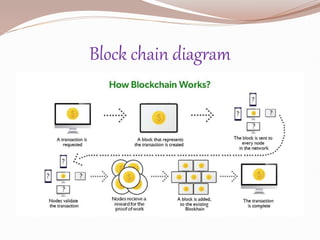
The document provides an overview of domain names and blockchain technology. It explains that a domain name corresponds to an IP address for accessing websites, while blockchain is described as a decentralized digital ledger for recording transactions. Key benefits of blockchain include increased security, transparency, and reduced costs, with applications in areas like money transfer, IoT, and healthcare.