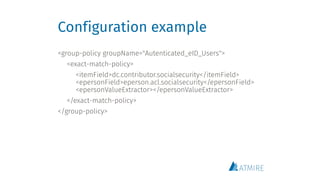
The document discusses metadata-based access control strategies for managing sensitive data within open repositories, emphasizing the importance of authorization groups and matching eperson characteristics to item metadata for access rights. It outlines both advantages, such as scalability and performance, and disadvantages, including the need for careful metadata editing and the risks associated with unauthorized access. Actionable takeaways include assessing risk severity based on probability and impact, with available code for implementation on GitHub.