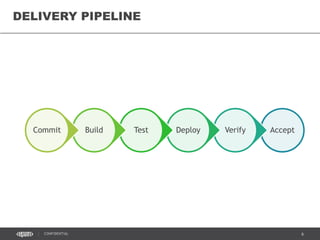
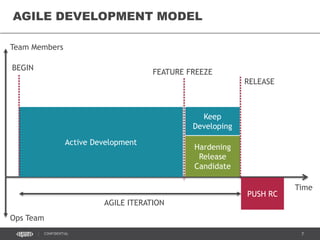
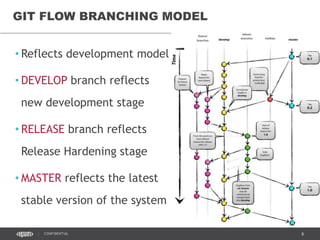
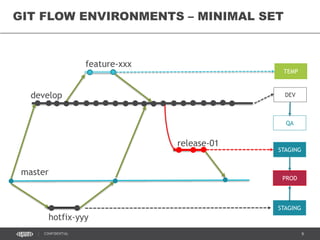
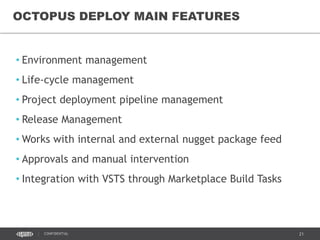
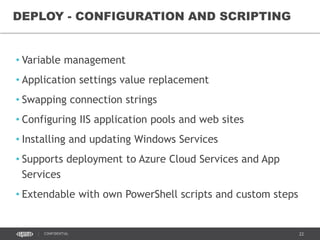
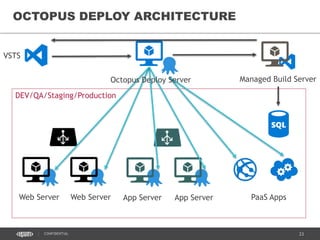
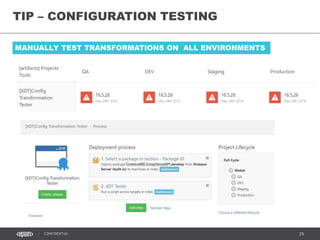
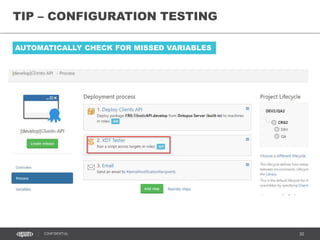
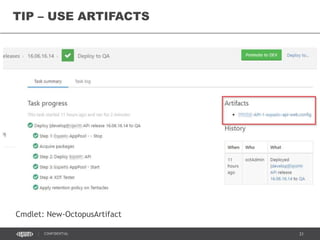
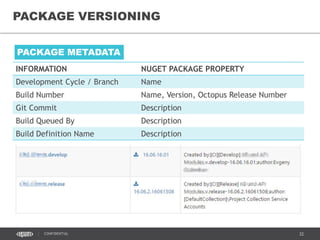
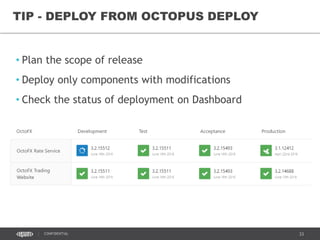
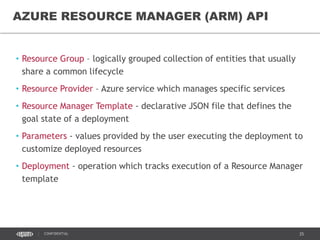
This document discusses continuous delivery practices using Visual Studio Team Services (VSTS), Git Flow branching model, Octopus Deploy, and Azure Resource Manager (ARM) for enterprise environments. It defines continuous delivery and release management, and describes how to implement a Git Flow branching model and delivery pipeline in VSTS. It also provides an overview of using Octopus Deploy for release management and deployment, ARM for infrastructure provisioning, and Role-Based Access Control (RBAC) for user permissions. Key recommendations include using VSTS for continuous integration, Octopus Deploy for releases, ARM templates for environments, and RBAC for administration.












![38CONFIDENTIAL
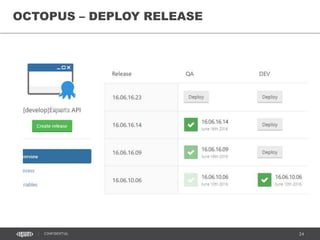
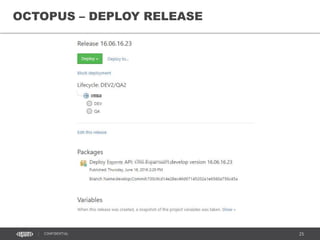
[TOPIC]
xxxD
xxxOps
xxxQ xxxS xxxP
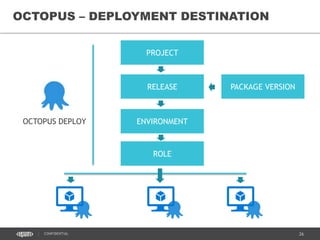
• Resource Group (RG) contains all resources which
belong to particular environment.
• RG name starts with common prefix and the letter,
which identifies the environment purpose: Dev, Qa,
Staging and Production
• RG name is included into the billing report and used to
track costs.
RESOURCE GROUPS AS CONTAINERS](https://image.slidesharecdn.com/azuredayreleasemanagement-160627220538/85/AzureDay-Kyiv-2016-Release-Management-35-320.jpg)
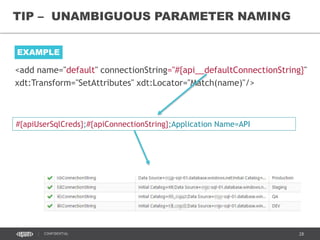
![39CONFIDENTIAL
network-01 (v2)
[TOPIC]
RESOURCE GROUP
front-subnet-01
back-subnet-01
Gateway Subnet
network-01 (Classic)
Gateway Subnet
Use Network Security Groups to limit
ports exposure on the subnet layer.
FE subnet network security Group:
Inbound Connections:
- Allow all HTTP and HTTPS from any
source
- Allow all from AD network address
space
- Allow/Block RDP connections from
EPAM and NYC offices
- Allow Octopus port from Virtual
Network
BE subnet network security Group:
Inbound Connections:
- Allow application ports from VNet
- Allow all from AD network address
space
- Allow/Block RDP connections from
EPAM and NYC offices
- Allow Octopus port from Virtual
Network
NETWORK SECURITY GROUPS](https://image.slidesharecdn.com/azuredayreleasemanagement-160627220538/85/AzureDay-Kyiv-2016-Release-Management-36-320.jpg)