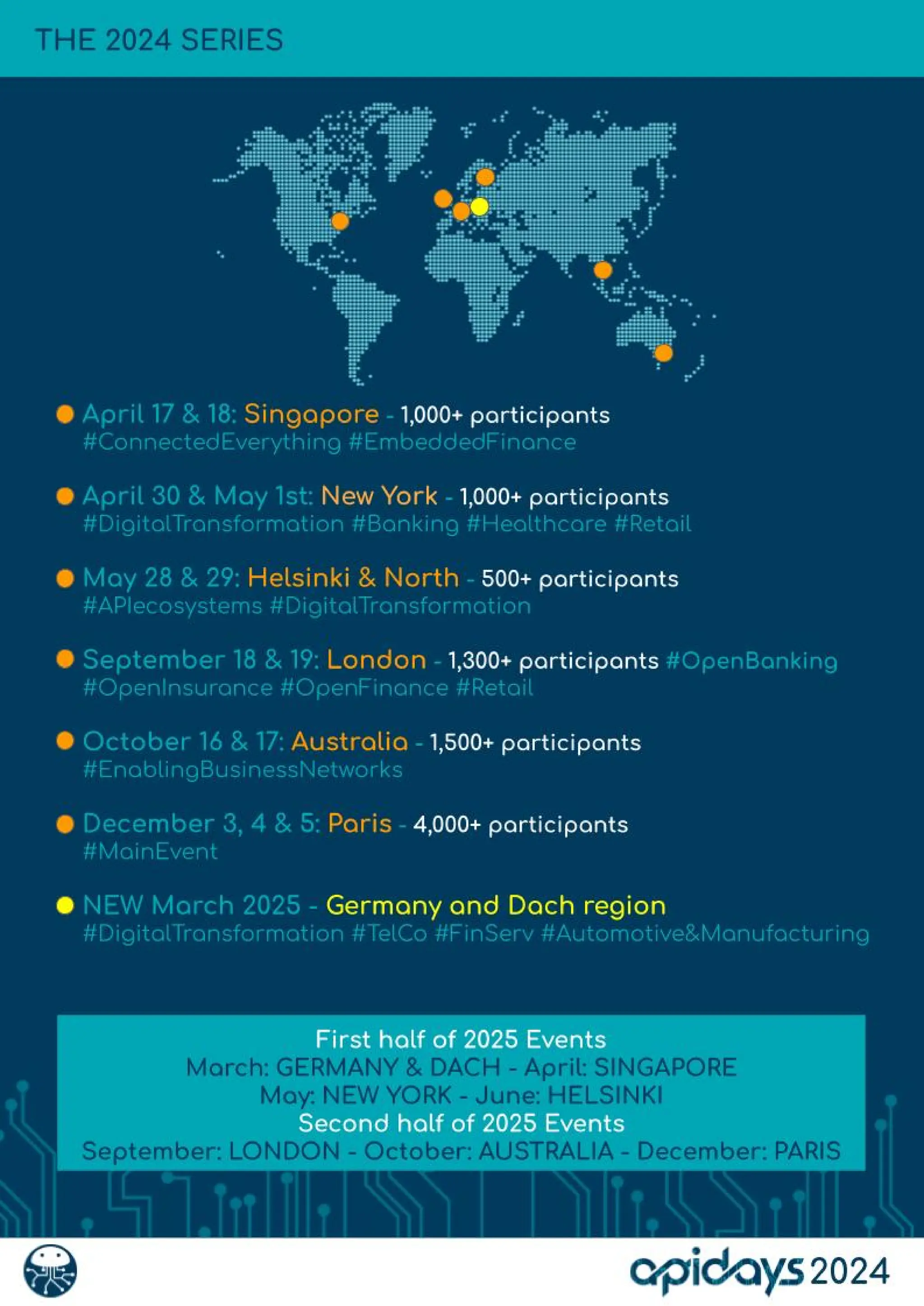
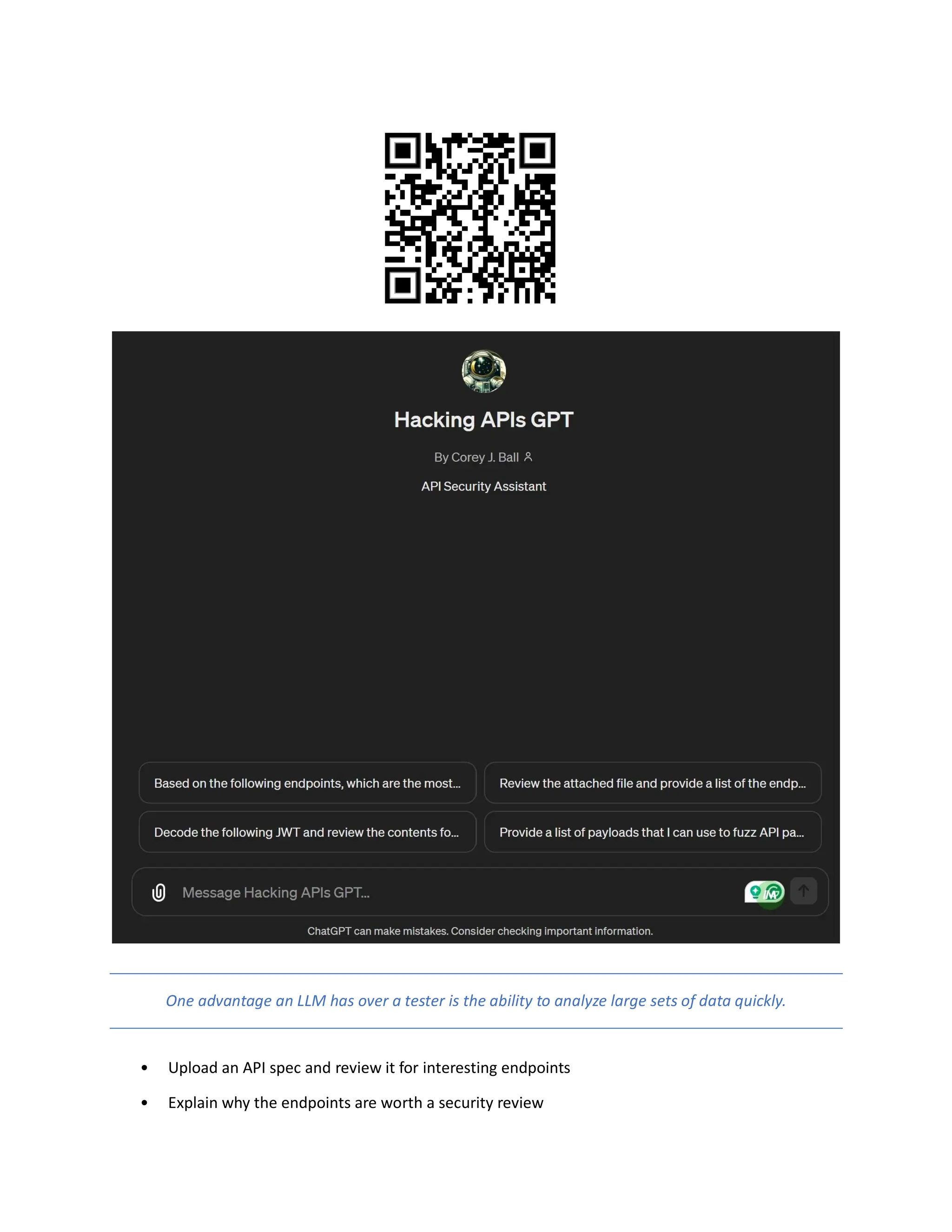
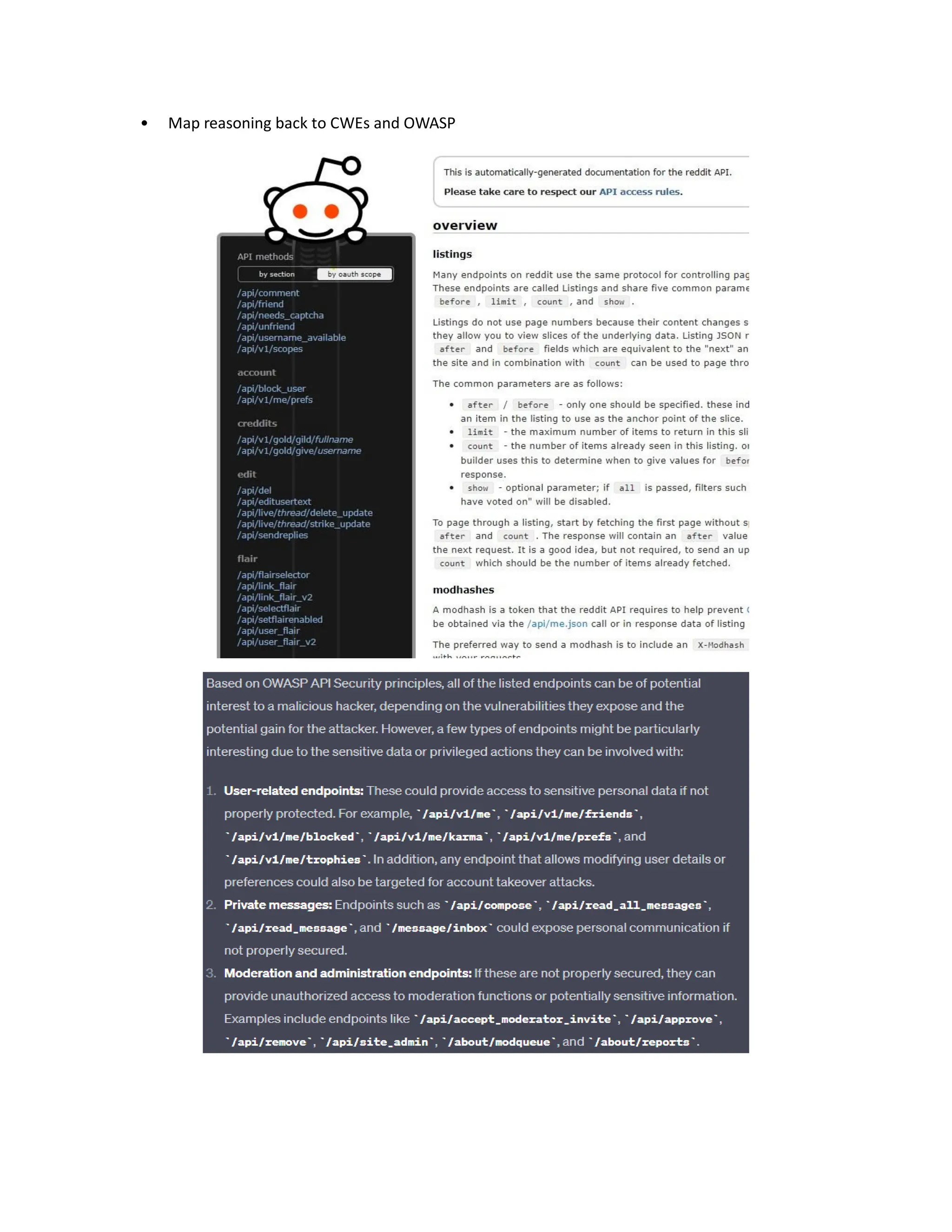
