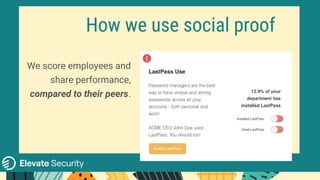
This document discusses using behavioral science techniques to improve cybersecurity compliance. It explains that people don't lack understanding but lack motivation, so motivating people is key. Three techniques are discussed: nudging to subtly influence decisions, social proof to highlight what the majority does, and positive reinforcement to encourage desired behaviors. The document provides examples of how these techniques can be applied to cybersecurity, such as frequent personalized communications, sharing anonymous performance comparisons, and rewarding strong performers with badges and time off.