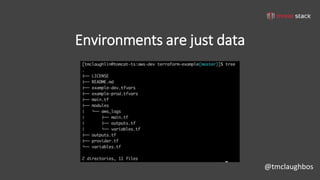
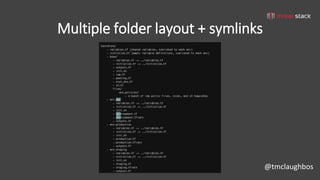
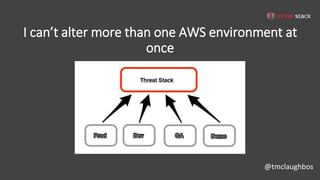
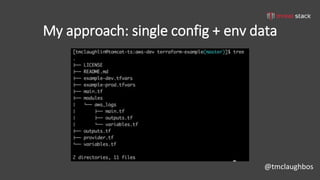
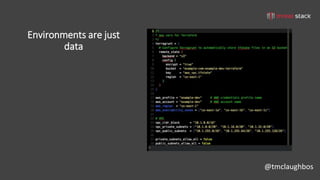
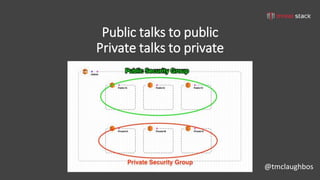
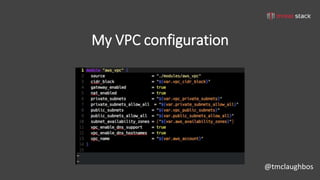
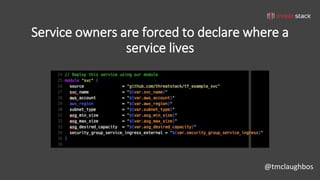
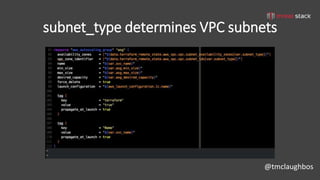
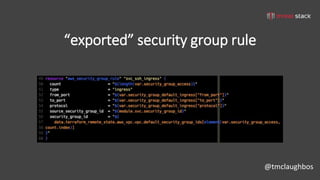
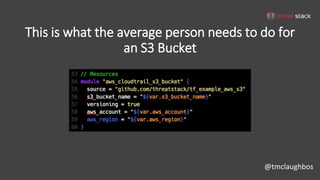
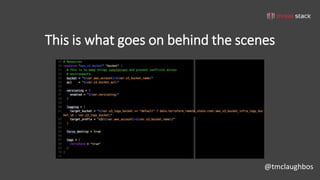
This document discusses security best practices for incorporating AWS security into Terraform configurations. It describes the speaker's background and approach to infrastructure as code which focuses on guardrails over gates, allowing freedom to fail while experimenting, and prioritizing getting something done over perfection. The speaker's Terraform design philosophy emphasizes modularity, reusability, and separating environments into single accounts to prevent lateral movement. Specific practices mentioned include network segmentation between public and private resources, using bastion hosts as the only publicly accessible instances, and enabling CloudTrail logging.