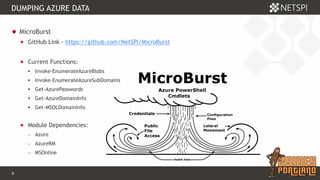
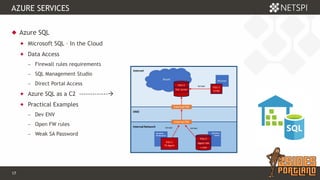
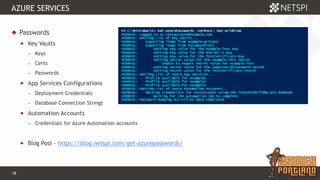
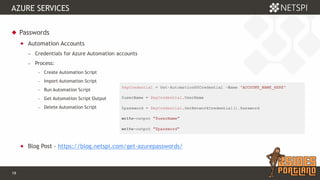
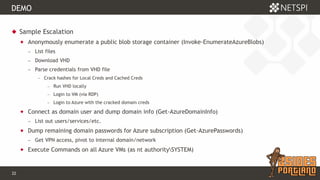
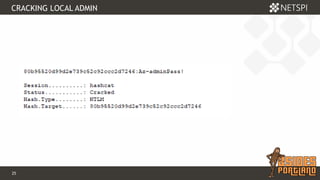
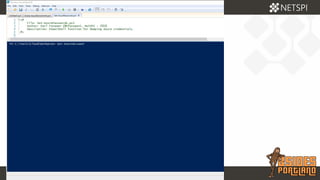
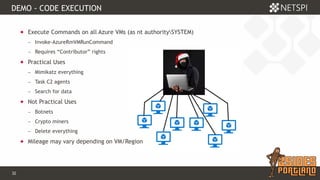
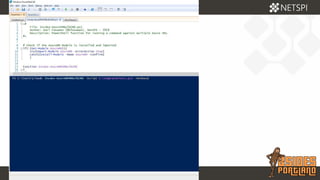
The document discusses techniques for extracting data from Azure environments using PowerShell, highlighting the importance of Azure management security. It outlines various Azure services, tools like Microburst, and demonstrates methods for unauthorized access and escalation. Recommendations for securing Azure accounts include limiting management access, addressing misconfigurations, and implementing multi-factor authentication.