventing customers from moving to the cloud. Network and connectivity play a crucial part. That's why Vodafone and IBM have joined forces and will create end-to-end solutions under one roof. This includes edge cloud services and mobile applications in exclusive collaboration with Apple.
Researching How Cloud Computing Enhances the Businesses Growth

The Internet of Things (IoT) changes several sectors, including education, logistics, and manufacturing. The IoT is a web-based system that integrates and syncs a wide range of machines or appliances with gates, third-party technologies, and apps on machinery and cloud computing networks. Cloud computing performs a significant part in the framework layer with the thriving development of IoT. In a range of industries cloud computing technology was built into unique forms of cloud computing: Everything-as-a-Sevice (Xaas), Education-as-a-Service (EaaS), Logistics-as-a-Service (LaaS), and Manufacturing-as-a-Service (MaaS). Researchers and professionals have drawn substantial attention to the applicability of cloud computing in different sectors. Essential evaluation, framework architecture, and structural study are the primary forms of science. Large data, computational technology, service orientation, and IoT refer to cloud computing systems (e.g., XaaS, EaaS, LaaS, MaaS). This research analyzed the technological patterns in new cloud computing technology and examined cloud computing studies. The results demonstrate that knowledge and innovation are the main concerns guiding cloud science.
Redefining Business Mobility and Customer Experience

The financial services industry faces unprecedented pressure from customer demands, regulatory mandates, emerging technologies and highly-competitive markets. Citrix powers
financial services mobility to help companies deliver consistent customer service across traditional and digital channels, improve employee productivity and retention, and increase
IT efficiency, while at the same time ensuring security across their evolving infrastructures.
Infographic flexible connectivity with hybrid network

A flexible and secure hybrid network is more and more required for modern entreprises.
This kind of network can evolve with businesses as they grow.
2016 Cloud Unbound Briefing

The Microsoft Cloud includes Azure, Office 365 and much more. During this presentation I give an overview of the platform and talk specifically about the productivity portion of the Microsoft Cloud and the services Oakwood provides to implement Office 365 for customers.
Preparing healthcare networks for mobility, digitalization and IoT

Healthcare Solutions: Will your network support the growing demands that mobility, digitization and IoT will bring?
Data API as a Foundation for Systems of Engagement

From the creators of SlashDB (http://www.slashdb.com).
Enterprise evolution to Systems of Engagement will only succeed if they can leverage existing Systems of Record - databases. But database content can be difficult to discover and share.
We are introducing the idea of Resource Oriented Architecture as a foundation for building enterprise systems of engagement. ROA is a data abstraction layer (API), which uses URLs as references to the data at source (database).
- Triumph over data silos
- Enable data science and self-service reporting
- Develop enterprise mobile applications
The Top 10 IT Issues in Higher Ed

Extreme Networks presents the Top 10 IT Issues in Higher Ed for 2015 according to Educause.
Mobility at the network’s edge

Mobility at the network’s edge: how important is the network in the CIO’s end-user computing strategy?
I Brought My Own Device. Now What?

I Brought My Own Device. Now What? by Paul Andersen, Marketing Manager at Array Networks .
The consumerization of IT is underway. In its report Tablets Will Rule the Future Personal Computing Landscape, Forrester predicts sales of 375 million tablets in 2016 with over 750 million tablets in use.
Designing End-User Experience for Workplace of the Future

This whitepaper highlights how enterprises can use virtualization technologies to design and deliver superior end-user experience for Workplaces of the Future.
empowering your business with top-notch cybersecurity services.pdf

The urgency of cybersecurity cannot be underlined enough, especially in the face of alarming statistics released by the Federal Bureau of Investigation (FBI). The FBI's Internet Crime Complaint Center reported a staggering 69% increase in reported cybercrime incidences from 2019 to 2020.
More Related Content
What's hot
Cloud Managed Mobility

Looking back over the past decade on the technologies that have had the most significant business impacts, mobility and the cloud would certainly be among top contenders.
The place where mobility and the cloud come together—called Cloud-Managed Mobility—is having an even bigger impact.
If you have any questions, please reach us at questions@coranet.com.
Leveraging mobility - turning enterprise wireless into a business enabler

Mobility is no longer about the provisioning of remote access or BYOD. Mobility is about enabling organisations to communicate with customers in different ways, create new revenue streams, reduce infrastructure costs and obtain a competitive advantage in the market, without compromising on security or manageability.
Ericom Connect datasheet 

Whether you require workforce mobility, extreme scalability or an easy, out-of-the-box connection broker, Ericom Connect offers it all — in one secure, robust access management solution that is easy to deploy and use.
Connect features 100% web-based administration, powerful reporting for business insight and an advanced grid architecture that is capable of supporting thousands of hosting servers and hundreds of thousands of user sessions.
For more information, visit: http://j.mp/Ericom-Connect
Twitter and ibm form strategic relationship

