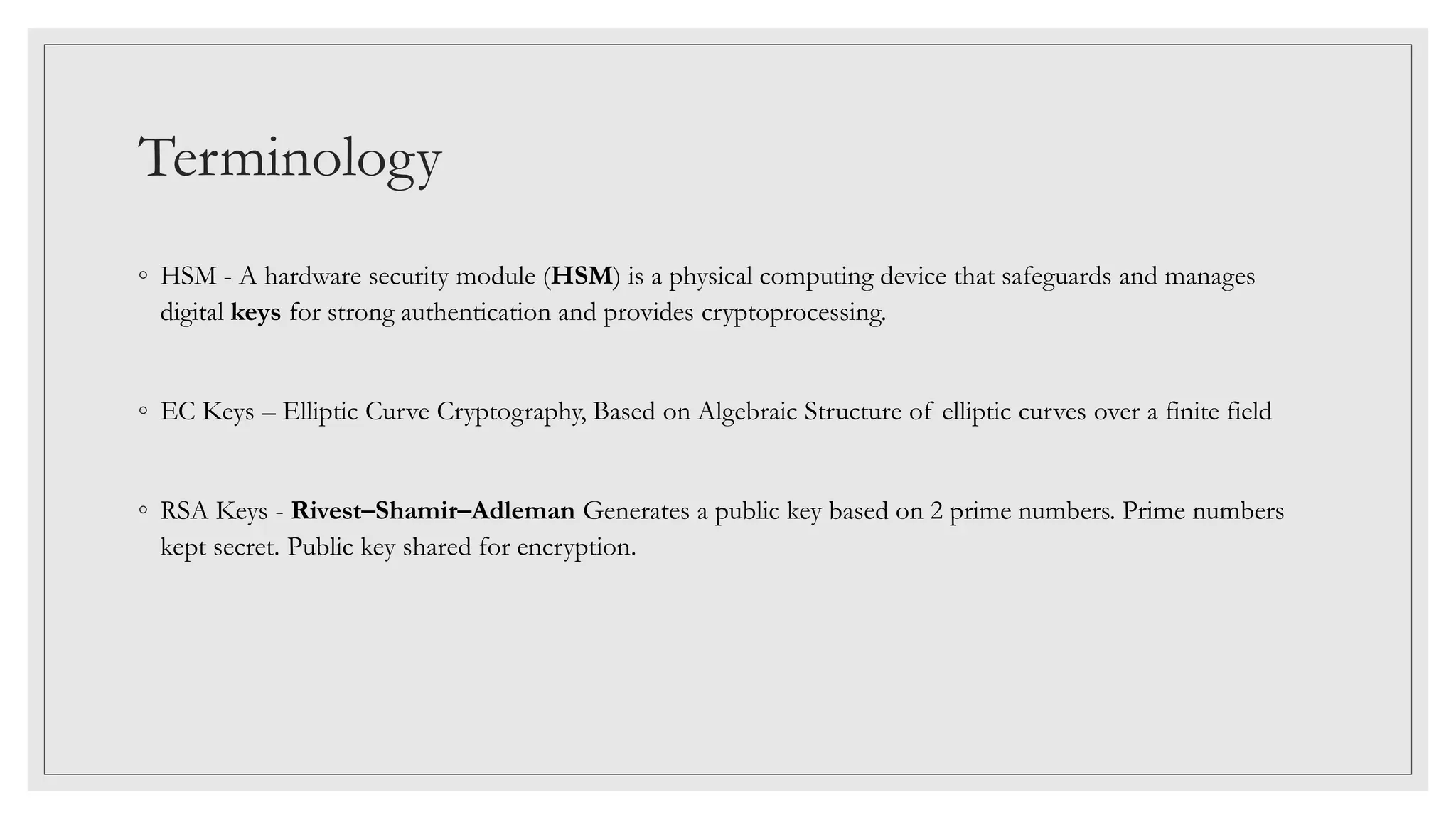
This document discusses Azure Key Vault, which allows centralizing application secrets and securing storage of keys and secrets. It can simplify administration by centralizing configurations and allowing monitoring of access and usage. The document demonstrates how to create an Azure Key Vault and connect to it from Visual Studio using managed identities. It also discusses how Azure Key Vault can integrate with app settings and be called externally with a token.