Alphabeta
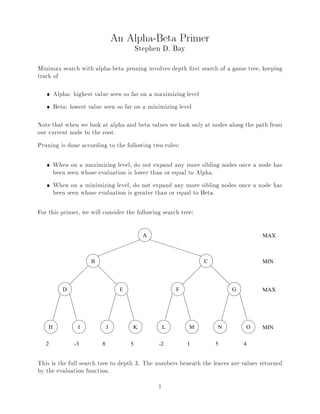
- 1. An Alpha-Beta Primer Stephen D. Bay Minimax search with alpha-beta pruning involves depth rst search of a game tree, keeping track of Alpha: highest value seen so far on a maximizing level Beta: lowest value seen so far on a minimizing level Note that when we look at alpha and beta values we look only at nodes along the path from our current node to the root. Pruning is done according to the following two rules: When on a maximizing level, do not expand any more sibling nodes once a node has been seen whose evaluation is lower than or equal to Alpha. When on a minimizing level, do not expand any more sibling nodes once a node has been seen whose evaluation is greater than or equal to Beta. For this primer, we will consider the following search tree: A MAX B C MIN D E F G MAX H I J K L M N O MIN 2 -3 8 5 -2 1 5 4 This is the full search tree to depth 3. The numbers beneath the leaves are values returned by the evaluation function. 1
- 2. Step 1 A MAX MIN MAX MIN alpha = unde ned, beta = unde ned, Expand A Step 2 A MAX B C MIN MAX MIN alpha = unde ned, beta = unde ned, Expand B 2
- 3. Step 3 A MAX B C MIN D E MAX MIN alpha = unde ned, beta = unde ned, Expand D Step 4 A MAX B C MIN D E MAX H I MIN 2 alpha = unde ned, beta = unde ned, Evaluate H and propagate values upwards. 3
- 4. Step 5 A MAX B C MIN >= 2 D E MAX H I MIN -3 alpha = 2, beta = unde ned, Evaluate I and propagate values upwards. Step 6 A MAX <= 2 B C MIN 2 D E MAX H I MIN alpha = unde ned, beta = 2, Expand E. Note that alpha is unde ned since we are at E and we only consider alpha-beta values from E to the root A i.e. values at B and A. 4
- 5. Step 7 A MAX = 2 B C MIN D E MAX H I J K MIN 8 alpha = unde ned, beta = 2, Evaluate J and propagate values upwards. Step 8 A MAX = 2 B C MIN = 8 D E MAX H I J K MIN alpha = 8, beta = 2, Prune K as evalj 8 2. Once K has been pruned we can propagate values up to A. 5
- 6. Step 9 = 2 A MAX 2 B C MIN D E MAX H I J K MIN alpha = 2, beta = unde ned, Expand C Step 10 = 2 A MAX B C MIN D E F G MAX H I J K MIN alpha = 2, beta = unde ned, Expand F 6
- 7. Step 11 = 2 A MAX B C MIN D E F G MAX H I J K L M MIN -2 alpha = 2, beta = unde ned, Evaluate L and propagate values upward. Step 12 = 2 A MAX B C MIN = -2 D E F G MAX H I J K L M MIN 1 alpha = 2, beta = unde ned, Evaluate M and propagate values upward. 7
- 8. Step 13 = 2 A MAX = 1 B C MIN 1 D E F G MAX H I J K L M MIN alpha = 2, beta = 1, Prune G as evalF 1 2. Once G has been pruned we can propagate values up to A. Step 14 2 A MAX 1 B C MIN D E F G MAX H I J K L M MIN The computer choses the move that leads to B. 8