Quick recap of the IBM and Twitter relationship and effects
Discussion paper: ”The coming obsolescence of the enterprise network” 

A new Ericsson discussion paper suggests the demand for accessibility and flexibility is changing enterprises attitude towards their networks, moving the focus from protecting the perimeter of the enterprise network to protecting the business-critical data and application environment. It opens up opportunities for telecom operators to provide as-a-service offering. Read the paper and talk to Ericsson to find more about, for example, how to address this transformation, what a winning strategy looks like for operators, what bundled offerings are like to gain most market traction.
The Relevance of IoT and 5G for Multicloud - Vodafone and IBM join Forces

Cloud drives digitization. But what's preventing customers from moving to the cloud. Network and connectivity play a crucial part. That's why Vodafone and IBM have joined forces and will create end-to-end solutions under one roof. This includes edge cloud services and mobile applications in exclusive collaboration with Apple.
Researching How Cloud Computing Enhances the Businesses Growth

The Internet of Things (IoT) changes several sectors, including education, logistics, and manufacturing. The IoT is a web-based system that integrates and syncs a wide range of machines or appliances with gates, third-party technologies, and apps on machinery and cloud computing networks. Cloud computing performs a significant part in the framework layer with the thriving development of IoT. In a range of industries cloud computing technology was built into unique forms of cloud computing: Everything-as-a-Sevice (Xaas), Education-as-a-Service (EaaS), Logistics-as-a-Service (LaaS), and Manufacturing-as-a-Service (MaaS). Researchers and professionals have drawn substantial attention to the applicability of cloud computing in different sectors. Essential evaluation, framework architecture, and structural study are the primary forms of science. Large data, computational technology, service orientation, and IoT refer to cloud computing systems (e.g., XaaS, EaaS, LaaS, MaaS). This research analyzed the technological patterns in new cloud computing technology and examined cloud computing studies. The results demonstrate that knowledge and innovation are the main concerns guiding cloud science.
Redefining Business Mobility and Customer Experience

The financial services industry faces unprecedented pressure from customer demands, regulatory mandates, emerging technologies and highly-competitive markets. Citrix powers
financial services mobility to help companies deliver consistent customer service across traditional and digital channels, improve employee productivity and retention, and increase
IT efficiency, while at the same time ensuring security across their evolving infrastructures.
Infographic flexible connectivity with hybrid network

A flexible and secure hybrid network is more and more required for modern entreprises.
This kind of network can evolve with businesses as they grow.
2016 Cloud Unbound Briefing

The Microsoft Cloud includes Azure, Office 365 and much more. During this presentation I give an overview of the platform and talk specifically about the productivity portion of the Microsoft Cloud and the services Oakwood provides to implement Office 365 for customers.
Preparing healthcare networks for mobility, digitalization and IoT

Healthcare Solutions: Will your network support the growing demands that mobility, digitization and IoT will bring?
Data API as a Foundation for Systems of Engagement

From the creators of SlashDB (http://www.slashdb.com).
Enterprise evolution to Systems of Engagement will only succeed if they can leverage existing Systems of Record - databases. But database content can be difficult to discover and share.
We are introducing the idea of Resource Oriented Architecture as a foundation for building enterprise systems of engagement. ROA is a data abstraction layer (API), which uses URLs as references to the data at source (database).
- Triumph over data silos
- Enable data science and self-service reporting
- Develop enterprise mobile applications
The Top 10 IT Issues in Higher Ed

Extreme Networks presents the Top 10 IT Issues in Higher Ed for 2015 according to Educause.
Mobility at the network’s edge

Mobility at the network’s edge: how important is the network in the CIO’s end-user computing strategy?
I Brought My Own Device. Now What?

I Brought My Own Device. Now What? by Paul Andersen, Marketing Manager at Array Networks .
The consumerization of IT is underway. In its report Tablets Will Rule the Future Personal Computing Landscape, Forrester predicts sales of 375 million tablets in 2016 with over 750 million tablets in use.
Designing End-User Experience for Workplace of the Future

This whitepaper highlights how enterprises can use virtualization technologies to design and deliver superior end-user experience for Workplaces of the Future.
What's hot (20)
Leveraging mobility - turning enterprise wireless into a business enabler

Leveraging mobility - turning enterprise wireless into a business enabler
Discussion paper: ”The coming obsolescence of the enterprise network” 

Discussion paper: ”The coming obsolescence of the enterprise network”
The Relevance of IoT and 5G for Multicloud - Vodafone and IBM join Forces

The Relevance of IoT and 5G for Multicloud - Vodafone and IBM join Forces
Researching How Cloud Computing Enhances the Businesses Growth

