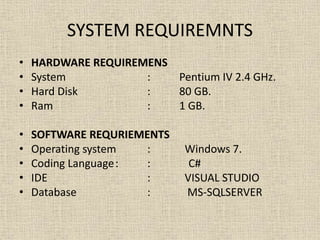
This document discusses an attribute-based storage system that supports secure deduplication of encrypted data in the cloud. It aims to allow data providers to outsource encrypted data to the cloud while maintaining confidentiality. The system uses a hybrid cloud setting where a private cloud detects duplicates and a public cloud manages storage. This allows confidential data sharing through access policies rather than key sharing, and provides semantic security for data confidentiality. Existing systems only provide weaker security. The system requirements for hardware include a Pentium IV 2.4 GHz processor and 1 GB RAM, and for software include Windows 7, C# coding, Visual Studio IDE, and MS SQL Server database.