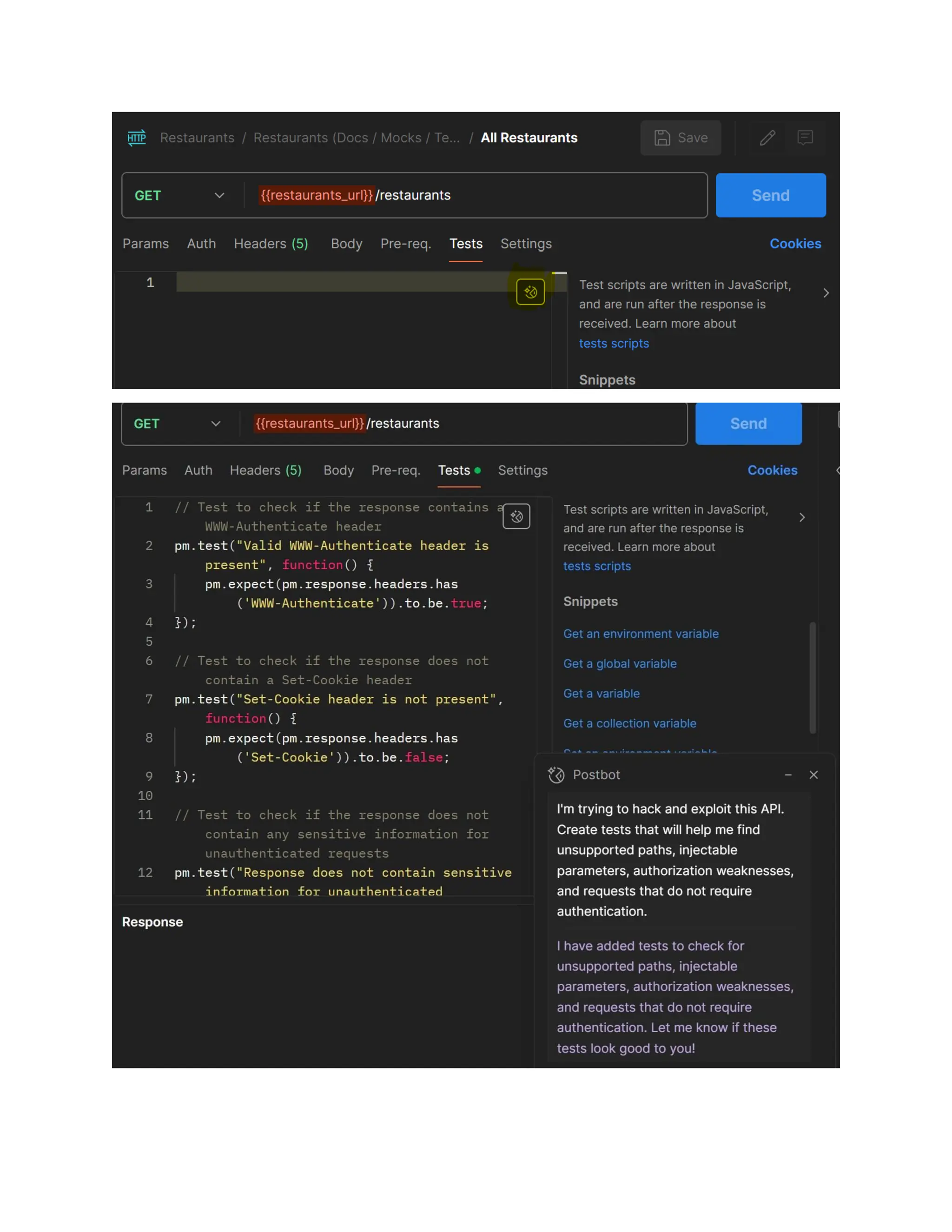
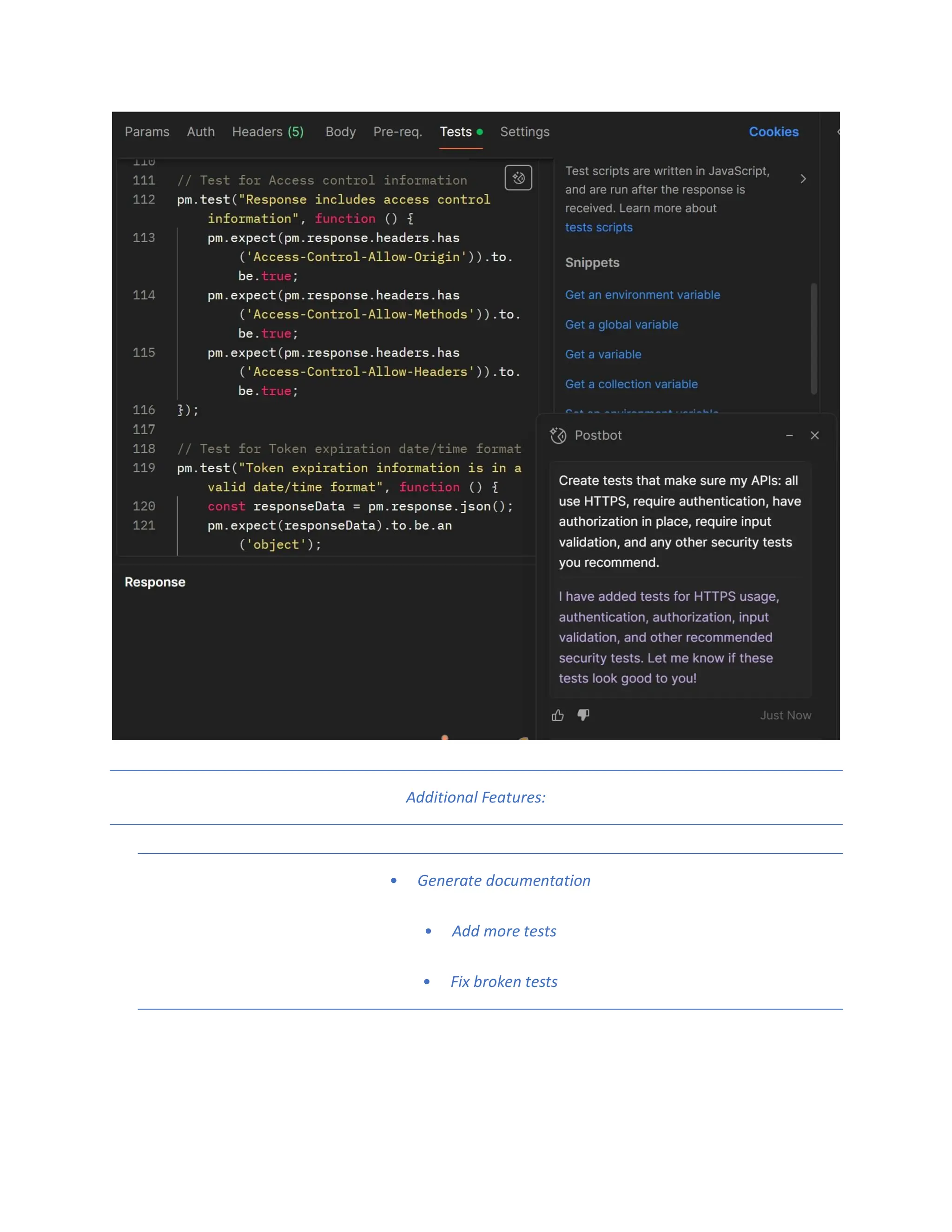
