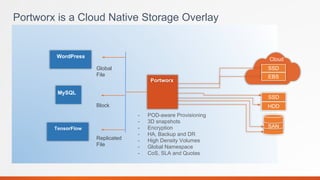
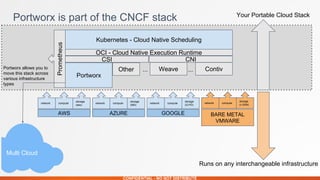
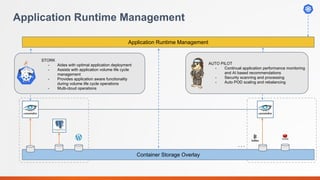
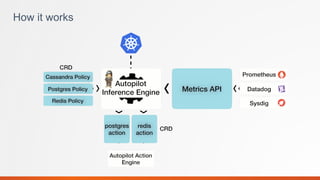
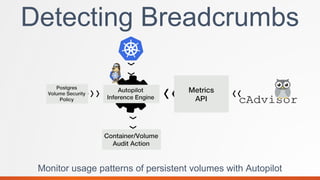
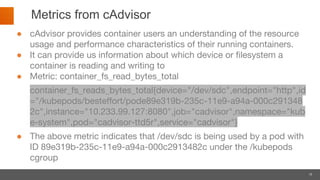
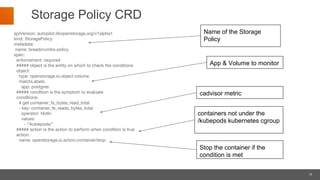
Portworx is a leading cloud-native storage solution optimized for large-scale deployments, providing features like high availability, multi-cloud support, and efficient resource management. It integrates tightly with Kubernetes, enabling automation and security features for containerized applications while offering tools for application runtime management monitoring. Autopilot enhances application performance and security management through a rule-based analytical engine that acts on defined metrics and conditions.