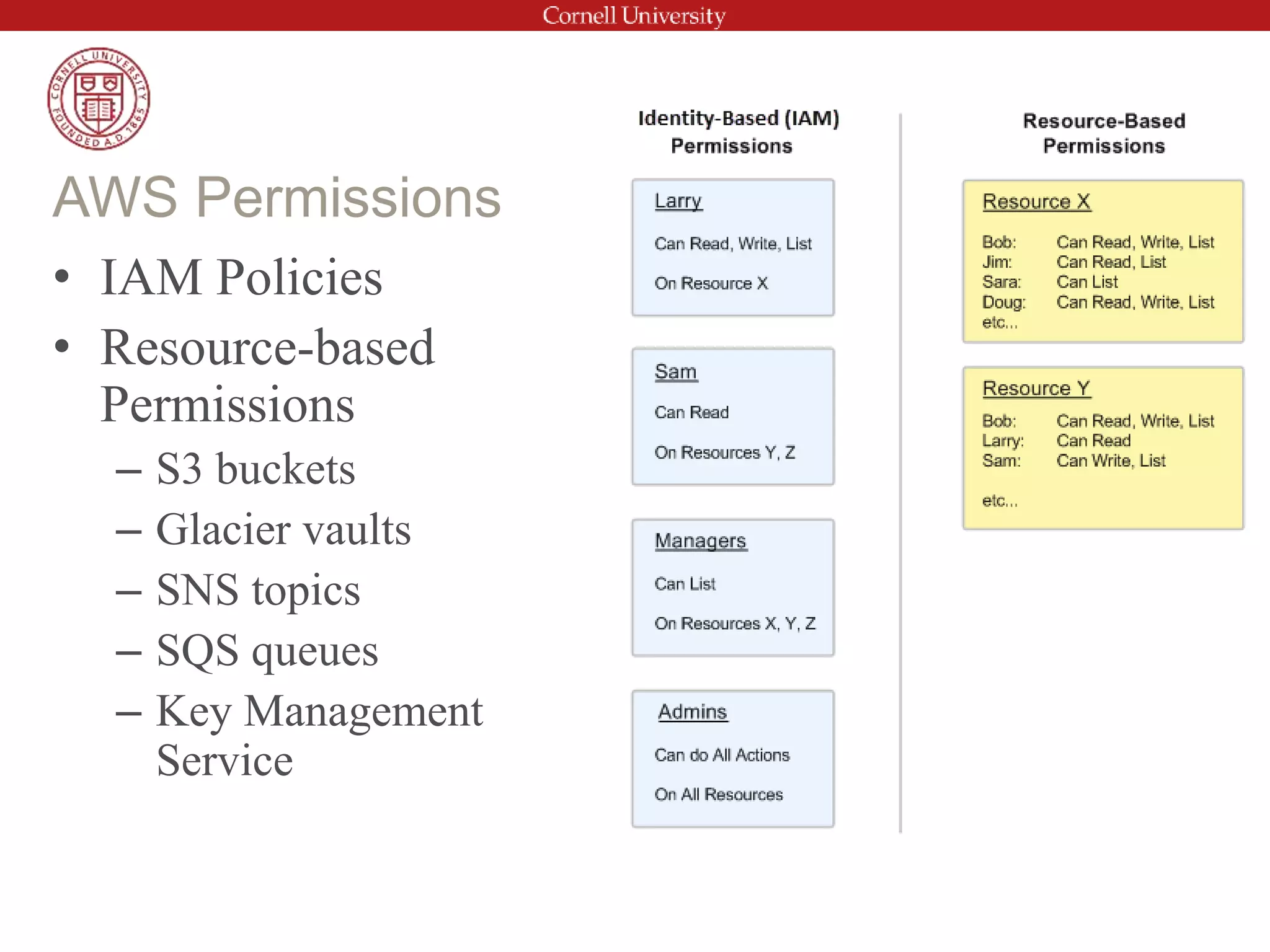
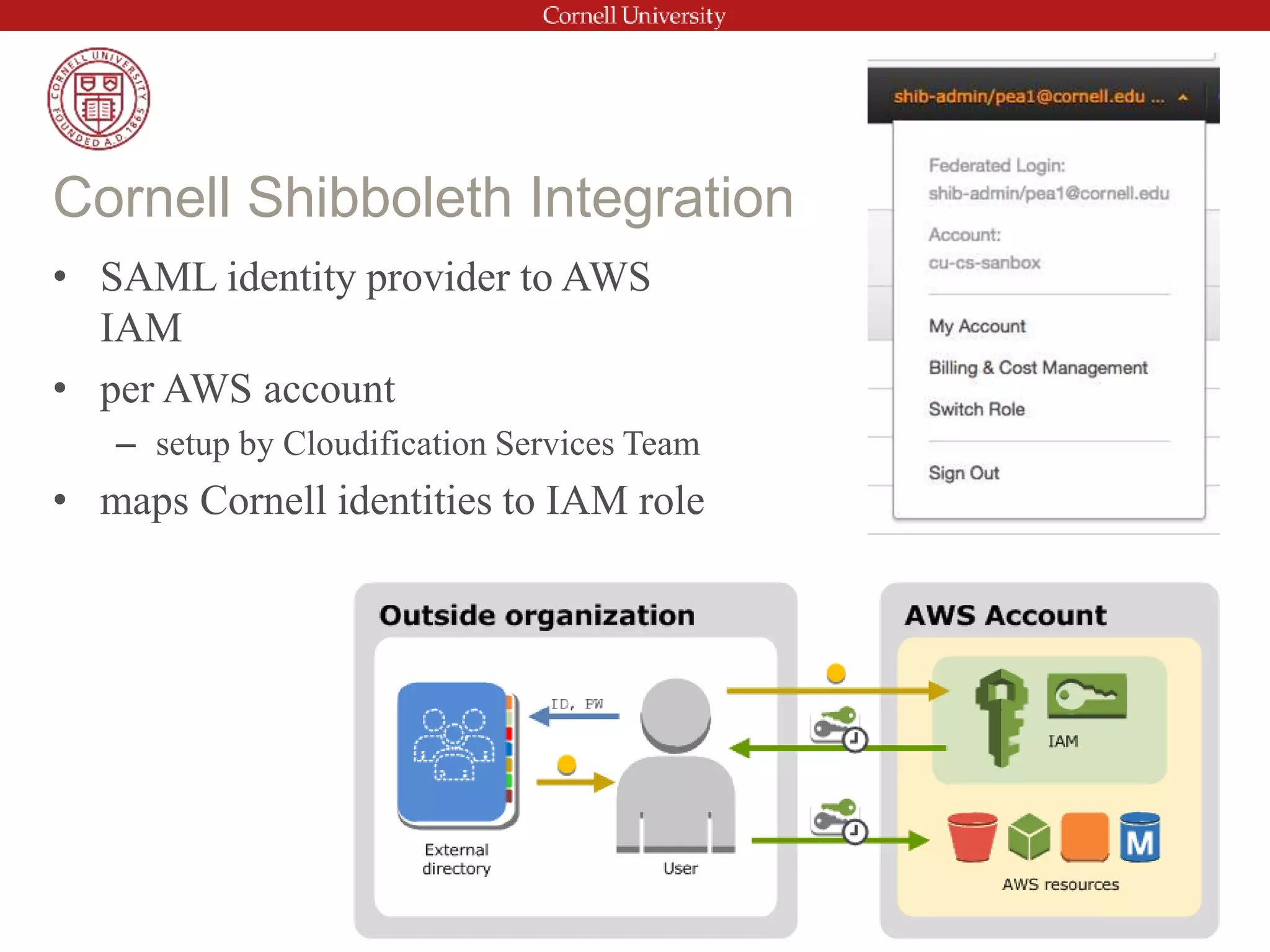
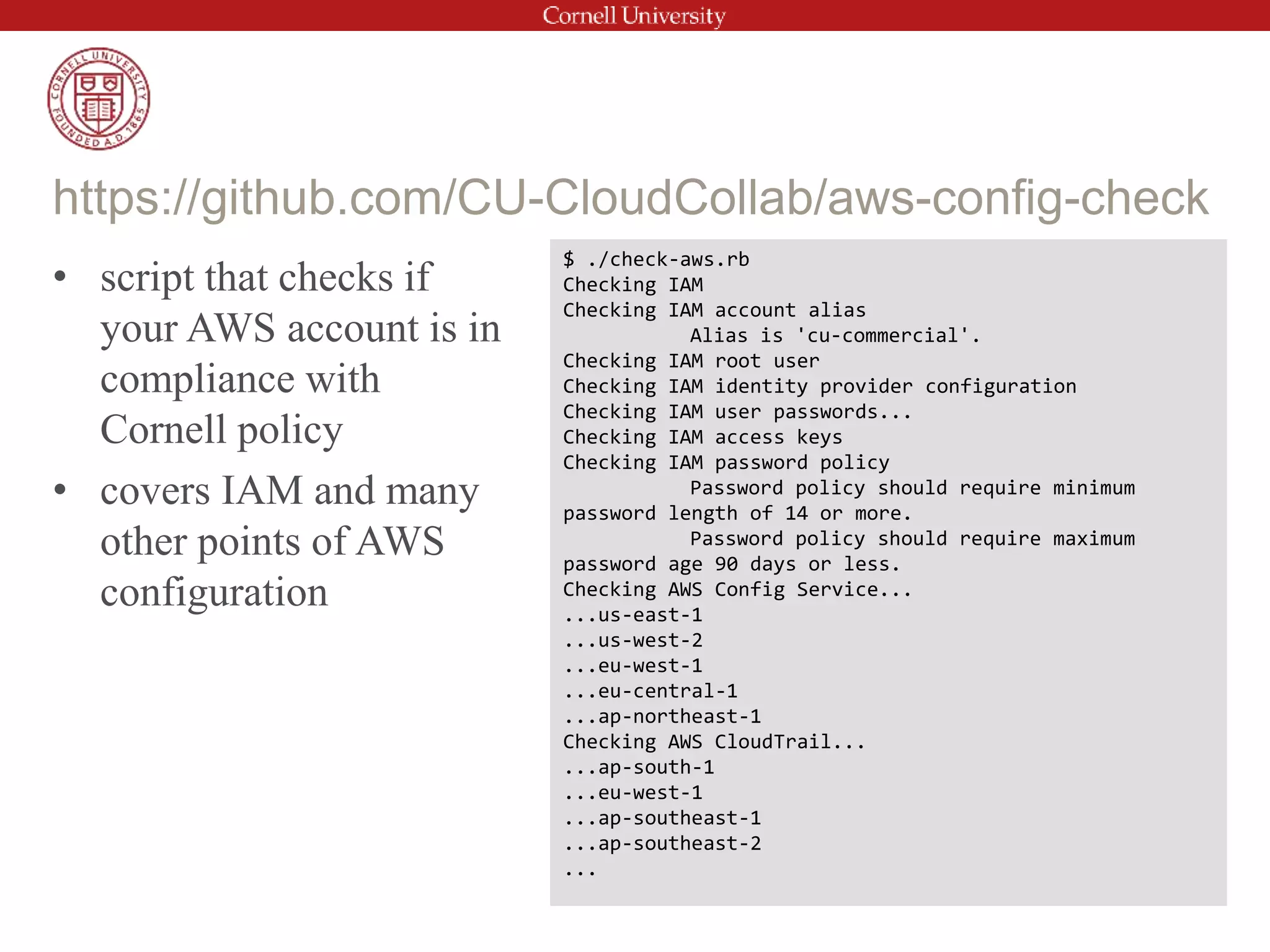
This document provides an introduction to AWS Identity and Access Management (IAM). It discusses IAM concepts such as users, groups, policies and roles. It also covers best practices for IAM configuration including using groups to manage permissions, strong password policies, multi-factor authentication, and minimizing the use of the root account. The document outlines Cornell's Shibboleth integration for single sign-on to AWS and notes additional security considerations outside of IAM.






![• set of permissions to
be granted or denied
• JSON documents
• can be assigned
directly to IAM users
IAM Concepts – Policies
{
"Version": "2012-10-17",
"Statement": [ {
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "arn:aws:s3:::*"
}, {
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetBucketLocation"],
"Resource":
"arn:aws:s3:::EXAMPLE-BUCKET-NAME”
}, {
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:GetObject",
"s3:DeleteObject" ],
"Resource":
"arn:aws:s3:::EXAMPLE-BUCKET-NAME/*"
} ] }](https://image.slidesharecdn.com/aws-iam-intro-2016-08-03-230331145659-e1f59e70/75/AWS-IAM-intro-2016-08-03-pptx-8-2048.jpg)