Researching How Cloud Computing Enhances the Businesses Growth
Redefining Business Mobility and Customer Experience

Redefining Business Mobility and Customer Experience
Infographic flexible connectivity with hybrid network

Infographic flexible connectivity with hybrid network
Preparing healthcare networks for mobility, digitalization and IoT

Preparing healthcare networks for mobility, digitalization and IoT
Data API as a Foundation for Systems of Engagement

Data API as a Foundation for Systems of Engagement
Designing End-User Experience for Workplace of the Future

Designing End-User Experience for Workplace of the Future
Similar to Why cyber security is a priority for your retail business
empowering your business with top-notch cybersecurity services.pdf

The urgency of cybersecurity cannot be underlined enough, especially in the face of alarming statistics released by the Federal Bureau of Investigation (FBI). The FBI's Internet Crime Complaint Center reported a staggering 69% increase in reported cybercrime incidences from 2019 to 2020.
Cyber security providers adopt strategic defences 

Digital security providers are taking on a military approach in defending network security as more companies suffer from cyber attacks.
What is the significance of cybersecurity in cloud.pptx

Cloud security, often known as cloud computing security, is a branch of cybersecurity that focuses on protecting cloud computing platforms.
https://www.infosectrain.com/courses/ccsp-certification-training/
Cybersecurity- What Retailers Need To Know

The retail industry is favorite among cyber-attackers due to a large number of payment transactions on a regular basis. Protect your retail business from cyber-attacks. Cybersecurity is a major concern for retailers that need to be advanced with time.
What is the significance of cybersecurity in cloud.pptx

Cloud security, often known as cloud computing security, is a branch of cybersecurity that focuses on protecting cloud computing platforms. Cloud security refers to the entire bundle of technology, protocols, regulations, and best practices that secure cloud computing environments, cloud-based applications, and cloud-based data. Cloud security, to put it simply, is the discipline of defending cloud-based data, applications, and infrastructure against cyber threats.
TechFai.com.pdf

A technology business specializes in developing and providing innovative solutions, products, or services that leverage advanced digital tools and processes to address various needs and challenges across industries.
Why Cloud Security Matters in Today's Business World

While the benefits of cloud computing are abundant, transitioning to this modern platform requires a thorough understanding of the associated risks and, more importantly, how to safeguard the organization, its personnel, and its customers. Exploring the specifics of cloud security is essential to addressing these concerns.
Cybersecurity – a critical business issue

Cybersecurity companies measures can help with risk management by preventing cyber-attacks, data breaches, and identity theft.
Information Security Management System in the Banking Sector

Information Security Management System design. Information security governance approaches comparison. ISMS processes. ISMS implementation. The biggest threats in the Banking sector. The future of banking and payment systems. The challenges and future of banking. Cybersecurity solutions for Financial services.
Cybersecurity

Cyber crimes are on the rise and especially prevalent during the global pandemic where hackers leverage the vulnerabilities of organisations for new opportunities through technology.
Hospitals, for instance, are more likely to pay ransoms to restore access to their servers. Similarly, criminals may believe that corporations grappling with economic turmoil or logistical crises will be similarly easy to manipulate.
Crucial Layers_ Exploring the Depth of Enterprise Cyber Security.pdf

Enterprise cybersecurity is a multi-layered approach that demands continuous adaptation to the evolving threat landscape. By understanding and implementing the crucial layers discussed above, businesses can fortify their defenses against cyber threats. Choosing the right enterprise IT solutions and adopting a proactive mindset are key to maintaining a robust cybersecurity posture in the age of digital connectivity.
HOW TO AUGMENT YOUR CNI CYBERSECURITY WHEN USING CLOUD TECHNOLOGY.docx

Ensuring that businesses’ most critical cybersecurity infrastructures are secure and resilient must be a top priority.
Keeping your critical data from being attacked or exploited by internal or external threats is vital. With digitalisation and digitisation, many businesses are making the transition from traditional networks to cloud technology, giving cyber-attackers more leverage to access critical data. https://voror.io/sd-wan-cryptography/
Skills You Need for A Career in Cyber Security

You can learn from specialists to acquire these crucial abilities, which you must develop to have a successful career in cyber security. The top training facility for cyber security education in Delhi is CETPA Infotech.
Improve network safety through better visibility – Netmagic

What makes the next-generation firewall better than the traditional firewalls in protecting your data from hackers? Know more information from Netmagic!
Similar to Why cyber security is a priority for your retail business (20)
empowering your business with top-notch cybersecurity services.pdf

empowering your business with top-notch cybersecurity services.pdf
What is the significance of cybersecurity in cloud.pptx

What is the significance of cybersecurity in cloud.pptx
What is the significance of cybersecurity in cloud.pptx

