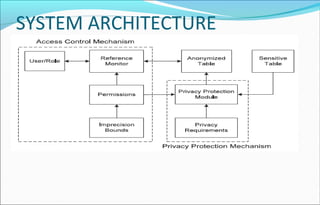
This document presents a privacy-preserving access control framework that balances accuracy and anonymity by incorporating heuristics for anonymization algorithms. It addresses the limitations of existing systems in minimizing imprecision and enforcing privacy policies while protecting sensitive data from linking attacks. The proposed system combines access control and privacy protection to satisfy predefined accuracy and privacy requirements, supported by specific hardware and software configurations.