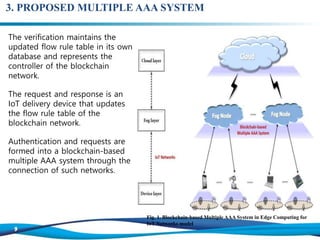
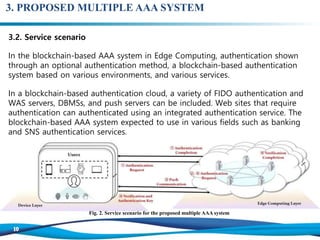
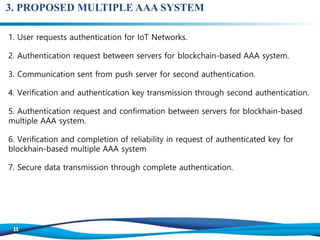
The document discusses the importance of edge computing and blockchain technology in enhancing security for Internet of Things (IoT) networks, proposing a blockchain-based multiple authentication, authorization, and accounting (AAA) system. It emphasizes the necessity for secure data processing due to the rise of IoT devices and outlines a model that includes cloud, fog, and device layers for effective credential management. The proposed system addresses current challenges in centralized data management by introducing a decentralized approach that improves resilience and security.