What is the significance of cybersecurity in cloud.pptx
Why Cloud Security Matters in Today's Business World

Why Cloud Security Matters in Today's Business World
Information Security Management System in the Banking Sector

Information Security Management System in the Banking Sector
Crucial Layers_ Exploring the Depth of Enterprise Cyber Security.pdf

Crucial Layers_ Exploring the Depth of Enterprise Cyber Security.pdf
HOW TO AUGMENT YOUR CNI CYBERSECURITY WHEN USING CLOUD TECHNOLOGY.docx

HOW TO AUGMENT YOUR CNI CYBERSECURITY WHEN USING CLOUD TECHNOLOGY.docx
Improve network safety through better visibility – Netmagic

Improve network safety through better visibility – Netmagic
More from Tata Tele Business Services
from-adding-value-to-adding-revenue-a-changed-landscape-of-outsourcing.pdf

from-adding-value-to-adding-revenue-a-changed-landscape-of-outsourcing.pdfTata Tele Business Services
Outsourcing changes the landscape from adding value to adding revenues
Leading Digital Marketing Agency Integrates Voice and Data Communication with...

Leading Digital Marketing Agency Integrates Voice and Data Communication with...Tata Tele Business Services
Know why a unified communication system with voice and data services was designed without uprooting the existing setup.
SmartOffice Business Broadband

Digital adoption in India has sparked the ability to access high speed, reliable internet to increase productivity, revenue, and accelerate growth.
MPLS VPN Solution

Know how MPLS VPN solution enhanced data speed and helped the Analytical Instrument Supplier company to manage traffic.
Big Data and the Telecom Industry

Get an understanding of how the proliferation of smartphones and the growth in mobile internet led to the emergence of big data.
SMS Solutions 

Know how With an sms solution, enterprises can handle all of their bulk messaging requirements in one place.
CyberSecurity

Our Endpoint security solution enables IT teams to
pinpoint and impede the cyber risks that usually go
undetected.
MPLS VPN 

MPLS network providers help set up an MPLS VPN for your business that will boost the connectivity and growth of your company. The choice regarding the service provider also depends on other factors such as cost, current business needs, long-term goals, routing protocols, etc.
Smart Internet

The new Smart Internet offering from Tata Tele
Business Services (TTBS) is a state-of-the-art solution
which helps SMBs get robust connectivity, security,
manageability, and clear visibility of its users and
network. It is an internet leased line bundled with
cloud-based security and a Do-It-Yourself (DIY)
interface which is easy to access, install, use, and view.
Ultra Lola

Ultra LOLA offered by Tata Tele Business Services is an ultra low latency leased line tailored for high speed trading. Its is a two way connectivity channel to bring NSE and BSE on a secure network.
How is the cloud empowering the education industry. 

Cloud-based platforms saved the 2020-21 session from becoming a zero academic year, and the education industry realised the long-term potential of this technology for its operations.
Microsoft 365 Brochure - 헠헲헲혁 헬헼혂헿 헕혂혀헶헻헲혀혀 헚헼헮헹혀

Microsoft 365 is a full suite of productivity tools, now bundled together and priced attractively to ensure that all SMBs can simplify their internal processes, boost their productivity, and protect their valuable data against cybercriminals
EZ Cloud Connect 

EZ Cloud Connect from Tata Tele Business Services (TTBS) is designed to address these concerns and offers businesses a one-stop solution that, along with eliminating multiple-entry interaction is SLA-compliant and easily operable.
How is the cloud empowering the education industry.

Digitalisation became even more critical in the pandemic phase when the cloud helped the education sector to survive and thrive.
Fleet Tracking Systems Across Businesses

As an application of IoT technology, a fleet tracking solution helps a business track its moving vehicles. Signals shared between sensors and GPS satellites monitor the movement of trucks, cars, and buses.
Smartflo - Cloud Communication Suite

Flow forward with our cloud communication solutions, Smartflo for a business world without boundaries.
DoBig Webinar | The Rise of #SaaS | Software Benefits without CapEx

#SaaS is proving to be a game-changer with its cost-saving advantages for businesses of all sizes. But that's not it. Watch on to explore the possibilities.
Mr Omkar Malage, Senior Industry Analyst, Frost & Sullivan, tells us how #SaaS is shaping businesses by making technology more affordable, accessible, secure, and adaptable.
Tata Tele Business Services has a wide range of SaaS. Be technology ready with our state-of-the-art solutions:
1. Hosted IVR - https://bit.ly/2ZqjQI5
2. Hosted OBD - https://bit.ly/2YmTCKb
3. Digital Survey - https://bit.ly/2YEBJG4
4. Live Chat - https://bit.ly/2SZlvlL
5. Document Management System - https://bit.ly/2HmVCbP
Visit our website to know more about our Connectivity, Collaboration, Security, Cloud-and-SaaS, IoT and Marketing Solutions: https://www.tatateleservices.com/
Like. Comment. Share.
Place your business enquiries here: http://bit.do/eN9Tj
Follow us on social media:
Facebook: http://bit.do/eHacx
LinkedIn: http://bit.do/eHacN
Twitter: http://bit.do/eHacP
Instagram: http://bit.do/eHacT
YouTube: https://bit.ly/31nHxS9
DoBig Webinar | #Cloud Computing in Business | Cloud for Enhanced Business Co...