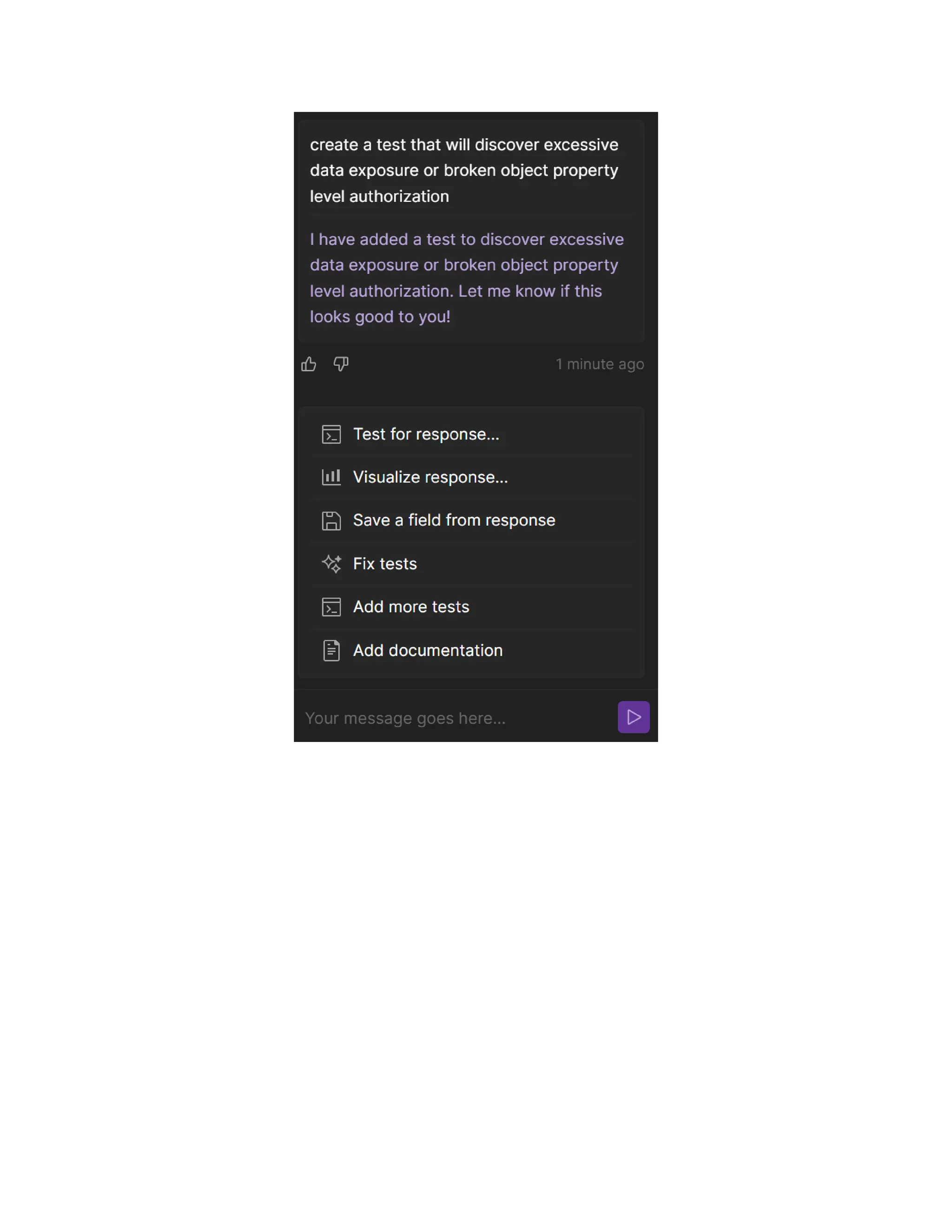
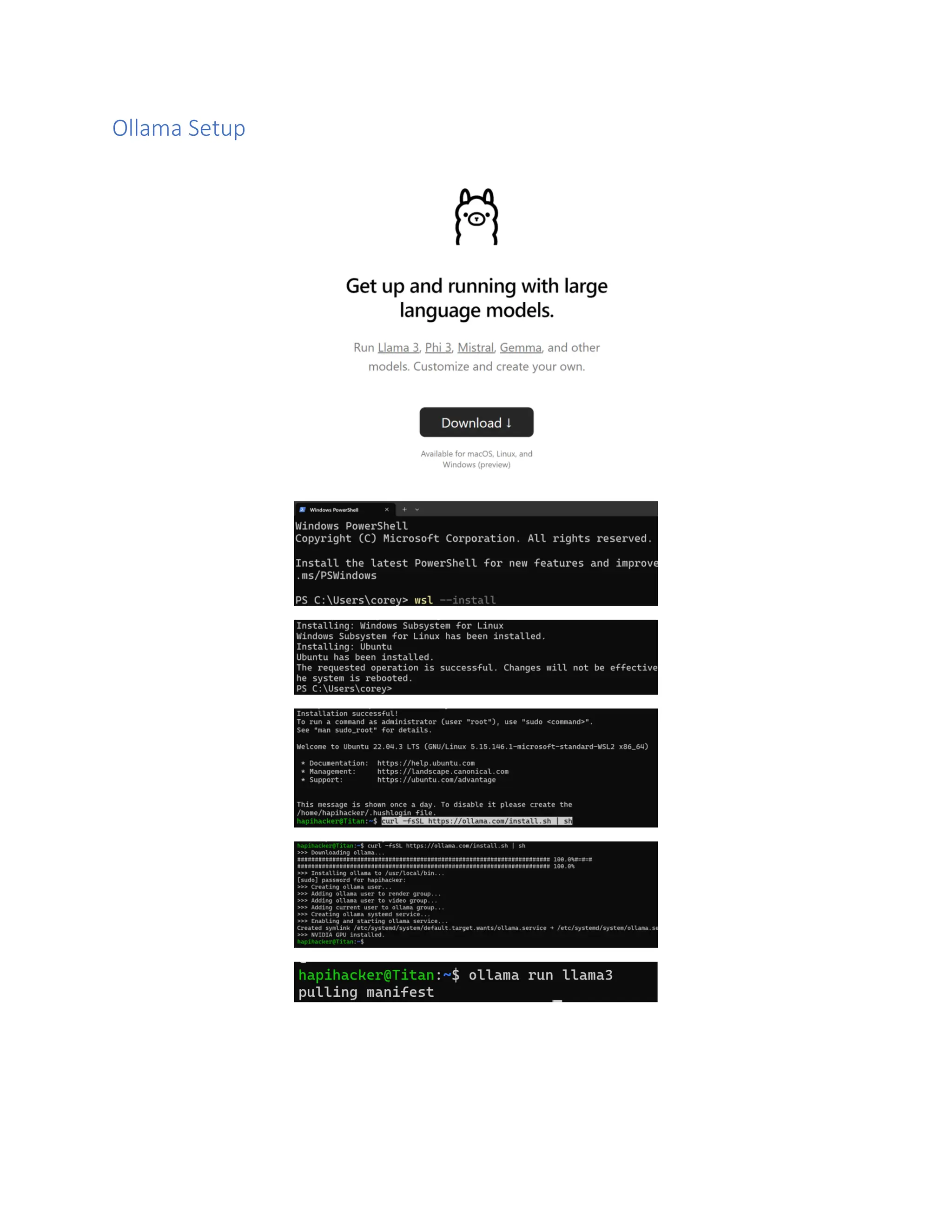
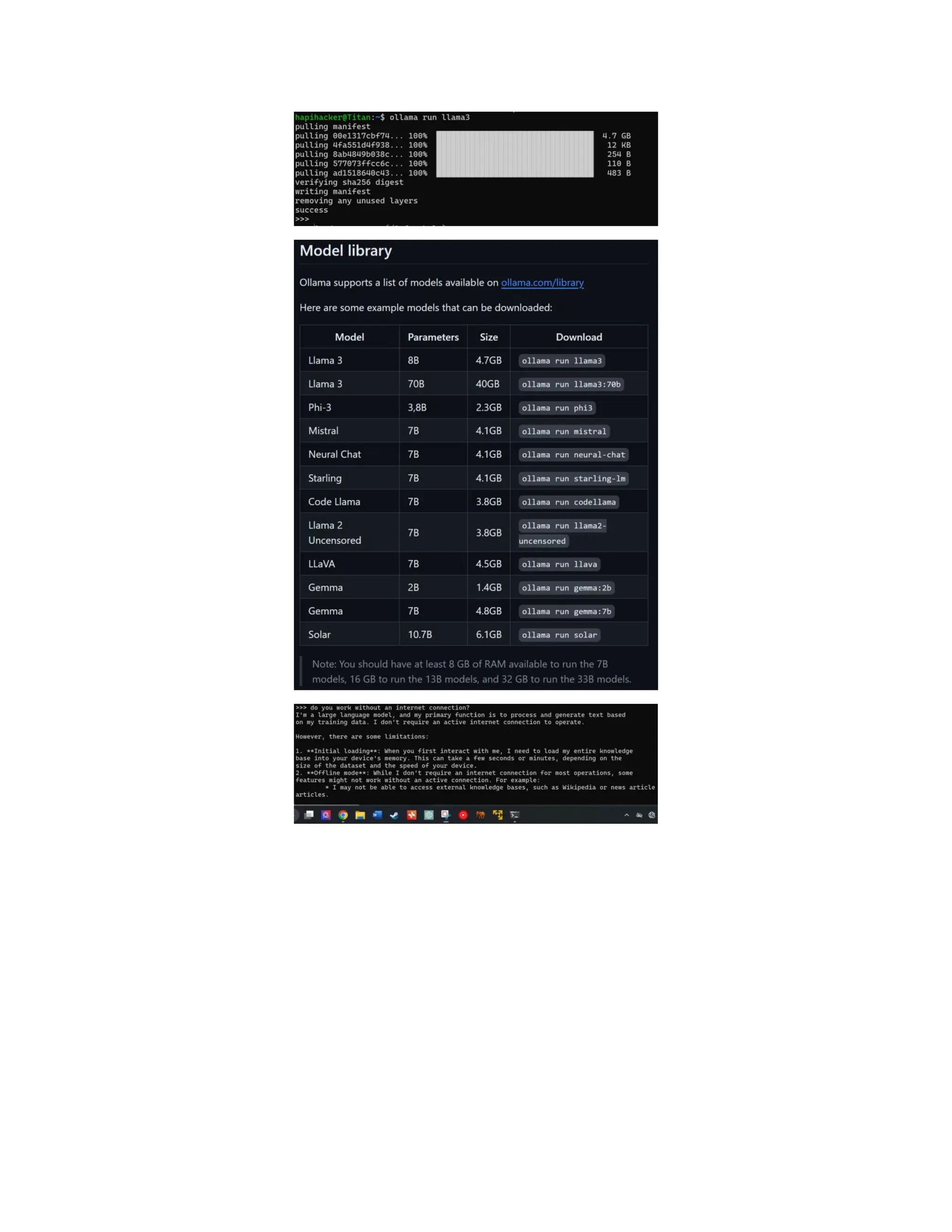
