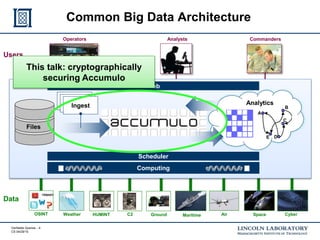
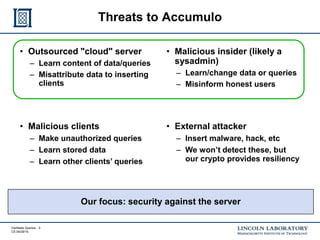
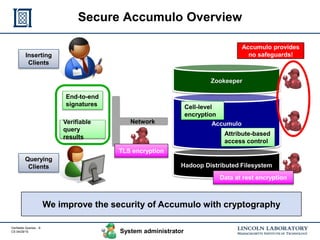
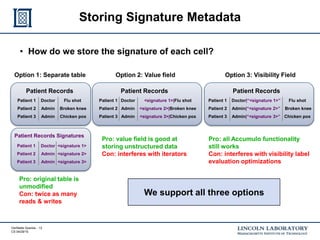
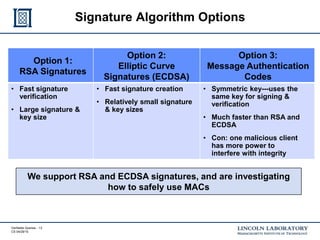
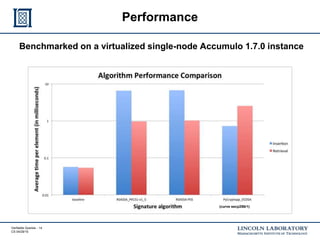
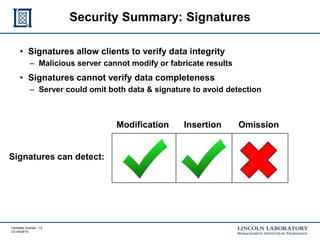
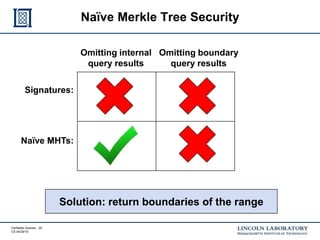
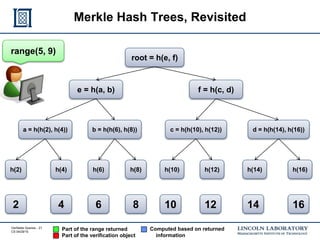
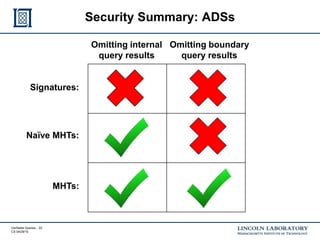
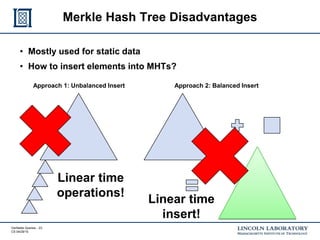
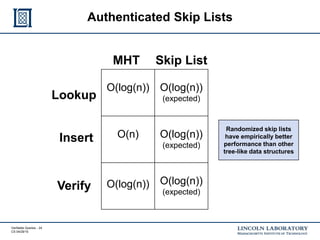
This document discusses enhancing the security of Apache Accumulo through cryptographic methods to ensure verifiable query results. It outlines various threats to data integrity and the implementation of end-to-end digital signatures, as well as the uses of authenticated data structures like Merkle hash trees and skip lists. The authors present their approach to improve data integrity, confidentiality, and performance within the context of big data architectures for national security applications.