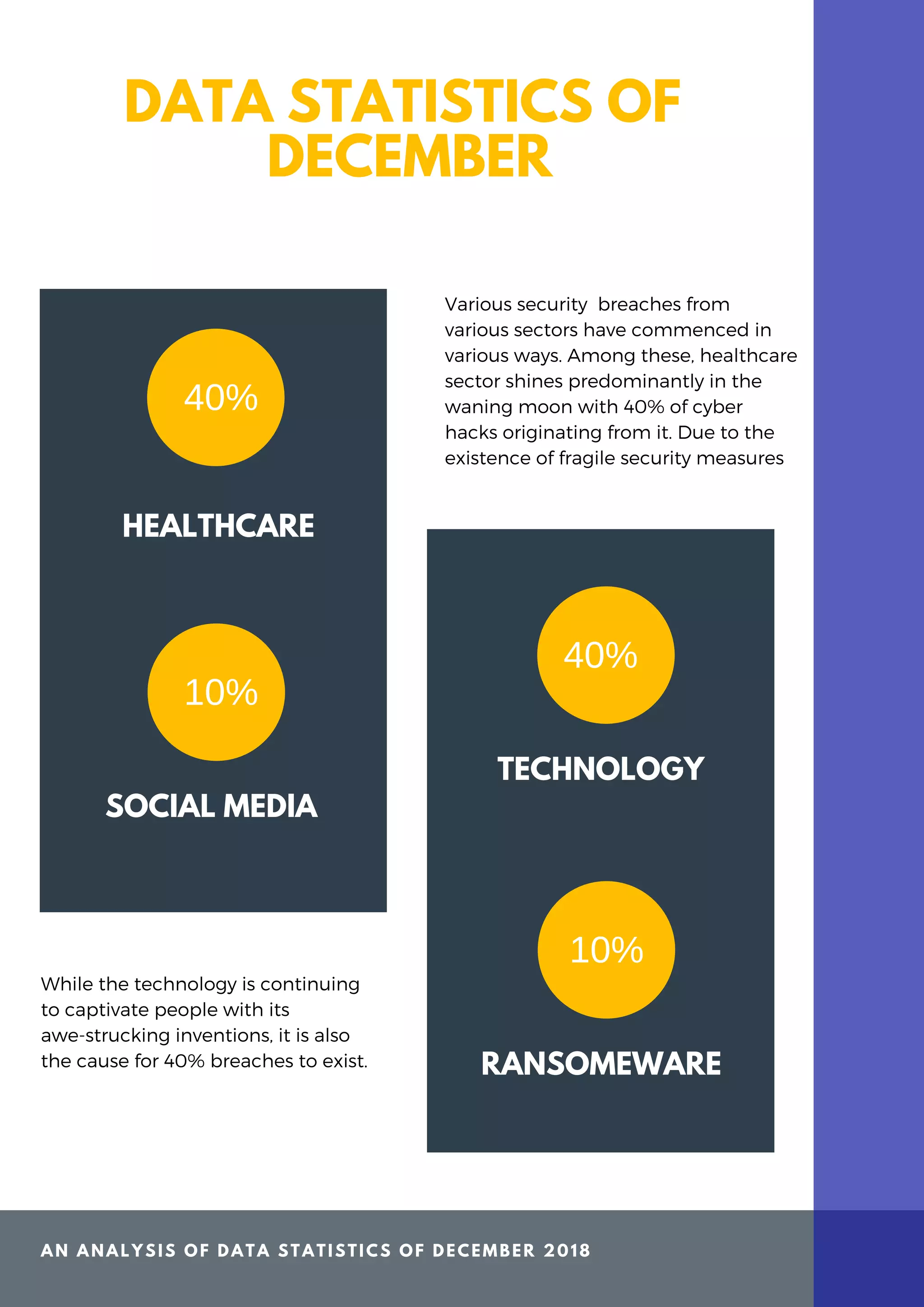
The ThreatSploit January 2019 report highlights significant cybersecurity breaches, particularly in the healthcare sector, which accounts for 40% of attacks. Key incidents include a ransomware attack impacting over 16,000 patient records and various breaches resulting from third-party vendor hacks and email errors, emphasizing the urgent need for improved cybersecurity measures. The report concludes that despite vulnerabilities, healthcare organizations have not sufficiently invested in security protocols, leaving them exposed to cyber threats.