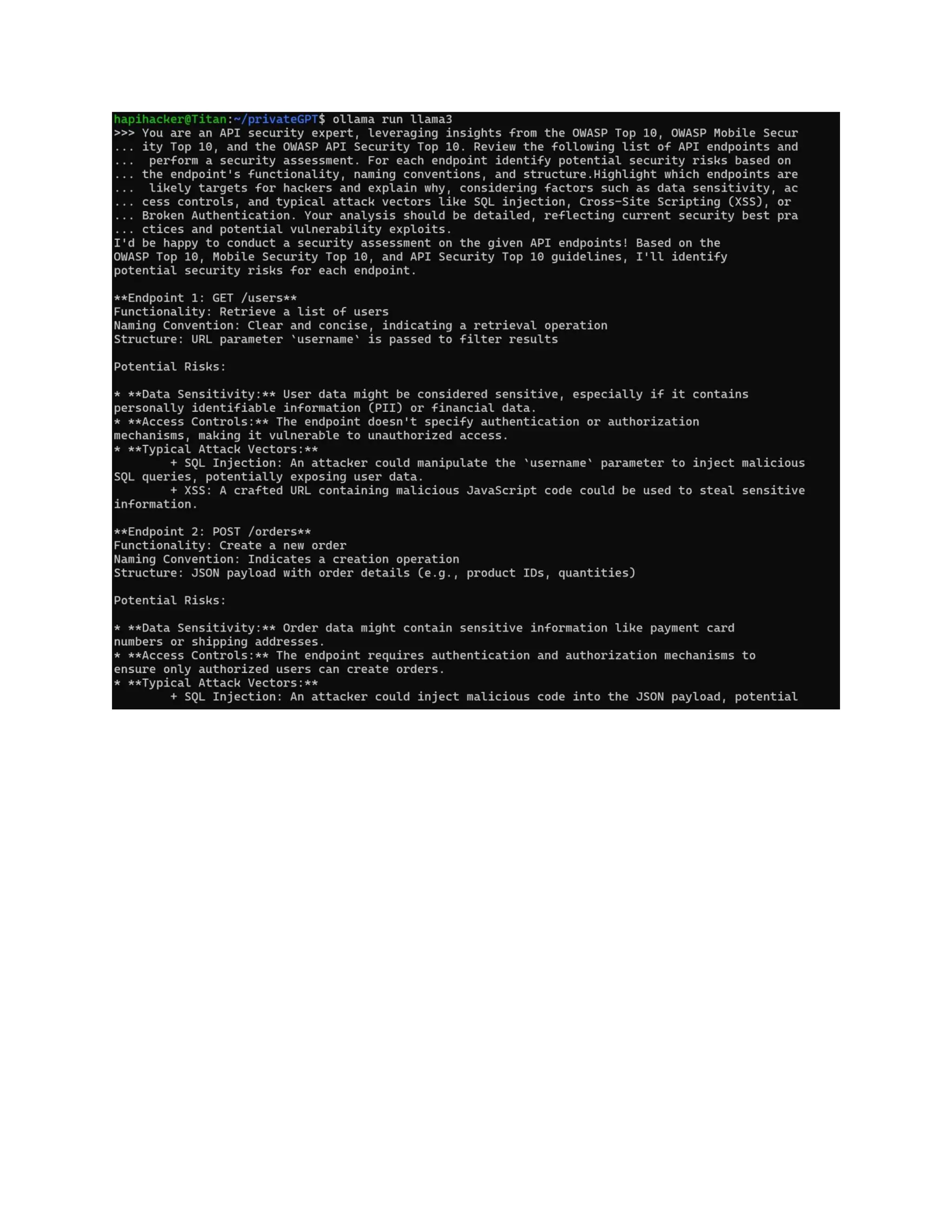
The document discusses enhancing API security using AI, highlighting the benefits of combining human testers with AI technologies for more effective security assessments. It introduces tools like Hacking APIs GPT and Postman's Postbot for security testing, showcasing features such as endpoint analysis, JWT review, and payload generation. The document emphasizes the need for sophisticated security measures as adversaries increasingly utilize AI in their attacks.