DoBig Webinar | #Cloud Computing in Business | Cloud for Enhanced Business Co...Tata Tele Business Services
The power of #Cloud is unifying communications seamlessly across the globe.
Nithin Ramesh Rao, Consulting Analyst, Frost & Sullivan, helps us understand how Cloud Telephony increases revenue and reduces capital expenditure, operational costs, and market penetration barriers.
#Webinar #Technology #TechWorld #Trending
Our Cloud solutions like Document Management System, Content Delivery Network, Live Chat, and Digital Survey ensure reliable, cost-efficient, and secure connectivity and collaboration.
Check out our Cloud solutions: https://www.tatateleservices.com/business-services/cloud-and-saas
Visit our website to know more about our Connectivity, Collaboration, Security, Cloud-and-SaaS, IoT and Marketing Solutions: https://www.tatateleservices.com/
Like. Comment. Share.
Check out various webinars by Tata Tele Business Services where industry experts deep-dive into the world of technology and decipher the uses of the latest technology trends into small and medium businesses.
Discover more webinars: http://bit.do/eWqcE
Place your business enquiries here: http://bit.do/eN9Tj
Follow us on social media:
Facebook: http://bit.do/eHacx
LinkedIn: http://bit.do/eHacN
Twitter: http://bit.do/eHacP
Instagram: http://bit.do/eHacT
YouTube: https://bit.ly/31nHxS9DoBig Webinar - How #IoT can transform your business - Omkar Malage, Frost & ...

DoBig Webinar - How #IoT can transform your business - Omkar Malage, Frost & ...Tata Tele Business Services
Do you know how #IoT can help your business grow? Watch this webinar with us and understand the uses of IoT in the transformation of business operations.
Mr. Omkar Malage, Senior Industry Analyst, Frost & Sullivan guides us all through how Internet of Things can empower new enterprises with upcoming technologies.
Visit our website to know more about our Connectivity, Collaboration, Security, Cloud-and-SaaS, IoT and Marketing Solutions: https://www.tatateleservices.com/
Check out our IoT enabled solutions here: https://www.tatateleservices.com/business-services/iot-solutions
Like. Comment. Share.
Place your business enquiries here: http://bit.do/eN9Tj
Follow us on social media:
Facebook: http://bit.do/eHacx
LinkedIn: http://bit.do/eHacN
Twitter: http://bit.do/eHacP
Instagram: http://bit.do/eHacT
YouTube: http://bit.do/eT9AWLocation Based Services - IoT Enabled Solutions for Real-Time Location Update...

Location Based Services - IoT Enabled Solutions for Real-Time Location Update...Tata Tele Business Services
Mr. Abhijit Roy, IoT, Cloud & SaaS – Product Strategy Lead at TTBS explains how IoT enabled Location Based Services offered by TTBS empower businesses of all sizes with visibility and tracking facility of their assets.
He further elaborates on how IoT devices are the future of technology and are ever growing.
With solutions like Asset Management, School Bus Tracking, Fleet Management, Workforce Management and RFID based tracking, Tata Tele Business Services aims to widen the IoT ecosystem.
Visit our website to know more about our Connectivity, Collaboration, Security, Cloud-and-SaaS, IoT and Marketing Solutions: https://www.tatateleservices.com/
Like. Comment. Share.
Follow us on social media:
Facebook: http://bit.do/eHacx
LinkedIn: http://bit.do/eHacN
Twitter: http://bit.do/eHacP
Instagram: http://bit.do/eHacTMore from Tata Tele Business Services (20)
from-adding-value-to-adding-revenue-a-changed-landscape-of-outsourcing.pdf

from-adding-value-to-adding-revenue-a-changed-landscape-of-outsourcing.pdf
Leading Digital Marketing Agency Integrates Voice and Data Communication with...

Leading Digital Marketing Agency Integrates Voice and Data Communication with...
How is the cloud empowering the education industry. 

How is the cloud empowering the education industry.
How is the cloud empowering the education industry.

How is the cloud empowering the education industry.
DoBig Webinar | The Rise of #SaaS | Software Benefits without CapEx

DoBig Webinar | The Rise of #SaaS | Software Benefits without CapEx
DoBig Webinar | #Cloud Computing in Business | Cloud for Enhanced Business Co...

