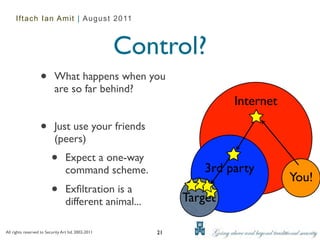
The document is a presentation by Iftach Ian Amit on data exfiltration techniques. It discusses infiltrating target networks through both technical exploits and social engineering. It then covers targeting specific data for acquisition using tools like ZeuS or SpyEye. Finally, it outlines various methods for exfiltrating the acquired data covertly, such as using SSL encryption, avoiding detection by DLP and IPS systems, and encoding the data.