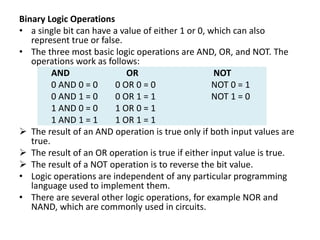
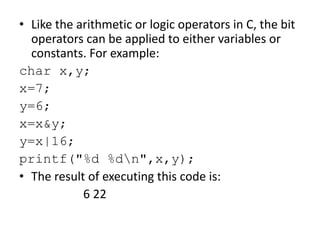
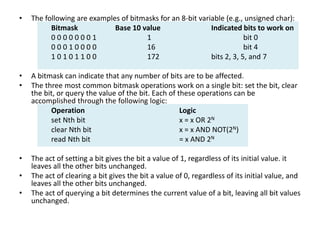
Bitwise operations allow manipulating individual bits within binary representations of data. Common bitwise operations include AND, OR, NOT, and shifting bits left or right. Bitmasks are used to isolate specific bits for setting, clearing, or reading their values. Bitwise logic is applied extensively in areas like graphics, embedded systems, data structures, and networking where individual bits need to be manipulated.