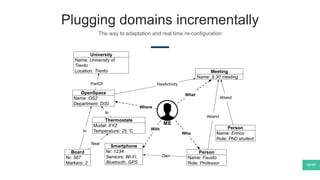
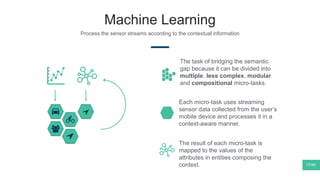
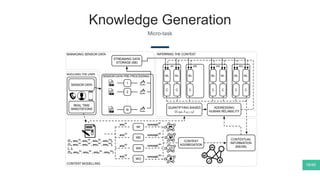
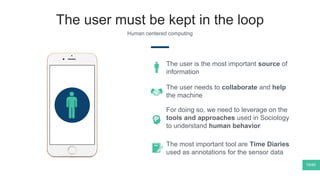
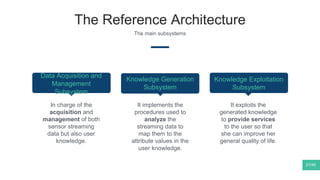
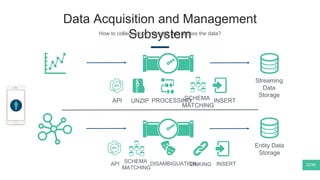
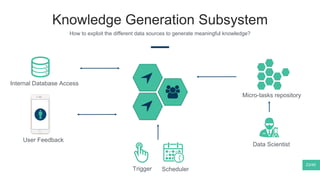
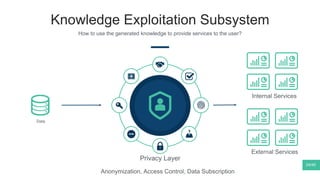
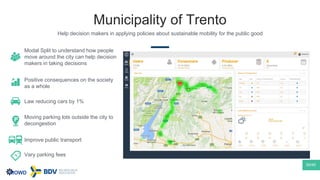
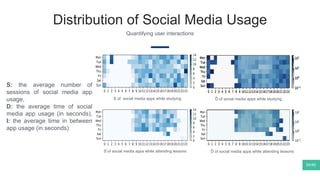
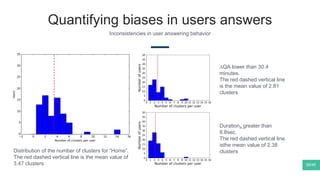
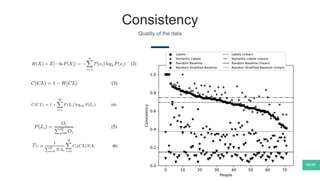
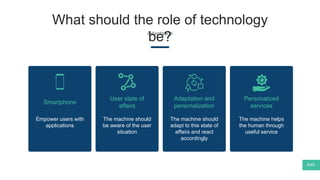
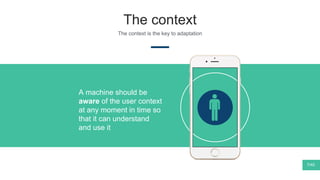
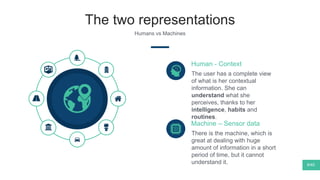
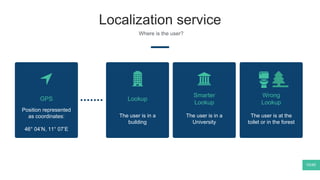
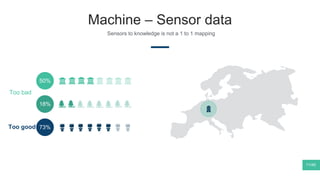
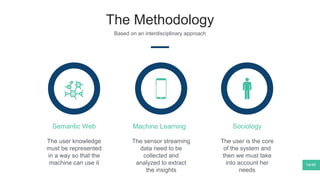
The document summarizes Mattia Zeni's thesis work on bridging sensor data streams from smartphones with human contextual knowledge to power personalized services. It describes a methodology using semantic web ontologies to represent user knowledge, machine learning to analyze sensor data and extract insights, and involving users through time diary annotations. A reference architecture is proposed with subsystems for data management, knowledge generation, and service exploitation. The work has been applied to help municipalities with transportation planning and to analyze university students' academic performance based on mobile app usage data.




![Semantics
Represent the user knowledge
Ontologies provide structured data that are
general, compositional, reusable and
incremental allowing us to operate in open
domain.
What are the advantages?
We modelled the user and the world using
the Entity Centric approach.
How can it be used?
A set of representational primitives with
which to model a domain of knowledge
[Gruber, 1993]
What is an ontology?
[Gruber,1993] “A translation approach to portable ontology specifications”. Knowledge acquisition, 5(2), 199-220. 15/40](https://image.slidesharecdn.com/presentation-180202104840/85/Bridging-Sensor-Data-Streams-and-Human-Knowledge-15-320.jpg)