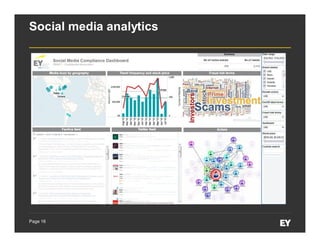
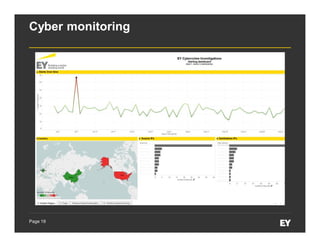
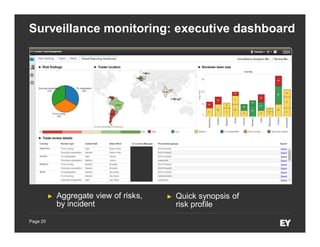
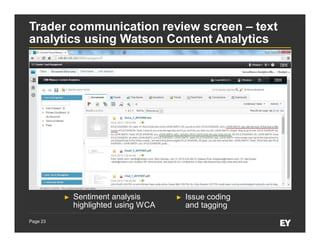
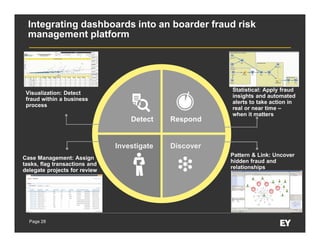
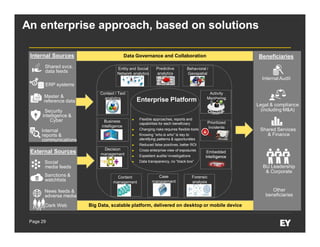
This document discusses forensic data analytics and its use in fraud risk management. It begins with an agenda on key analytics trends, "big data thinking," and examples of anti-fraud use cases like employee and vendor transaction risk scoring. The document then covers the forensic data analytics landscape, increasing regulatory focus on advanced monitoring, and how analytics can help improve compliance efficiency. It discusses challenges of forensic data analytics and integrating visualization into risk management platforms. The document concludes with success factors for deploying forensic data analytics like focusing on priority projects and gaining leadership support.