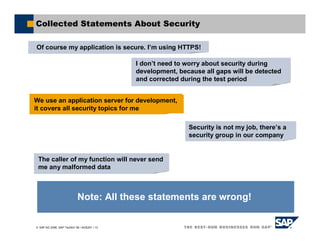
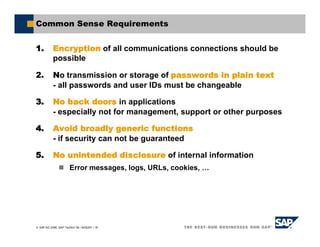
This document provides an overview of addressing web application security vulnerabilities. It discusses common security risks like cross-site scripting, SQL injection, and viruses. It emphasizes that security is everyone's responsibility and should be considered throughout the entire development process, from design to testing. The document also outlines different types of hackers and their motivations as well as best practices for input validation, access control, and virus protection.



















![SAP AG 2006, SAP TechEd ’06 / AGS201 / 26
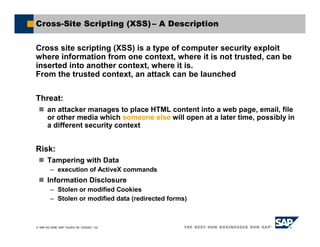
Cross Site Scripting – Attack Scenario 1
Output BETWEEN tags
StringsUtils.escapeToHTML()
<head>
<title>[CASE1]</title>
</head>
<table>
<tr>
<td>Username</td>
<td>[CASE1]</td>
</tr>
</table>](https://image.slidesharecdn.com/addressingwebapplicationsecurityvulnerabilities-230622100729-caeeeb4b/85/Addressing-Web-Application-Security-Vulnerabilities-pdf-26-320.jpg)
![SAP AG 2006, SAP TechEd ’06 / AGS201 / 27
Cross Site Scripting – Attack Scenario 2
Output INSIDE tags, but output is not a URL
StringUtils.escapeToAttributeValue()
<form name="[CASE2]">
<input type="text" name="user" value="[CASE2]">
<input type="text" name="user" value='[CASE2]'>
</form>
<a name="[CASE2]"><img height="50" width="[CASE2]"></a>
! Caveat:
Be sure to enclose values in double or single quotes! Omitting those
will make an attack easier](https://image.slidesharecdn.com/addressingwebapplicationsecurityvulnerabilities-230622100729-caeeeb4b/85/Addressing-Web-Application-Security-Vulnerabilities-pdf-27-320.jpg)
![SAP AG 2006, SAP TechEd ’06 / AGS201 / 28
Cross Site Scripting – Attack Scenario 3
Output is a URL
StringUtils.escapeToURL()
<a href='[CASE3]' style="[CASE3]">
<img src="[CASE3]" lowsrc="[CASE3]">
</a>
! Caveat:
Be sure to enclose values in double or single quotes! Omitting those
will make an attack easier](https://image.slidesharecdn.com/addressingwebapplicationsecurityvulnerabilities-230622100729-caeeeb4b/85/Addressing-Web-Application-Security-Vulnerabilities-pdf-28-320.jpg)
![SAP AG 2006, SAP TechEd ’06 / AGS201 / 29
Cross Site Scripting – Attack Scenario 4
Output is inside a SCRIPT context
StringUtils.escapeToJS()
<script>
var a = '[CASE4]';
alert("[CASE4]");
var a = [CASE4];
[CASE4];
</script>](https://image.slidesharecdn.com/addressingwebapplicationsecurityvulnerabilities-230622100729-caeeeb4b/85/Addressing-Web-Application-Security-Vulnerabilities-pdf-29-320.jpg)



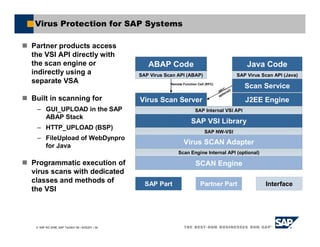
![SAP AG 2006, SAP TechEd ’06 / AGS201 / 35
Using the Virus Scan Interface
try {
myInstance = vsiService.getInstance();
if (myInstance != null) {
/* perform virus scan */
if (! myInstance.scanBytes(<your data>)) {
/* there was an infection,
* what needs to be done comes here */
}
} else {
/* The returned instance was null, this means, the virus scan profile is
not active
* => do here nothing to allow the scan to be switched
off */
}
} catch (VirusInfectionException vse) {
Infection[] myInfections = vse.getInfections();
String errorText = vse.getLocalizedMessage();
/* print out only the locale error text */
if (myInfections.length == 1) {
/* the scan engine has found the infection */
// ...
} else {
/* not expected error */
// ...
}
}](https://image.slidesharecdn.com/addressingwebapplicationsecurityvulnerabilities-230622100729-caeeeb4b/85/Addressing-Web-Application-Security-Vulnerabilities-pdf-35-320.jpg)