1. Benetton Group is a global fashion brand founded in 1965 in Italy that now has over 6,500 stores in 120 countries.
2. Compton Computers Pvt. Ltd. is an ISO 9001 certified Indian IT solutions provider and systems integrator with over 17 years of experience.
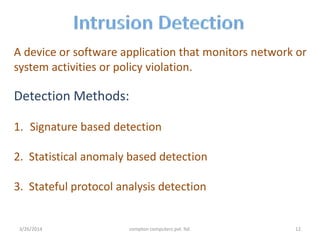
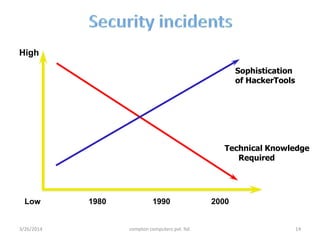
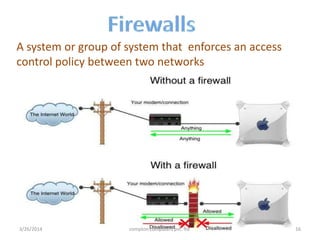
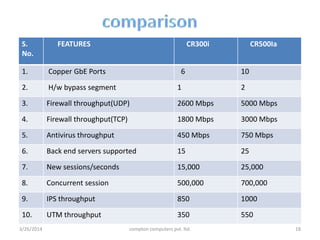
3. The presentation discusses network security problems such as privacy, authentication, data storage and loss, and intrusion detection, as well as solutions like encryption, redundancy, and cryptography.