DoBig Webinar | #Cloud Computing in Business | Cloud for Enhanced Business Co...
DoBig Webinar - How #IoT can transform your business - Omkar Malage, Frost & ...

DoBig Webinar - How #IoT can transform your business - Omkar Malage, Frost & ...
Location Based Services - IoT Enabled Solutions for Real-Time Location Update...

Location Based Services - IoT Enabled Solutions for Real-Time Location Update...
Recently uploaded
Knowledge engineering: from people to machines and back

Keynote at the 21st European Semantic Web Conference
Elevating Tactical DDD Patterns Through Object Calisthenics

After immersing yourself in the blue book and its red counterpart, attending DDD-focused conferences, and applying tactical patterns, you're left with a crucial question: How do I ensure my design is effective? Tactical patterns within Domain-Driven Design (DDD) serve as guiding principles for creating clear and manageable domain models. However, achieving success with these patterns requires additional guidance. Interestingly, we've observed that a set of constraints initially designed for training purposes remarkably aligns with effective pattern implementation, offering a more ‘mechanical’ approach. Let's explore together how Object Calisthenics can elevate the design of your tactical DDD patterns, offering concrete help for those venturing into DDD for the first time!
Key Trends Shaping the Future of Infrastructure.pdf

Keynote at DIGIT West Expo, Glasgow on 29 May 2024.
Cheryl Hung, ochery.com
Sr Director, Infrastructure Ecosystem, Arm.
The key trends across hardware, cloud and open-source; exploring how these areas are likely to mature and develop over the short and long-term, and then considering how organisations can position themselves to adapt and thrive.
Essentials of Automations: Optimizing FME Workflows with Parameters

Are you looking to streamline your workflows and boost your projects’ efficiency? Do you find yourself searching for ways to add flexibility and control over your FME workflows? If so, you’re in the right place.
Join us for an insightful dive into the world of FME parameters, a critical element in optimizing workflow efficiency. This webinar marks the beginning of our three-part “Essentials of Automation” series. This first webinar is designed to equip you with the knowledge and skills to utilize parameters effectively: enhancing the flexibility, maintainability, and user control of your FME projects.
Here’s what you’ll gain:
- Essentials of FME Parameters: Understand the pivotal role of parameters, including Reader/Writer, Transformer, User, and FME Flow categories. Discover how they are the key to unlocking automation and optimization within your workflows.
- Practical Applications in FME Form: Delve into key user parameter types including choice, connections, and file URLs. Allow users to control how a workflow runs, making your workflows more reusable. Learn to import values and deliver the best user experience for your workflows while enhancing accuracy.
- Optimization Strategies in FME Flow: Explore the creation and strategic deployment of parameters in FME Flow, including the use of deployment and geometry parameters, to maximize workflow efficiency.
- Pro Tips for Success: Gain insights on parameterizing connections and leveraging new features like Conditional Visibility for clarity and simplicity.
We’ll wrap up with a glimpse into future webinars, followed by a Q&A session to address your specific questions surrounding this topic.
Don’t miss this opportunity to elevate your FME expertise and drive your projects to new heights of efficiency.
Accelerate your Kubernetes clusters with Varnish Caching

A presentation about the usage and availability of Varnish on Kubernetes. This talk explores the capabilities of Varnish caching and shows how to use the Varnish Helm chart to deploy it to Kubernetes.
This presentation was delivered at K8SUG Singapore. See https://feryn.eu/presentations/accelerate-your-kubernetes-clusters-with-varnish-caching-k8sug-singapore-28-2024 for more details.
From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP...

From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP of Product, Amplitude
Connector Corner: Automate dynamic content and events by pushing a button

Here is something new! In our next Connector Corner webinar, we will demonstrate how you can use a single workflow to:
Create a campaign using Mailchimp with merge tags/fields
Send an interactive Slack channel message (using buttons)
Have the message received by managers and peers along with a test email for review
But there’s more:
In a second workflow supporting the same use case, you’ll see:
Your campaign sent to target colleagues for approval
If the “Approve” button is clicked, a Jira/Zendesk ticket is created for the marketing design team
But—if the “Reject” button is pushed, colleagues will be alerted via Slack message
Join us to learn more about this new, human-in-the-loop capability, brought to you by Integration Service connectors.
And...
Speakers:
Akshay Agnihotri, Product Manager
Charlie Greenberg, Host
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Epistemic Interaction - tuning interfaces to provide information for AI support

