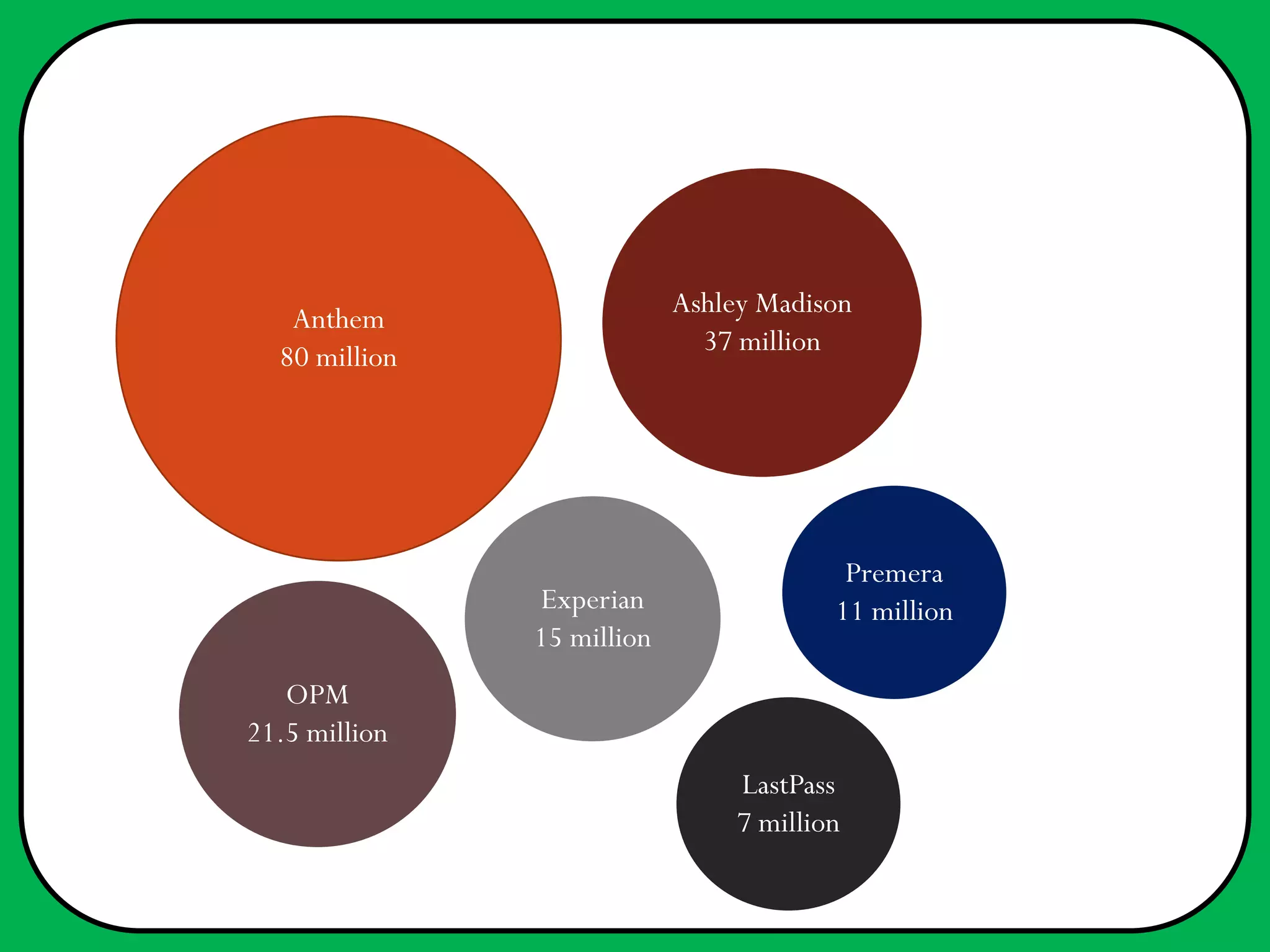
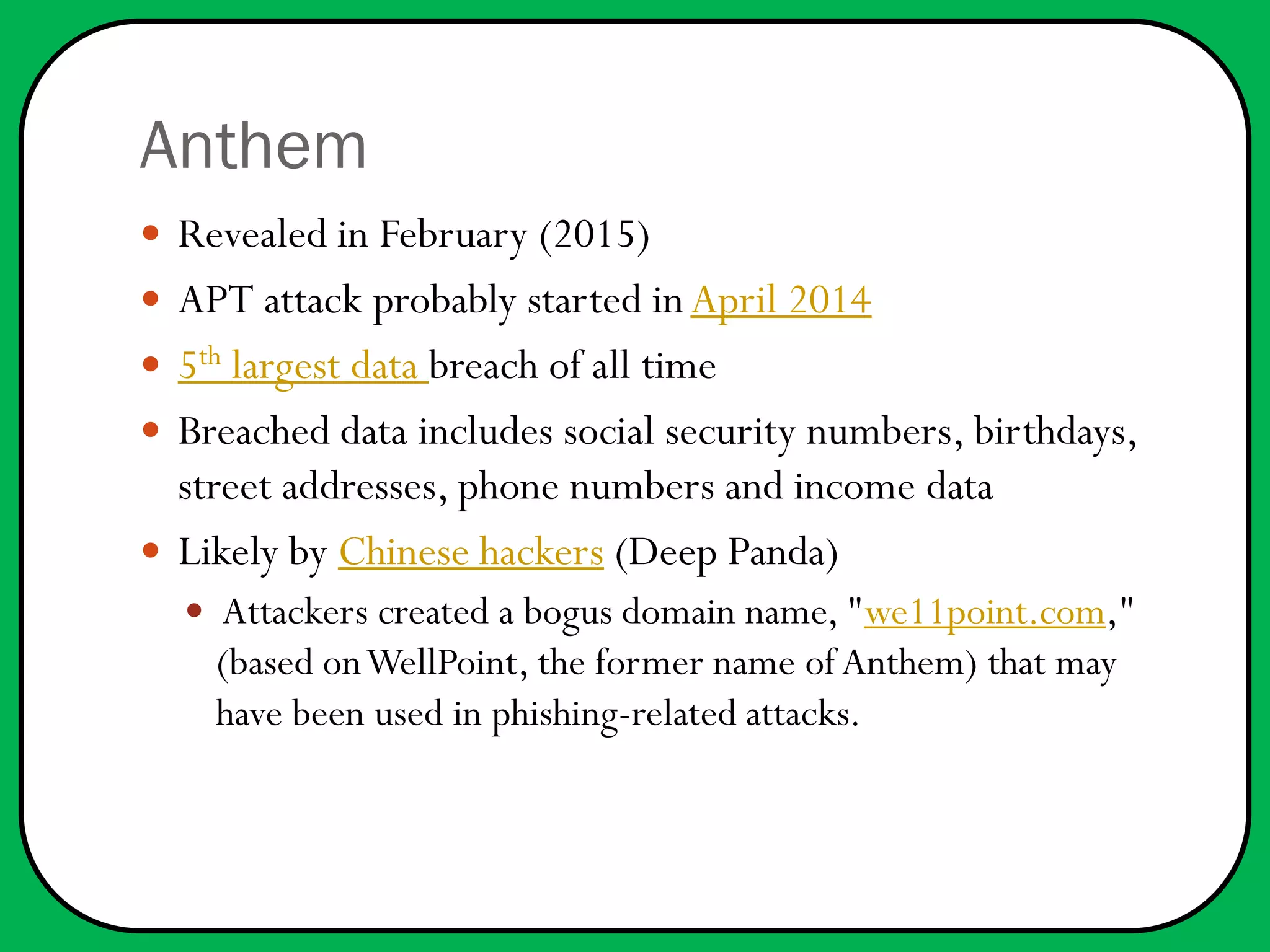
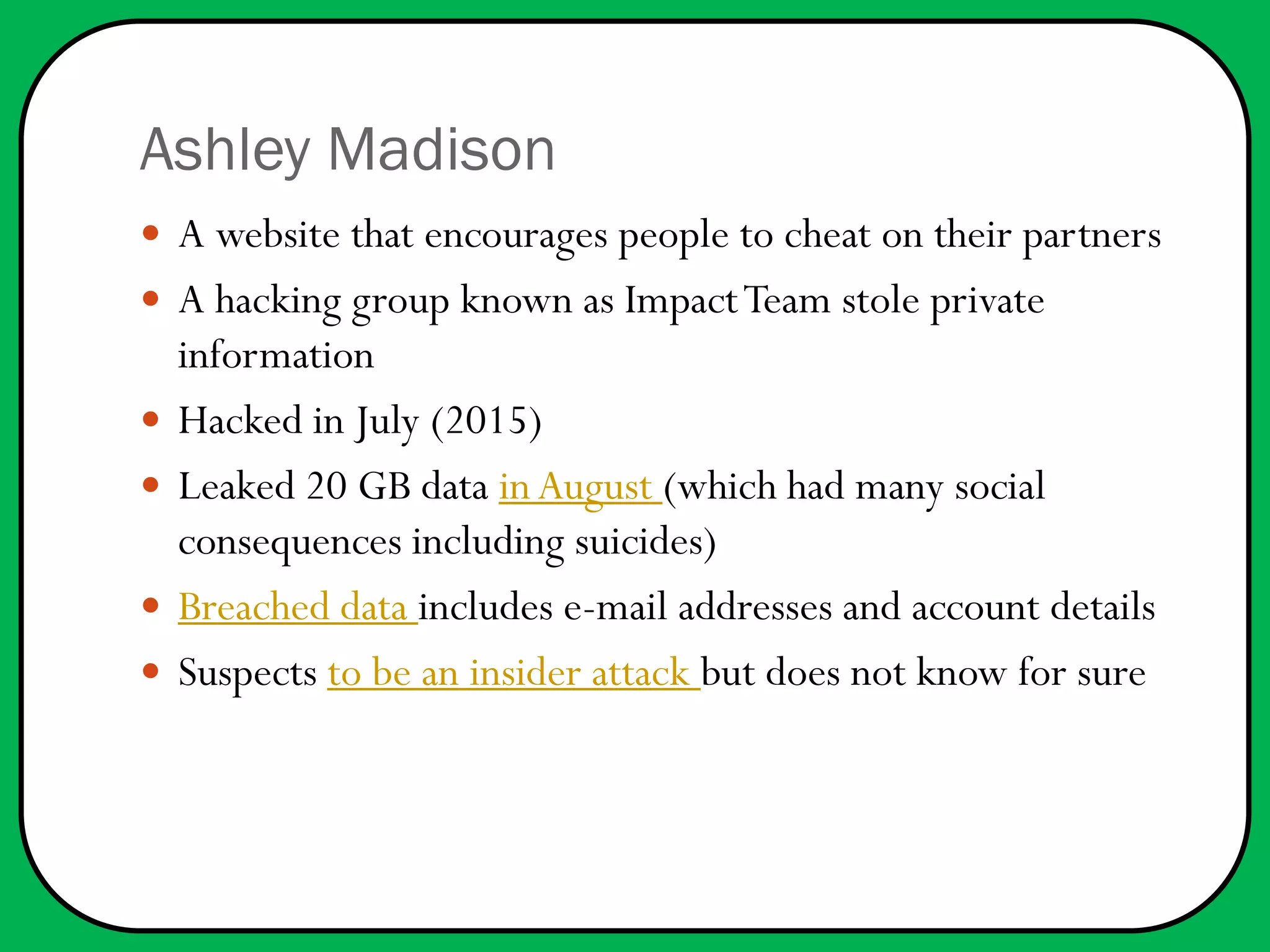
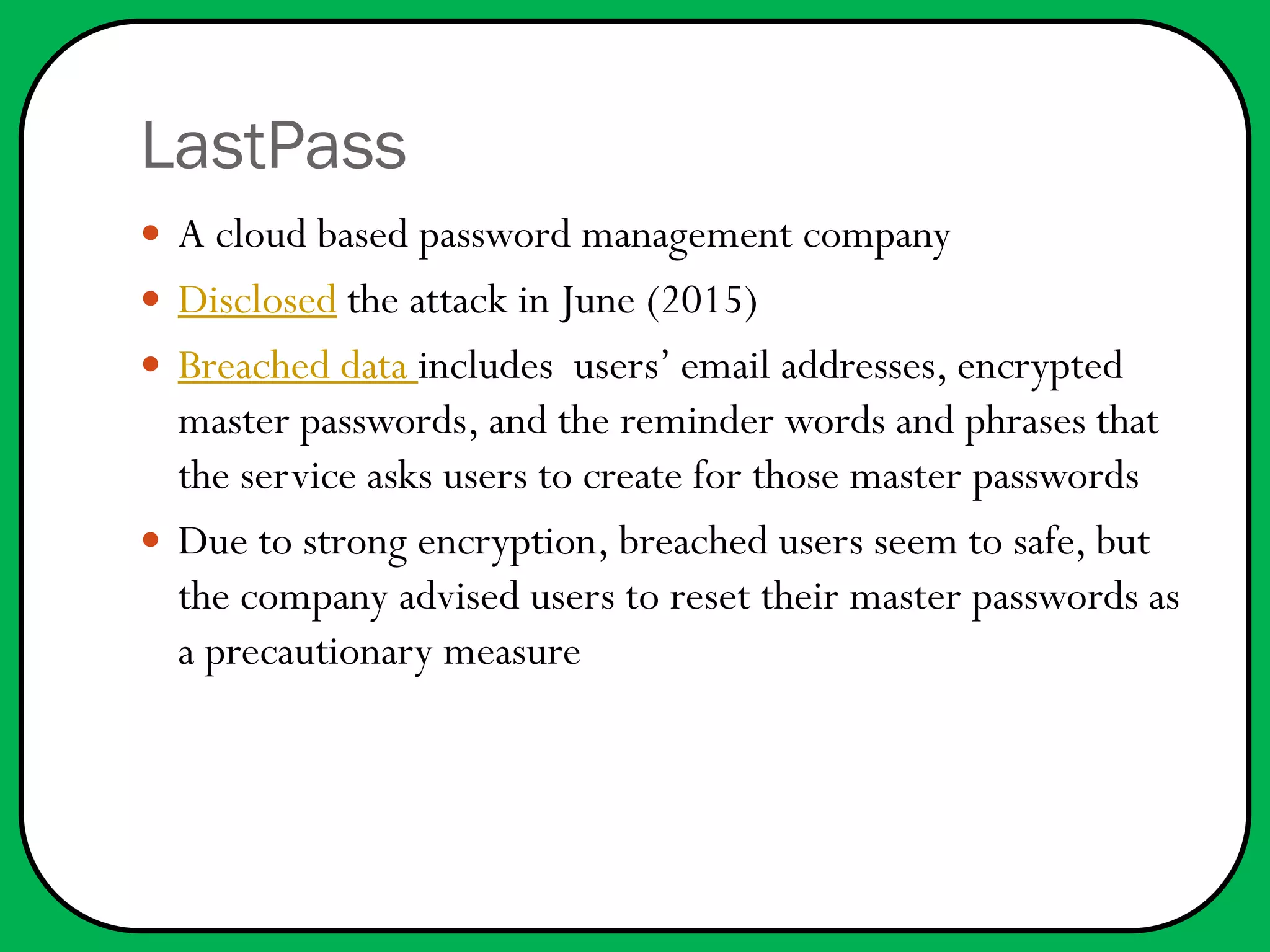
In 2015, several significant data breaches occurred, affecting millions, including Anthem (80 million records), Ashley Madison (37 million), and the U.S. Office of Personnel Management (21.5 million). Most breaches involved sensitive personal information and were attributed to various cybercriminals, including suspected state-sponsored hackers. Recommendations for improved security include better encryption, detection technologies, and heeding warnings about potential vulnerabilities.