Paper presented at SYNERGY workshop at AVI 2024, Genoa, Italy. 3rd June 2024
https://alandix.com/academic/papers/synergy2024-epistemic/
As machine learning integrates deeper into human-computer interactions, the concept of epistemic interaction emerges, aiming to refine these interactions to enhance system adaptability. This approach encourages minor, intentional adjustments in user behaviour to enrich the data available for system learning. This paper introduces epistemic interaction within the context of human-system communication, illustrating how deliberate interaction design can improve system understanding and adaptation. Through concrete examples, we demonstrate the potential of epistemic interaction to significantly advance human-computer interaction by leveraging intuitive human communication strategies to inform system design and functionality, offering a novel pathway for enriching user-system engagements.
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
UiPath Test Automation using UiPath Test Suite series, part 4

Welcome to UiPath Test Automation using UiPath Test Suite series part 4. In this session, we will cover Test Manager overview along with SAP heatmap.
The UiPath Test Manager overview with SAP heatmap webinar offers a concise yet comprehensive exploration of the role of a Test Manager within SAP environments, coupled with the utilization of heatmaps for effective testing strategies.
Participants will gain insights into the responsibilities, challenges, and best practices associated with test management in SAP projects. Additionally, the webinar delves into the significance of heatmaps as a visual aid for identifying testing priorities, areas of risk, and resource allocation within SAP landscapes. Through this session, attendees can expect to enhance their understanding of test management principles while learning practical approaches to optimize testing processes in SAP environments using heatmap visualization techniques
What will you get from this session?
1. Insights into SAP testing best practices
2. Heatmap utilization for testing
3. Optimization of testing processes
4. Demo
Topics covered:
Execution from the test manager
Orchestrator execution result
Defect reporting
SAP heatmap example with demo
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Have you ever wanted a Ruby client API to communicate with your web service? Smithy is a protocol-agnostic language for defining services and SDKs. Smithy Ruby is an implementation of Smithy that generates a Ruby SDK using a Smithy model. In this talk, we will explore Smithy and Smithy Ruby to learn how to generate custom feature-rich SDKs that can communicate with any web service, such as a Rails JSON API.
Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...

In today's fast-changing business world, Companies that adapt and embrace new ideas often need help to keep up with the competition. However, fostering a culture of innovation takes much work. It takes vision, leadership and willingness to take risks in the right proportion. Sachin Dev Duggal, co-founder of Builder.ai, has perfected the art of this balance, creating a company culture where creativity and growth are nurtured at each stage.
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

The publishing industry has been selling digital audiobooks and ebooks for over a decade and has found its groove. What’s changed? What has stayed the same? Where do we go from here? Join a group of leading sales peers from across the industry for a conversation about the lessons learned since the popularization of digital books, best practices, digital book supply chain management, and more.
Link to video recording: https://bnctechforum.ca/sessions/selling-digital-books-in-2024-insights-from-industry-leaders/
Presented by BookNet Canada on May 28, 2024, with support from the Department of Canadian Heritage.
Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality

In this insightful webinar, Inflectra explores how artificial intelligence (AI) is transforming software development and testing. Discover how AI-powered tools are revolutionizing every stage of the software development lifecycle (SDLC), from design and prototyping to testing, deployment, and monitoring.
Learn about:
• The Future of Testing: How AI is shifting testing towards verification, analysis, and higher-level skills, while reducing repetitive tasks.
• Test Automation: How AI-powered test case generation, optimization, and self-healing tests are making testing more efficient and effective.
• Visual Testing: Explore the emerging capabilities of AI in visual testing and how it's set to revolutionize UI verification.
• Inflectra's AI Solutions: See demonstrations of Inflectra's cutting-edge AI tools like the ChatGPT plugin and Azure Open AI platform, designed to streamline your testing process.
Whether you're a developer, tester, or QA professional, this webinar will give you valuable insights into how AI is shaping the future of software delivery.
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovation With Your Product by VP of Product Design, Warner Music Group
How world-class product teams are winning in the AI era by CEO and Founder, P...

How world-class product teams are winning in the AI era by CEO and Founder, Product School
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
Recently uploaded (20)
Knowledge engineering: from people to machines and back

Knowledge engineering: from people to machines and back
Elevating Tactical DDD Patterns Through Object Calisthenics

Elevating Tactical DDD Patterns Through Object Calisthenics
Key Trends Shaping the Future of Infrastructure.pdf

Key Trends Shaping the Future of Infrastructure.pdf
Essentials of Automations: Optimizing FME Workflows with Parameters

Essentials of Automations: Optimizing FME Workflows with Parameters
Accelerate your Kubernetes clusters with Varnish Caching

Accelerate your Kubernetes clusters with Varnish Caching
From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP...

From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP...
Connector Corner: Automate dynamic content and events by pushing a button

Connector Corner: Automate dynamic content and events by pushing a button
Epistemic Interaction - tuning interfaces to provide information for AI support

Epistemic Interaction - tuning interfaces to provide information for AI support
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...
UiPath Test Automation using UiPath Test Suite series, part 4

UiPath Test Automation using UiPath Test Suite series, part 4
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Generating a custom Ruby SDK for your web service or Rails API using Smithy
Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...

Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

Transcript: Selling digital books in 2024: Insights from industry leaders - T...
Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality

Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...
How world-class product teams are winning in the AI era by CEO and Founder, P...

How world-class product teams are winning in the AI era by CEO and Founder, P...
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
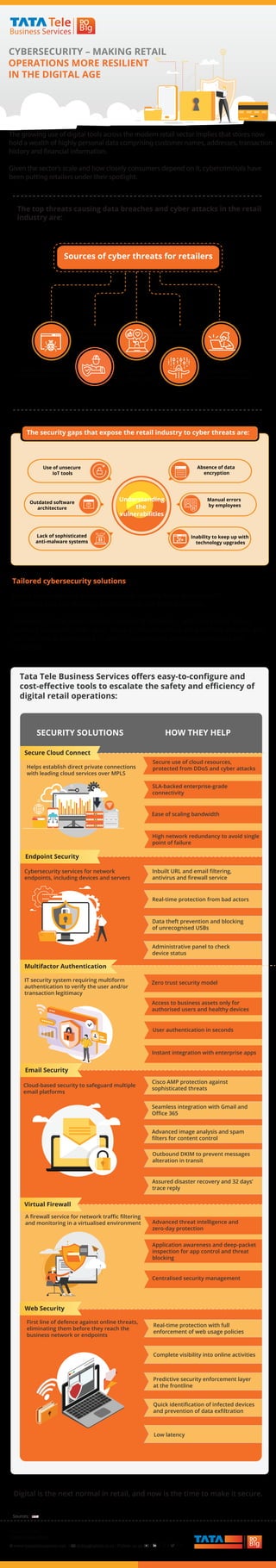
Why cyber security is a priority for your retail business
- 1. Major marketplaces and retail brands usually have dedicated IT administrators to manage cybersecurity for their business. However, for the small, locally operating retailers – who use public cloud services to launch their apps, store critical business data in their devices and do not have a specialised IT team – customised cybersecurity tools are essential. Sources: #TimeToDoBig 1800-266-1800 www.tatatelebusiness.com | dobig@tatatel.co.in | Follow us on IT security system requiring multiform authentication to verify the user and/or transaction legitimacy A firewall service for network traffic filtering and monitoring in a virtualised environment Digital is the next normal in retail, and now is the time to make it secure. Information available on social media Malware infestation by phishing/hacking Malware infestation by 3rd party/own systems Insider's job with malicious intent Usage of advanced technologies such as ML by hackers CYBERSECURITY – MAKING RETAIL OPERATIONS MORE RESILIENT IN THE DIGITAL AGE The growing use of digital tools across the modern retail sector implies that stores now hold a wealth of highly personal data comprising customer names, addresses, transaction history and financial information. Given the sector’s scale and how closely consumers depend on it, cybercriminals have been putting retailers under their spotlight. The top threats causing data breaches and cyber attacks in the retail industry are: The security gaps that expose the retail industry to cyber threats are: Use of unsecure IoT tools Outdated software architecture Absence of data encryption Tailored cybersecurity solutions Tata Tele Business Services offers easy-to-configure and cost-effective tools to escalate the safety and efficiency of digital retail operations: Cybersecurity services for network endpoints, including devices and servers Helps establish direct private connections with leading cloud services over MPLS Endpoint Security Multifactor Authentication Cloud-based security to safeguard multiple email platforms Email Security Virtual Firewall First line of defence against online threats, eliminating them before they reach the business network or endpoints Web Security Understanding the vulnerabilities Lack of sophisticated anti-malware systems Manual errors by employees Inability to keep up with technology upgrades Sources of cyber threats for retailers SECURITY SOLUTIONS HOW THEY HELP Secure Cloud Connect Secure use of cloud resources, protected from DDoS and cyber attacks SLA-backed enterprise-grade connectivity Ease of scaling bandwidth High network redundancy to avoid single point of failure Inbuilt URL and email filtering, antivirus and firewall service Real-time protection from bad actors Data theft prevention and blocking of unrecognised USBs Administrative panel to check device status Zero trust security model Access to business assets only for authorised users and healthy devices User authentication in seconds Instant integration with enterprise apps Cisco AMP protection against sophisticated threats Seamless integration with Gmail and Office 365 Advanced image analysis and spam filters for content control Outbound DKIM to prevent messages alteration in transit Assured disaster recovery and 32 days’ trace reply Advanced threat intelligence and zero-day protection Application awareness and deep-packet inspection for app control and threat blocking Centralised security management Real-time protection with full enforcement of web usage policies Complete visibility into online activities Predictive security enforcement layer at the frontline Quick identification of infected devices and prevention of data exfiltration Low latency
